
Networking plays a crucial role in modern communication, and understanding routing mechanisms is essential for building efficient and secure systems. In this section, we dive deep into the fundamentals and strategies that govern the movement of data across networks. Whether you are setting up small-scale configurations or optimizing complex infrastructures, grasping these concepts will provide you with the tools needed to succeed.
Routing protocols are the backbone of network communication, ensuring data reaches its intended destination through the most efficient path. Mastering these protocols requires not only theoretical knowledge but also practical skills in configuring and troubleshooting devices. Through careful study and hands-on practice, you will learn how to manage and optimize network routes effectively.
Understanding how to handle different routing methods can dramatically impact the performance and reliability of your network. This section will provide you with the insight and techniques to navigate through challenges, configure devices correctly, and enhance network efficiency. By the end, you will be well-equipped to handle real-world networking tasks with confidence.
CCNA 2 Chapter 9 Exam Overview
In this section, we will explore the key concepts and skills necessary to navigate through one of the most critical areas in networking. The focus is on understanding the configuration, troubleshooting, and optimization of routing protocols, which are essential for maintaining efficient communication across networks. A strong grasp of these topics is fundamental for anyone aiming to succeed in real-world networking tasks.
Routing Protocols and Their Importance

Routing protocols are essential for directing traffic through networks, ensuring that data reaches its correct destination through the most efficient route. Understanding the differences between dynamic and static routing, along with the application of various algorithms, will prepare you to configure devices and manage complex networking environments effectively.
Key Skills and Concepts Covered
This section provides the foundation for mastering the configuration of various network devices, from routers to switches. It includes key skills such as network addressing, routing protocols like OSPF and EIGRP, as well as troubleshooting common issues. The ability to optimize routing performance and handle network failures is crucial for maintaining smooth operations.
| Topic | Description |
|---|---|
| Routing Protocols | Learn how different protocols like OSPF and EIGRP operate and how to configure them. |
| Network Addressing | Understand IP addressing schemes, subnetting, and address allocation methods. |
| Configuration Management | Master the setup and configuration of routers and switches in diverse network scenarios. |
| Troubleshooting | Identify and resolve routing issues using diagnostic tools and techniques. |
Key Topics for Chapter 9 Exam
This section highlights the essential concepts and skills required to excel in one of the most significant areas of networking. It covers the configuration and management of routing protocols, network addressing, and troubleshooting techniques that are necessary for maintaining robust communication across networks. These key topics will form the foundation for handling complex networking tasks effectively.
Understanding how to implement various routing protocols, manage IP addressing schemes, and optimize network performance will equip you with the expertise needed to manage dynamic network environments. These topics not only test your technical knowledge but also your ability to solve practical networking challenges in real-world situations.
Becoming proficient in these areas ensures that you are well-prepared to configure, troubleshoot, and optimize networks, addressing potential issues swiftly and efficiently. Mastering these concepts is crucial for anyone looking to advance in the field of networking and take on more complex roles in the industry.
Understanding Routing Protocols in Detail
Routing protocols are essential components of any network, directing the flow of data across various paths to ensure it reaches its destination. By learning how these protocols operate, you gain the ability to manage and optimize the communication between network devices. This understanding is vital for configuring efficient, scalable, and reliable network systems.
Types of Routing Protocols
There are several routing protocols that perform specific functions within a network. These protocols vary based on their operation, the type of network they support, and how they handle route discovery. Below are the primary categories:
- Distance-Vector Protocols: These protocols use hop count as the metric to determine the best path. Examples include RIP (Routing Information Protocol).
- Link-State Protocols: These protocols use the state of links and the network topology to compute the best paths. OSPF (Open Shortest Path First) is a key example.
- Hybrid Protocols: These protocols combine features of both distance-vector and link-state protocols. EIGRP (Enhanced Interior Gateway Routing Protocol) is an example.
How Routing Protocols Work
Routing protocols function by exchanging information between devices in a network. This data helps devices maintain an up-to-date routing table, ensuring that packets are directed to their destination through the most efficient route. Here’s how the process generally works:
- Route Discovery: Devices learn about available paths and network topology through protocol exchanges.
- Routing Table Update: Devices update their routing tables based on the information received from other devices.
- Path Selection: Once the network devices have all the data, they select the most optimal path based on certain metrics (e.g., hop count, bandwidth, etc.).
