Mastering the principles of network communication is a crucial step for anyone pursuing a career in technology. This guide focuses on foundational concepts that help you understand how systems interact and transmit information efficiently.
Through a detailed exploration of essential topics, you will learn about the various components, protocols, and methods used to ensure seamless connectivity across devices. Understanding these basics lays the groundwork for more advanced studies in system architecture and network management.
Whether you are reviewing core principles or preparing for assessments, this resource provides clear explanations and practical insights to enhance your knowledge. With a focus on real-world applications, you can build the skills necessary to excel in this dynamic field.
Understanding the Basics of CCNA 1
Building a strong foundation in networking concepts is essential for anyone aiming to excel in the field of digital communication. This section highlights the key principles that form the backbone of network systems, helping you grasp how information is transferred and managed effectively.
Core Concepts of Network Operations
At the heart of modern communication systems lies the ability to interconnect devices seamlessly. By studying how data is routed, processed, and secured, you gain insight into the mechanisms that keep networks functional and reliable. This knowledge is crucial for troubleshooting and optimizing performance in both small and large infrastructures.
Understanding Protocols and Configurations
Protocols act as the rules that govern communication between devices, ensuring that data reaches its intended destination without errors. Learning about these protocols and how they influence configurations provides a deeper understanding of how networks operate. From addressing schemes to secure transmissions, these elements are integral to efficient system management.
Key Networking Concepts for Beginners
Understanding the foundational elements of digital communication is essential for anyone starting in the field. These concepts provide the tools needed to grasp how information moves across interconnected systems and the technologies that enable seamless interactions.
The Role of Communication Systems
Every network relies on a set of components working together to exchange data efficiently. From routing paths to connection types, recognizing how these elements contribute to the overall system helps in managing and improving connectivity. Learning these basics ensures a smoother transition into more advanced topics.
Importance of Structured Frameworks
A structured approach to organizing and managing data flow is critical for efficiency and reliability. Frameworks ensure that each process, from sending to receiving information, happens in a controlled and predictable manner. By familiarizing yourself with these systems, you can better navigate the complexities of modern communication technologies.
Essential Components of Modern Networks
To understand how digital communication operates, it is vital to explore the primary elements that form the backbone of network systems. These components ensure smooth connectivity, efficient data transfer, and secure communication between devices.
- Switches: Devices that connect multiple systems within a local area, enabling seamless communication between them by directing data to the correct destination.
- Routers: Essential for connecting different networks, these devices manage traffic by determining the most efficient path for data to travel.
- Access Points: Provide wireless connectivity, allowing devices to join the network without physical connections.
- Cables and Connectors: Serve as the physical medium for transferring information in wired setups, ensuring a stable and secure connection.
In addition to hardware, software tools are equally important in maintaining and monitoring system performance. These tools help identify and resolve issues, optimizing the overall efficiency of the network infrastructure.
- Firewall Software: Protects systems by managing and blocking unauthorized access, ensuring secure operations.
- Monitoring Tools: Track performance metrics and identify potential bottlenecks or failures.
How Data Flows Through Networks
Efficient communication across connected systems relies on the seamless movement of information. Understanding the process of data transfer is key to optimizing performance and ensuring reliable interactions between devices.
- Data Segmentation: Large chunks of information are divided into smaller units, called packets, to facilitate easier transfer and reassembly at the destination.
- Routing and Switching: Packets are directed through various paths using devices that determine the most efficient route based on network conditions and configurations.
- Protocol Management: Protocols establish the rules for communication, ensuring packets are transmitted and received without errors or loss.
The journey of data involves several layers, each handling specific aspects of the process:
- Physical Transmission: Data moves through cables, wireless signals, or other mediums, depending on the network setup.
- Addressing and Identification: Each packet carries destination and source addresses, enabling devices to recognize where information should go.
- Reassembly and Interpretation: Once received, packets are combined, and their content is interpreted by the receiving device or application.
By analyzing this flow, you can identify potential points of failure, optimize routing, and enhance the overall efficiency of communication systems.
The Role of IP Protocols in Networking
Communication across interconnected systems depends heavily on structured rules that govern the transfer of data. IP protocols play a vital role in ensuring seamless and efficient interaction between devices, regardless of their location or type.
Understanding the Core Functions
IP protocols provide a framework for assigning unique addresses to devices, directing data packets to their intended destinations, and ensuring they arrive in the correct sequence. These functions are critical for maintaining order in complex networks.
