
In this section, we delve into a crucial part of the networking curriculum that focuses on protecting and securing network infrastructures. Understanding the core concepts in this area is essential for anyone looking to advance in the field of network management. With a mix of theory and practical skills, this content equips you with the knowledge necessary to tackle various real-world challenges.
The material here is designed to test your grasp of fundamental principles, technologies, and protocols. It emphasizes both defensive strategies and the tools required to safeguard digital environments from potential threats. As you work through the questions, you will build a strong foundation in network defense mechanisms, enhancing your ability to design and implement secure systems.
By approaching this content strategically, you will not only prepare for certification assessments but also gain valuable insights applicable to everyday networking tasks. The techniques and practices discussed are vital for securing sensitive data, preventing breaches, and maintaining the integrity of communication channels across diverse platforms.
CCNA Security Chapter 7 Exam Answers
This section is dedicated to helping you reinforce your understanding of critical networking concepts related to infrastructure protection. It explores various scenarios and challenges that network professionals may face when securing their systems. You will gain valuable insights into protocols, best practices, and defensive measures to effectively safeguard digital environments.
As you work through this content, it is important to focus on both theoretical knowledge and practical applications. By testing your understanding with real-world examples, you can deepen your grasp of the technologies that play a vital role in securing networks. The following table provides a summary of key points covered in this section:
| Topic | Description |
|---|---|
| Network Defense | Understanding defensive mechanisms to safeguard network infrastructure |
| Protocols | Exploring secure communication methods and their applications |
| Threats and Vulnerabilities | Identifying potential risks and weaknesses within a network |
| Security Tools | Examining tools and technologies used to enhance network protection |
These topics represent key areas that will be tested and are essential for understanding how to maintain secure and reliable networks. Focusing on these concepts will give you the confidence needed to tackle any related questions successfully.
Understanding Key Exam Topics
In this section, we focus on the fundamental subjects that are critical to mastering network protection and defense. These topics form the backbone of any comprehensive study plan and provide the foundation for understanding how to effectively secure communication channels. By gaining a deeper understanding of these core concepts, you will be better equipped to tackle complex challenges in network security.
Network Security Principles
One of the primary areas of focus is the principles behind network security. This includes the strategies and methodologies employed to ensure data confidentiality, integrity, and availability. A solid grasp of these principles is essential for recognizing potential vulnerabilities and implementing the right defensive measures. Topics such as firewalls, intrusion detection systems, and secure access protocols are central to this area.
Common Threats and Mitigation Techniques
Another key area to understand is the range of potential threats that could compromise the network’s safety. This involves learning about various types of attacks such as man-in-the-middle, denial of service, and social engineering. Equally important is the knowledge of countermeasures used to prevent or mitigate these risks, such as encryption, authentication, and access control policies.
Common Questions in Chapter 7
In this section, we will explore some of the most frequently encountered topics and inquiries that arise in the study of network protection. These questions are designed to test your comprehension of key concepts and practical implementations. By addressing them, you will strengthen your understanding of the material and gain insight into the types of challenges you may face when securing a network environment.
These questions typically revolve around identifying vulnerabilities, selecting the appropriate defense mechanisms, and understanding how different technologies interact within a secured infrastructure. It is crucial to focus not only on theoretical knowledge but also on practical application. By doing so, you will develop a more comprehensive skill set to protect and manage digital systems effectively.
For example, you may encounter questions that ask you to determine the best method for implementing access control policies or to analyze different types of network attacks and how they can be mitigated. Being able to answer these questions correctly is essential for demonstrating a clear understanding of secure network management practices.
Effective Study Strategies for Success
Success in mastering network protection concepts depends heavily on the study methods you choose. To excel in this field, it is essential to adopt strategies that enhance both your understanding and retention of complex topics. By following a structured approach, you can approach your studies with confidence and ensure that you are well-prepared for practical challenges.
