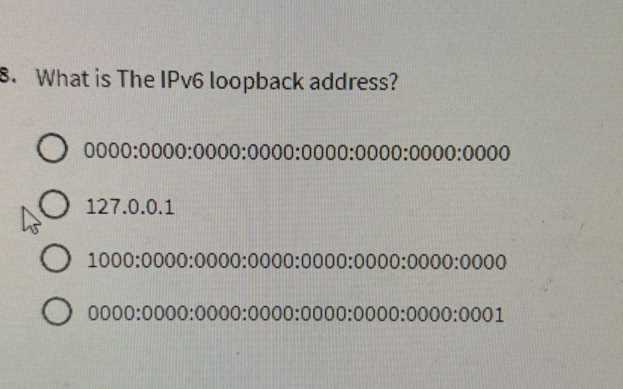
When preparing for a certification focused on advanced network technologies, understanding the core principles and configurations is essential. Whether you are a beginner or looking to deepen your knowledge, mastering these concepts will help you succeed in various assessments.
The content covered often focuses on topics such as addressing, routing, and the transition from older protocols to more modern solutions. It’s crucial to grasp the underlying structures and functions to confidently tackle real-world scenarios and certification tests alike.
By familiarizing yourself with key topics and practicing troubleshooting techniques, you can improve both your theoretical understanding and practical skills. Strong foundational knowledge is the key to addressing more complex scenarios and performing effectively during your training or assessments.
Ipv6 Exam Questions and Answers
As you prepare for a certification focused on the latest network protocols, it is essential to familiarize yourself with common topics that are frequently assessed. Understanding key concepts and practical scenarios will help you to excel and apply your knowledge confidently in real-world situations.
Key Areas to Focus On
To succeed, it is vital to concentrate on certain core areas, which will be central to the assessment. Here are the most commonly tested topics:
- Addressing schemes and their structure
- Routing protocols and mechanisms
- Security features in modern networking
- Network configuration and troubleshooting methods
- Transition strategies from older protocols
Preparation Tips for Success
Thorough preparation involves not only understanding theoretical concepts but also practicing real-life scenarios. Here are some steps to ensure you are well-prepared:
- Review the basics of network architecture and protocols
- Practice configuration and troubleshooting with various devices
- Test your knowledge through mock assessments
- Stay updated with the latest network standards and technologies
By focusing on these areas and incorporating hands-on practice, you will build the confidence necessary to tackle any challenge during your certification journey.
Understanding the Basics of Ipv6
In order to effectively manage modern network infrastructures, it is crucial to understand the fundamental principles that govern the operation of next-generation networking systems. These systems rely on advanced addressing and routing techniques, which form the backbone of the internet today. A solid grasp of these foundational concepts will provide the necessary framework for tackling more complex networking tasks.
Addressing Structure
At the core of the system is a new method for addressing devices on the network. This approach utilizes a much larger address space compared to older protocols, ensuring scalability and future-proofing for global connectivity. The addressing format is designed to accommodate an increasing number of devices, addressing a key limitation of previous systems.
Routing and Communication
Routing plays a crucial role in how data travels across networks, ensuring that information reaches its intended destination efficiently. Modern routing protocols are optimized to handle the increased volume of traffic and more complex network topologies. A deep understanding of these routing mechanisms is vital for maintaining smooth communication in a dynamic digital landscape.
Key Differences Between Ipv4 and Ipv6
As technology advances, newer networking standards emerge to address growing demands. One of the most significant developments in networking protocols is the transition from older addressing systems to more advanced and scalable solutions. Understanding the fundamental differences between these two systems is essential for network professionals and anyone looking to stay ahead in the industry.
Address Space and Format
The most noticeable difference lies in the size of the address space. The previous system utilized a 32-bit address, which limited the number of unique identifiers that could be assigned to devices. In contrast, the modern approach uses a 128-bit address, significantly expanding the available space. This change allows for a vastly larger number of devices to be connected, meeting the needs of the growing Internet of Things (IoT).
Configuration and Compatibility
Another key distinction is the method of configuration. The older system often requires manual configuration or additional tools for managing network settings, while the newer system offers enhanced automatic configuration features. This makes device setup and integration easier and more efficient. Additionally, compatibility between older and newer systems is often handled through transition mechanisms, but full compatibility is not always seamless.