Comparison of Protocol Versions
Different versions of IP protocols have distinct characteristics and are optimized for varying requirements. The evolution of these versions reflects the growing need for scalability, speed, and security.
| Feature | Version 4 | Version 6 |
|---|---|---|
| Address Space | 32-bit, supports approximately 4.3 billion addresses | 128-bit, supports a virtually unlimited number of addresses |
| Security | Basic support with optional configurations | Integrated security features, including encryption |
| Efficiency | Designed for earlier networks, less efficient for modern use | Optimized for high-speed and scalable systems |
By understanding these protocols, network managers can make informed decisions about configurations and upgrades to support growing demands and enhance overall performance.
Network Security Fundamentals Explained
In today’s interconnected world, safeguarding data and network infrastructure has become a top priority. Understanding the principles of network protection is essential for preventing unauthorized access, data breaches, and other cyber threats.
Network security involves a combination of technologies, policies, and practices designed to protect the integrity, confidentiality, and availability of systems and data. The goal is to block potential threats before they can infiltrate and disrupt network operations.
Effective network security requires a multi-layered approach, addressing both external and internal vulnerabilities. Measures range from basic defenses, such as firewalls, to advanced techniques like encryption and intrusion detection systems, all working together to form a secure environment.
By focusing on key aspects such as access control, data encryption, and monitoring, organizations can reduce the risk of malicious attacks and ensure their systems remain secure against evolving threats.
Common Network Devices and Their Functions
In a network, various devices work together to enable communication, data transfer, and overall system management. Each device serves a specific function that contributes to the smooth operation of the network infrastructure.
Network devices can range from simple connectors to advanced systems designed to manage traffic, secure data, and optimize performance. Understanding the role of these devices is essential for configuring and maintaining a network that is both efficient and secure.
Some of the most commonly used devices in a network include:
- Router: A router directs data packets between different networks, ensuring they reach their intended destinations based on IP addresses. It typically connects local networks to the internet.
- Switch: A switch connects devices within the same network, facilitating communication and efficient data transfer between them. It operates at a data link layer and reduces network traffic congestion.
- Firewall: A firewall acts as a barrier that monitors and controls incoming and outgoing network traffic, based on predetermined security rules, to protect against unauthorized access.
- Access Point: An access point enables wireless devices to connect to a wired network, extending network reach and supporting mobility within the coverage area.
- Modem: A modem modulates and demodulates signals for data transmission over communication lines, enabling connectivity to the internet over phone lines or cable systems.
Each device plays a crucial role in ensuring reliable network operation, and proper configuration of these devices is key to maintaining performance and security across the network.
OSI Model Layers and Their Roles
The OSI model is a conceptual framework that defines how different network protocols interact and communicate within a network. It breaks down the complex task of data transmission into manageable layers, each responsible for specific functions that contribute to the overall operation of the network.
There are seven layers in the OSI model, and each plays a critical role in ensuring seamless data communication between devices. Understanding the responsibilities of each layer helps in troubleshooting and optimizing network performance.
Here is a breakdown of the seven layers of the OSI model:
- Layer 1: Physical Layer – This layer deals with the physical transmission of data over a network, including cables, switches, and electrical signals. It is responsible for transmitting raw bits across a physical medium.
- Layer 2: Data Link Layer – The data link layer handles error detection, flow control, and the reliable transmission of data frames between devices. It ensures that data is transferred without errors between directly connected devices.
- Layer 3: Network Layer – This layer is responsible for routing data packets across multiple networks. It defines the addressing scheme and uses protocols such as IP to determine the best path for data delivery.
- Layer 4: Transport Layer – The transport layer ensures reliable data transfer by managing end-to-end communication. It controls data flow, error correction, and retransmission of lost data using protocols like TCP and UDP.
- Layer 5: Session Layer – The session layer establishes, manages, and terminates communication sessions between devices. It ensures that data is properly synchronized and organized during transmission.
- Layer 6: Presentation Layer – This layer is responsible for translating data into a format that the application layer can understand. It handles encryption, compression, and data translation to ensure compatibility between different systems.
- Layer 7: Application Layer – The application layer is the topmost layer and interacts directly with end-user applications. It provides network services such as email, file transfer, and web browsing, facilitating communication between programs and the network.
Each layer in the OSI model serves a distinct purpose, and together they form a foundation for how networks function. Understanding these layers is essential for anyone working with networking technologies, as it helps in diagnosing issues and designing effective network systems.