One effective strategy is to break down the material into manageable sections and focus on mastering one concept at a time. This helps prevent feeling overwhelmed and allows you to build a strong foundation of knowledge. Consider using the following approaches to maximize your study effectiveness:
- Active Learning: Engage with the material through practical exercises, labs, and simulations. This hands-on experience reinforces theoretical knowledge and helps you better understand how to apply it in real-world scenarios.
- Regular Review: Consistently review what you’ve learned to reinforce key concepts. Regular revision helps ensure that information is retained and ready for application when needed.
- Practice with Sample Questions: Work through sample questions to get used to the format and types of inquiries you might encounter. This also helps you identify areas where further study may be needed.
- Group Study Sessions: Collaborating with peers can be highly beneficial. Discussing difficult concepts together often leads to a deeper understanding and allows you to learn from others’ perspectives.
- Time Management: Organize your study time effectively. Set aside specific periods for each topic and avoid cramming at the last minute. Consistent, scheduled study sessions help reinforce your knowledge over time.
By incorporating these techniques into your routine, you can significantly improve your performance and develop a thorough understanding of network protection principles. The goal is to not only memorize information but to be able to apply it in practical scenarios confidently.
Important Security Concepts Covered
This section explores essential principles that play a crucial role in protecting digital infrastructures. Understanding these concepts is fundamental for anyone working in network management and risk mitigation. The knowledge gained here will help you effectively safeguard networks from potential threats and vulnerabilities.
Network Defense Mechanisms

One of the primary areas covered is the range of defense techniques designed to protect network systems. This includes the deployment of firewalls, intrusion prevention systems (IPS), and intrusion detection systems (IDS). These technologies are vital in identifying and blocking unauthorized access, ensuring that only trusted users can interact with critical resources. Additionally, encryption methods and secure communication protocols are discussed, which help to maintain the integrity and confidentiality of data.
Risk Management and Threat Identification
Another key area of focus is recognizing and managing potential threats to network integrity. This includes understanding common types of attacks such as denial-of-service (DoS), phishing, and man-in-the-middle attacks. Effective risk management involves identifying vulnerabilities within the network, evaluating the potential impact of various threats, and applying the appropriate mitigation strategies. Implementing proper access control mechanisms and ensuring data protection are also essential elements in minimizing risks.
Hands-on Practice for Exam Preparation
One of the most effective ways to prepare for assessments is through hands-on experience. This allows you to apply theoretical knowledge to real-world scenarios, reinforcing your understanding and problem-solving skills. By working directly with tools, systems, and configurations, you can gain practical insights that are invaluable for tackling complex challenges in the field of network protection.
Practical exercises help bridge the gap between theoretical concepts and their real-world applications. Engaging in labs and simulations not only strengthens your technical abilities but also boosts your confidence in dealing with various security tasks. Consider integrating the following practices into your study routine:
- Simulation Tools: Use network simulators to create and manage virtual networks. This will allow you to experiment with different configurations and troubleshoot issues without the risk of disrupting live systems.
- Hands-on Labs: Participate in hands-on labs that mimic real-world network environments. These exercises enable you to practice configuring security devices, such as firewalls and routers, and implement security protocols.
- Configuration Challenges: Regularly engage in configuration challenges that require you to set up secure communication channels, implement access controls, and perform network hardening.
- Monitoring and Analysis: Set up monitoring tools and learn how to analyze logs for signs of unauthorized activity. This practice helps develop your ability to identify potential threats and respond effectively.
- Scenario-Based Practice: Work through scenario-based exercises where you need to design and secure a network based on given requirements. This helps to build strategic thinking and apply your knowledge in different contexts.
By dedicating time to hands-on activities, you not only improve your technical skills but also prepare yourself for real-world tasks that you will encounter in professional settings. Practical experience is an indispensable part of mastering network protection concepts.
