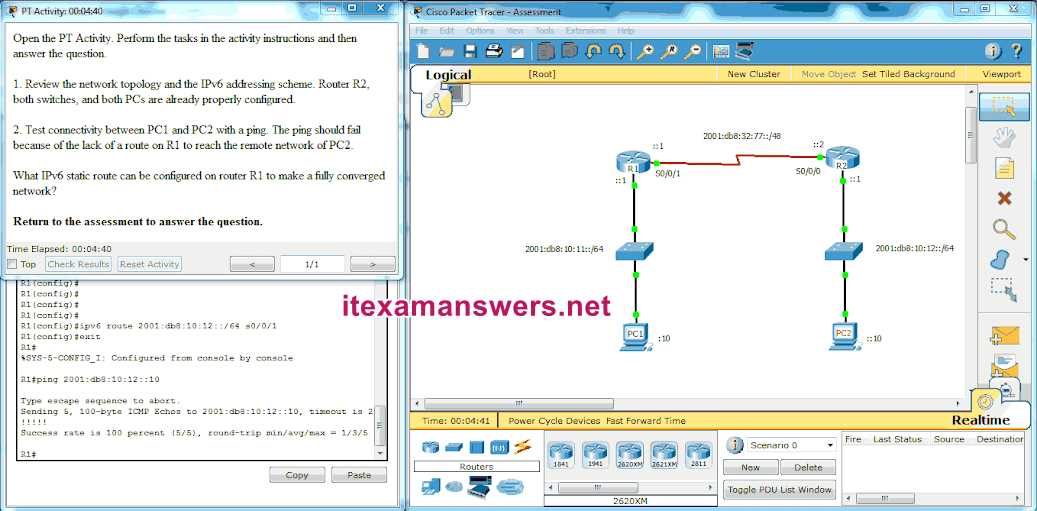
Understanding the foundational aspects of network configuration and troubleshooting is essential for anyone looking to advance in the field of IT. This section focuses on the core concepts that will challenge your comprehension and application of key networking principles. Whether you’re preparing for an evaluation or aiming to solidify your knowledge, the material is designed to test your ability to apply learned skills in real-world scenarios.
From managing network addresses to understanding how devices communicate, the knowledge covered here will enhance your ability to design, configure, and troubleshoot networks efficiently. You will explore critical protocols and configurations, which are crucial for building reliable and secure communication channels. A solid grasp of these topics is vital for ensuring optimal network performance and addressing common issues that arise in the field.
As you progress, you’ll face practical challenges that will test your skills in areas such as subnetting, routing techniques, and network security. Mastering these concepts is key to excelling in networking roles and achieving long-term success in the industry.
CCNA 2 Chapter 6 Exam Overview

This section covers essential network concepts that are vital for anyone aiming to master the fundamentals of network management and configuration. It focuses on evaluating your understanding of how devices interact within a network, and how to configure and troubleshoot various network protocols. The key topics discussed here will help you develop a deep understanding of how networks operate and how to apply theoretical knowledge in real-world scenarios.
Throughout this section, you will explore addressing schemes, routing protocols, and techniques for subnetting, all of which are foundational elements of efficient network setup. Special attention is given to configuring routers and understanding the data flow across different network segments. You will also be required to demonstrate your ability to manage these networks effectively through various simulated tasks.
Successfully mastering the material in this section is essential for moving forward in the field of network administration. The skills you develop will be tested through practical applications, helping you gain confidence in managing networks, diagnosing issues, and optimizing overall system performance.
Key Concepts for Chapter 6 Exam
This section highlights the critical topics that will test your understanding of networking principles and their real-world applications. A strong grasp of these concepts is essential for troubleshooting, configuring, and securing network infrastructures. These key ideas will lay the foundation for your practical knowledge and ensure that you are prepared for future networking challenges.
