
In the world of information technology, a strong grasp of key concepts and protocols is crucial for anyone looking to excel in the field. Whether you’re starting your journey or preparing to solidify your expertise, understanding the underlying principles is essential for tackling real-world challenges. The knowledge required for success can seem complex at first, but with the right approach, anyone can grasp the core elements and apply them effectively.
To help you succeed, we’ve compiled a guide focused on the critical topics that are often covered in assessments. These subjects are the building blocks of modern communication systems, from data transfer to security measures. By focusing on mastering these areas, you’ll be able to demonstrate your skills with confidence and clarity. As you prepare, it’s important to recognize not only the theoretical aspects but also the practical applications of the knowledge gained.
Each section will explore a different facet of this field, providing insights into what is tested and how to best approach the material. Understanding the core principles of system design, connectivity, and troubleshooting will help you achieve your goals. Emphasizing real-world scenarios will also allow you to connect the dots between theory and practice, ensuring you’re ready for any challenge ahead.
Networking Essentials Final Exam Answers
When preparing for assessments in this field, it’s important to focus on the fundamental concepts that test your ability to apply theoretical knowledge in practical scenarios. Mastering key topics, from system design to troubleshooting techniques, ensures that you’re equipped to handle any situation that may arise. Understanding the relationship between various protocols, devices, and topologies forms the backbone of effective communication systems.
In this section, we will cover a variety of questions that assess the core principles you’ve studied. By analyzing these key areas, you can refine your understanding and approach, making sure you’re able to not only recall information but also apply it confidently. These subjects typically include IP addressing, routing protocols, device configuration, and network security measures. With a clear grasp of each concept, you’ll be well-prepared to demonstrate your knowledge and problem-solving abilities under test conditions.
Successfully navigating through questions related to these topics requires both theoretical insight and hands-on practice. It’s essential to review each concept carefully, ensuring that you can explain how different technologies interact and why certain solutions are more effective than others. By focusing on clarity and real-world applications, you’ll gain a comprehensive understanding of the material and increase your readiness for any challenge.
Key Topics in Networking Essentials Exam
To succeed in this field, it’s crucial to understand the core concepts that lay the foundation for modern communication systems. These key areas cover everything from basic infrastructure to complex problem-solving strategies. Gaining a deep knowledge of these topics allows you to not only grasp theoretical concepts but also understand their real-world applications.
Core Networking Concepts
In this section, focus on the essential building blocks that form any network system. Topics include the design of network topologies, protocols that facilitate communication, and the devices that enable connectivity. Understanding these components will allow you to troubleshoot and optimize systems effectively.
Configuration and Troubleshooting Skills
The ability to configure devices such as routers and switches and troubleshoot network issues is a key area of focus. Knowing how to diagnose and fix common problems is vital for any professional in this field. Hands-on experience and a clear understanding of different configurations will be essential to pass any assessment.
| Topic | Description |
|---|---|
| IP Addressing | Learn about IP address structures, subnetting, and how to assign addresses for efficient communication. |
| Routing Protocols | Study the different protocols that help direct data traffic between devices in a network. |
| Network Security | Understand key security measures, including encryption, firewalls, and access control to protect data. |
| Device Configuration | Learn how to configure routers, switches, and other devices to establish a functional network. |
How to Prepare for Networking Essentials
Preparation for any technical assessment in the field of communication systems requires a structured approach. The process involves gaining a deep understanding of core principles and practicing their application in real-world scenarios. Success comes from both theoretical study and hands-on experience, ensuring that you’re ready to tackle any challenge with confidence.
Building a Strong Foundation
Begin by mastering the fundamental concepts that form the backbone of this field. This includes understanding basic protocols, the architecture of devices, and how data travels through different layers. Without a solid grasp of these core elements, more advanced topics will be difficult to understand. Start by reviewing textbooks, online resources, and video tutorials to reinforce your knowledge.
Practical Application and Practice
Next, focus on applying what you’ve learned through practical exercises. Set up your own test environment where you can experiment with configuring devices, troubleshooting issues, and implementing network protocols. Hands-on practice will not only strengthen your skills but will also give you the confidence to apply theoretical knowledge in real-world situations.
Common Networking Terms You Should Know
In the world of communication systems, there are several key terms that you must become familiar with in order to navigate the field effectively. These terms represent the building blocks of the technology that powers modern digital communication, and understanding them is essential for both troubleshooting and optimization. Mastering these concepts ensures you can work confidently with the equipment and protocols that make up any digital infrastructure.