- Route Maintenance: Routing tables are constantly updated to reflect any changes in the network topology, ensuring the routes remain accurate and efficient.
Mastering the details of these protocols allows network administrators to effectively configure and troubleshoot routes, ensuring the network functions smoothly and efficiently even in dynamic environments.
Importance of Subnetting for Networking
Subnetting is a fundamental concept that plays a crucial role in organizing and optimizing a network. By dividing a large network into smaller, more manageable sub-networks, administrators can improve performance, security, and network efficiency. This practice is essential for ensuring that the available IP address space is used effectively and that network traffic is handled more efficiently.
Efficient Use of IP Addresses: One of the main benefits of subnetting is the ability to maximize the use of available IP addresses. Without subnetting, networks may waste addresses, resulting in an inefficient allocation of resources. By carefully dividing address space into smaller segments, more devices can be connected without running into issues of IP address exhaustion.
Improved Network Performance: Subnetting also helps reduce network congestion by segmenting traffic into smaller, more manageable chunks. Smaller subnets reduce the size of broadcast domains, which limits unnecessary traffic and ensures that communication is faster and more reliable within each subnet.
Enhanced Security: Dividing a network into subnets can also enhance security by isolating different segments of the network. If one subnet experiences a security breach, the damage is often contained within that subnet, preventing the entire network from being compromised.
Facilitating Network Management: Subnetting simplifies the management of complex networks by allowing network administrators to apply different configurations, policies, and security measures to individual subnets. This flexibility enables better control over network traffic, access, and resources.
In summary, subnetting is essential for any network design, offering improved resource utilization, better performance, and increased security. Mastering this concept is crucial for anyone working with networks and helps ensure their smooth and efficient operation.
Configuring OSPF for CCNA 2 Exam
OSPF (Open Shortest Path First) is a dynamic routing protocol commonly used in large-scale networks. It is designed to efficiently manage routing information and ensure optimal data packet delivery. Configuring OSPF requires a clear understanding of how to implement the protocol and ensure it communicates properly between routers. In this section, we will go over the necessary configuration steps for implementing OSPF in a network setup.
Key Configuration Steps
The configuration process for OSPF involves a series of steps that enable routers to communicate with one another. Below is an overview of the general configuration process:
- Enable OSPF: First, activate OSPF on the router by accessing the global configuration mode and entering the OSPF process.
- Assign Router ID: Each router in the OSPF network needs a unique router ID (RID), which identifies the router within the OSPF domain.
- Configure OSPF Areas: OSPF works based on areas. Define areas to segment the network and enhance scalability and performance.
- Configure Networks: Specify the networks that will participate in OSPF by using network commands and associating them with their respective areas.
- Activate OSPF on Interfaces: Ensure OSPF is activated on the router interfaces that are connected to other routers or networks.
- Verify OSPF Configuration: After configuration, use show commands to verify that OSPF is operating correctly and that routers have established neighbor relationships.
OSPF Network Types
OSPF operates using different network types depending on the network’s topology and design. Each type has its specific configuration requirements. Understanding these types is essential for efficient OSPF operation:
| Network Type | Description |
|---|---|
| Broadcast | Used in Ethernet environments, where OSPF routers can automatically discover neighbors through multicast. |
| Non-Broadcast | Common in networks lacking multicast support, requiring manual configuration of neighbors. |
| Point-to-Point | Typically used for direct connections between two routers, such as serial links. |
| Point-to-Multipoint | Used when one router is connected to multiple remote routers over a non-broadcast network. |
By understanding the configuration process and network types, network administrators can effectively implement OSPF in their environments. Proper OSPF configuration ensures the network operates efficiently, with routers exchanging the correct routing information in a scalable manner.
How to Troubleshoot Routing Issues
When dealing with network issues, troubleshooting routing problems can be one of the most challenging tasks. Routing issues can cause disruptions in network traffic and prevent devices from communicating with one another. Identifying the source of the problem requires a systematic approach, analyzing various factors that might be affecting the routing process. Here, we will explore the steps involved in diagnosing and resolving routing issues efficiently.
Common Routing Problems
Before diving into the troubleshooting process, it’s important to recognize the typical issues that can arise in routing:
- Routing Loops: These occur when a route is continuously passed between routers, resulting in an endless cycle that can degrade network performance.
