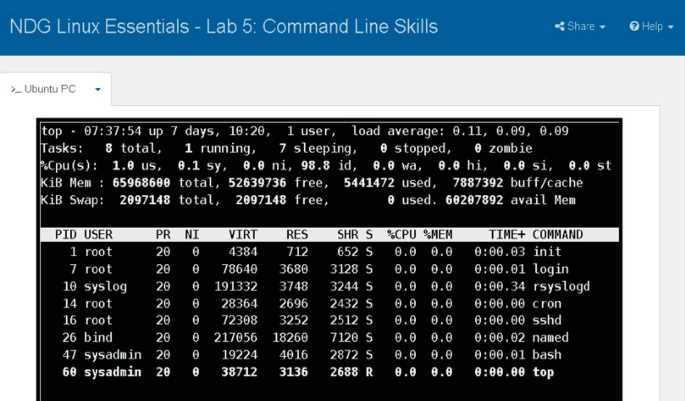
In this section, we will explore key topics related to the management of computer systems. The focus will be on understanding the fundamentals of operating systems, file management, and user control, providing you with essential skills for effective system administration. These concepts are foundational for anyone looking to work with server environments or troubleshoot common system issues.
We will cover a range of practical scenarios, from executing simple commands in the terminal to understanding complex system structures. By the end, you will be able to confidently navigate through system configurations and solve problems that arise in daily operations. Each concept will be explained with clear examples, ensuring that you not only understand the theory but also gain hands-on experience.
Be prepared to dive into topics that require attention to detail and problem-solving skills. Whether you’re looking to enhance your knowledge or get ready for certification, this guide will provide you with the right tools to succeed. Focus on the key areas and practice regularly to strengthen your understanding and mastery of these vital system management skills.
Ndg Linux Essentials Chapter 10 Exam Answers
This section is dedicated to providing a comprehensive overview of the key topics and practical knowledge necessary for mastering system administration tasks. It focuses on understanding the fundamental commands, configurations, and management techniques that form the backbone of any operating system. By thoroughly covering these concepts, this guide helps you prepare for real-world challenges and tests of your technical proficiency.
As you proceed through this material, you will gain insights into essential system functions, file operations, and user management tools. Each concept is explained with practical examples, making complex ideas easier to grasp. The goal is to build your confidence and ensure you are well-prepared to handle various administrative tasks, from managing users to configuring system settings.
In addition to theoretical knowledge, this section emphasizes practical application. You’ll learn how to implement the discussed principles effectively in real environments, ensuring that you’re equipped to handle both routine and advanced tasks. Focus on mastering these areas, as they are key to both your performance in assessments and your ability to solve everyday system management problems.
Understanding Commands and Syntax
Mastering system commands and syntax is the cornerstone of effective administration and troubleshooting. The ability to correctly interpret and execute commands is essential for managing a system, handling files, and configuring settings. This section will walk you through the key principles of command structure, highlighting the importance of accuracy and consistency in each operation.
Key Components of Command Structure
Every command in a terminal consists of several components: the command itself, options (or flags), and arguments. Understanding how each part works is crucial for utilizing the full potential of the command line. The command typically specifies what action should be performed, while options modify the behavior of the command, and arguments define the targets for the command to act upon.
Practical Examples and Common Commands
By working through practical examples, you will become familiar with common commands used to navigate the system, manage files, and control system processes. Each command follows a set syntax that must be adhered to for successful execution. Familiarity with these structures helps in reducing errors and optimizing workflow during system administration tasks.
Key Topics Covered in Chapter 10

This section delves into the critical concepts and tasks necessary for effective system management. It highlights the key areas that form the foundation of administrative practices, focusing on tools and techniques for configuring and maintaining a well-functioning environment. Each topic is designed to enhance your ability to manage resources, troubleshoot issues, and optimize the performance of your system.
Among the key topics covered are user management, file system structure, and permissions, which are essential for controlling access and maintaining security. Additionally, you will explore how to configure system settings, monitor system processes, and manage hardware resources. Mastering these areas ensures a deep understanding of both the theoretical and practical aspects of system administration.
Preparation Tips for Success
Effective preparation is the key to performing well in any technical assessment. Success in this type of evaluation requires more than just memorizing facts–it involves gaining a solid understanding of the concepts and applying them in real-world scenarios. This section will guide you through strategies that will help you approach the material confidently and efficiently.