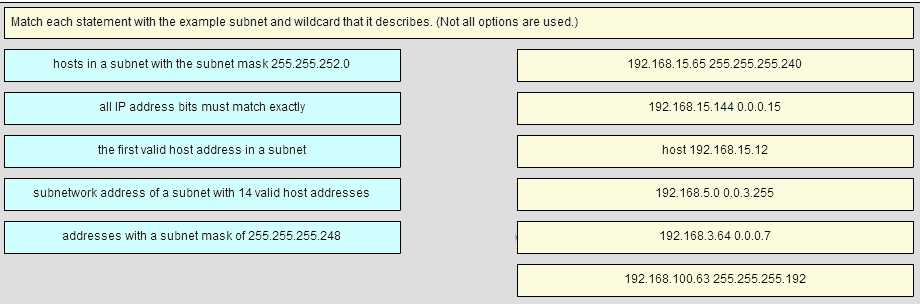
Network Addressing and Subnetting

One of the core areas in this section is understanding how to divide networks into smaller, manageable segments. Properly subnetting a network is crucial for efficient use of IP addresses and ensuring that the network functions optimally. You will explore both IPv4 and IPv6 addressing, along with subnet masks and the process of network segmentation.
Routing Protocols and Configuration
Routing plays a pivotal role in how devices within different network segments communicate with each other. In this section, you will focus on configuring routers, understanding routing tables, and applying routing protocols like RIP and OSPF. A solid understanding of these protocols ensures that network traffic is directed correctly and efficiently, which is vital for network stability and performance.
Understanding Network Addressing in Depth
Effective network communication relies on proper addressing, which ensures that data packets are routed correctly from one device to another. This section focuses on the essential techniques for assigning addresses, including both logical and physical addressing schemes. Understanding the structure and application of these addressing systems is key to maintaining an organized and functional network.
IPv4 Addressing and Subnetting

IPv4 addresses are the foundation of most networks, and subnetting plays a crucial role in dividing large networks into smaller, more manageable segments. A solid understanding of the address format and subnetting techniques is necessary to efficiently allocate IP addresses and optimize network performance. Subnet masks are used to distinguish the network portion from the host portion of the address, helping to define network boundaries and improve security.
IPv6 Addressing and Structure
IPv6 was developed to address the limitations of IPv4, especially the limited number of available addresses. It uses a larger address space, making it capable of supporting a vast number of unique IP addresses. Understanding the structure and benefits of IPv6 addressing is becoming increasingly important as more networks transition to this newer protocol.
| IPv4 Address | IPv6 Address |
|---|---|
| 32-bit address | 128-bit address |
| Written in four decimal octets | Written in eight hexadecimal blocks |
| Limited address space | Vast address space |
| Uses subnetting | Auto configuration & simplified routing |
IP Routing Basics for Success
Routing is the backbone of effective communication across networks, ensuring that data packets travel efficiently from their source to the correct destination. A clear understanding of routing principles is essential for anyone working with network infrastructures. This section covers the foundational concepts that will help you master routing configurations and enhance network performance.
Routing Protocols Overview
Routing protocols determine how routers exchange information about network routes, enabling them to forward data correctly. There are various types of routing protocols, each designed to suit different network requirements. Below are some of the most commonly used protocols:
- RIP (Routing Information Protocol) – A distance-vector protocol that uses hop count as its metric for path selection.
- OSPF (Open Shortest Path First) – A link-state protocol that uses the shortest path first algorithm to determine the best route.
- EIGRP (Enhanced Interior Gateway Routing Protocol) – A hybrid protocol that combines the best features of distance-vector and link-state protocols.
Understanding Routing Tables
Routing tables are essential for determining the best path for data packets. They contain information about available routes and the associated metrics, helping routers decide how to forward data. Each entry in the routing table includes:
- Destination Network – The network or IP address to reach.
- Next Hop – The next router on the path to the destination.
- Metric – A value used to evaluate the cost of the route (e.g., hop count or delay).
- Interface – The local interface through which the data will exit the router.
By understanding how routers make decisions based on these entries, you can configure and optimize your network routing effectively. Properly managing routing tables ensures that data flows efficiently and securely through the network.
