
In today’s interconnected world, understanding the principles behind protecting digital assets is more critical than ever. Preparing effectively for assessments on this subject helps build a solid foundation for safeguarding systems and data.
This guide aims to provide a clear and practical overview of essential strategies and techniques. From exploring potential vulnerabilities to reviewing key prevention measures, each section is designed to deepen your understanding and enhance your preparedness.
By focusing on proven methods and real-world applications, you’ll gain insights that not only aid in achieving success during evaluations but also empower you to apply these concepts in practical scenarios. Let’s dive into the essentials and build a strong knowledge base together.
Understanding Key Concepts in Cybersecurity
Grasping the essential ideas behind protecting digital environments is crucial in navigating today’s technological landscape. These core principles form the backbone of maintaining resilience against potential threats to digital assets.
At the heart of these concepts lies the ability to identify weaknesses and implement protective measures. This includes strategies such as controlling access to systems, encrypting sensitive data, and developing frameworks to detect unusual activities effectively.
By mastering these foundational ideas, you not only enhance your theoretical understanding but also gain the practical skills necessary for tackling challenges in diverse digital ecosystems. Recognizing and applying these key concepts ensures a robust approach to maintaining digital integrity.
Preparing Effectively for Security Exams
Achieving success in evaluations focused on digital defense requires a strategic approach to studying. Understanding the core themes and prioritizing efficient learning techniques can significantly enhance readiness.
Creating a Comprehensive Study Plan
Developing a structured schedule is essential for thorough preparation. Allocate specific time for each topic, ensuring balanced coverage of all critical areas. Include time for reviewing materials, practicing applications, and revisiting challenging concepts.
- Divide topics into manageable sections.
- Set realistic goals for daily or weekly progress.
- Incorporate breaks to maintain focus and retention.
Using Diverse Learning Resources
Relying on a variety of materials can deepen understanding and provide multiple perspectives on key themes. Consider supplementing traditional textbooks with other formats for a well-rounded grasp of the subject.
- Review online tutorials and guides for detailed explanations.
- Participate in forums or discussion groups to clarify doubts.
- Practice using mock assessments to simulate real scenarios.
By combining a systematic approach with diverse resources, you can build the confidence and knowledge needed to excel in any evaluation on digital defense topics.
Common Threats and How to Address Them
Understanding potential risks in the digital realm is essential for creating effective strategies to mitigate them. Identifying common challenges and learning how to handle them can significantly reduce vulnerabilities and enhance overall protection.
Types of Risks in Digital Environments
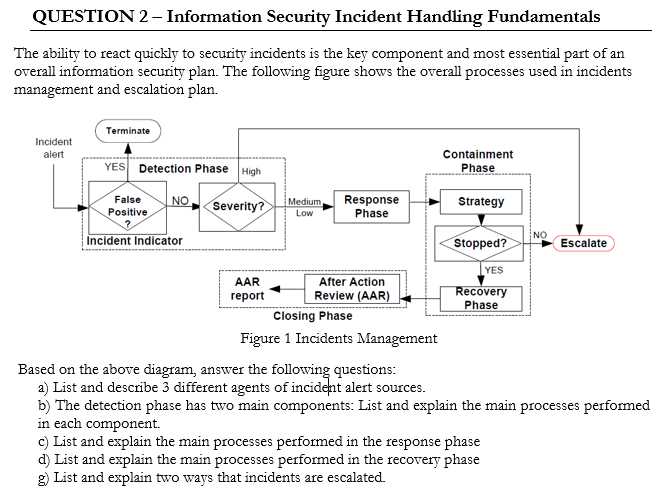
Various challenges arise in modern systems, ranging from unauthorized access to malicious software. Each type of risk requires tailored measures to manage and prevent its impact.
| Threat Type | Description | Preventive Measures |
|---|---|---|
| Phishing | Deceptive attempts to steal sensitive details through fake communications. | Avoid clicking on suspicious links and verify sender authenticity. |
| Malware | Harmful software designed to damage or disrupt systems. | Install and update robust antivirus programs regularly. |
| Unauthorized Access | Gaining entry into systems without proper credentials. | Use strong passwords and enable multi-factor authentication. |
| Data Breaches | Unauthorized exposure of sensitive information. | Encrypt data and limit access based on roles. |
Implementing Practical Defense Strategies
Building a proactive approach to digital protection involves regular assessments and adopting advanced technologies. Frequent system updates, employee awareness training, and strong governance policies play crucial roles in minimizing risks.