Commonly Asked Ipv6 Exam Questions
When preparing for a certification related to advanced network protocols, certain topics are frequently covered due to their importance in understanding the fundamentals. These areas are often revisited in assessments to evaluate your ability to apply the concepts in practical situations. Being familiar with the most commonly addressed topics can greatly improve your chances of success.
Key Concepts Frequently Tested
Some topics are consistently highlighted in assessments due to their significance in real-world network management. Below is a table outlining the areas that are typically emphasized:
| Topic | Description |
|---|---|
| Addressing | Understanding the structure and format of modern network identifiers. |
| Routing | How data is directed through networks, including protocols and methods. |
| Security Features | Common security mechanisms to protect data and ensure privacy. |
| Transition Mechanisms | Methods for transitioning from older protocols to modern systems. |
| Configuration | Setting up network devices and managing addresses automatically. |
Understanding Configuration and Routing
Configuration and routing are critical for any network professional. These two areas are often tested for both their theoretical understanding and practical application. Ensuring you can configure network devices correctly and route data efficiently is essential for passing certification assessments.
IPv6 Addressing: Concepts You Must Know
Mastering the fundamentals of network addressing is essential for anyone working with modern networking protocols. With the expansion of the digital world, new methods of assigning unique identifiers to devices have emerged. These address formats are vital for ensuring proper communication between devices, allowing them to be routed across vast networks without conflict.
The core of this system revolves around the format and structure of network identifiers. These identifiers are far more expansive than previous systems, offering greater flexibility and scalability for the growing number of connected devices. Familiarity with key concepts such as address types, prefixes, and notation is essential for understanding how devices are recognized and how data is routed effectively.
Subnetting in IPv6: A Simple Guide
Subnetting is an essential concept in network management, enabling efficient use of address space by dividing a larger network into smaller, more manageable subnets. This technique is fundamental for organizing network traffic, improving security, and simplifying network administration. Understanding how to break down address blocks into subnets is a crucial skill for working with modern networking protocols.
Why Subnetting is Important
Subnetting helps optimize network performance by limiting broadcast domains and improving security by isolating traffic. It also makes address management more efficient, allowing network administrators to allocate address space based on actual need rather than using large address blocks inefficiently.
Basic Steps for Subnetting
Subnetting involves a few key steps to ensure proper division of address space. Here are the main concepts to understand:
- Determine the Network Size: Identify how many subnets and host addresses are needed.
- Choose the Right Prefix Length: The prefix defines the size of each subnet.
- Subnet Address Calculation: Use the prefix length to calculate valid subnet ranges.
- Assign Addresses: Allocate addresses within each subnet according to your network requirements.
By mastering these principles, you’ll be able to break down large address spaces effectively and ensure efficient network operation.
IPv6 Routing and Address Assignment
Routing and address assignment are fundamental aspects of modern networking, ensuring that data can travel efficiently across large, distributed systems. Properly configuring network devices to route traffic and allocate unique identifiers to each connected device is essential for maintaining connectivity and network integrity. These processes are integral to enabling communication across a wide variety of devices, from servers to end-user equipment.
Routing involves directing data packets through the network based on the destination addresses. Address assignment, on the other hand, ensures that every device has a unique identifier to ensure proper delivery. Both of these functions work together to provide a reliable and scalable networking environment that can support a growing number of connected devices and services.
Address Assignment Methods
There are several methods for assigning addresses to devices within a network, each serving different purposes depending on the network size and design:
- Static Assignment: Manually assigning a fixed address to each device. This method is typically used for servers and network devices that need a consistent, unchanging address.
- Dynamic Assignment: Automatically assigning addresses through protocols like DHCP, simplifying the process for large networks and ensuring efficient address distribution.
- Link-Local Addressing: A special type of address used for communication within a local network segment, without requiring global uniqueness.
Routing Mechanisms

Routing in modern networks is managed through various protocols designed to direct traffic based on destination addresses. Some common routing methods include:
- Static Routing: A fixed routing table configured manually, suitable for simple networks or when exact control is needed.