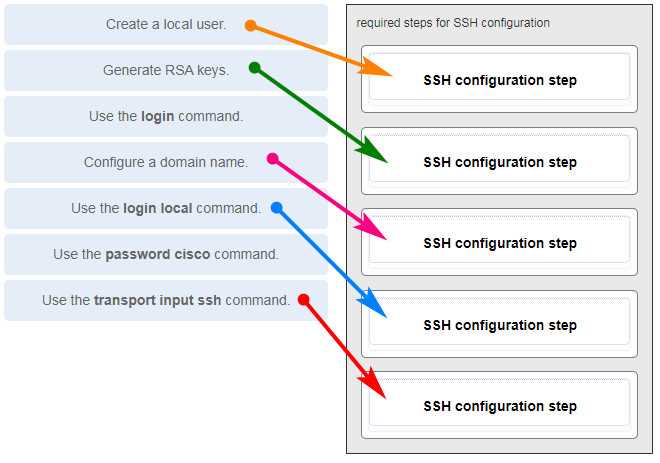
Configuring and Managing Cisco Devices
Setting up and maintaining network devices is a crucial skill in network management. These devices, often used in large and complex networks, require precise configuration to ensure optimal performance and security. Proper management involves configuring their settings, monitoring performance, and troubleshooting any issues that arise during operation.
When working with Cisco equipment, it is essential to understand the core concepts of device configuration, including setting up IP addresses, routing protocols, and security features. Additionally, managing these devices involves regular monitoring, updates, and resolving network-related issues to maintain a smooth, uninterrupted flow of data.
Here are some key steps involved in configuring and managing Cisco devices:
| Step | Description |
|---|---|
| 1. Accessing the Device | Use a console cable or remote connection method to access the Cisco device, typically through SSH or a direct serial connection. |
| 2. Initial Configuration | Configure basic settings such as hostname, IP addresses, and interfaces. Set up routing protocols and VLANs if necessary. |
| 3. Secure Configuration | Implement security measures like setting passwords, enabling SSH for secure remote access, and configuring access control lists (ACLs). |
| 4. Monitoring and Maintenance | Regularly monitor device performance using command-line tools or network management software. Perform routine checks for software updates and security patches. |
| 5. Troubleshooting | Use diagnostic commands to identify and resolve issues such as network connectivity problems or hardware malfunctions. |
By following these steps, administrators can ensure that their Cisco devices are properly configured and managed, keeping networks running smoothly and securely. The configuration process may vary depending on the device model and the specific network requirements, but the principles remain the same.
Basic Troubleshooting Techniques for Networks
Network issues can disrupt communication and hinder productivity, making troubleshooting an essential skill for any network administrator. Identifying the root cause of problems is the first step in resolving connectivity or performance issues effectively. A systematic approach is necessary to diagnose and address various network-related problems quickly.
The following steps are common practices used to troubleshoot network issues:
Step 1: Verify Physical Connections

Before diving into complex troubleshooting, ensure that all physical connections are properly established. Check cables, network ports, and ensure devices are powered on. Loose or disconnected cables are often the simplest yet most overlooked issue.
Step 2: Use Diagnostic Tools
There are various built-in diagnostic tools available to help network administrators assess the health of their networks. Tools such as ping, traceroute, and ipconfig can help determine whether devices are properly connected and whether packets are being transmitted correctly.
By following these techniques, you can begin to identify common network issues and apply the right solutions efficiently. Remember, troubleshooting is a process that requires patience and a methodical approach to isolate and resolve the problem.
Importance of Network Addressing Systems
In any communication system, the ability to uniquely identify and locate devices is essential. Network addressing systems are crucial in ensuring that data can be correctly routed between devices within a network and across the internet. Properly assigning and managing these addresses is key to maintaining seamless communication, security, and scalability.
Addressing systems, such as IP addressing, serve as the foundation for organizing networks and ensuring that each device has a unique identifier. These systems help networks function efficiently by enabling devices to send and receive information to the correct destinations. Without a robust addressing system, data would struggle to navigate through the complex maze of interconnected networks.
Understanding and implementing network addressing protocols, including the allocation of public and private addresses, subnetting, and managing address spaces, is essential for maintaining network performance, security, and growth. It allows network administrators to properly segment networks, control traffic, and ensure that each device can reliably communicate with others.
Wireless Networking Basics and Protocols
Wireless networking allows devices to connect and communicate without the need for physical cables, providing flexibility and mobility. This form of connectivity is essential in modern communication, enabling users to access the internet, share resources, and transfer data seamlessly. Wireless networks have become a fundamental aspect of both personal and business environments, offering convenience and scalability.
At the core of wireless communication are the various protocols that govern how data is transmitted and received. These protocols define the rules for data exchange, security measures, and how devices authenticate and interact within a network. Common wireless protocols include Wi-Fi, which operates primarily in home and office networks, and Bluetooth, used for short-range communication between devices.