Focus on Core Concepts
Ensure that you have a strong grasp of the fundamental principles. Spend time revisiting the core topics, such as system configurations, user management, and file systems. Practice using commands and tools regularly to solidify your understanding and improve your ability to work under time constraints.
Simulate Real-Life Scenarios
Prepare by creating practical exercises that simulate common administrative tasks. Hands-on experience is one of the most effective ways to test your knowledge and identify areas that need improvement. Working through real-world examples will help you develop problem-solving skills and ensure you are ready for any challenge that may arise.
Common Mistakes to Avoid in the Exam
When preparing for a technical evaluation, it’s crucial to be aware of the common pitfalls that can undermine your performance. These mistakes often stem from a lack of attention to detail or a misunderstanding of key concepts. Avoiding these errors will not only help you save time but also improve the accuracy of your responses.
Rushing Through Questions
One of the most common mistakes is rushing through questions without carefully considering each one. Taking the time to read the instructions and fully understand what is being asked is vital. Rushed answers often lead to missing important details or making unnecessary errors. Pace yourself and ensure that you are addressing all parts of the question.
Neglecting to Practice Commands
Another frequent mistake is failing to practice the essential commands regularly. Simply reading about commands or reviewing theory is not enough. Hands-on experience is critical for mastering the terminal and ensuring you are comfortable executing commands quickly and correctly under pressure. Practice regularly to build your confidence.
How to Effectively Use the Terminal
Mastering the terminal is an essential skill for system administrators and anyone working with command-line interfaces. The terminal allows you to interact directly with the system, making it a powerful tool for executing tasks, managing files, and configuring settings. Understanding how to use it effectively can significantly improve your productivity and problem-solving abilities.
Basic Commands and Navigation
Before diving into more advanced tasks, it’s important to get comfortable with basic navigation commands. These commands allow you to move around the system, access files, and check directory contents. Below is a table of some common terminal commands for effective navigation:
| Command | Description |
|---|---|
| cd | Change directory |
| ls | List files and directories |
| pwd | Display current directory |
| mkdir | Create a new directory |
| rmdir | Remove an empty directory |
Using Advanced Features for Efficiency
As you become more familiar with basic commands, it’s important to learn how to use advanced terminal features, such as piping, redirection, and job control. These features allow you to combine commands, redirect input and output, and manage processes more efficiently. Mastering these tools will help you execute tasks more quickly and automate repetitive processes.
Detailed Breakdown of Chapter 10 Questions
This section provides a comprehensive analysis of the key questions and topics found in the assessment. Understanding each question’s requirements and knowing how to approach them is critical for success. By breaking down the concepts and providing clear explanations, this guide will help you navigate the material with ease and confidence.
The questions often cover a wide range of topics, from basic system commands to more complex configuration tasks. The following table highlights some of the key areas and typical question formats you may encounter:
| Topic | Key Focus | Typical Question Format |
|---|---|---|
| System Commands | Basic navigation, file operations, and permissions | Which command is used to list files in a directory? |
| File Management | Creating, modifying, and removing files and directories | How would you create a new directory? |
| Permissions | Understanding user and group permissions | What command would you use to change file permissions? |
| Process Management | Monitoring and managing system processes | Which command is used to check the running processes? |
| System Configuration | Configuring system settings and services | How do you restart a system service? |
By reviewing these areas and practicing the corresponding tasks, you will be better prepared to tackle any question related to these topics. It’s important to not only understand the theory but also to be familiar with practical applications and command syntax.
Practical Examples to Master System Skills
One of the most effective ways to strengthen your system management skills is through hands-on practice. By working through real-world examples, you gain a deeper understanding of the core concepts and commands necessary for effective administration. This section will guide you through several practical exercises to help you build and refine your expertise.
Managing Files and Directories
File and directory management is a fundamental aspect of system operations. Below is a practical example to help you get comfortable with creating, modifying, and deleting files and directories using terminal commands:
Example Task: Create a new directory, add files to it, and then delete the directory when you’re done.
Steps:
- Use
mkdirto create a directory. - Use
touchto create files within that directory. - Use
rmto delete files andrmdirto remove the directory.
Managing User Permissions
Understanding how to manage user access and permissions is essential for system security. Below is a practical example of how to modify file permissions for different users:
Example Task: Change the permissions of a file to allow only the owner to read and write, while others can only read it.