- Dynamic Routing: Protocols such as RIPng, OSPFv3, and BGPv6 are used to adapt the routing tables automatically as the network topology changes.
Mastering routing and address assignment techniques is crucial for ensuring that networks run smoothly and scale to meet the increasing demand for connectivity. A thorough understanding of these concepts will equip network professionals with the skills needed to configure and manage large-scale networks efficiently.
Multicast and Anycast in IPv6
In modern networking, communication methods play a vital role in ensuring data is transmitted efficiently across vast infrastructures. Two notable techniques for optimizing network traffic are multicast and anycast. These strategies are used to improve the way information is delivered, either to multiple recipients at once or to the most appropriate destination based on specific conditions. Both offer distinct benefits, depending on the type of data exchange required.
Comparison of Multicast and Anycast
The table below highlights the primary differences between multicast and anycast methods:
| Attribute | Multicast | Anycast |
|---|---|---|
| Communication Type | One-to-many | One-to-nearest |
| Recipient Target | Group of devices | Closest available endpoint |
| Common Use Cases | Live streaming, video conferences | DNS resolution, content delivery |
| Routing Process | Data sent to a group address | Data routed to the nearest server |
| Efficiency | Reduces bandwidth for group delivery | Minimizes latency by targeting proximity |
Applications in Real-World Scenarios
Multicast is particularly useful in situations where a single data stream needs to be sent to multiple users or devices simultaneously. Common applications include media streaming, live broadcasting, and online video conferencing, where delivering the same content to multiple viewers at once reduces the strain on network resources. By targeting a group address, multicast ensures that data is sent efficiently, eliminating the need to transmit separate copies to each individual receiver.
In contrast, anycast is most effective when the goal is to direct traffic to the closest or most responsive server. This is commonly seen in content delivery networks (CDNs) or Domain Name System (DNS) services, where users’ requests are routed to the nearest available server, thereby minimizing delay and improving overall network performance. Anycast ensures that the data reaches the intended recipient as quickly as possible, reducing latency and enhancing the user experience.
Both methods serve unique purposes in optimizing data flow across networks. While multicast efficiently manages traffic for large-scale broadcasts, anycast ensures low-latency connections by directing users to the best available resource. Together, they contribute to more effective network management, providing tailored solutions for different communication needs.
IPv6 Security Features and Protocols
As the landscape of networking evolves, ensuring robust security measures becomes increasingly critical. With growing concerns about data breaches and cyber threats, securing network communication is essential. A variety of built-in security features and protocols are designed to protect data integrity, confidentiality, and authentication in modern network environments. These protocols are vital in safeguarding the communication channels and preventing unauthorized access or tampering.
Key Security Features
- Encryption: Many protocols offer end-to-end encryption, ensuring that data transmitted across the network is unreadable to anyone who might intercept it.
- Authentication: Secure methods are in place to verify the identities of devices or users attempting to access the network, preventing unauthorized access.
- Data Integrity: Mechanisms are employed to ensure that data has not been altered or tampered with during transmission.
- Access Control: Control lists and firewalls are often used to restrict access to sensitive parts of the network or specific services.
Protocols Enhancing Security
Several protocols have been developed specifically to enhance security at various layers of the network. These protocols work together to protect data, ensure secure communication, and verify authenticity.
- IPsec (Internet Protocol Security): A suite of protocols that provides encryption, authentication, and integrity for IP packets. It operates at the network layer to secure communication between devices.
- SEcure Neighbor Discovery (SEND): A security extension to the Neighbor Discovery Protocol (NDP), designed to protect against spoofing attacks, such as address resolution attacks.
- Authentication Header (AH): A protocol used for data integrity and authentication. It ensures that the data has not been modified and that the sender is verified.
- Encapsulating Security Payload (ESP): This protocol provides confidentiality, integrity, and authentication by encrypting the payload data and creating security associations.
Security Considerations
- Privacy Concerns: With the large-scale deployment of devices, it’s crucial to ensure that personal information is protected from potential misuse.
- Threat Detection: Continuous monitoring and analysis of network traffic are necessary to detect and preve
Configuring IPv6 on Network Devices
Setting up advanced network configurations is crucial for ensuring smooth communication and optimal performance across a network. As networks grow, the need for a robust addressing system becomes evident. Network devices must be properly configured to handle modern addressing schemes. The configuration process involves enabling support for this new addressing format and ensuring that devices communicate efficiently within the network.