By recognizing these common threats and applying the appropriate solutions, individuals and organizations can create a safer digital environment and reduce exposure to potential harm.
Network Security Basics for Beginners
Protecting interconnected systems requires understanding foundational principles. By learning how networks function and recognizing potential weaknesses, even beginners can contribute to maintaining a safer digital infrastructure.
Essential Components of a Protected Network
Networks consist of multiple devices and systems that require safeguarding. Each component plays a critical role, and addressing vulnerabilities at every level ensures comprehensive protection.
| Component | Purpose | Best Practices |
|---|---|---|
| Routers | Direct traffic between devices and external connections. | Change default credentials and enable firewall settings. |
| Switches | Connect multiple devices within a local network. | Segment networks and monitor device activity regularly. |
| Access Points | Provide wireless connectivity to devices. | Use strong encryption protocols and hidden network names. |
| Servers | Host data and applications for network users. | Ensure regular updates and restrict unauthorized access. |
Simple Practices to Reduce Risks
Beginners can follow straightforward steps to enhance the safety of networks. Regular updates, monitoring for unusual activities, and using tools like firewalls and antivirus software are effective starting points. Familiarity with these basics sets the stage for more advanced learning and implementation.
Building strong habits and focusing on core principles equips individuals to create safer environments for themselves and others. A clear understanding of these foundational concepts is the first step toward mastering advanced techniques in system protection.
Essential Tools for Data Protection
Preserving sensitive information requires using reliable resources to shield it from unauthorized access or damage. By leveraging advanced technologies and tools, individuals and organizations can maintain the integrity of their digital assets.
Several solutions are available to help ensure confidentiality and prevent potential risks. These tools address different aspects of protection, from access control to real-time monitoring, creating a comprehensive approach to safeguarding information.
Encryption software is one of the most effective methods, converting readable data into an unreadable format that only authorized users can access. Password managers provide secure storage for complex authentication keys, encouraging better practices in credential management. Firewalls serve as barriers, controlling and filtering traffic to block harmful activities.
Additionally, backup solutions ensure recovery in case of accidental loss or malicious attacks. Regularly creating copies of important files on secure servers or external devices helps mitigate the impact of unforeseen events.
Choosing the right combination of tools tailored to specific needs can significantly reduce vulnerabilities, offering peace of mind and robust safeguards for valuable digital information.
Best Practices for Online Safety
Ensuring a safe experience in the digital world involves adopting good habits and employing effective techniques to protect personal and sensitive data from potential threats. By following some simple yet essential practices, users can minimize risks and enjoy a safer online environment.
Strong Authentication Methods
One of the primary measures to enhance online safety is using strong, unique passwords for each account. Avoid reusing passwords across multiple platforms, as this increases vulnerability in case of a breach. Additionally, enable multi-factor authentication (MFA) whenever possible, adding an extra layer of protection by requiring more than just a password to gain access.
Regular Monitoring and Updates
Keeping software up-to-date is crucial to safeguarding against newly discovered vulnerabilities. Regularly updating operating systems, applications, and security software ensures that any patches or fixes are applied promptly. Furthermore, periodically reviewing account activity and settings can help detect any suspicious behavior early on.
Implementing these practices can greatly reduce the likelihood of falling victim to cyber threats. Being proactive and staying informed about the latest safety tips will enable users to navigate the digital landscape with confidence and security.
Differences Between Encryption Methods
Various techniques are available to protect sensitive data by converting it into an unreadable format. Understanding the differences between these methods is essential in choosing the best one for a given situation. Each encryption approach has its strengths and weaknesses, making it crucial to select the right method based on the level of protection required.
Symmetric vs Asymmetric Encryption
Two primary categories of encryption methods are symmetric and asymmetric encryption. Both aim to protect data, but they work differently.
- Symmetric Encryption: In this method, the same key is used to both encrypt and decrypt the data. It is faster and more efficient but requires careful management of the encryption key, as it must be kept secret. Popular algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
- Asymmetric Encryption: This method uses a pair of keys–one public and one private. The public key is used to encrypt data, while the private key decrypts it. Although it is slower, it offers higher levels of security, especially for communications and transactions. RSA and ECC (Elliptic Curve Cryptography) are widely used algorithms.