- Incorrect Routing Table Entries: Misconfigured routes or missing entries in the routing table can prevent proper data flow.
- Network Configuration Mismatches: Discrepancies in network configurations across routers, such as incorrect subnet masks or IP addresses, can lead to communication failures.
- Neighbor Relationship Failures: A router failing to form or maintain neighbor relationships with other routers can stop routing updates from being exchanged.
Troubleshooting Steps
To resolve routing issues effectively, follow a structured approach to isolate and fix the problem:
- Check the Routing Table: Start by reviewing the routing table on each router. Verify that the correct routes are present and that they are properly configured.
- Verify Connectivity: Use tools like ping and traceroute to test connectivity between devices. This helps identify whether the issue is with the route itself or the physical connection.
- Examine Routing Protocols: Ensure that the routing protocol is correctly configured on all routers and that there are no misconfigurations or mismatched settings, such as wrong network statements or AS numbers.
- Check for Access Control Lists (ACLs): Inspect any ACLs that may be blocking traffic. Ensure that the ACLs are not inadvertently filtering legitimate routes or traffic.
- Monitor Routing Updates: Use commands like show ip ospf neighbor or show ip route to view routing updates and check for any errors in the process.
- Review Physical Layer: Examine the physical connections, ensuring cables, switches, and routers are functioning properly. Faulty hardware can sometimes lead to routing problems.
By methodically following these steps, network administrators can troubleshoot and resolve routing issues, ensuring smooth and efficient communication across the network.
Best Practices for Routing Table Management
Efficient routing table management is essential for maintaining optimal network performance. The routing table plays a critical role in directing traffic across the network, ensuring data reaches its destination accurately and efficiently. Proper management helps to minimize issues like incorrect routing paths, network congestion, and unnecessary complexity. This section outlines key practices to manage routing tables effectively, ensuring smooth communication within the network.
One of the fundamental aspects of routing table management is keeping it clean and organized. Over time, as routes change or devices are added or removed, routing tables can become cluttered, which can lead to inefficiencies. Properly managing the table involves monitoring and pruning outdated entries and ensuring that only necessary and valid routes are maintained.
Implementing Route Summarization
Route summarization is an important technique for reducing the size and complexity of routing tables. By summarizing a group of IP addresses into a single route, the table size can be reduced, improving routing efficiency and reducing CPU load on routers. This technique is particularly useful in large networks, where numerous subnets can be grouped into a single summary address.
Using Static Routes Where Appropriate
Static routes are manually configured paths that are particularly useful for directing traffic to specific destinations. They can help to improve routing efficiency by providing direct routes for critical traffic. However, they should be used carefully, as they require regular updates and maintenance to ensure they remain accurate as the network changes.
Monitoring Routing Protocols
Active monitoring of routing protocols is essential for ensuring the accuracy of routing tables. Regularly reviewing protocol configurations, such as those for OSPF, EIGRP, or RIP, helps ensure that updates are propagated correctly and that routing paths remain optimal. Troubleshooting and adjusting the configuration of routing protocols can prevent issues like routing loops or inefficient path selection.
Minimizing Routing Table Size
Routing tables can become bloated over time, especially in large-scale networks. To reduce the size of the routing table, administrators should implement filtering and route aggregation, ensuring that only essential routes are included. This reduces memory usage and enhances routing performance across the network.
By following these best practices, network administrators can effectively manage routing tables, leading to a more efficient, secure, and reliable network infrastructure.
Exploring Network Address Translation Concepts
Network Address Translation (NAT) is a technique that allows network devices to communicate with each other across different network environments while using a small number of public IP addresses. This process modifies the IP address information in the packet headers, which enables private networks to interact with the public internet. By managing the translation of IP addresses, NAT not only helps conserve the limited number of available public addresses but also improves security and privacy for devices within a local network.
Types of Network Address Translation
There are various types of Network Address Translation, each serving distinct purposes in managing IP addresses effectively. Below are the three main types:
- Static NAT: This type of NAT creates a one-to-one mapping between a private IP address and a public IP address. It is often used when a device inside a private network, such as a web server, needs to be accessed from the outside world.
- Dynamic NAT: Unlike static NAT, dynamic NAT uses a pool of public IP addresses and dynamically assigns them to private addresses when needed. This method is beneficial when the number of private IP addresses exceeds the number of available public addresses.