Steps:
- Use
chmodto modify permissions. For example,chmod 644 filenamewill give read and write permissions to the owner and read-only permissions to others. - Check permissions using the
ls -lcommand.
By practicing these tasks regularly, you will gain confidence and proficiency in using system commands efficiently and accurately.
Focus Areas for the Assessment
To ensure optimal preparation for the assessment, it’s essential to focus on the key areas that are most likely to appear in the questions. These areas typically cover a broad range of fundamental skills, from basic system operations to more advanced configurations. Understanding these focus areas will help you allocate your study time effectively and improve your overall performance.
Key System Commands
One of the most critical focus areas involves mastering the fundamental system commands. You should be able to navigate the system, manage files and directories, and manipulate file permissions efficiently. Commands such as cd, ls, chmod, and mkdir are integral for daily system administration tasks. Being comfortable with these will enable you to answer a wide range of questions related to system navigation and file management.
Process and Service Management
Understanding how to manage system processes and services is another major area of focus. This includes being able to view, start, stop, and configure system processes. Tools like ps, top, and systemctl are crucial for monitoring and controlling system activities. Questions in this area often involve troubleshooting process-related issues or restarting services, so familiarity with these commands is essential.
Explaining Key Concepts in Depth

Understanding core system concepts is essential for any user working in an administrative role. These concepts form the foundation of your ability to interact with the operating system effectively. In this section, we’ll dive into some of the most important ideas that underpin system management, from user permissions to process handling.
File System Hierarchy

The file system hierarchy is a key concept that defines how files and directories are organized on the system. Understanding the structure is crucial for navigation, file management, and troubleshooting. Below are the primary elements of the system’s file hierarchy:
- /root: The root directory, where the system’s core files are stored.
- /home: User-specific directories for storing personal files.
- /bin: Essential binary executables needed for system operation.
- /etc: Configuration files for the system and installed applications.
- /var: Files that change in size and content, such as logs and temporary files.
Familiarity with this structure will help you navigate the system efficiently and ensure that important files and configurations are easily accessible.
Permissions and Ownership
Understanding how permissions and ownership work is crucial for ensuring that only authorized users have access to sensitive data. Every file or directory has associated permissions that define which users can read, write, or execute it. These permissions are categorized as follows:
- Read (r): Grants the ability to view the content of the file or list the contents of a directory.
- Write (w): Allows modification of the content of a file or the addition/removal of files in a directory.
- Execute (x): Grants permission to run a file as a program or script.
Users and groups are assigned ownership of files, and permissions are granted based on these ownership levels. Understanding how to modify permissions using commands like chmod and chown is essential for maintaining system security and functionality.
Process Management

Managing system processes is another critical skill. A process refers to an active program or task running on the system. The ability to monitor and control processes ensures the smooth operation of the system. Key concepts in process management include:
- Foreground and Background Processes: Processes can run in the foreground (actively using the terminal) or in the background (running without interacting with the terminal).
- Process IDs (PID): Every process is assigned a unique PID, which is used to track and control it.
- Signals: Signals are used to communicate with running processes, such as sending a
killsignal to terminate a process.
Tools like ps and top allow you to monitor the status of processes, while kill can be used to terminate processes that are unresponsive or causing issues.
By mastering these foundational concepts, you will be able to perform tasks more efficiently and with greater confidence in your role as a system administrator.
What You Need to Know About Permissions

Permissions are an essential part of any system as they govern who can access, modify, and execute specific files and directories. Understanding how permissions work ensures the security and proper functionality of the system. Without the correct permission settings, users or processes could either be blocked from performing necessary tasks or, conversely, gain unauthorized access to sensitive information. This section covers the core concepts of file permissions and how they impact system administration.
Understanding the Permission Model
In a typical system, every file and directory has associated permissions that define how users can interact with them. These permissions are represented in a three-character format, where each character represents one of the following actions:
| Permission | Meaning |
|---|---|
| r | Read: Permission to view the content of a file or list the contents of a directory. |
| w | Write: Permission to modify the content of a file or add/remove files in a directory. |
| x | Execute: Permission to run a file as a program or script. |
The three positions represent the owner, the group, and all other users. For example, the permission string rwxr-xr-- indicates that the owner has full access, the group has read and execute access, and others have read-only access.