Key Communication Protocols
Protocols are the set of rules that govern data exchange between devices. Familiarity with these rules is vital for configuring systems and ensuring smooth operation. Some of the most widely used protocols include TCP/IP, which governs data transmission across networks, and HTTP, the protocol that facilitates web browsing. Other protocols like DNS and FTP are also crucial for managing domain names and file transfers, respectively.
Devices and Hardware Components
In any digital setup, devices such as routers, switches, and hubs play critical roles in directing and managing data flow. Routers handle traffic between different networks, while switches direct data within a local network. Hubs, though less common in modern setups, broadcast data to all devices on a network. Understanding the function and interaction of these devices is essential for network configuration and management.
Understanding Network Topologies and Types
One of the fundamental aspects of designing and managing a system is understanding how devices are connected to one another. The structure in which these devices communicate, known as a topology, plays a significant role in determining the efficiency, scalability, and fault tolerance of a network. Different topologies offer distinct advantages and limitations, making it essential to select the most appropriate one based on the specific needs of the system.
Common Topology Types
There are several popular topologies that are commonly used in different environments, each suited to particular use cases and sizes. Understanding the characteristics of each will help you design and troubleshoot systems more effectively. Some of the most common include:
- Bus Topology: A single central cable connects all devices in a linear fashion, ideal for smaller networks but less scalable and prone to congestion.
- Star Topology: All devices are connected to a central hub or switch, offering high reliability and ease of management. This is one of the most common topologies for larger systems.
- Ring Topology: Devices are connected in a closed loop, with data passing in one direction. It’s simple but can be vulnerable if a single connection fails.
- Mesh Topology: Every device is connected to every other device, providing excellent fault tolerance but requiring more cabling and management.
Choosing the Right Topology
The choice of topology depends largely on the size of the system, the required performance, and the available budget. For smaller systems, simpler topologies like bus or ring may be sufficient, while larger, more complex setups might benefit from star or mesh configurations. It’s important to also consider factors such as ease of expansion, fault tolerance, and maintenance costs when making a decision.
Essentials of IP Addressing and Subnetting
Understanding how devices communicate over a network requires a solid grasp of IP addressing and subnetting. These are fundamental skills for organizing and managing a network effectively. Properly configured IP addresses allow devices to identify and communicate with one another, while subnetting ensures that traffic flows efficiently within a network. Mastering these concepts enables smooth data transfer, optimal performance, and better management of network resources.
IP addresses are divided into classes, each serving a different purpose depending on the size and requirements of the network. Subnetting, on the other hand, helps in segmenting larger networks into smaller, more manageable subnets, improving security and performance. By understanding how to divide address spaces and calculate subnet masks, you can optimize network infrastructure and troubleshoot issues with ease.
| IP Class | Range of Addresses | Default Subnet Mask |
|---|---|---|
| Class A | 1.0.0.0 to 127.255.255.255 | 255.0.0.0 |
| Class B | 128.0.0.0 to 191.255.255.255 | 255.255.0.0 |
| Class C | 192.0.0.0 to 223.255.255.255 | 255.255.255.0 |
| Class D (Multicast) | 224.0.0.0 to 239.255.255.255 | N/A |
| Class E (Reserved) | 240.0.0.0 to 255.255.255.255 | N/A |
Router and Switch Configuration Basics
Configuring routers and switches is an essential skill for anyone working with modern communication systems. These devices form the backbone of any network, directing data between devices and segments, and ensuring smooth traffic flow. Understanding the basic configuration steps for both routers and switches is crucial for setting up a secure and efficient infrastructure. Proper configuration enables reliable connections, secure data transfer, and optimized performance.