Basic Configuration Steps
To set up a network device to support the new addressing format, the following steps are commonly involved:
- Enable IPv6 on the Interface: The first step is to activate the appropriate network interface for the new addressing scheme.
- Assign an Address: Assign a unique address to the device or interface. This can be either static or dynamic, depending on the network requirements.
- Configure Routing: Set up appropriate routing protocols to ensure that the device can forward traffic to other network devices or external networks.
- Verify Connectivity: Once the basic configurations are complete, testing the connectivity with other devices is essential to ensure proper communication.
Types of Address Assignment
Network devices can obtain addresses in different ways depending on the network setup. These methods are:
- Static Address Assignment: Manually configuring an address on the device for a permanent setup. This ensures that the address remains the same even after rebooting.
- Dynamic Address Assignment: Using protocols like DHCP to automatically assign an address to the device as it joins the network. This approach reduces manual configuration efforts.
- Link-Local Addressing: A self-configured address used for communication between devices on the same local network without requiring external configuration.
Configuring Routing Protocols
Routing is an essential part of the configuration process, ensuring devices can communicate across different subnets. Common routing protocols include:
- OSPFv3 (Open Shortest Path First version 3): A popular interior gateway protocol used to distribute routing information between devices within an autonomous system.
- RIPng (Routing Information Protocol next generation): A simplified distance-vector routing protocol used for smaller networks.
- BGP (Border Gateway Protocol): An exterior gateway protocol that is
Common Mistakes in IPv6 Configuration
When setting up modern networking systems, incorrect configurations can often lead to communication issues, poor performance, or security vulnerabilities. Some common errors occur during the setup of addressing and routing protocols, which can hinder the efficiency of a network. Understanding these mistakes and how to avoid them is key to ensuring that devices operate as expected in a dynamic network environment.
Common Configuration Errors
Here are several typical mistakes often encountered during configuration:
- Incorrect Address Assignment: Assigning the wrong type of address, such as using a global address where a link-local address is needed, can cause devices to fail to communicate properly.
- Misconfigured Prefix Length: Incorrectly setting the subnet mask or prefix length can lead to routing issues or devices being unable to communicate with one another.
- Failing to Enable Routing Protocols: Forgetting to enable the necessary routing protocols or not configuring them correctly can prevent devices from exchanging information, leading to connectivity issues.
- Incorrect Default Gateway Settings: Failing to correctly configure the default gateway address can result in the device being unable to route traffic to other networks.
Addressing and Connectivity Issues
Addressing errors are among the most frequent causes of network connectivity problems. Here are some specific pitfalls:
- Using the Wrong Address Scope: Assigning an address in the wrong scope (such as a global address on a private network) can cause devices to be unreachable, particularly when trying to communicate across different segments of the network.
- Not Configuring Address Autoconfiguration Properly: Failing to enable address autoconfiguration on devices can result in static IP addressing that may not align with network requirements or growth.
- Overlapping Addresses: Using overlapping address ranges in different subnets can lead to routing conflicts and packets being dropped or misdirected.
Routing Protocol Setup Mistakes
Routing protocols are critical for the proper flow of data across multiple networks. Misconfiguring routing can lead to devices being unable to find the correct path to communicate. Here are some common errors:
- Missing or Incorrect Routing Tables: Fa
Understanding IPv6 Header Structure
The header structure of modern networking protocols plays a critical role in ensuring that data is transmitted efficiently across networks. A well-designed header not only contains essential information for routing and delivery but also supports various features like security and quality of service. Understanding the components of the header is crucial for network administrators and engineers to configure and troubleshoot communication effectively.