- Port Address Translation (PAT): Often referred to as “overloading,” PAT allows multiple private IP addresses to share a single public IP address. It differentiates the connections using unique port numbers, making it especially useful for smaller networks or home routers.
Advantages of Using NAT
There are several advantages to using Network Address Translation in network management:
- Address Conservation: By enabling multiple devices within a private network to share a single public IP address, NAT helps conserve the limited availability of public IP addresses.
- Enhanced Security: NAT provides an additional layer of security by hiding the internal IP addresses of network devices, making it more difficult for external attackers to access them directly.
- Flexibility: NAT allows changes to the internal network without affecting external communications. This is particularly useful when modifying or restructuring networks.
Despite the numerous benefits, NAT also introduces some challenges, especially with certain protocols that require end-to-end communication. However, it remains an essential tool for modern networks, offering both efficiency and security in IP address management.
Example of NAT Configuration
| Type of NAT | Configuration Example |
|---|---|
| Static NAT | Maps one private IP address (e.g., 192.168.1.10) to one public IP address (e.g., 203.0.113.5). |
| Dynamic NAT | Maps a range of private IP addresses to a pool of public IP addresses as needed. |
| Port Address Translation (PAT) | Multiple internal devices are mapped to a single public IP address, using different ports for each device. |
Understanding the different types of NAT and their configurations is crucial for network administrators when deciding how to set up their networks efficiently while ensuring security and functionality.
Examining IP Addressing and Addressing Schemes
IP addressing is a fundamental aspect of network management that enables devices to communicate over a network. By assigning unique identifiers to each device, an IP address scheme helps organize and route traffic across complex network infrastructures. Understanding different addressing strategies and their applications is key to designing efficient and scalable networks. This section delves into the structure of IP addresses, addressing schemes, and the principles behind subnetting, which allows networks to be divided into smaller, manageable segments.
Types of IP Addressing
IP addresses come in various types, each serving specific roles within a network. The two main categories are:
- IPv4 (Internet Protocol Version 4): This is the most widely used addressing scheme, using a 32-bit address space, represented in four octets. IPv4 provides over 4 billion unique addresses, but the rapid growth of the internet has led to concerns about address exhaustion.
- IPv6 (Internet Protocol Version 6): With a 128-bit address space, IPv6 addresses the limitations of IPv4 by offering an almost infinite number of addresses. It uses hexadecimal notation and is designed to accommodate the increasing number of devices on the internet.
Addressing Schemes and Subnetting
Addressing schemes are designed to organize and allocate IP addresses in a way that optimizes network performance and security. Subnetting, a process that divides an IP network into smaller subnetworks, plays a key role in this. Here are some common approaches:
- Classful Addressing: The traditional method of IP address classification divides the address space into five classes (A, B, C, D, E). Class A, B, and C are used for regular devices, while D and E are reserved for multicast and experimental purposes.
- Classless Inter-Domain Routing (CIDR): CIDR allows for more flexible address allocation by eliminating the rigid structure of classful addressing. It uses a notation that specifies the network prefix and the subnet mask, making it more efficient for allocating IP addresses.
Subnetting allows network administrators to create subnets within a network, improving performance by reducing congestion and isolating broadcast domains. The process involves borrowing bits from the host portion of the IP address to create a larger network prefix. This technique is essential for managing address space and ensuring efficient routing in larger networks.
Both IPv4 and IPv6 addressing schemes and subnetting techniques are essential skills for managing networks. By understanding how to allocate, subnet, and route IP addresses, network administrators can optimize the functionality and scalability of their networks.
Evaluating Routing Protocol Performance
Routing protocols are critical for ensuring efficient data transmission across networks. They determine how routers exchange routing information and select the best paths for data packets. Evaluating the performance of these protocols is essential to ensure they operate optimally in varying network conditions. Key factors such as convergence time, scalability, resource utilization, and fault tolerance must be assessed when determining the suitability of a routing protocol for a specific network.
Key Metrics for Routing Protocol Evaluation
Several metrics are used to evaluate the effectiveness and efficiency of routing protocols. Understanding these metrics helps network administrators choose the right protocol based on their specific network requirements.
- Convergence Time: The time it takes for all routers in the network to update their routing tables after a network change or failure. A protocol with fast convergence time ensures minimal disruption in network traffic.
- Scalability: The ability of a routing protocol to handle an increasing number of routers or devices in the network without significant performance degradation. Scalable protocols are essential for large networks.