Common Topics and Focus Areas
As you prepare to demonstrate your understanding of networking principles, it is important to focus on the key areas that will be heavily tested. These topics are fundamental to network design, configuration, and troubleshooting, and mastering them will help you effectively apply your knowledge in real-world scenarios. This section will guide you through the most common focus areas and their essential concepts.
Subnetting and IP Addressing
One of the most critical skills is understanding how to manage and assign IP addresses effectively. Subnetting allows you to divide a larger network into smaller segments for better performance and security. Key concepts include:
- Subnet Masks – Understanding how to apply subnet masks to divide networks.
- IP Classes – Recognizing the different types of IP address classes and their uses.
- Calculating Subnet Ranges – Mastering the ability to calculate subnets and address allocation.
Routing Protocols and Configuration
Routing is a core component of network communication. Understanding how routers direct data packets between different network segments is essential. Key routing protocols and concepts include:
- Distance-Vector Protocols – Understanding RIP and its limitations.
- Link-State Protocols – Grasping the fundamentals of OSPF and its advanced capabilities.
- Configuring Routers – Setting up routing tables, interfaces, and network routes.
Focusing on these topics will help you gain a deeper understanding of how networks operate and how to troubleshoot common issues that arise in network environments.
How to Approach Subnetting Problems
Subnetting can seem challenging at first, but breaking down the problem into manageable steps makes it more approachable. The key to solving subnetting issues is understanding how IP addresses and subnet masks work together to divide a network into smaller segments. This section will guide you through the process of efficiently calculating subnets and address ranges, ensuring accurate and optimized network configurations.
To approach subnetting problems, follow these general steps:
- Identify the Network Requirements – Determine how many subnets and hosts are needed for the network.
- Convert to Binary – Convert the IP address and subnet mask to binary form to see how the network is divided.
- Calculate the New Subnet Mask – Adjust the subnet mask based on the number of required subnets.
- Divide the Address Space – Break the available address space into the necessary subnets.
- Determine the Address Ranges – Calculate the first and last usable IP addresses for each subnet.
To better illustrate the process, consider the following example with an IPv4 address and a subnet mask:
| IP Address | Subnet Mask | Number of Subnets | Subnet Address Range |
|---|---|---|---|
| 192.168.1.0 | 255.255.255.0 | 256 | 192.168.1.0 – 192.168.1.255 |
| 192.168.1.0 | 255.255.255.128 | 2 | 192.168.1.0 – 192.168.1.127 |
By practicing these steps and using examples, you will become proficient in solving subnetting challenges and effectively allocating IP addresses within a network.
Analyzing Routing Protocols in Chapter 6
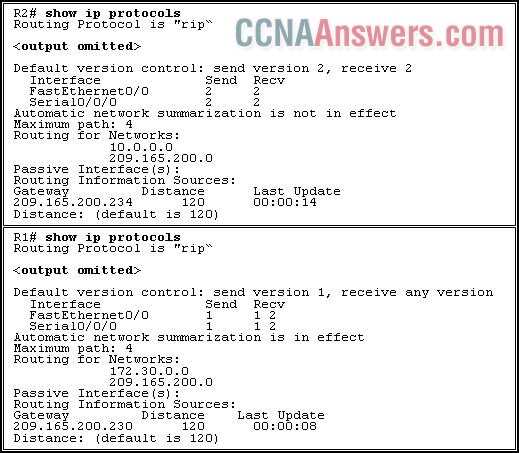
Routing protocols are essential for directing traffic across networks, ensuring that data packets travel efficiently from one point to another. In this section, we delve into the various protocols that play a critical role in determining the best path for data to take. By understanding how these protocols function and interact, you can effectively manage and optimize network performance, ensuring that devices communicate seamlessly within diverse network topologies.
Different routing protocols use distinct methods to discover and maintain routes within a network. The most commonly used protocols can be broadly categorized into distance-vector and link-state types, each offering unique features to suit different network needs.
Distance-Vector Protocols rely on routers exchanging information about the entire network topology. One popular example of this is the Routing Information Protocol (RIP), which uses hop count as its metric to determine the best route. While simple to configure, RIP has limitations in larger networks due to its slow convergence time and lack of scalability.