Exam Format and Question Types
Understanding the structure and types of questions commonly encountered in assessments is essential for effective preparation. Knowing what to expect allows you to focus your study efforts on areas that are most likely to appear, as well as improve your time management and problem-solving skills during the assessment. This section will outline the different formats and question types you can expect when testing your knowledge of network protection and defense.
Multiple-Choice Questions

Multiple-choice questions are one of the most common question types found in these types of assessments. These questions typically present a scenario followed by several possible answers. Your task is to select the most accurate or appropriate option based on your understanding of the material. To excel in this format, it’s crucial to understand key concepts and be able to quickly identify the most relevant answer.
Simulations and Configuration Tasks
In addition to traditional multiple-choice questions, many assessments also include simulations and configuration tasks. These require you to interact with virtual environments and make configurations based on specific instructions. For example, you might be asked to configure network devices, implement security measures, or troubleshoot issues in a simulated network environment. Practicing hands-on skills in real-world scenarios is essential to performing well in this type of question.
By becoming familiar with these formats, you will be better prepared to approach the assessment with confidence and demonstrate your knowledge of securing network infrastructures effectively.
Tips for Time Management During the Exam
Proper time management during an assessment is crucial to ensuring that you can complete all questions accurately without rushing. Effective time allocation allows you to approach each question with focus, giving yourself the best chance to demonstrate your knowledge fully. In this section, we’ll explore strategies to help you make the most of your time during the test.
Strategies for Efficient Time Use
One of the most important factors in time management is knowing how to pace yourself throughout the test. Below are some practical tips to help you manage your time effectively:
- Read through the entire test: Before starting, take a few minutes to skim through all the questions. This gives you an overview of what’s covered and helps you identify easier questions to tackle first.
- Set time limits for each section: Allocate a specific amount of time for each group of questions. Stick to this time limit to avoid spending too much time on one section.
- Start with the easier questions: Begin with questions you are most comfortable with. This builds confidence and ensures you gain points early in the test.
- Don’t dwell on difficult questions: If you encounter a challenging question, move on and return to it later. This prevents wasting too much time on one issue while allowing you to complete the easier ones.
Managing Time During Practical Tasks
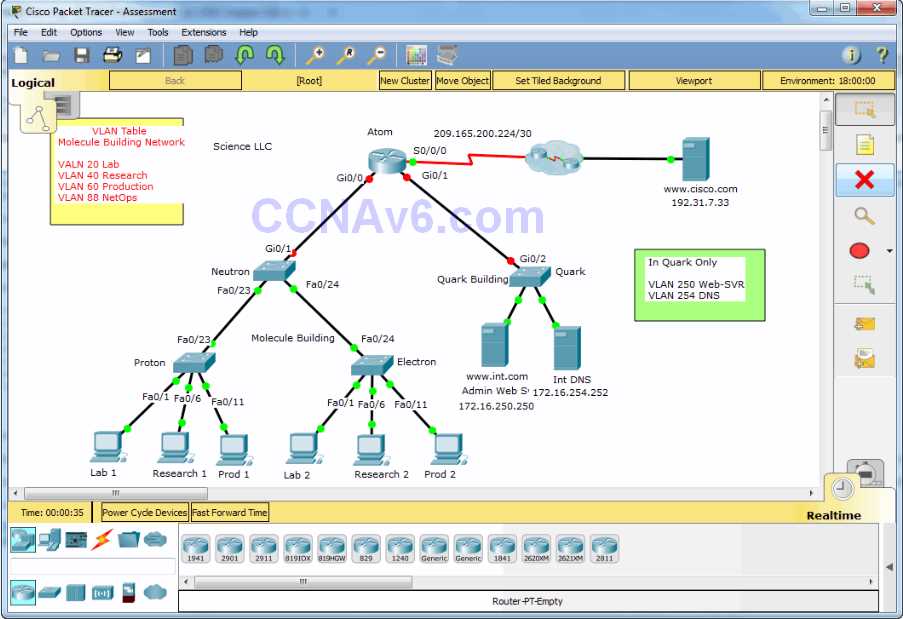
For assessments that include hands-on tasks or simulations, time management becomes even more critical. Follow these additional strategies:
- Practice beforehand: Get familiar with the tools and environments you will be using. The more comfortable you are with the system, the faster you can complete tasks.