Components of the Header
The header structure consists of multiple fields, each serving a distinct function in the data transmission process. These fields help to route, deliver, and manage the packet efficiently. Below is a table that breaks down the primary components of the header:
Field Description Version Specifies the version of the protocol being used, ensuring that the packet is compatible with the correct protocol standard. Traffic Class Indicates the type of traffic and helps prioritize packets based on the service requirements. Flow Label Used for label-based packet handling and can prioritize certain data streams, improving the handling of real-time data like video or voice. Payload Length Defines the length of the data in the packet, excluding the header, allowing the receiver to determine the size of the transmitted data. Next Header Indicates the type of the next header that follows the current header, allowing multiple protocols to work together in the data transmission process. Hop Limit Specifies the maximum number of hops (routers) the packet can pass through before being discarded, protecting the network from endless loops. Source Address Specifies the originating device’s address, allowing the receiver to identify the source of the packet. Exam Tips for IPv6 Network Configuration
Successfully configuring networks requires both theoretical knowledge and practical skills. Whether you’re setting up a small-scale home network or managing complex enterprise systems, having a solid understanding of network configuration principles is essential. There are several tips and strategies that can help streamline the configuration process and ensure you’re prepared for real-world challenges.
1. Understand the Addressing Scheme
One of the most important aspects of network configuration is knowing how to assign and manage addresses. It is crucial to understand the structure of address formats, including how to assign static and dynamic addresses correctly. Familiarize yourself with address types like unicast, multicast, and anycast, as well as their respective usage scenarios.2. Master Routing Protocols
Routing protocols play a vital role in network communication. Make sure to understand both static and dynamic routing protocols, such as the differences between RIPng, OSPFv3, and BGP, as well as how they interact with addressing schemes to guide data across the network efficiently.3. Plan for Subnetting
Subnetting is an essential skill for managing large networks. Understanding how to divide the address space into smaller subnets is crucial for both performance and security. Practice subnetting to ensure you can quickly calculate subnet sizes and ranges when needed.4. Utilize Security Features
Network security should always be a top priority. Learn about built-in security mechanisms such as IPsec and how to configure firewalls, access control lists (ACLs), and other protective measures to secure your network.5. Get Comfortable with Configuration Commands
Being able to quickly execute configuration commands in a command-line interface (CLI) will greatly improve your efficiency. Practice using common commands related to address assignment, routing, and network diagnostics.6. Test and Troubleshoot
Testing is an integral part of network configuration. Always validate your setup by using tools like ping, traceroute, and show commands to ensure eHow to Troubleshoot IPv6 Connectivity
Network connectivity issues can be frustrating, especially when troubleshooting advanced protocols. Identifying and resolving these problems involves a systematic approach to isolate the source of the issue. Whether dealing with misconfigurations, hardware failures, or routing problems, effective diagnostic steps are key to ensuring reliable network performance.
1. Check Physical Connections
Before diving into software or configuration issues, ensure that all cables, devices, and hardware components are properly connected. This includes verifying network interfaces on routers, switches, and end devices. A loose or faulty cable can cause connectivity problems, so it’s always a good idea to start by inspecting physical connections.2. Verify Address Assignment
One common issue is improper address assignment. Confirm that devices have the correct addresses and are within the proper address range. You can use tools like ipconfig (on Windows) or ifconfig (on Linux) to check for correct IP address configurations, including the network prefix and gateway addresses.3. Test Connectivity with Ping
Once addresses are verified, use the ping command to test connectivity between devices. If devices fail to respond, it could indicate issues with routing, address assignment, or firewall settings. Try pinging the local gateway first, followed by remote devices, to isolate where the connectivity breakdown occurs.4. Use Traceroute to Identify Hops
To troubleshoot routing problems, use the traceroute command. This will help identify where the packets are being dropped or delayed along the path. The output will show each hop along the route and provide insight into where the issue may lie, such as in intermediate routers or misconfigured routing tables.5. Check for Proper Routing Configuration
Routing misconfigurations are a frequent cause of connectivity issues. Ensure that the routing tables are correctly set up on routers and that routing protocols are functioning properly. Verify that the correct routes exist for local and remote network destinations, and check for any conflicting entries that could block traffic.6. Review Firewall Settings
Firewalls can block traffic if they are not configured properly. Check the firewall settings on both routers and end devices to ensure that there are no rules preventing necessary traffic. Make sure that the required ports are open and that no security policies are misconfigured to block legitimate traffic.7. Test DNS Resolution
If users can access IP addresses but not domain names, the issue may lie with the DNS configuration. Ensure that DNS servers are correctly specified on devices and that they are responsive. Use commands like nslookup to verify that DNS queries are being resolved properly.8. Check for Duplicate Addresses
Duplicate IP addresses on a network can cause severe connectivity issues. If two devices are assigned the same address, network traffic can be disrupted. Check for duplicates by examining the device logs or using network scanning tools that detect conflicting addresses.9. Review Configuration Documentation
Sometimes, the issue can be traced back to an error in the original network configuration. Reviewing the configuration documentation or any recent changes can provide insight into what may have been misconfigured. Compare current settings with the intended design to spot any discrepancies.10. Use Diagnostic Tools
Finally, leverage advanced diagnostic tools and logs. Network analyzers like Wireshark can capture packets in real time, helping you observe traffic flow and identify where packets are being lost or misrouted. Additionally, checking device logs may reveal critical error messages or warning signs that can lead to the root cause of the problem.Real-World Applications of IPv6
As the demand for internet-connected devices continues to surge, the need for a more scalable, secure, and efficient addressing system has become increasingly evident. The transition to a new addressing protocol has opened up numerous opportunities across various sectors. This change allows for enhanced performance, seamless communication, and more reliable network services in modern infrastructures.