Link-State Protocols like Open Shortest Path First (OSPF) take a more dynamic approach. These protocols allow routers to have a complete map of the network’s topology and make more informed routing decisions based on the shortest path. OSPF is widely used in enterprise networks due to its efficiency and scalability.
By understanding the key differences between these protocols, you can choose the most suitable one for your network, balancing factors such as speed, reliability, and network size. The ability to configure and troubleshoot these protocols is crucial for anyone working with large-scale networking environments.
Important Commands for Network Configuration
Configuring a network requires familiarity with essential commands that enable administrators to manage devices, set up routing protocols, and troubleshoot network issues. Mastery of these commands is vital for configuring interfaces, checking connectivity, and verifying routing information. This section highlights the most commonly used commands that network professionals rely on to ensure efficient operation and smooth communication across the network.
Among the most important commands for managing routers and switches are those used to view and configure network interfaces. The show ip interface brief command provides a quick overview of the status of all interfaces on a router or switch, while the interface command allows configuration of a specific interface’s settings.
For verifying network connectivity, the ping command is indispensable. It tests the reachability of a device by sending Internet Control Message Protocol (ICMP) packets. Similarly, the traceroute command is used to track the path that packets take to reach their destination, providing insight into network performance and potential bottlenecks.
Other important commands include show ip route to display the routing table and show running-config to view the active configuration on a device. These commands help network professionals monitor, adjust, and troubleshoot network configurations effectively.
Preparing for Packet Tracer Simulations
Packet Tracer simulations provide an interactive environment for practicing and testing network configurations, troubleshooting, and design scenarios. These simulations are invaluable for hands-on learning, allowing users to build and configure networks without requiring physical hardware. To make the most out of these simulations, it is essential to understand how to approach them methodically, ensuring that you are prepared for various network challenges.
The first step in preparing for these simulations is to familiarize yourself with the Packet Tracer interface and its various tools. Understanding how to navigate the software, add devices, and configure network elements will significantly improve your efficiency. The simulation environment allows you to simulate real-world network topologies, making it crucial to practice building different types of networks to gain a well-rounded understanding of routing, switching, and troubleshooting techniques.
It is also important to review the network objectives of each simulation. Be sure to understand the specific requirements and goals outlined in the task. Break down the steps methodically–begin with basic configurations such as IP addressing and routing, and progressively move towards more complex scenarios such as configuring VLANs, security settings, or advanced routing protocols. Testing each part as you go will help ensure that everything is functioning correctly.
Finally, practice is key. The more you work with simulations, the more comfortable you will become with troubleshooting and adjusting configurations on the fly. By practicing regularly, you will build confidence and develop the problem-solving skills needed for real-world network scenarios.
Reviewing ACLs and Their Application
Access Control Lists (ACLs) are a critical component in network security, used to control the flow of traffic through a network by filtering incoming and outgoing packets. They enable network administrators to define rules that permit or deny specific traffic based on parameters such as IP address, protocol type, or port number. Understanding how to configure and apply ACLs effectively is essential for maintaining secure network environments and ensuring proper traffic management.
There are two main types of ACLs: Standard ACLs and Extended ACLs. Each type serves a distinct purpose, and knowing when to use one over the other is key to designing secure network systems. Standard ACLs primarily filter traffic based on the source IP address, while extended ACLs provide more granular control by allowing filtering based on multiple criteria such as destination IP, protocol type, and port numbers.
Configuring Standard ACLs
Standard ACLs are simpler to configure and are often applied closer to the destination network. They allow for basic packet filtering based solely on the source address, making them ideal for situations where only the origin of traffic needs to be controlled. However, due to their limited functionality, they are less flexible than extended ACLs for more complex filtering requirements.
Implementing Extended ACLs
Extended ACLs offer greater flexibility and control over network traffic. By specifying both the source and destination IP addresses, along with the type of traffic (such as TCP or UDP) and port numbers, extended ACLs can be used to implement more detailed security policies. They are typically placed closer to the source network to prevent unwanted traffic before it enters the network.