- Work methodically: Stay organized by completing tasks step by step. Double-check configurations only after completing the primary steps to avoid unnecessary delays.
- Track your time: Regularly check the time to ensure you’re staying on track and adjust your approach if necessary.
By incorporating these time management techniques into your study and exam strategies, you will be better prepared to efficiently handle the tasks and complete the test with confidence.
Analyzing Previous Exam Questions
Reviewing past questions is an excellent way to prepare for any assessment, as it allows you to familiarize yourself with the format and the types of topics that are typically covered. By analyzing previous questions, you can identify patterns and focus your study efforts on the most commonly tested areas. This method also helps you become more efficient in answering questions, improving both speed and accuracy.
When going through past questions, it is important to not only focus on the correct answers but also to understand the reasoning behind them. This enables you to gain deeper insights into the subject matter and ensures you are able to approach similar problems with confidence.
- Identify recurring topics: Many questions in previous assessments revolve around certain core concepts. Pay attention to these key areas and make sure you fully understand them.
- Practice with different question types: Past assessments often include a mix of question formats, such as multiple-choice, simulations, and short-answer. Practicing with each type will help you be prepared for whatever format you may encounter.
- Understand common pitfalls: Many candidates make similar mistakes in their answers. By analyzing incorrect responses in past questions, you can identify common pitfalls and avoid them during your own assessment.
- Time your responses: Practice answering previous questions within the allotted time to simulate real test conditions. This will help you manage your time effectively during the actual test.
By consistently analyzing past questions, you can fine-tune your understanding of the material and improve your performance on the actual assessment.
Reviewing Key Networking Protocols
Mastering the fundamental protocols used in networking is essential for understanding how data is transmitted securely and efficiently across various systems. These protocols form the backbone of communication between devices, ensuring that data flows correctly and securely. In this section, we will explore some of the most crucial protocols that you should review to strengthen your knowledge and troubleshooting skills in network environments.
Each protocol serves a specific purpose, and understanding how they interact with one another is key to effective network management. Below are some of the most important protocols to focus on:
- Transmission Control Protocol (TCP): This protocol is responsible for ensuring reliable communication between devices. It guarantees that data packets are sent and received in the correct order.
- Internet Protocol (IP): IP is essential for addressing and routing data packets across networks. It ensures that data reaches the correct destination by using unique IP addresses.
- Hypertext Transfer Protocol (HTTP): Used for transferring web pages, HTTP allows web browsers and servers to communicate. It is the foundation of data exchange on the internet.
- File Transfer Protocol (FTP): FTP is used to transfer files between computers over a network. It supports both uploading and downloading files and is commonly used in data management tasks.
- Simple Mail Transfer Protocol (SMTP): SMTP is used to send email messages between servers. It ensures that your messages are routed to the correct destination mail server.
- Domain Name System (DNS): DNS translates human-readable domain names (like www.example.com) into IP addresses, making it easier for users to access websites.
Familiarizing yourself with these protocols will help you understand how data is transmitted, how communication between devices is established, and how to troubleshoot common network issues. Make sure to study how these protocols are configured and how they interact with each other in different network setups.
Common Mistakes to Avoid
When preparing for any type of assessment, it’s easy to make mistakes that could have been easily avoided with a little more attention to detail. Understanding these common pitfalls will help you focus on the right strategies and ensure that you don’t fall into the traps that many candidates encounter. In this section, we will highlight some frequent errors and provide tips on how to avoid them during your preparation and on the day of the test.
One of the key factors in successful preparation is staying organized and focused. Many people fall into the habit of rushing through their study material, hoping to cover everything quickly. However, this can lead to misunderstandings or missed key concepts. Taking a more methodical approach is essential for retaining and applying what you’ve learned.