Router Configuration Essentials
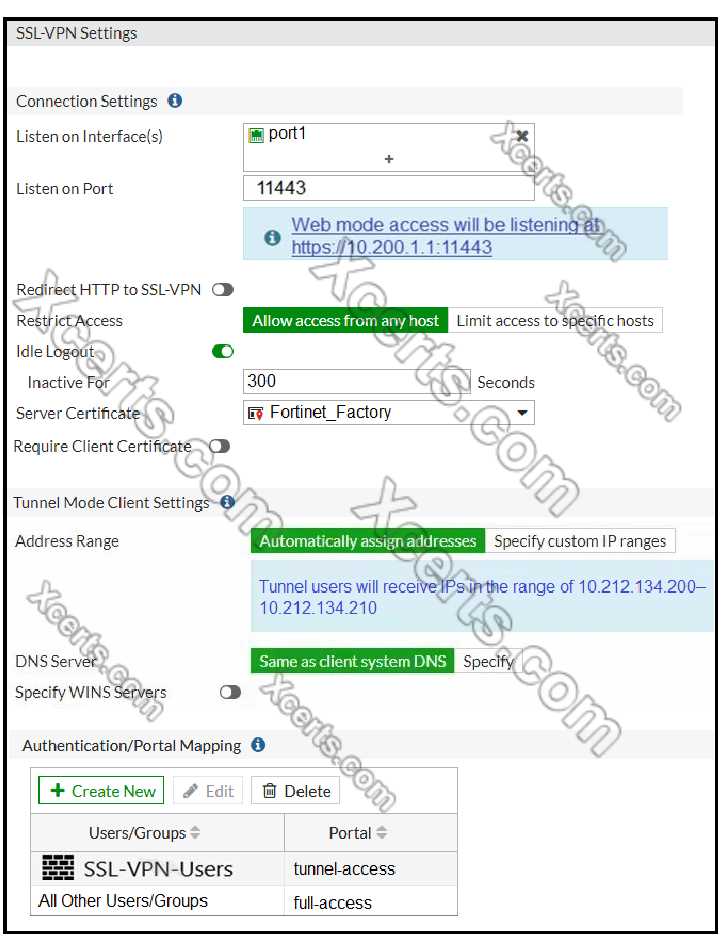
Routers are responsible for directing data between different networks. They perform a critical role in managing traffic, ensuring that data packets reach the correct destination. Basic router configuration involves setting up interfaces, IP addresses, and routing protocols. Below are the key steps for configuring a router:
- Access Router CLI: Connect to the router via console cable or SSH, depending on the device setup.
- Assign IP Addresses: Set up the IP addresses for the router’s interfaces to allow communication with connected devices.
- Configure Routing Protocols: Select and configure routing protocols (such as OSPF or EIGRP) to manage data paths across different networks.
- Save Configuration: Ensure that your settings are saved to the startup configuration to persist after reboots.
Switch Configuration Essentials
Switches operate within local networks, directing data packets between devices on the same network. Basic switch configuration involves setting up VLANs, assigning ports to specific VLANs, and enabling necessary protocols. The following steps outline the key tasks for configuring a switch:
- Access Switch CLI: Connect to the switch via console or SSH to begin configuration.
- Set Up VLANs: Define Virtual Local Area Networks (VLANs) to segment network traffic and improve security.
- Assign Ports to VLANs: Map switch ports to the appropriate VLANs to group devices logically.
- Enable Spanning Tree Protocol (STP): Prevent network loops by configuring STP on switches.
- Save Configuration: Like routers, it’s essential to save the configuration on the switch to retain changes after rebooting.
TCP/IP Model and Its Components
The TCP/IP model is the foundational framework that governs how data is transmitted across different types of communication systems. This model defines the rules and protocols that allow devices to communicate effectively, ensuring reliable and secure data exchange. Understanding the layers and components of this model is essential for anyone working with digital communication systems. Each layer in the model has a distinct role, from the physical transmission of data to ensuring that it reaches its destination correctly.
Layers of the TCP/IP Model
The TCP/IP model consists of four key layers, each of which handles specific tasks related to data transfer. These layers work together to ensure that data is sent, routed, and received accurately. Below is a breakdown of each layer:
- Application Layer: This layer interfaces with end-user applications, providing protocols for tasks such as web browsing, email, and file transfers. Protocols like HTTP, FTP, and SMTP operate at this layer.
- Transport Layer: Responsible for ensuring reliable data transfer, this layer manages end-to-end communication. Protocols like TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) function here.
- Internet Layer: This layer is responsible for addressing and routing data packets between devices across different networks. IP (Internet Protocol) is the key protocol operating at this layer.
- Network Access Layer: The lowest layer in the TCP/IP model, it deals with the physical transmission of data over the network. This layer manages hardware interfaces like Ethernet and Wi-Fi.