When configuring ACLs, it is essential to apply them in the correct order and ensure they are placed on the right interfaces. The order of rules within an ACL is crucial, as the first matching rule will be applied, and the rest will be ignored. Additionally, ACLs should be tested thoroughly to verify that traffic is being filtered according to the desired security policies.
Mastering IPv4 and IPv6 Concepts
Understanding IP addressing is fundamental to the operation of networks. Both IPv4 and IPv6 serve as the backbone for routing traffic across the internet and within private networks. While IPv4 has been the dominant protocol for decades, the growing demand for IP addresses has led to the development and adoption of IPv6. Mastering the concepts behind both protocols is essential for network professionals to effectively configure and troubleshoot modern networks.
IPv4, the fourth version of the Internet Protocol, uses a 32-bit address space, which provides approximately 4.3 billion unique addresses. Although this may have been sufficient in the early stages of the internet, the rapid expansion of devices and services has led to IPv4 address exhaustion. This limitation is addressed by techniques such as Network Address Translation (NAT) and CIDR (Classless Inter-Domain Routing), but these solutions are not long-term fixes.
IPv6 and Its Advantages
IPv6 was developed to overcome the limitations of IPv4, offering a much larger address space through its 128-bit address structure. This vast number of unique addresses allows for an almost unlimited number of devices to be connected to the internet. IPv6 also introduces features such as simplified header formats, built-in security, and better support for mobile devices, making it a forward-looking solution for global networking needs.
Key Differences Between IPv4 and IPv6
While both protocols serve the same purpose, the differences between them are significant. IPv4 addresses are written in four octets, represented in decimal format, while IPv6 addresses are written in eight groups of four hexadecimal digits. Additionally, IPv6 eliminates the need for NAT, as its larger address space allows for direct addressing of every device. IPv6 also supports autoconfiguration, which makes it easier to set up networks without the need for a DHCP server.
As IPv6 adoption increases, network administrators must be proficient in both IPv4 and IPv6 to ensure smooth transitions and effective network management. Being familiar with the address structures, configuration methods, and potential challenges will ensure a strong foundation in modern networking practices.
Top Mistakes to Avoid During the Exam
When preparing for and taking technical assessments, it’s easy to make mistakes that can negatively impact your performance. These errors often stem from a lack of understanding, poor time management, or rushing through questions. Avoiding common pitfalls is crucial to maximizing your score and ensuring that you demonstrate your full knowledge of the material. By being aware of the most frequent mistakes, you can better prepare yourself and approach the test with confidence.
Rushing Through Questions
One of the most common mistakes during any technical assessment is rushing through questions, especially when you feel the pressure of time. It’s easy to make careless errors when you try to answer too quickly. Read each question carefully and take your time to consider all the options before selecting an answer. If you’re unsure about a particular question, mark it and come back to it later. Prioritize accuracy over speed to ensure you don’t overlook important details.
Ignoring Key Concepts and Details
Another frequent mistake is neglecting to fully understand or remember key concepts, especially when it comes to complex topics like networking protocols, addressing schemes, and configuration tasks. Even if you feel confident in certain areas, it’s important to review and refresh all the material before the test. Misunderstanding or overlooking small details can result in incorrect answers, especially in questions that require a deep level of technical knowledge. Make sure to focus on all aspects of the material and avoid skipping over sections, even if they seem less important.
By avoiding these mistakes, you can increase your chances of success. Proper preparation, careful reading, and attention to detail are essential for achieving your best results. Stay calm, stay focused, and make the most of your study time to ensure you are fully prepared when it’s time to take the test.
Practice Questions for Chapter 6 Topics
Practicing with questions related to the key topics is a vital step in solidifying your understanding and improving retention. Engaging with a variety of practice problems will help you assess your grasp of the material and identify areas that need further attention. By simulating the format and structure of the actual assessment, you’ll be better prepared to handle the challenges presented during the actual test.
Sample Question 1: Subnetting

Given the IP address 192.168.10.0/24, how many subnets can you create with a subnet mask of 255.255.255.240? What is the range of valid IP addresses for each subnet?