- Overlooking the basics: It’s tempting to jump straight into complex topics, but neglecting the foundational concepts can lead to gaps in understanding. Review the core principles before moving on to advanced material.
- Ignoring practice questions: Simply reading through study guides or textbooks may not be enough. Practicing with sample questions helps reinforce your knowledge and prepares you for the test format.
- Skipping review sessions: It’s easy to underestimate the value of revisiting material. Regularly reviewing past topics ensures that you retain information and can recall it when needed.
- Spending too much time on one topic: While it’s important to understand every subject, spending excessive time on one area can result in neglecting others. Ensure a balanced approach by allocating time effectively across all topics.
- Failing to manage time: During both your study sessions and the test, managing your time is crucial. Avoid rushing through the questions, but also be mindful not to spend too much time on any one issue.
- Not staying calm under pressure: Stress can affect your performance. If you feel anxious during the test, take a deep breath and move forward. Staying calm allows you to think clearly and make better decisions.
By avoiding these common mistakes and adopting a more strategic approach, you’ll increase your chances of success and feel more confident when it’s time to take the test.
Understanding Network Security Threats
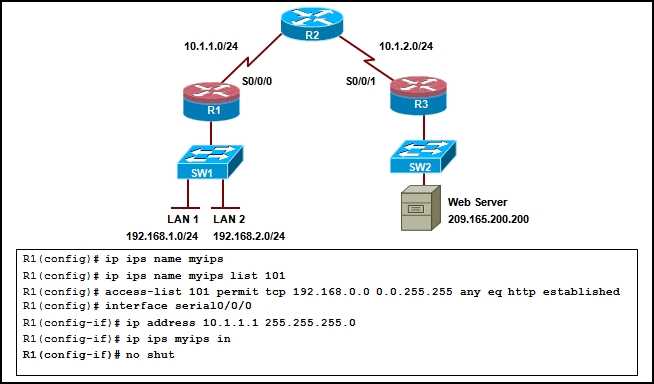
As technology continues to advance, the risks to networked systems and data have become more complex and diverse. In any network environment, threats can come from a variety of sources, ranging from malicious actors to unintentional human error. It is essential to understand the different types of threats that can compromise the integrity of a network and how to mitigate them effectively. This section will explore common network security threats and provide insights on how to protect against them.
Types of Threats

Network threats can be categorized into several different types, each requiring specific preventive measures. Some of the most common threats include:
- Malware: This is a broad category that includes viruses, worms, ransomware, and spyware. These programs can infect computers and networks, causing damage, stealing data, or even taking control of systems.
- Phishing Attacks: Phishing involves tricking individuals into revealing sensitive information, such as usernames, passwords, or financial details, by impersonating trustworthy entities in emails or websites.
- Denial of Service (DoS) Attacks: These attacks aim to overwhelm a network or server with traffic, rendering it unavailable to legitimate users. Distributed Denial of Service (DDoS) attacks are a more sophisticated version, utilizing multiple systems to flood the target.
- Man-in-the-Middle (MitM) Attacks: In this type of attack, the attacker intercepts and potentially alters the communication between two parties without their knowledge. This can lead to data theft or unauthorized access to sensitive information.
Preventive Measures
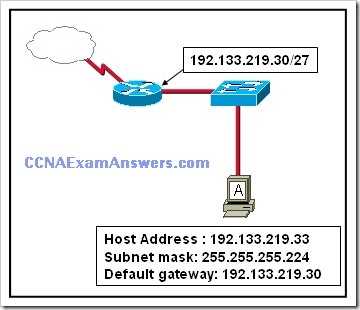
Once you understand the various threats that can affect a network, the next step is to implement effective security measures. Here are some strategies to consider:
- Use of Firewalls: Firewalls are essential in filtering incoming and outgoing traffic, blocking malicious data from entering a network.