Key Differences to Consider
Choosing between these methods depends on factors like speed, resource requirements, and security needs. Symmetric encryption is typically used for encrypting large amounts of data due to its efficiency, while asymmetric encryption is commonly used for secure key exchange and digital signatures, where security is paramount.
In practice, both methods can be used together in hybrid systems, combining the strengths of each to optimize performance and protection. For example, asymmetric encryption can be used to securely exchange a symmetric key, which is then used to encrypt and decrypt the actual data.
Importance of Access Control Policies
Establishing guidelines to manage who can access certain resources within an organization is crucial in maintaining a well-structured and secure environment. Access control policies play a fundamental role in defining and enforcing limits on access, ensuring that only authorized individuals are granted permissions based on their roles and responsibilities.
Key Benefits of Implementing Access Control
Implementing effective access control measures offers numerous advantages, including protecting sensitive data and ensuring that the right people have the appropriate levels of access to necessary resources.
- Prevents Unauthorized Access: By enforcing clear rules about who can access what, it significantly reduces the chances of unauthorized users gaining access to critical systems or data.
- Reduces Risk of Data Breaches: Restricting access to sensitive data to only those who need it helps minimize the risk of data leaks or breaches, protecting the integrity and privacy of organizational assets.
- Enhances Compliance: Many industries are subject to regulatory requirements regarding data protection. Strong access control policies help meet these regulations and demonstrate a commitment to responsible data management.
Types of Access Control Models
Several access control models exist, each with different ways of managing user permissions. The most common models include:
- Discretionary Access Control (DAC): In this model, owners of resources have the authority to decide who can access their data. While flexible, it can be difficult to manage in large organizations.
- Mandatory Access Control (MAC): A stricter model where access to resources is determined by pre-defined policies, often used in highly regulated environments.
- Role-Based Access Control (RBAC): This model assigns access rights based on a user’s role within the organization, ensuring that individuals have access only to the resources necessary for their job functions.
By understanding and implementing the right access control policies, organizations can greatly enhance their ability to protect sensitive information, prevent unauthorized actions, and ensure overall operational integrity.
Analyzing Real-World Security Breaches
Understanding how real-world incidents occur is crucial for learning how to prevent future breaches. By examining high-profile cases, organizations can identify vulnerabilities in their systems and learn valuable lessons about the effectiveness of various protective measures. These incidents provide insight into how attackers exploit weaknesses and the steps that can be taken to mitigate such risks.
Case Study: Major Data Breach in 2017
One of the most notable incidents occurred in 2017, where a large corporation experienced a massive data breach. The attackers gained access to millions of customer records, including sensitive personal information. The breach occurred due to an unpatched vulnerability in the company’s system, which allowed unauthorized access. This breach was a wake-up call for the industry, highlighting the importance of regular software updates and security patches.
Lessons Learned from Real-World Incidents
Every security incident carries with it valuable lessons. Analyzing breaches allows for a deeper understanding of the risks involved and how to protect against similar threats in the future. Key takeaways include:
- Timely Patching and Updates: Many breaches happen due to known vulnerabilities in outdated systems. Regularly updating software can prevent attackers from exploiting these weaknesses.
- Employee Awareness: Human error remains one of the most common causes of breaches. Training staff to recognize phishing attempts and suspicious activity is critical.
- Data Encryption: Protecting sensitive data through encryption adds an extra layer of defense. Even if attackers gain access to the system, encrypted data is far less useful without the decryption key.
By analyzing these breaches and understanding their causes, organizations can adopt more effective measures to prevent similar events from occurring in the future, reducing their exposure to potential risks.
Key Principles of Ethical Hacking
Ethical hacking plays a crucial role in identifying vulnerabilities before malicious actors can exploit them. It involves authorized testing and examination of systems to uncover weaknesses, ensuring that they are addressed proactively. Understanding the core principles behind ethical hacking helps professionals carry out assessments responsibly while maintaining legal and moral boundaries.
One of the fundamental aspects of ethical hacking is authorization. Before any system is tested, ethical hackers must ensure they have explicit permission from the system owner to perform assessments. This legal agreement protects both the tester and the organization. Without proper authorization, even well-intentioned actions can result in significant legal consequences.