Modifying Permissions
To modify file and directory permissions, administrators use the chmod (change mode) command. The permissions can be set using either symbolic notation (letters) or numeric notation (numbers). The numeric system assigns a value to each permission:
| Permission | Numeric Value |
|---|---|
| Read (r) | 4 |
| Write (w) | 2 |
| Execute (x) | 1 |
For example, to give full permissions to the owner, and read and execute permissions to others, the numeric value would be 755. You can use the following command to apply this:
chmod 755 filenameUnderstanding how to modify permissions effectively ensures that only authorized users can access or modify critical system files.
Working with Filesystems and Directories
Effective management of files and directories is a critical skill for system administrators. Understanding how the system organizes and stores data is essential for both troubleshooting and efficient file management. The filesystem is the structure that allows users to store, retrieve, and organize their files. It consists of directories and files, each with their own set of attributes and permissions.
In any operating environment, directories play a key role in maintaining an organized file structure. They allow users to group related files together, creating a logical and easily navigable system. Filesystems provide a way to access, modify, and store data, but knowing how to interact with these systems using the proper tools can enhance productivity and security.
To manage directories and files, commands like ls (list), cd (change directory), and mkdir (make directory) are commonly used. The ls command shows the contents of a directory, while cd changes the current working directory. If a directory doesn’t exist, the mkdir command is used to create one.
Another key element in filesystem management is understanding file paths. File paths can either be absolute, starting from the root directory (e.g., /home/user/documents), or relative, which are based on the current directory (e.g., documents/file.txt). Mastering the use of these paths is essential for effective navigation within the system.
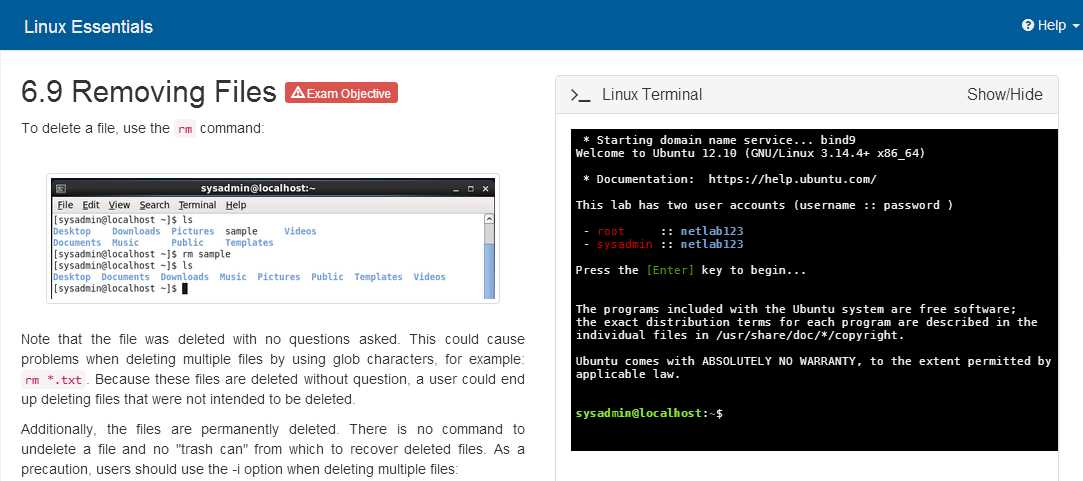
In addition to the basic navigation commands, there are a number of tools that help manage files and directories, such as cp (copy), mv (move), and rm (remove). These commands allow users to manipulate files and directories, ensuring that data is stored in the correct location and that unnecessary files are removed to keep the system organized.
Understanding the structure of the filesystem, along with the commands and tools used to interact with it, is an essential skill for anyone working with data management or system administration. This knowledge ensures smooth operation and better control over the file storage environment.
Managing Users and Groups
Managing users and groups is a fundamental aspect of system administration. These components allow administrators to control access to system resources, ensuring that only authorized individuals can perform specific actions. By managing user accounts and groups efficiently, it becomes easier to organize users, implement security measures, and maintain overall system stability.
Users represent individuals or entities who access and interact with the system. Each user has a unique identity, defined by a username and a corresponding user ID (UID). They also have a home directory, where personal files are stored, and a set of permissions that determine what actions they can perform.
Groups are collections of users who share similar privileges. By grouping users together, administrators can apply the same set of permissions to multiple users at once. This simplifies access control and improves efficiency when managing large numbers of users.