- Resource Utilization: This refers to the amount of CPU, memory, and bandwidth consumed by the routing protocol. Efficient protocols use fewer resources, allowing the network to handle more traffic.
- Fault Tolerance and Redundancy: The ability of a protocol to maintain network connectivity despite link failures. Protocols with strong fault tolerance mechanisms can quickly adapt to changes, ensuring continuous service.
Comparing Routing Protocols
Different routing protocols offer varying levels of performance based on these metrics. Some of the most commonly evaluated protocols include:
- RIP (Routing Information Protocol): An older, distance-vector protocol that is simple but lacks scalability and fast convergence. It is best suited for small networks.
- OSPF (Open Shortest Path First): A link-state protocol that provides faster convergence and better scalability than RIP. It is widely used in medium to large enterprise networks.
- EIGRP (Enhanced Interior Gateway Routing Protocol): A hybrid protocol that combines the best features of distance-vector and link-state protocols. It offers fast convergence and is efficient in larger, more complex networks.
By analyzing these factors and comparing the performance of routing protocols, network administrators can ensure optimal configuration and performance for their network’s needs. A well-chosen routing protocol can enhance network stability, performance, and overall efficiency.
Configuring EIGRP in Network Environments
Efficient routing within a network depends heavily on selecting the right protocol to dynamically determine the best paths for data transmission. Enhanced Interior Gateway Routing Protocol (EIGRP) is an advanced routing protocol that provides quick convergence and scalability, making it an excellent choice for large and complex networks. Proper configuration of EIGRP ensures stable and optimized routing by adjusting settings that impact network performance and reliability.
Basic EIGRP Configuration Steps
To configure EIGRP, administrators follow a series of steps to enable the protocol and define the network parameters. These steps include activating the routing protocol, identifying participating networks, and adjusting essential settings to optimize performance.
- Enable EIGRP: Begin by entering the router configuration mode and activating EIGRP with the
router eigrp [AS-number]command, where the AS number is the identifier for the routing process. - Specify Networks: Define which IP networks should participate in the EIGRP process using the
network [network-address]command. This step tells the router which interfaces should be included in the EIGRP routing updates. - Set EIGRP Metrics: Adjust the EIGRP metric values such as bandwidth, delay, and reliability to influence the route selection process. Fine-tuning these metrics can enhance routing decisions based on specific network needs.
- Adjust Timers: Modify EIGRP hello and hold timers to control how often the router sends hello packets and maintains neighbor relationships. This can optimize convergence time and overall network stability.
Advanced EIGRP Configuration Features
Once basic EIGRP configuration is in place, additional features can be implemented to improve network performance, scalability, and security.
- Passive Interfaces: Configure passive interfaces to prevent EIGRP from sending hello packets on unused interfaces, reducing unnecessary network traffic.
- Route Summarization: Aggregate multiple subnet routes into a single summarized route to minimize the size of the routing table and enhance network efficiency.
- Load Balancing: EIGRP supports equal-cost load balancing, allowing the use of multiple paths simultaneously if they have the same metric, which enhances redundancy and load distribution across the network.
- Authentication: Secure EIGRP communications by configuring authentication on routers, ensuring that routing updates are exchanged only between trusted devices.
By following these configuration steps and implementing advanced features, administrators can ensure a robust, scalable, and secure routing environment within their network infrastructure, enhancing overall performance and stability.
Practice Scenarios for Exam Preparation
Preparing for a networking certification requires hands-on experience with real-world scenarios that test both theoretical knowledge and practical skills. Practice scenarios help reinforce concepts, identify areas that need improvement, and build confidence in troubleshooting and configuration tasks. These simulations offer an opportunity to solve problems that mimic the challenges faced in live environments, enabling candidates to apply what they’ve learned in a controlled setting.