- A. 4 subnets, with a range of 192.168.10.1-192.168.10.14
- B. 8 subnets, with a range of 192.168.10.1-192.168.10.30
- C. 16 subnets, with a range of 192.168.10.1-192.168.10.30
- D. 2 subnets, with a range of 192.168.10.1-192.168.10.15
Sample Question 2: Routing Protocols
Which routing protocol uses a link-state algorithm and is commonly used in larger enterprise networks for faster convergence?
- A. RIP
- B. OSPF
- C. EIGRP
- D. BGP
These practice questions are designed to test your understanding of fundamental networking concepts such as subnetting, IP addressing, and routing protocols. By regularly practicing questions like these, you will improve your ability to solve problems quickly and accurately during the actual test. Make sure to review your answers and understand why certain choices are correct or incorrect, as this will enhance your comprehension and build confidence for the real assessment.
How to Manage Time During the Test
Effective time management during any assessment is crucial for ensuring you complete all tasks and answer as many questions correctly as possible. Without a solid strategy, it’s easy to waste valuable time on more challenging questions and miss opportunities to address simpler ones. By pacing yourself and prioritizing, you can enhance both your confidence and performance throughout the test.
Here are a few key strategies to optimize your time during the assessment:
| Time Management Strategy | Description |
|---|---|
| Start with Easy Questions | Begin by answering the questions you find simplest, as this will build confidence and save time for harder sections. |
| Set Time Limits | For each section or group of questions, set a specific time limit to prevent spending too long on any one part of the test. |
| Skip and Return | If you encounter a difficult question, skip it and return to it later after addressing easier ones. This prevents frustration and time wastage. |
| Review the Entire Test | Before you begin, quickly skim through the test to get a sense of the types of questions and allocate time accordingly. |
By employing these strategies, you can ensure that you manage your time wisely and avoid running out of time before completing all the sections. Keep a steady pace, but don’t rush–focus on accuracy and efficiency, and give yourself the best chance of success.
Using Study Resources Effectively
Maximizing the potential of available study materials is essential for mastering key concepts and achieving success in assessments. The right resources can help you reinforce your understanding, practice skills, and deepen your knowledge in areas that require more focus. However, it’s important to approach these materials strategically to get the most out of your study sessions.
Here are some practical ways to use study resources effectively:
Leverage Different Types of Resources
- Textbooks and Manuals: These provide a structured approach and in-depth explanations of core concepts. Use them to build a solid foundation.
- Online Tutorials: Interactive lessons and videos can break down complex topics, making them easier to understand and apply.
- Practice Tests: Take practice quizzes and mock exams to simulate real-world scenarios and gauge your readiness.
- Study Groups: Collaborating with others can help clarify difficult concepts, and it provides an opportunity to discuss and reinforce learning.
Develop a Focused Study Plan
- Set Clear Goals: Identify the areas where you need the most improvement and prioritize those topics.
- Balance Resources: Use a mix of written, visual, and hands-on learning to reinforce knowledge and skills.
- Allocate Time Wisely: Dedicate specific time blocks to different types of materials to avoid spending too much time on any single resource.
By utilizing a combination of resources and adopting a focused approach, you can optimize your study routine and improve your overall performance. Consistency, planning, and variety are key to mastering the material and achieving your learning objectives.
Importance of Hands-on Practice
While theoretical knowledge forms the foundation of any technical field, practical experience is essential for mastering the concepts and applying them effectively. Hands-on practice allows learners to engage directly with the material, gain real-world experience, and reinforce what they’ve learned in a practical setting. This active involvement not only builds confidence but also enhances problem-solving abilities.
Here are some key reasons why hands-on practice is crucial:
- Application of Concepts: Practicing with real equipment or simulations helps transform theoretical knowledge into usable skills. Understanding how concepts work in practice is essential for success.
- Developing Troubleshooting Skills: Hands-on exercises give learners the opportunity to identify issues, troubleshoot, and resolve problems–skills that are vital for success in technical roles.