Another critical principle is confidentiality. Ethical hackers must maintain the privacy of the information they come across during testing. Sensitive data, such as customer details, proprietary systems, or business plans, must be handled carefully to avoid exposure. Breaching confidentiality can lead to reputational damage and potential lawsuits, making it essential to respect privacy at all times.
Integrity is also central to ethical hacking. Hackers must conduct assessments honestly, reporting their findings accurately and avoiding tampering with data or systems. They should not alter or destroy anything during testing. The goal is to uncover vulnerabilities without creating additional risks or harm to the organization’s assets.
Finally, responsibility ensures that ethical hackers are always working in the best interest of the organization. They are expected to prioritize the safety and stability of systems, avoid disruptions, and offer actionable recommendations for remediation. Ethical hackers must act in good faith to improve systems’ security without exploiting their findings for personal gain.
By adhering to these principles, ethical hackers can make significant contributions to a safer digital environment, helping organizations identify potential risks while maintaining ethical standards.
Risk Assessment Strategies in Security
In any organization, understanding and managing potential threats is essential for maintaining the integrity of digital environments. Identifying risks and evaluating their potential impact can help develop strategies to mitigate those threats before they cause harm. Risk assessment serves as a foundational element in ensuring that the necessary precautions are in place to protect assets, data, and systems.
The process begins with identifying potential risks, including vulnerabilities in systems, external threats, or even internal weaknesses. By analyzing these risks, businesses can assess the likelihood of an attack or breach occurring. This evaluation allows for a more focused and efficient approach to managing resources to combat potential threats.
Risk Identification and Prioritization
Once risks are identified, they need to be prioritized based on their likelihood and the severity of their potential impact. Some risks may be less likely but catastrophic if realized, while others may be frequent but manageable. By prioritizing, organizations can ensure that they allocate resources effectively, addressing the most pressing threats first.
Risk Mitigation Plans
After understanding and ranking risks, the next step is developing mitigation strategies. These plans often include implementing security measures such as firewalls, encryption, and access control mechanisms to protect against potential breaches. Additionally, businesses may need to plan for incident response and recovery processes to minimize damage in case a threat is realized.
Regularly revisiting and updating risk assessments is vital as the landscape of potential threats evolves over time. By staying proactive, organizations can better adapt to new challenges and reinforce their resilience against ever-changing risks.
Understanding Malware and Its Types
Malicious software, often referred to as malware, poses a significant threat to digital environments. It is designed to damage, disrupt, or gain unauthorized access to computer systems, networks, and data. The primary goal of malware is to compromise the functionality or integrity of targeted systems, often with the intention of stealing valuable information or causing widespread damage. Understanding the different types of malware is crucial for effectively preventing and mitigating these threats.
Common Types of Malware
Malware comes in various forms, each designed for specific malicious purposes. Below are some of the most common types:
- Viruses: These programs attach themselves to legitimate software or files and spread when those files are executed. Once activated, viruses can corrupt or delete data, slow down system performance, or spread to other devices.
- Worms: Worms are self-replicating programs that spread across networks without any user interaction. Unlike viruses, they do not need to attach to a file but exploit network vulnerabilities to spread and cause harm.
- Trojans: These deceptive programs appear as legitimate software or files but contain hidden malicious functions. Once downloaded or executed, Trojans can steal data, install other malicious software, or create backdoors for hackers to access the system.
- Ransomware: This type of malware encrypts a victim’s files or locks their system, demanding a ransom payment in exchange for restoring access to the data or system. Ransomware attacks can be devastating for both individuals and organizations.
- Spyware: Spyware secretly monitors a user’s activities, collects sensitive information such as passwords and credit card details, and sends it to third parties. It often works in the background without the user’s knowledge.
- Adware: While not always malicious, adware displays unwanted ads, often in the form of pop-ups or banners, and can sometimes cause disruptions or direct users to harmful websites.
Protecting Against Malware
To protect against malware, it is essential to implement preventive measures such as:
- Using reputable antivirus software that scans and detects malicious programs.
- Regularly updating software and operating systems to patch known vulnerabilities.
- Avoiding suspicious email attachments, links, and downloads from untrusted sources.
- Using firewalls to block unauthorized access to networks and systems.
- Backing up critical data to minimize the impact of potential malware infections.
By understanding malware types and adopting effective countermeasures, users and organizations can minimize the risks and safeguard their digital assets against malicious attacks.