Key Practice Areas to Focus On
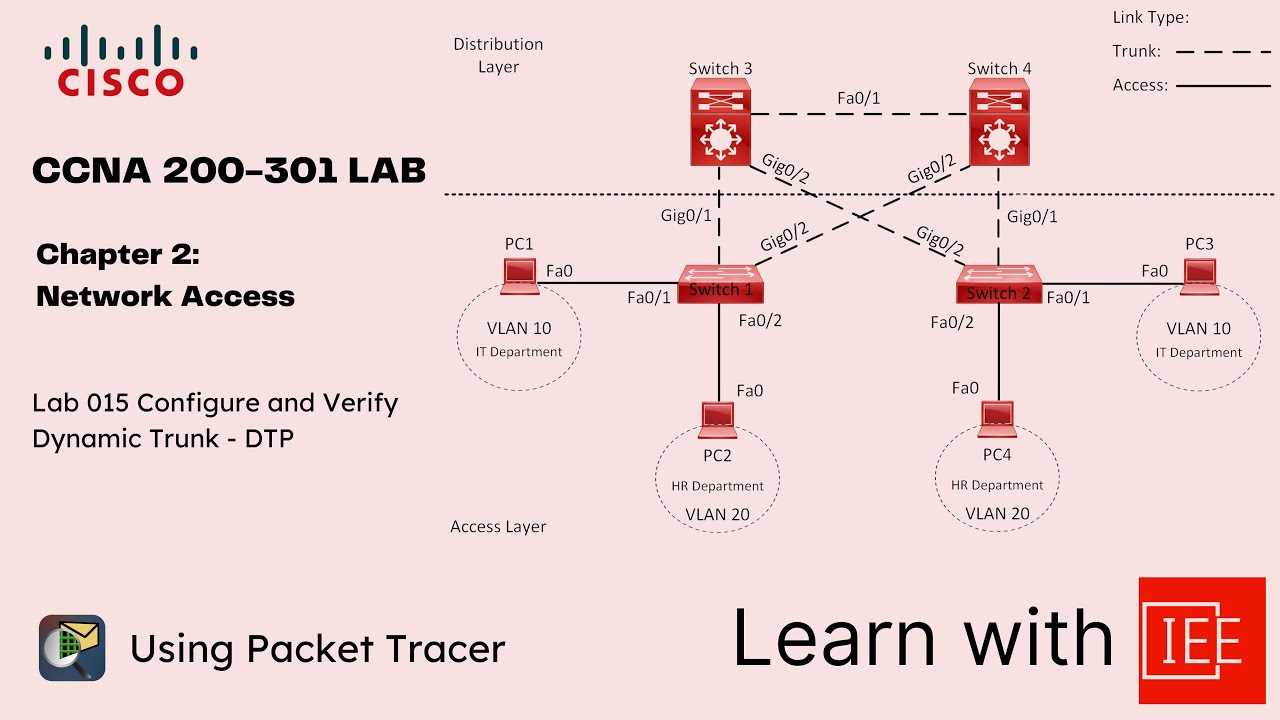
While studying for the certification, focusing on the following practice areas will ensure you’re well-prepared for the challenges that may appear in the test or real-world applications:
- IP Addressing and Subnetting: Practice configuring and troubleshooting IP addresses and subnet masks. Exercises should involve creating subnetting schemes, calculating address ranges, and assigning IP addresses within a network.
- Routing Protocols Configuration: Simulate scenarios involving dynamic routing protocols such as RIP, OSPF, and EIGRP. These exercises should cover setting up, optimizing, and troubleshooting routing configurations, as well as analyzing routing tables and network performance.
- Network Security: Practice configuring security features such as access control lists (ACLs), firewall rules, and VPN setups. This helps ensure that a network can be safeguarded from external and internal threats.
- VLAN Configuration and Management: Work on creating and managing VLANs, configuring trunking, and ensuring proper inter-VLAN routing. Understanding how to segment networks efficiently is critical for network performance and security.
- Wireless Network Setup: Test wireless configurations, including the creation of SSIDs, security protocols, and troubleshooting common issues like signal interference and coverage gaps.
Simulating Troubleshooting Scenarios
In addition to configuration tasks, practicing troubleshooting is essential for success. Common network problems, such as routing issues, IP address conflicts, and connectivity problems, should be simulated to develop a systematic approach to solving real-world problems. For example:
- Routing Loops: Practice identifying and resolving routing loops using tools like traceroute and examining routing tables.
- Interface Issues: Work on detecting issues related to interface configurations, such as incorrect IP assignments or missing routes.
- Latency Problems: Simulate high-latency scenarios and practice identifying bottlenecks in the network, such as bandwidth limitations or misconfigured equipment.
By regularly practicing these types of scenarios, candidates will gain a deeper understanding of network behaviors and be well-prepared for any challenges that arise in real-world network environments.