- Building Confidence: Working through practical scenarios builds self-assurance, preparing individuals for real-world challenges.
- Engagement and Retention: Active involvement in hands-on activities enhances retention and understanding, as learners are more likely to remember what they’ve physically experienced.
Incorporating hands-on practice into your study routine can significantly improve your ability to perform tasks under real-world conditions. Whether through physical labs, virtual simulations, or network configuration tools, practical experience is indispensable for mastering complex concepts and becoming proficient in the field.
Tips for Retaining Networking Knowledge

Mastering networking concepts can be challenging, but the key to long-term success is retaining the information learned. Retention involves not only understanding the material but also being able to recall and apply it when needed. Incorporating effective study techniques and strategies can significantly improve memory and comprehension, making it easier to build a strong knowledge base.
Effective Strategies for Retaining Knowledge
- Regular Practice: Continuous exposure to real-world networking tasks is essential. The more you practice, the more the concepts will solidify in your memory.
- Active Recall: Instead of passively reading or watching tutorials, test your knowledge by recalling information from memory. This active engagement reinforces neural connections and strengthens retention.
- Teach What You Learn: Teaching others what you’ve learned is one of the best ways to solidify your understanding. If you can explain it clearly, you’re more likely to remember it.
- Break Down Complex Topics: Divide large concepts into smaller, manageable chunks. This will make it easier to understand and remember key details without feeling overwhelmed.
- Visual Aids and Diagrams: Many networking concepts, such as IP addressing and routing, are easier to remember when represented visually. Create diagrams or flowcharts to help connect ideas.
- Use Mnemonics and Acronyms: Create memory aids to recall complex information. Acronyms or phrases can make it easier to remember lists or technical details.
Reinforcing Learning with Consistency
- Frequent Review: Regularly revisit previously learned material. Spacing out review sessions ensures the information remains fresh and prevents forgetting over time.
- Simulations and Hands-on Exercises: Engaging in practical labs and simulations provides an opportunity to apply knowledge in real-world scenarios, which reinforces the learning process.
- Join Study Groups: Collaborating with peers can help you reinforce your knowledge, exchange ideas, and fill in gaps in understanding.
By implementing these techniques into your study routine, you will not only retain more information but also gain the ability to apply it effectively when the time comes. Consistency and active engagement are the keys to mastering complex networking topics.
Exam Day Strategy and Mental Prep
The final step before achieving your certification involves preparing both mentally and strategically for the test. Success on the day of the evaluation relies not only on the knowledge you’ve acquired but also on your ability to manage time, stay focused, and maintain composure under pressure. Proper mental preparation and a solid strategy can make all the difference between performing well and feeling overwhelmed.
Strategic Planning for the Day
- Arrive Early: Arriving at the testing center ahead of time allows you to settle in, calm your nerves, and mentally prepare before starting.
- Time Management: Know how much time you have and pace yourself throughout the assessment. Spend more time on questions that require deeper thought, but don’t get stuck on any single question.
- Read Instructions Carefully: Before answering any questions, ensure that you understand what is being asked. Misinterpreting a question can lead to unnecessary mistakes.
- Skip and Return: If you come across a particularly challenging question, skip it and move on. You can always return to it later with a fresh perspective.
- Stay Calm and Confident: Confidence is key. If you encounter a difficult problem, take a deep breath and approach it step by step. Trust in the preparation you’ve done.
Mental Preparation Before the Test
- Get Adequate Rest: Ensure you have a good night’s sleep before the test day. Fatigue can cloud your thinking and reduce focus.
- Eat Well: Eat a balanced meal before the assessment. Avoid heavy or sugary foods that could lead to a crash in energy during the test.
- Stay Positive: Maintain a positive mindset leading up to the test. Visualize yourself performing well, and remind yourself of the hard work you’ve put in.
- Practice Relaxation Techniques: Simple breathing exercises or short breaks can help relieve stress and help you stay focused during the assessment.
By having a clear strategy for the test day and preparing mentally, you set yourself up for success. A calm and focused mindset, combined with effective time management, will help you navigate the test with confidence and clarity.