Role of Firewalls in Network Defense
Firewalls play a crucial role in protecting digital environments from unauthorized access and cyber threats. They act as barriers between trusted internal networks and untrusted external networks, such as the internet, filtering the data that flows between them. By monitoring incoming and outgoing traffic based on a set of predetermined rules, firewalls help block harmful activities, ensuring that only legitimate communications pass through. The effectiveness of firewalls lies in their ability to detect and prevent malicious activities before they can infiltrate a network.
In addition to blocking unauthorized access, firewalls also help in monitoring traffic for unusual or suspicious behavior, often serving as an early warning system for potential threats. By configuring and maintaining firewalls properly, organizations can prevent many common types of cyberattacks, such as hacking attempts, malware infections, and denial-of-service attacks.
Types of Firewalls
There are various types of firewalls, each designed to address specific network needs:
- Packet Filtering Firewalls: These are the most basic type of firewalls, operating at the network layer. They inspect each packet of data that passes through the firewall and compare it to predefined rules. If the packet matches the rule set, it is allowed; if not, it is blocked.
- Stateful Inspection Firewalls: Unlike packet filtering, stateful firewalls keep track of the state of active connections. They ensure that the data packets are part of a valid, established connection before allowing them to pass through.
- Proxy Firewalls: Proxy firewalls act as intermediaries between the internal network and the outside world. They prevent direct communication between the two by handling requests on behalf of clients, ensuring that no internal resources are directly exposed to external networks.
- Next-Generation Firewalls (NGFW): NGFWs combine traditional firewall features with advanced security functions such as deep packet inspection, intrusion detection, and application awareness. These firewalls are capable of identifying and blocking sophisticated threats, including those that target applications and bypass conventional security measures.
Benefits of Using Firewalls
Utilizing firewalls brings several key advantages to a network:
- Access Control: Firewalls enforce access policies, ensuring that only authorized users and devices can connect to the network.
- Threat Prevention: Firewalls can block malicious traffic, including viruses, malware, and attempts to exploit vulnerabilities.
- Traffic Monitoring: They provide real-time monitoring of network traffic, helping to identify potential threats before they cause harm.
- Reduced Risk of Data Breaches: By preventing unauthorized access, firewalls significantly lower the chances of data theft or loss.
In conclusion, firewalls remain one of the most vital components in defending against cyber threats, providing organizations with an effective means of controlling network traffic and minimizing risk.
How Security Protocols Ensure Safety
Protocols designed to protect digital systems are crucial in maintaining the integrity and confidentiality of data exchanged across networks. These protocols use a series of rules and procedures to ensure that communications are safeguarded against various threats, including unauthorized access, data alteration, and eavesdropping. By establishing standards for how information should be transmitted and authenticated, these protocols create a reliable framework for protecting sensitive activities and transactions.
The core objective of such protocols is to ensure that the transmission of data is secure and that it remains intact and confidential. They achieve this by employing encryption, authentication, and integrity checks to prevent unauthorized entities from accessing or manipulating the information during its journey across a network. These protocols are implemented in a variety of services, ranging from web browsing to email communication, and their effectiveness lies in their ability to evolve in response to new threats and vulnerabilities.
Key Types of Security Protocols
Several types of protocols are designed to secure communications across different channels:
- Transport Layer Security (TLS): TLS is widely used to secure data sent over the internet. It encrypts the data stream between a client and server, ensuring that the transmitted data cannot be intercepted or read by unauthorized parties. TLS is commonly used in web browsers for HTTPS connections.
- Secure Sockets Layer (SSL): SSL, now largely replaced by TLS, was the predecessor to the TLS protocol. Like TLS, SSL ensures the encrypted transmission of sensitive data over the internet, particularly in web browsing and online transactions.
- IPsec: This protocol is used to secure IP communications by authenticating and encrypting each IP packet in a communication session. IPsec is commonly used in virtual private networks (VPNs) to ensure that data sent over public networks is protected.
- Secure Shell (SSH): SSH is a protocol used for secure remote access to systems over a network. It provides an encrypted channel for users to securely log into servers, transfer files, and run commands remotely, preventing unauthorized access to sensitive systems.
How These Protocols Enhance Digital Safety
The effectiveness of these protocols in ensuring safety is due to their ability to:
- Encrypt Data: By encrypting data, these protocols ensure that even if the data is intercepted, it cannot be read without the proper decryption key.