Importance of Router Configuration in Networking
Router configuration plays a critical role in the functionality and efficiency of modern networks. A router serves as a central device that forwards data packets between different network segments, ensuring effective communication across diverse devices and systems. Properly configuring routers ensures optimal performance, security, and scalability, enabling networks to handle increasing data traffic while maintaining stability and security. Without correct configurations, routers can become sources of network issues such as connectivity problems, data loss, or security vulnerabilities.
One of the key benefits of router configuration is the ability to implement network routing protocols, which allow routers to make intelligent decisions about the best paths for data packets. These protocols can adapt to network changes, such as the addition of new devices or the failure of network links, ensuring seamless communication across different network segments. Additionally, routers can be configured with various features like firewall settings, IP address allocation, and Quality of Service (QoS) settings to optimize network traffic and enhance security.
Effective router management is essential for the overall health of a network. Network administrators must be proficient in configuring routers for tasks such as:
- Routing Protocol Configuration: Ensuring that routing protocols like OSPF, EIGRP, and RIP are set up correctly for optimal path selection and dynamic routing.
- Network Security: Configuring access control lists (ACLs), VPNs, and firewall rules to protect the network from unauthorized access and potential attacks.
- Traffic Management: Implementing QoS policies to prioritize critical traffic and ensure smooth data delivery, especially in networks with limited bandwidth.
- IP Addressing: Properly allocating IP addresses and managing subnets to facilitate efficient data routing and minimize address conflicts.
Overall, the proper configuration of routers is a fundamental element of any network’s success, as it directly influences network performance, security, and scalability.
Common Errors in Routing Configuration
Incorrect routing configuration can lead to significant network issues, including connectivity problems, inefficient data transfer, and security vulnerabilities. These mistakes often occur during setup or modification of routing protocols, which can prevent devices from communicating effectively across different network segments. Identifying and correcting these errors is essential for maintaining network performance and reliability.
1. Incorrect IP Addressing and Subnetting
One of the most frequent errors in routing configuration is improper IP addressing or subnetting. When network administrators mistakenly configure incorrect IP addresses or fail to properly divide the network into subnets, routers may not be able to forward traffic correctly. This can lead to packet loss, communication delays, or complete network isolation between devices.
2. Routing Loop Issues
Routing loops occur when data packets endlessly circulate between routers without reaching their destination. These loops typically arise when routing protocols are misconfigured or when routers are given contradictory routing information. The presence of routing loops can severely degrade network performance and cause traffic congestion.
3. Mismatched Routing Protocols
Another common mistake involves mismatched or incompatible routing protocols between routers. For example, if one router is configured to use OSPF while another is set to use RIP, the two routers will not be able to exchange routing information properly. Ensuring that all routers in the network use the same or compatible routing protocols is critical for seamless communication.
4. Missing or Incorrect Routing Entries
In some cases, routers may be missing necessary routing entries, or the entries themselves may be configured incorrectly. This can lead to incomplete or faulty route tables, causing traffic to be misrouted or dropped. Regularly reviewing and updating routing tables is essential to avoid such errors.
5. Misconfigured Access Control Lists (ACLs)
Access control lists are often used to filter network traffic, but misconfigured ACLs can inadvertently block legitimate traffic or allow unauthorized traffic. When configuring ACLs, it is important to ensure that the correct rules are in place to prevent security risks while allowing necessary data flows.
To prevent these errors, network administrators should regularly verify routing configurations, conduct thorough testing, and ensure proper training in routing protocol management. Addressing these issues early helps maintain a stable and efficient network environment.
Optimizing Network Performance for Routing
Ensuring optimal network performance requires careful consideration of routing processes and configurations. By improving how data is forwarded across the network, organizations can reduce latency, enhance throughput, and provide a more reliable service to users. Achieving optimal routing performance involves various strategies, including fine-tuning routing protocols, adjusting routing metrics, and minimizing network congestion.
1. Fine-Tuning Routing Protocols
To optimize routing performance, it’s important to configure routing protocols efficiently. This includes adjusting the parameters of protocols such as OSPF or EIGRP to suit the network’s specific needs. For example, modifying hello and dead intervals can help reduce the frequency of updates, thus reducing unnecessary overhead. Similarly, adjusting the cost or metric values used by a protocol ensures that traffic is routed along the most efficient path.