- Encryption: Encrypting sensitive data ensures that even if it is intercepted, it cannot be read without the proper decryption key.
- Regular Software Updates: Keeping all software, including operating systems and applications, up to date is crucial in closing vulnerabilities that could be exploited by attackers.
- Employee Training: Educating staff on the importance of security practices, such as avoiding suspicious links or attachments, is vital in preventing human error from compromising a network.
By recognizing the various types of network threats and implementing the appropriate safeguards, you can significantly reduce the risk of a breach and ensure the continued security of your systems and data.
How to Prepare for Simulation Questions
Simulation questions are designed to test practical skills and problem-solving abilities by simulating real-world scenarios. These types of questions require a hands-on approach, as they assess your understanding of concepts in a dynamic environment rather than relying on memorized facts. Preparing for simulation-based challenges requires a different strategy than traditional multiple-choice questions. This section will provide tips on how to effectively prepare for these types of questions.
Understanding the Key Concepts

Before diving into the practice of simulations, it’s essential to grasp the foundational concepts that will be tested. Having a strong theoretical knowledge will help you navigate real-world problems effectively. Some areas to focus on include:
- Network Configuration: Familiarize yourself with configuring various network devices, such as routers, switches, and firewalls, to perform specific tasks.
- Troubleshooting: Practice diagnosing and resolving issues related to connectivity, security, and network performance.
- Protocol Understanding: Understand key networking protocols and how they interact within a network environment.
Hands-On Practice
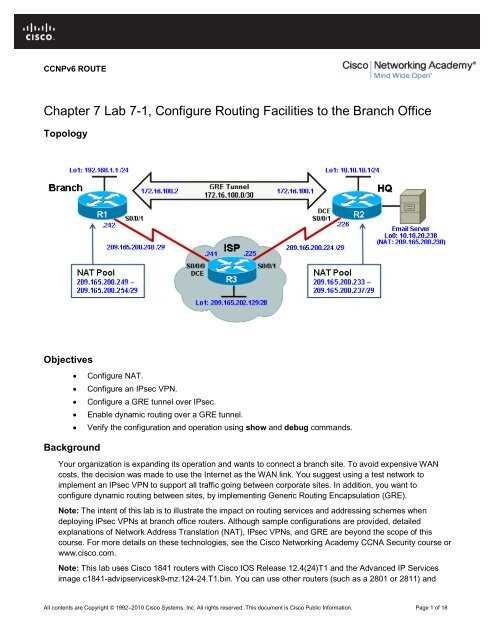
Simulation questions are best tackled with plenty of hands-on practice. Setting up virtual labs or using online simulators will allow you to apply your knowledge in a realistic environment. Here’s how you can prepare:
- Set Up Virtual Labs: Use simulation tools or platforms like GNS3, Packet Tracer, or other network simulators to practice configuring networks, routing, and troubleshooting issues.
- Work on Real-Life Scenarios: Try to recreate common issues and resolve them by applying troubleshooting steps in a controlled environment. This will sharpen your practical skills and improve your confidence in dealing with similar scenarios during testing.
- Time Management: Practice solving problems under time constraints to improve your speed and efficiency during the actual test.
By focusing on understanding core concepts and engaging in hands-on practice, you will be well-prepared to tackle simulation questions effectively. Building confidence through real-world scenarios will enable you to approach these questions with clarity and precision.
Tools and Resources for Exam Prep
Effective preparation for any certification requires the right set of tools and resources. From interactive simulations to comprehensive study guides, the right materials can significantly enhance your ability to grasp complex concepts and perform well under test conditions. This section will highlight some of the most useful tools and resources available to aid in your preparation process.
Recommended Study Materials

Having access to high-quality study materials is crucial for mastering the topics covered in any certification. Some of the top resources include:
- Books and Guides: Books tailored to certification objectives offer detailed explanations, examples, and practice questions. Popular choices often include those written by industry experts.