Understanding the basic principles of wireless technology is crucial for setting up and maintaining secure and efficient networks. This includes choosing the right protocol for the right environment, ensuring optimal signal strength, and safeguarding against potential interference or security breaches. Wireless protocols are continuously evolving to support faster speeds, greater capacity, and more reliable connections.
How to Analyze Network Performance
Network performance analysis is essential for identifying issues that can affect the efficiency and speed of data transmission across a network. It involves measuring key parameters such as speed, latency, packet loss, and throughput to assess whether the network is functioning optimally. By understanding these metrics, network administrators can take appropriate actions to optimize performance and address any underlying problems.
Key Metrics to Measure
- Speed: Refers to the rate at which data is transferred across the network. This is usually measured in Mbps or Gbps.
- Latency: The time it takes for data to travel from the source to the destination. Low latency is crucial for applications requiring real-time communication, such as video conferencing.
- Packet Loss: Occurs when packets of data are lost in transit. High packet loss can severely degrade network performance.
- Throughput: The actual amount of data successfully transferred over the network in a given period, which can be affected by congestion or hardware limitations.
Tools for Network Performance Analysis
- Ping: A basic tool used to measure latency and packet loss by sending ICMP echo requests between devices.
- Traceroute: This tool helps identify the path data takes across the network and can reveal bottlenecks or problematic links.
- Network Analyzers: Software like Wireshark captures and analyzes network traffic in detail, allowing deeper insights into packet flow and performance issues.
By continuously monitoring these metrics and using the appropriate tools, network performance can be assessed and optimized for better user experiences and efficient data transmission.
Understanding Network Topologies and Design
Network topology refers to the arrangement of various network components such as devices, connections, and links within a network. The design of a network topology directly influences its performance, scalability, and resilience. It plays a critical role in how data travels across the network and how efficiently different devices communicate with each other. Proper network design ensures that the infrastructure can handle current demands and scale for future needs, while also maintaining reliability and security.
There are several common network topologies, each suited for different requirements and organizational sizes. These topologies determine how data flows and how devices are connected, impacting network performance, cost, and complexity. Understanding these structures helps in selecting the appropriate design for specific use cases and operational needs.
In addition to topology, the overall network design must consider factors like redundancy, fault tolerance, security, and ease of maintenance. A well-designed network ensures minimal downtime, efficient resource allocation, and the ability to handle increased loads as the network grows.
Preparing for the Certification Exam
Successfully obtaining a networking certification requires a structured and focused approach. It involves mastering essential concepts, practical skills, and troubleshooting techniques to ensure a deep understanding of networking principles. Preparation for this certification exam involves studying a wide range of topics, including networking fundamentals, protocols, security measures, and device configuration. Proper preparation not only boosts confidence but also equips you with the expertise necessary for real-world networking tasks.
Study Plan and Resources
Creating a study plan is crucial for covering all necessary topics in a timely manner. Utilizing a variety of resources such as textbooks, online courses, and hands-on labs can provide both theoretical knowledge and practical experience. Simulation tools and practice exams are particularly useful for reinforcing learning and getting familiar with the exam format.
Hands-On Practice
Real-world experience is vital for mastering networking concepts. Setting up virtual labs or using physical devices allows you to apply what you’ve learned in a controlled environment. Working with routers, switches, and other network devices helps solidify your understanding of configuration, troubleshooting, and monitoring tasks.
Staying focused, reviewing key topics regularly, and practicing consistently are the keys to success in achieving certification.
Tips for Studying Module 1 Effectively
Mastering the first set of topics in any networking curriculum requires a strategic and organized approach. By focusing on key concepts, developing a study routine, and engaging in practical exercises, you can build a solid foundation that will support further learning. Proper preparation ensures you understand essential networking concepts, which will be crucial as you advance to more complex topics.
Develop a Structured Study Plan
A structured study plan is essential for tackling the material efficiently. Breaking down complex topics into smaller, manageable chunks can help maintain focus and improve retention. Set clear goals for each study session to track your progress.
- Prioritize foundational concepts such as IP addressing and network topologies.
- Allocate time for both theoretical understanding and hands-on practice.
- Review regularly to reinforce knowledge and prevent forgetting.
Utilize a Variety of Learning Resources
Using a range of resources enhances your learning experience and provides different perspectives on the same topics. Complement textbooks with video tutorials, interactive labs, and online forums to deepen your understanding.
- Explore simulation tools for hands-on configuration experience.
- Join study groups or online communities for discussions and knowledge sharing.
- Use practice tests to assess your understanding and identify weak areas.
By staying organized, using diverse resources, and maintaining consistent practice, you can effectively absorb the foundational concepts and prepare for more advanced networking topics.