Smart Cities and Internet of Things (IoT)
One of the most significant uses of advanced networking technology is in the development of smart cities and the growing ecosystem of IoT devices. With millions of connected devices generating vast amounts of data, a robust addressing system is essential for enabling smooth communication between these devices. As more objects, from household appliances to traffic sensors, require unique IP addresses, the availability of a much larger address space becomes crucial.
Smart home automation systems, wearable technology, smart meters, and even connected vehicles all rely on an efficient network infrastructure to operate. The larger address pool enables each of these devices to maintain unique identifiers without the risk of address conflicts, facilitating the seamless integration of various systems within smart environments.
Enhanced Security Features
Security is another area where advanced networking protocols provide noticeable benefits. The new addressing system integrates advanced security features, including built-in encryption and authentication mechanisms, offering a more secure foundation for communication. These features help reduce vulnerabilities that exist in legacy protocols, ensuring that data is transmitted safely between devices and networks.
As businesses, government entities, and other organizations increasingly rely on digital infrastructures, the need for stronger security protocols grows. The modern protocol offers a more resilient framework that mitigates common attacks like spoofing or eavesdropping, providing a more secure internet experience for both individuals and organizations alike.
Telecommunications and Mobile Networks
Telecommunications and mobile service providers are also among the key industries benefiting from the shift to more advanced networking technologies. The exponential growth in mobile data usage, especially with the advent of 5G networks, demands a more robust addressing scheme to handle the higher volume of mobile devices and data traffic. Network operators can now support more mobile devices simultaneously, ensuring stable performance even as the number of connected devices skyrockets.
In addition, mobile networks benefit from improved routing and simplified configuration processes. Devices can now connect with greater efficiency, experiencing fewer interruptions in service, as the overall addressing system can handle a much higher number of connections without the same risk of congestion.
IPv6 Study Resources and Tools
To successfully navigate the complexities of modern networking technologies, utilizing a variety of study materials and tools is essential. These resources provide valuable insights into advanced networking concepts, protocols, and configurations, preparing individuals for real-world application as well as certification assessments. Understanding these systems in depth requires access to comprehensive guides, interactive platforms, and practice scenarios.
Online Courses and Tutorials
Engaging with structured online learning platforms is one of the most effective ways to build foundational knowledge and refine specific technical skills. Many reputable websites and institutions offer specialized courses that cover all aspects of network management, including address allocation, routing principles, and configuration techniques.
- Udemy
- LinkedIn Learning
- Coursera
- Pluralsight
These platforms often feature video tutorials, quizzes, and hands-on labs, allowing learners to reinforce their understanding through practical exercises. Some even offer certifications upon completion, which can be valuable for career advancement.
Books and Guides
Books dedicated to networking provide in-depth coverage of theoretical and practical aspects. Key titles often explain the principles behind network architecture, configuration, security features, and troubleshooting techniques, all of which are essential for mastering the subject. These resources allow readers to study at their own pace and refer to them as needed.
- Networking Fundamentals by Michael K. – A comprehensive guide to understanding networking protocols and practices.