- Online Courses: Many platforms provide comprehensive video lessons that break down key concepts into digestible parts. These can be especially helpful for visual learners.
- Practice Tests: Practice exams simulate the real test environment and help you assess your knowledge while managing time efficiently.
Simulation Tools for Hands-On Experience
Simulation tools play an essential role in preparing for real-world scenarios. These tools allow you to create network configurations, troubleshoot issues, and gain practical experience without needing physical hardware. Consider the following:
- Packet Tracer: A powerful network simulator that provides a virtual environment for configuring routers, switches, and other network devices.
- GNS3: Another advanced network simulator that enables users to build virtual networks using real networking operating systems.
- Virtual Labs: Many websites offer virtual labs where you can practice configuring and troubleshooting real network devices and systems.
Other Helpful Resources
In addition to the core study materials and tools, several other resources can enhance your preparation:
| Resource | Description |
|---|---|
| Online Forums | Communities like Reddit, Stack Exchange, and other specialized forums provide insights, tips, and discussions with peers and professionals. |
| Flashcards | Flashcards are great for memorizing terminology, commands, and key concepts. Digital platforms often offer pre-made sets that align with exam objectives. |
| Study Groups | Joining a study group can help reinforce your understanding by discussing difficult concepts with others preparing for the same certification. |
Using a combination of these tools and resources will help you cover both theoretical knowledge and practical skills, ensuring you are well-prepared for the certification challenges ahead.
Exam Taking Tips from Experts
Performing well during a certification test requires more than just knowledge. Effective strategies for managing time, staying focused, and approaching questions with a clear mindset are crucial for success. Expert advice on how to tackle assessments emphasizes planning, efficiency, and maintaining composure throughout the process. These practical tips are designed to help candidates optimize their performance and increase their chances of achieving a favorable result.
Pre-Test Preparation
Successful test-taking begins long before the actual assessment. Proper preparation and mindset play a vital role in ensuring you’re ready to perform at your best.
- Get Rest: A good night’s sleep is essential. Being well-rested helps improve focus and cognitive function during the test.
- Review Key Topics: Focus on revisiting essential concepts and areas of weakness during your final review. Avoid cramming new information.
- Prepare Your Environment: Choose a quiet and comfortable location to take the test. A distraction-free environment will help you maintain concentration.
Effective Time Management During the Test
Managing your time effectively during the test is critical for ensuring you complete all questions without feeling rushed.
- Read Instructions Carefully: Take the time to read each question and its instructions thoroughly. Understanding the requirements will help you avoid costly mistakes.
- Prioritize Questions: Start with the questions that you feel most confident about. This will help build momentum and improve your overall pacing.
- Track Your Time: Be mindful of how much time you’re spending on each section. Don’t dwell too long on difficult questions. Move on and come back if needed.
- Skip and Return: If a question is too challenging, mark it and return to it after answering others. This ensures you don’t get stuck.
Post-Test Reflection

After completing the test, it’s important to reflect on your performance to improve your approach for future assessments. Even if you don’t get immediate feedback, analyzing your experience will help you prepare more effectively next time.
| Strategy | Description |
|---|---|
| Stay Calm | Maintain a calm and positive attitude during the test. Managing stress can help you think more clearly and stay focused. |
| Learn from Mistakes | If possible, review the questions you struggled with after the test. Understanding where you went wrong can prevent similar mistakes in the future. |
| Be Confident | Confidence in your preparation can help you tackle difficult questions with a clearer mind and more assertive answers. |
By incorporating these expert tips into your test-taking routine, you’ll be better equipped to approach the assessment with clarity and confidence, increasing your chances of success.
Commonly Tested Security Technologies

Understanding various technological tools and concepts related to protecting networks and systems is fundamental to success in many technical assessments. The ability to identify, configure, and troubleshoot these technologies is often tested, requiring candidates to demonstrate practical knowledge in applying them effectively. Below are several key technologies frequently evaluated in these types of assessments.