- Authenticate Users and Devices: Protocols like TLS and SSH include mechanisms for verifying the identity of both users and devices, making sure that only authorized parties can access sensitive information.
- Ensure Data Integrity: These protocols include checksums and hash functions to verify that the data remains unchanged during transmission, preventing tampering or corruption.
- Prevent Eavesdropping: By encrypting communications, these protocols protect the privacy of the data, ensuring that no one can listen in on confidential conversations or transactions.
In summary, protocols that are built to secure digital communications play a crucial role in ensuring safe interactions in the online world. Their ability to encrypt data, authenticate users, and verify integrity makes them essential for maintaining the trust and privacy that are vital in modern digital environments.
Incident Response Steps and Procedures

When an organization faces a disruptive event, whether it be a breach, attack, or other forms of compromise, a structured response is essential to minimize the impact and restore normal operations. Effective incident management involves a series of organized steps aimed at identifying, containing, eradicating, and recovering from the situation. Following a predefined set of procedures helps mitigate risks, protect assets, and ensure a quick recovery.
The process of responding to an incident typically involves several critical phases. Each phase plays a specific role in addressing the immediate threats, analyzing the cause, and implementing measures to prevent future occurrences. Below is an overview of the standard steps involved in the incident response process.
| Step | Objective | Key Actions |
|---|---|---|
| Identification | Detecting and recognizing an incident | Monitor systems, analyze alerts, and identify signs of abnormal activity |
| Containment | Preventing further spread of the incident | Isolate affected systems, disconnect networks, or stop ongoing malicious activity |
| Eradication | Removing the cause of the incident | Delete malware, fix vulnerabilities, and ensure that no traces of the threat remain |
| Recovery | Restoring systems and services to normal operations | Restore from backups, monitor for abnormal behavior, and verify the integrity of systems |
| Lessons Learned | Improving future response strategies | Conduct post-incident analysis, update response plans, and strengthen security measures |
Each of these stages requires precise coordination, communication, and expertise. The response team must be well-prepared and trained, as incidents can escalate quickly, and timely action is crucial. By following these key steps and continuously refining procedures, an organization can improve its ability to handle future incidents and reduce potential damage.
Legal and Ethical Issues in Cybersecurity
As the digital landscape continues to evolve, protecting systems and data has become a priority for organizations and individuals alike. However, alongside the technical aspects of defending against threats, there are important legal and ethical considerations that must be addressed. These issues often intertwine, requiring careful thought and compliance with both legal frameworks and moral principles. Understanding these factors is crucial to ensure that practices remain lawful and fair, while still providing effective protection.
Legal aspects of handling cyber threats often focus on adherence to regulations that govern data privacy, intellectual property, and online conduct. Failing to comply with laws such as data protection regulations can result in severe penalties and reputational damage. On the other hand, ethical concerns revolve around how actions are taken to prevent and mitigate cyber risks. This includes respecting privacy, avoiding harm, and ensuring transparency in cybersecurity practices.
Legal Considerations
Several key laws and regulations govern the digital world, providing guidelines for organizations on how to protect user data and maintain privacy. Some of the most well-known frameworks include:
- General Data Protection Regulation (GDPR): A European Union regulation aimed at enhancing data protection for individuals within the EU.
- Health Insurance Portability and Accountability Act (HIPAA): U.S. law that protects sensitive patient health information.
- Computer Fraud and Abuse Act (CFAA): U.S. law that criminalizes unauthorized access to computer systems and data.
- Digital Millennium Copyright Act (DMCA): U.S. law aimed at protecting copyright and limiting online piracy.
Ethical Considerations
In addition to following the law, professionals must also adhere to ethical standards in their efforts to protect systems and data. This involves:
- Privacy: Ensuring that sensitive personal information is protected and not misused.
- Transparency: Being open about cybersecurity measures, risks, and policies with stakeholders.
- Accountability: Taking responsibility for any mistakes or oversights in cybersecurity practices.
- Non-maleficence: Ensuring that actions taken to defend against threats do not cause harm to others.
While legal frameworks set the boundaries for acceptable behavior, ethical guidelines help define the responsible approach to maintaining a safe and fair digital environment. Both are essential to building trust and ensuring that cybersecurity practices are both effective and just.