2. Minimizing Network Congestion
Network congestion occurs when too much traffic is routed through a particular link, slowing down the entire network. To alleviate congestion, traffic engineering techniques can be applied, such as load balancing and route redistribution. By distributing traffic evenly across multiple paths, administrators can ensure better utilization of available bandwidth and prevent bottlenecks that negatively impact performance.
In addition, implementing Quality of Service (QoS) can help prioritize critical traffic and allocate bandwidth where it’s needed most. This ensures that time-sensitive data, such as voice or video traffic, gets through the network with minimal delay, even during periods of high load.
Regular network monitoring and performance analysis are essential to detect potential issues and optimize routing configurations. By using tools like traffic analyzers and route map verification, network administrators can identify inefficiencies and make necessary adjustments to keep the network running smoothly.
Advanced Topics in Routing
Advanced routing techniques are essential for network administrators looking to optimize performance and maintain scalability in large or complex networks. These methods involve deeper knowledge of routing protocols, policies, and strategies to address challenges such as redundancy, security, and efficient routing path selection. In this section, we explore key advanced topics that are crucial for managing dynamic and high-performance networks.
1. Route Redistribution
Route redistribution allows the integration of different routing protocols within the same network. By doing so, it ensures seamless communication between devices running different routing methods, such as OSPF and EIGRP. However, this process requires careful configuration to avoid routing loops and ensure that optimal paths are selected.
- Types of Route Redistribution: Redistribution can be either static or dynamic. Static redistribution is manually configured, while dynamic redistribution uses automatic routing updates.
- Managing Route Loops: Careful configuration of administrative distances and route filtering can prevent unwanted routing loops during redistribution.
- Using Route Maps: Route maps can be employed to control which routes are redistributed, providing finer control over routing decisions.
2. Policy-Based Routing (PBR)
Policy-Based Routing (PBR) is a technique that enables administrators to make routing decisions based on policies other than the destination address. This method offers greater flexibility in directing traffic, especially in cases where certain traffic types or applications need prioritized routing paths.
- Traffic Classification: PBR allows administrators to classify traffic based on various factors, such as source IP address, protocol type, or application.
- Routing Decisions: Once traffic is classified, PBR can be used to send that traffic along a specific path based on defined policies, improving both performance and security.
These advanced routing strategies help optimize networks by controlling traffic flow, enhancing scalability, and addressing network design challenges effectively. Proper implementation of these techniques ensures that large-scale networks function efficiently and securely, providing optimal user experiences even under heavy traffic conditions.
Final Tips for Success in the Exam

Achieving success in any certification assessment requires thorough preparation, strategic planning, and confidence in applying knowledge effectively. Whether you’re testing your understanding of networking concepts or troubleshooting routing issues, following a well-structured study plan and focusing on key topics will increase your chances of performing well. In this section, we highlight critical tips to help you navigate the assessment with ease and precision.
1. Master Core Concepts
Before tackling the practical portions of the exam, ensure you have a deep understanding of core networking principles. Key concepts often form the foundation for more complex scenarios and configurations. Focus on the following:
- Subnetting: Be comfortable with subnetting calculations and how they apply to IP addressing.
- Routing Protocols: Gain a solid grasp of how protocols like OSPF, EIGRP, and RIP work, and when to use each.
- IP Addressing: Understand different addressing schemes and how to manage IP address assignment in networks.
2. Practice with Real-Life Scenarios
Hands-on practice is essential for building confidence and refining your skills. Set up a lab environment using routers and switches to practice different configurations. Focus on:
- Network Configuration: Simulate real-world network designs and configure routers and switches accordingly.
- Troubleshooting: Practice diagnosing issues using command-line tools like ping, traceroute, and show commands.
- Routing Protocol Setup: Configure and test routing protocols in various network topologies to understand their behavior in different conditions.
3. Time Management During the Test
Efficient time management can be the key to success. During the assessment, make sure you allocate time wisely:
- Read Questions Carefully: Understand each question thoroughly before answering to avoid unnecessary mistakes.
- Prioritize Tasks: Address the easier tasks first, leaving more time for the challenging ones.
- Stay Calm: Keep a clear mind and avoid rushing through questions; staying focused will help you finish on time.
By mastering the essential concepts, practicing with realistic scenarios, and managing your time effectively, you’ll be better prepared to succeed. The key to performing well is confidence in your abilities and a calm, focused approach during the test.