- The Routing TCP/IP Series by Jeff Doyle – In-depth coverage of routing principles and best practices.
These textbooks often come with case studies, examples, and exercises that help deepen your understanding of complex concepts and improve problem-solving skills.
Interactive Simulators and Labs

Practical application through simulation is a great way to test knowledge in a controlled environment. Virtual labs and simulators allow learners to configure networks, troubleshoot issues, and simulate real-world scenarios without the need for physical devices. These tools offer a hands-on approach to mastering networking tasks in a risk-free setting.
Preparing for Advanced Network Configuration Topics
To master the intricate details of modern networking, it’s essential to prepare thoroughly for complex topics that involve advanced configurations, protocols, and troubleshooting. These topics often require a deep understanding of system behavior, how different protocols interact, and how to efficiently manage large-scale network environments. Preparation involves not only learning the theory but also gaining practical experience through hands-on exercises and real-world scenarios.
Key Areas to Focus On
When tackling advanced topics, focus on the following critical areas to build a strong foundation:
- Routing Protocols: Understanding dynamic routing, including RIPng, OSPFv3, and EIGRP for IPv6, is essential for configuring routing in large networks.
- Security Protocols: Mastering security mechanisms such as IPsec, access control lists (ACLs), and filtering is critical for safeguarding data transmission.
- Addressing and Subnetting: A thorough understanding of address planning, subnetting, and CIDR notation is crucial for efficient address allocation.
- Advanced Troubleshooting: Being able to quickly diagnose and resolve network issues through diagnostic tools like ping, traceroute, and packet captures is a must.
Recommended Study Strategies
To ensure a comprehensive understanding of advanced networking concepts, follow these strategies:
- Hands-On Practice: Use network simulators or set up your own lab to configure devices, simulate network traffic, and resolve issues in real-time.
- Lab Work and Case Studies: Work through case studies and lab exercises to apply theoretical knowledge to practical situations. This helps reinforce concepts and prepare for real-world applications.
- Review Network Design: Understand how large-scale networks are designed, implemented, and managed, with a focus on scalability and optimization.
Useful Tools for Preparation
Several tools can aid in the learning process by providing simulated environments for practice and enhancing understanding of complex network configurations:
- Packet Tracer: An essential tool for simulating various network configurations and testing routing protocols.
- GNS3: An advanced
Future Trends in IPv6 Technology
The rapid evolution of networking technologies is driven by the increasing demand for efficient, scalable, and secure solutions. With the growing number of devices and the rise of advanced applications such as the Internet of Things (IoT), 5G, and cloud computing, networking protocols must evolve to meet these new challenges. The future of network communication will focus on addressing limitations, ensuring scalability, improving security, and optimizing performance to support emerging innovations.
Emerging Technologies Shaping the Future
Several trends are set to transform the landscape of network protocols in the coming years:
- Growth of the Internet of Things (IoT): With an increasing number of connected devices, the need for scalable address solutions is paramount. Future protocols will need to handle vast numbers of devices, each requiring its own unique identifier.
- 5G Network Expansion: The deployment of 5G networks will demand enhanced capabilities for high-speed, low-latency communication. This will drive innovations in networking that can accommodate massive data throughput and more efficient connection management.
- Automation and Network Management: The rise of automation tools will enable more streamlined network configuration, monitoring, and troubleshooting. Automation will be key to reducing the complexity of managing large-scale network infrastructures.
- Focus on Security Enhancements: As cyber threats evolve, the need for advanced encryption, secure authentication, and proactive defense mechanisms will push the development of stronger security protocols that are integrated into the core of networking systems.
Technological Innovations on the Horizon
Several groundbreaking technologies are expected to further impact networking practices:
- Quantum Computing: The advent of quantum computing could revolutionize data processing and encryption, necessitating the development of new security measures to address the enhanced computational capabilities of quantum systems.
- Artificial Intelligence (AI): AI-powered network management tools will enable intelligent traffic routing, predictive maintenance, and automated security threat detection, allowing networks to operate more efficiently and securely.
- Edge Computing: The shift toward edge computing, where data is processed closer to the source, will require protocols that minimize latency and enhance real-time data handling. This will be particularly important for applications in autonomous vehicles, smart cities, and industrial automation.