Firewalls and Filtering Devices
Firewalls play a critical role in network security by controlling incoming and outgoing traffic based on predetermined security rules. These devices are often tested to evaluate an individual’s understanding of their configuration, management, and troubleshooting in a network environment.
- Stateful Inspection: Firewalls that track the state of active connections and make decisions based on the context of the traffic.
- Packet Filtering: The process of inspecting packets at the network layer and allowing or blocking traffic based on IP addresses, ports, and protocols.
- Proxy Servers: Used to filter requests and act as intermediaries between a client and the destination server, enhancing security and privacy.
Virtual Private Networks (VPNs)
VPNs enable secure communication over a less secure network, often a public one like the internet. Knowledge of VPN technologies, including the types of VPNs and their configurations, is commonly tested in scenarios related to secure remote access or site-to-site connections.
- IPsec VPN: A protocol suite used to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet in a communication session.
- SSL VPN: Typically used for remote access, this type of VPN uses Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols to secure data transmissions.
- Site-to-Site VPN: A method of connecting two networks securely over the internet, often used by businesses to link their branch offices.
Being familiar with these technologies and their practical applications is essential for excelling in assessments that focus on network protection and the mitigation of security risks. Knowledge of how to implement and configure these tools to safeguard data and systems is a key area of focus for candidates.
Final Review Checklist for Chapter 7
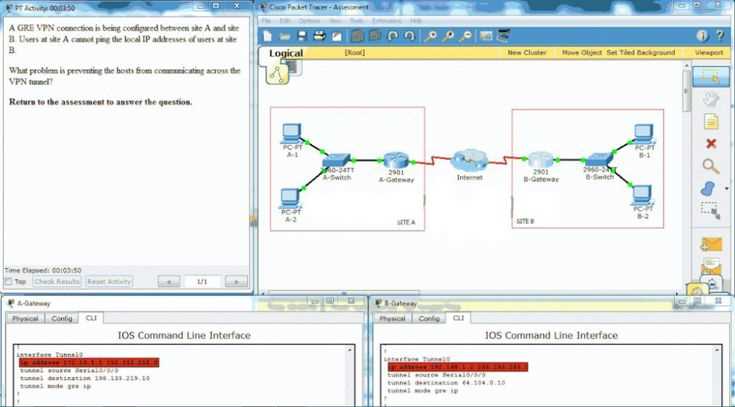
Before completing any technical evaluation, it’s important to ensure that you’ve covered all essential topics and concepts. A final review allows you to consolidate your knowledge and address any areas of uncertainty. This checklist will help you quickly assess whether you’re fully prepared and if there are any last-minute topics to review or practice.
Key Concepts to Verify
- Network Protection Mechanisms: Ensure you understand various methods of protecting networks, including firewalls, intrusion detection systems, and access control lists.
- Encryption Techniques: Review the different types of encryption and their roles in securing communication, such as symmetric vs. asymmetric encryption, SSL/TLS, and IPsec.
- Authentication Methods: Make sure you’re familiar with various authentication protocols and techniques, including multifactor authentication, RADIUS, and TACACS+.
- Virtual Private Networks (VPNs): Double-check your understanding of how VPNs function, and the differences between types such as IPsec and SSL VPNs.
Practical Skills to Test
- Configuration Skills: Have you practiced configuring security devices like firewalls and VPNs? Revisit any configuration steps that seem unfamiliar or challenging.
- Problem-Solving: Work through practice scenarios that involve troubleshooting security issues. Identify potential vulnerabilities and suggest ways to address them.
- Command-Line Knowledge: Review any relevant command-line utilities for configuring and managing network security tools. Ensure you can recall the necessary commands quickly.
By using this checklist, you can effectively gauge your preparedness and feel more confident when it comes time to apply your knowledge. A thorough review ensures that you’re ready to face real-world scenarios with a well-rounded understanding of critical networking concepts.