Key Protocols in the TCP/IP Model
Each layer of the TCP/IP model relies on specific protocols to perform its functions. These protocols ensure that data is transmitted efficiently and accurately across networks. Some of the most important protocols include:
- IP (Internet Protocol): Responsible for addressing and routing packets of data across different networks.
- TCP (Transmission Control Protocol): Provides reliable data transmission by ensuring packets are received in the correct order and without errors.
- UDP (User Datagram Protocol): Unlike TCP, UDP allows for faster but less reliable transmission, typically used for real-time applications.
- HTTP (Hypertext Transfer Protocol): The protocol used for transferring web pages and resources over the internet.
- FTP (File Transfer Protocol): Used for transferring files between devices on a network.
What to Expect in the Exam
When preparing for any certification assessment, understanding the format and types of questions you’ll encounter is crucial. This section aims to provide insight into what to expect during the test, helping you focus your study efforts and prepare effectively. The assessment typically evaluates your understanding of fundamental concepts, practical skills, and problem-solving abilities related to network systems and configurations.
Types of Questions
In this assessment, you can expect a mix of question types designed to test both your theoretical knowledge and hands-on skills. The following question formats are commonly included:
- Multiple Choice Questions: These questions will test your understanding of key concepts. You’ll need to select the correct answer from several options.
- Fill-in-the-Blank: These questions may require you to complete statements with the appropriate terms, ensuring you grasp specific terminology and definitions.
- True or False: You’ll be asked to evaluate statements and determine whether they are correct or incorrect based on your knowledge.
- Practical Scenarios: Some questions will present real-world network situations, where you’ll need to choose the best solution or diagnose issues.
Key Areas of Focus
The assessment will likely cover several important topics. It’s essential to familiarize yourself with the following areas:
- Device Configuration: Understanding how to configure routers, switches, and other devices is critical.
- Addressing and Subnetting: Be prepared to calculate and configure IP addresses and subnet masks correctly.
- Routing Protocols: Know the basic principles of routing, including dynamic and static protocols.
- Network Security: Expect questions related to security measures and best practices for protecting a network.
- Diagnostic Tools: Familiarize yourself with various tools used to troubleshoot and monitor networks.
Study Tips for Networking Essentials Exam
Effective preparation for any certification test requires a structured approach that combines both theoretical learning and practical application. This section provides useful study strategies to help you succeed in your upcoming assessment. By focusing on key areas and using the right resources, you can enhance your understanding and build the skills needed to tackle the challenges you’ll face.
Key Strategies for Preparation
To make the most of your study sessions, consider these tips:
- Understand the Core Concepts: Focus on understanding fundamental principles rather than memorizing facts. A solid grasp of the core topics will help you better apply your knowledge during the test.
- Use Practice Tests: Taking practice exams is one of the best ways to familiarize yourself with the format and identify areas where you need more practice.
- Review Study Guides: Use well-structured study materials, including books, video lessons, and online resources, to reinforce your understanding of the concepts.
- Join Study Groups: Collaborating with peers can help clarify difficult topics and expose you to different perspectives and study methods.
Time Management Tips
Managing your time effectively is crucial during your preparation. Follow these strategies to make the most of your study time:
- Set a Study Schedule: Create a study timetable that allows you to review all topics without cramming. Break down your study sessions into manageable chunks.
- Prioritize Weak Areas: Spend more time on topics that you find challenging. Focus on understanding difficult concepts rather than reviewing material you are already comfortable with.
- Stay Consistent: Regular study sessions are more effective than sporadic, last-minute cramming. Consistency is key to retaining information.
Common Pitfalls in Networking Concepts
When preparing for any certification or practical application in the field of network systems, it’s important to be aware of common mistakes that can hinder understanding and implementation. These errors often arise from misinterpretation of key principles or confusion between similar concepts. Identifying and addressing these pitfalls can ensure a clearer understanding and better performance in both theoretical and practical settings.
Below are some of the most frequently encountered challenges that students and professionals face when studying network configurations and protocols:
Misunderstanding IP Addressing
One of the most common errors is misunderstanding how IP addresses work, particularly when it comes to subnetting and addressing schemes. It’s essential to fully comprehend how addresses are divided into classes and how subnet masks affect network design. Confusing IPv4 with IPv6, or miscalculating subnet boundaries, can lead to errors in network setup and communication issues.