Creating and Managing Users
To create a new user, administrators can use the useradd command, followed by the desired username. For example:
useradd johnThis will create a user account for “john.” Administrators can also specify additional attributes such as the user’s home directory or default shell. After creating a user, the passwd command can be used to set or change the user’s password:
passwd johnTo delete a user, the userdel command is used:
userdel johnWorking with Groups
Groups are created using the groupadd command, followed by the group name:
groupadd adminOnce a group is created, users can be added to the group using the usermod command. For example, to add the user “john” to the “admin” group:
usermod -aG admin johnTo view which groups a user belongs to, the groups command can be used:
groups johnManaging user and group permissions is an essential part of system administration. It helps ensure that resources are used effectively while maintaining security and privacy. By organizing users into groups and managing access control with the appropriate tools, system administrators can efficiently oversee the system’s users and ensure a smooth and secure environment.
Networking Essentials to Study
Understanding network configuration and management is essential for working with any system. Proper networking allows devices to communicate with one another and access shared resources, making it an important aspect of system administration. Whether you’re setting up a small office network or working with large-scale infrastructure, mastering networking fundamentals is crucial to ensure efficient data transfer and secure communication.
In this section, we’ll cover the key topics and commands that are vital for understanding and managing network connections. Knowing how to configure IP addresses, troubleshoot connectivity issues, and optimize network performance is fundamental for any system administrator or network professional.
IP Addressing and Subnetting
One of the first concepts to grasp is how devices are identified on a network. This is done through IP addresses, which serve as unique identifiers for devices on a local or remote network. Understanding both IPv4 and IPv6 addressing is essential for configuring and managing networks.
- IPv4 addresses consist of four octets (32 bits) separated by dots, like
192.168.1.1. - IPv6 addresses use 128 bits and are represented as eight groups of four hexadecimal digits.
Subnetting is another crucial concept for network management. It involves dividing a larger network into smaller sub-networks to improve efficiency and security. Knowing how to calculate subnet masks and the range of IP addresses within a subnet is essential.
Network Configuration Tools
There are several tools and commands used to configure and troubleshoot network settings. Some of the most commonly used tools include:
ifconfig: Displays network interface configurations and allows for the configuration of IP addresses.ip: A more modern command used to configure network interfaces, assign IP addresses, and display routing tables.ping: Tests network connectivity by sending packets to a specified IP address or hostname.netstat: Displays network connections, routing tables, and interface statistics.
Routing and DNS Configuration
Routing determines how data is transferred between networks. Understanding how routers function and how to configure static and dynamic routing protocols is key to ensuring proper data flow. The route command is often used to add or modify static routes.
DNS (Domain Name System) is essential for resolving human-readable domain names to IP addresses. Understanding how to configure DNS settings and troubleshoot DNS issues is necessary for ensuring that systems can access websites and other services using domain names instead of IP addresses.
Firewall and Security
Managing firewall settings is an important aspect of network security. Firewalls control the flow of network traffic based on predefined security rules. Common firewall tools include iptables and the more modern firewalld. It’s essential to understand how to configure and maintain firewalls to protect against unauthorized access.
- Setting up inbound and outbound rules to block or allow traffic.
- Managing NAT (Network Address Translation) for routing traffic between different networks.
By studying these networking essentials, you’ll gain the skills needed to set up, configure, and troubleshoot network connections. Mastering these concepts will provide a strong foundation for managing and securing networked systems effectively.
How to Configure System Services
Configuring system services is an essential task for system administrators. These services control various aspects of the system, such as network connectivity, system logging, and application management. Proper configuration ensures that critical services are running as expected, providing the necessary functionality for both users and applications.
In this section, we will focus on how to manage and configure different types of system services, including how to start, stop, enable, and disable services. We will also cover service monitoring and how to troubleshoot service-related issues to maintain optimal system performance.
Managing System Services

System services are typically managed through a service manager that allows administrators to control which services are running on the system. The most common service management tools include systemd and init.d, which provide commands for controlling the state of system services.
- systemd: The modern and default init system on most systems. It uses
systemctlto manage services. - init.d: The older system used for managing services, still found on some legacy systems.