Emerging Trends in Information Protection
As technology continues to advance at a rapid pace, new methods and strategies are being developed to safeguard critical data and systems. These trends are driven by the increasing complexity of cyber threats, the evolving landscape of digital innovation, and the growing need for robust protective measures. Staying ahead of these developments is essential for organizations and individuals who aim to ensure the integrity and confidentiality of their digital assets.
Modern advancements in protecting sensitive digital content are centered around several key areas that focus on adapting to emerging challenges. Among these, automation, artificial intelligence, and cloud-based solutions are playing increasingly prominent roles in defense mechanisms. Additionally, regulatory frameworks are also evolving, making it crucial for businesses to stay informed and compliant with the latest requirements.
Key Emerging Trends
- Artificial Intelligence and Machine Learning: These technologies are being leveraged to detect anomalies, predict threats, and automate response processes. They enable systems to learn from past incidents and make real-time adjustments to prevent potential risks.
- Zero Trust Architecture: This approach assumes that no user or device can be trusted by default, and access to systems is continuously verified. It enhances protection by enforcing strict identity verification and limiting the spread of potential breaches.
- Cloud Security: With the growing adoption of cloud services, ensuring the protection of data stored remotely has become essential. New cloud security frameworks focus on data encryption, secure access protocols, and constant monitoring of cloud environments.
- Privacy-Enhancing Computation: Techniques such as homomorphic encryption and secure multiparty computation are being developed to allow computations on encrypted data without revealing the underlying information. This offers new ways to protect sensitive data during processing.
- Blockchain for Protection: Blockchain technology is being explored for its ability to provide decentralized, tamper-proof systems that ensure data integrity and transparency in transactions and records.
Adapting to the Digital Future
- Biometric Authentication: The use of physical attributes like fingerprints, retina scans, and facial recognition is gaining traction as a more secure and user-friendly alternative to traditional passwords.
- Regulatory Compliance: With an increasing focus on protecting user privacy and data, businesses are prioritizing compliance with evolving regulations such as the GDPR and CCPA to avoid penalties and enhance consumer trust.
- Extended Detection and Response (XDR): This integrated approach combines data from various security tools to provide a more comprehensive and holistic view of an organization’s defense posture, helping to detect and respond to threats faster.
As these trends continue to shape the landscape of digital defense, it is clear that the future of protecting digital assets will require continuous innovation, collaboration, and adaptability. Organizations that embrace these emerging technologies and strategies will be better equipped to handle the growing challenges of the digital age.
Reviewing Exam Questions with Confidence
Approaching test questions with a clear and confident mindset is a crucial skill for achieving success in any assessment. When reviewing questions, it’s important to focus on understanding each query thoroughly before attempting to answer. The process of carefully analyzing each question can prevent mistakes and improve accuracy, ensuring that all parts of the question are addressed properly.
Developing a strategic approach to answering questions can significantly enhance performance. This includes reading questions multiple times, identifying key terms, and taking time to plan responses before diving into the answer. A confident mindset comes from preparation, practice, and understanding the material deeply, which leads to more effective and accurate responses during the test.
Key Tips for Reviewing Questions
- Understand the Instructions: Carefully read all instructions before starting. Misunderstanding what is being asked can lead to unnecessary errors.
- Identify Key Terms: Focus on important words in the question, such as “define,” “compare,” or “analyze,” as they guide how you should structure your answer.
- Plan Your Time: Before answering, determine how much time you should spend on each question. Prioritize difficult or high-point questions to ensure you allocate sufficient time.
- Stay Calm and Focused: If you encounter a difficult question, take a deep breath and move on to others. Returning later with a fresh perspective often leads to better results.
Strategies for Confident Answering
- Break Down Complex Questions: If a question is complicated, break it into smaller parts. This makes it easier to answer each section thoroughly.
- Eliminate Incorrect Choices: When faced with multiple-choice questions, eliminate obviously incorrect options first to increase the chances of selecting the right answer.
- Review Your Responses: If time allows, go back and review your answers. Check for any missing details or areas where your response can be improved.
- Trust Your Knowledge: Rely on the preparation and study you’ve done before the assessment. Confidence grows from knowing you’ve put in the work to succeed.
By following these strategies, you can approach each question with confidence, ensuring that your answers are thoughtful, precise, and complete. The key to success lies in your ability to stay focused, organized, and calm throughout the entire process.