Here are some basic commands for managing services using systemctl:
systemctl start: Starts a service.systemctl stop: Stops a service.systemctl restart: Restarts a service to apply changes.systemctl enable: Enables a service to start at boot time.systemctl disable: Disables a service from starting at boot time.systemctl status: Displays the status of a service (active, inactive, etc.).
Service Configuration Files
Many system services are configured via text files located in specific directories, such as /etc/systemd/system/ for systemd services. These configuration files contain the settings and parameters that control how a service operates.
- Service Files: These files define how a service is started, stopped, and configured. They are usually stored in
/etc/systemd/system/or/lib/systemd/system/. - Configuration Files: Many services have their own configuration files that control parameters specific to the service, such as networking settings or user permissions. For example,
/etc/ssh/sshd_configis used to configure the SSH service.
After editing a service’s configuration file, you may need to reload the service manager to apply the changes. You can do this using the following command:
systemctl daemon-reloadService Monitoring and Troubleshooting
Monitoring the health and performance of system services is essential to ensure that they are running smoothly. Common tools used for monitoring include journalctl and top, which allow administrators to check logs and resource usage.
journalctl -u: Displays logs for a specific service.top: Displays real-time resource usage, including CPU and memory consumption by running services.systemctl is-active: Checks if a service is active.systemctl is-enabled: Checks if a service is enabled to start at boot.
If a service is not functioning as expected, checking the logs is often the first step in troubleshooting. Logs can provide error messages and detailed information about what may be causing the issue. Additionally, restarting the service using systemctl restart may help resolve transient problems.
Automating Service Management
For efficient system administration, automating service management tasks can save time and reduce errors. Tools like cron and systemd timers can be used to schedule service checks, restarts, or other maintenance tasks.
- cron: A job scheduler that allows administrators to schedule periodic tasks such as restarting services or clearing logs.
- systemd timers: A more advanced tool for scheduling tasks that integrates with the
systemdsystem.
By properly managing and configuring system services, administrators ensure that the system operates smoothly and securely. A good understanding of service management is essential for any administrator looking to maintain a healthy, stable environment.
Exam Strategies to Improve Your Score
Achieving a high score in any assessment requires more than just basic knowledge; it involves strategic preparation and efficient test-taking techniques. Understanding the content is essential, but knowing how to approach the test itself can make a significant difference in your performance. The following strategies will help you maximize your chances of success and improve your overall score.
Effective Study Techniques
When preparing for an assessment, it’s crucial to use study methods that not only help you retain information but also allow you to apply it effectively. Here are some tips to enhance your study process:
- Active Recall: Test yourself regularly on the material to strengthen memory retention. This technique helps you retrieve information more easily during the assessment.
- Spaced Repetition: Review topics at increasing intervals over time. This technique ensures long-term retention and helps you avoid cramming.
- Practice with Mock Tests: Simulate exam conditions by taking practice tests. This will help you get comfortable with the format and timing, improving your confidence.
Time Management During the Test
Time management is a critical aspect of any assessment. Efficiently allocating your time will allow you to complete all sections without feeling rushed. Consider the following strategies:
- Prioritize Easy Questions: Start by answering the questions you find easiest. This will help build momentum and secure quick points.
- Allocate Time for Each Section: Before you begin, review the test and allocate a specific amount of time to each section. Stick to this schedule to avoid spending too much time on any one question.
- Skip and Return: If you get stuck on a question, skip it and return to it later. This will prevent you from losing valuable time and energy on one difficult item.
Focus on Keywords and Key Concepts
When reading each question, pay close attention to the key terms and concepts. Often, assessments will include clues within the question that point to the correct answer. Look for:
- Action Words: Words like “define,” “explain,” “compare,” or “contrast” indicate the type of response expected.
- Important Terms: Make sure you understand the terminology used in the question. Misinterpreting these can lead to incorrect answers.
Stay Calm and Focused
Staying calm during the test is crucial to maintaining focus and avoiding mistakes. Here are some tips to help manage test anxiety:
- Take Deep Breaths: If you start to feel stressed, take a few deep breaths to relax and refocus.
- Stay Positive: Keep a positive mindset throughout the test. Negative thoughts can cloud your judgment and hinder performance.
- Review Your Answers: If time allows, review your answers before submitting the test. Look for any mistakes or questions you may have missed.
By following these strategies, you can approach your assessment with confidence and improve your chances of success. Effective preparation, good time management, and a calm mindset will help you achieve the best possible outcome.