Confusing Routing Protocols
Another common mistake involves mixing up routing protocols. Dynamic and static routing each have their use cases, and confusing their configurations can cause network instability. For example, confusing RIP (Routing Information Protocol) with OSPF (Open Shortest Path First) or BGP (Border Gateway Protocol) can lead to improper network traffic flow and routing loops.
Overlooking Security Measures
Many tend to underestimate the importance of security when setting up a network. Failing to implement proper security protocols such as firewalls, VPNs, or encryption can leave a system vulnerable to attacks. Network security should always be a primary concern, and ignoring it can lead to severe data breaches or loss of sensitive information.
Ignoring Physical Layer Connections
While it’s easy to focus on higher-level configurations like IP addressing and routing, neglecting the physical layer can lead to connectivity issues. Incorrect cabling, poor cable management, or improper hardware configurations can hinder performance, even if the logical network is configured correctly.
By being aware of these potential pitfalls and thoroughly understanding the underlying principles, you can avoid these mistakes and ensure a smoother experience when working with network systems.
Protocols and Their Functions in Networking
In any system that involves data communication, protocols play a crucial role in ensuring that information is transmitted and received correctly. These sets of rules and conventions enable devices to communicate with one another effectively, whether they are on the same local network or connected across vast distances. Understanding how each protocol functions and the purpose it serves is fundamental to configuring and maintaining robust communication systems.
Key Protocols in Data Communication
There are several protocols, each designed for specific tasks within a network. Some protocols govern the establishment of connections, while others are responsible for securing data or optimizing the flow of information. Below is an overview of some of the most widely used protocols and their primary functions:
| Protocol | Function |
|---|---|
| HTTP (HyperText Transfer Protocol) | Used for transferring web pages and multimedia content over the internet, allowing clients to request and receive web resources. |
| TCP (Transmission Control Protocol) | Ensures reliable, ordered delivery of data between devices by establishing a connection and managing data flow. |
| IP (Internet Protocol) | Responsible for routing data packets between devices on different networks and assigning unique IP addresses to ensure accurate delivery. |
| DNS (Domain Name System) | Translates human-readable domain names (like www.example.com) into machine-readable IP addresses, enabling proper communication between devices. |
| SMTP (Simple Mail Transfer Protocol) | Used to send and route emails across networks, ensuring reliable email delivery between clients and servers. |
How Protocols Interact in a Network
These protocols often work together to ensure smooth communication between devices. For example, when you access a website, your browser uses HTTP to send a request, TCP ensures that the data is transferred reliably, and DNS helps resolve the domain name to an IP address. The seamless interaction between these protocols makes it possible for complex tasks to be completed in the background, often without the user even realizing it.
By understanding these protocols and how they contribute to data communication, network administrators can better troubleshoot issues, optimize systems, and ensure that devices communicate effectively.
Hands-on Practice for Networking Success
Practical experience is essential for mastering any technical skill, especially when it comes to managing communication systems. While theoretical knowledge forms the foundation, real-world application allows individuals to grasp complex concepts and troubleshoot effectively. Engaging in hands-on practice helps reinforce learning and builds confidence when handling different scenarios in system management.
To succeed in this field, it’s crucial to simulate different environments and experiment with various configurations. Setting up and managing networks, configuring devices, and resolving common issues offer invaluable learning opportunities. By immersing yourself in practical exercises, you can better understand how various components interact and develop problem-solving skills that are crucial for success.
Additionally, utilizing simulation tools or building your own home lab with routers, switches, and firewalls will allow you to practice in a controlled environment. This practice will enhance your technical ability and prepare you for challenges in real-world settings.
Analyzing Exam Questions and Answers
When preparing for an assessment, understanding the structure and intent behind each question is just as important as knowing the material. Exam questions are designed to test both theoretical knowledge and practical understanding, and analyzing them carefully can significantly improve your performance. By breaking down questions, identifying key concepts, and interpreting them accurately, you can ensure you provide the most relevant and well-structured responses.
Identifying Key Information in Questions
One of the first steps in tackling any question is to identify the key information. This includes recognizing what the question is asking for, whether it’s a factual recall, a concept explanation, or a scenario-based problem. Pay attention to terms like “define,” “compare,” “explain,” and “describe,” as they give you clues about the type of answer required. Understanding these cues helps you avoid unnecessary elaboration and focus on what is truly important.
Understanding Common Traps in Multiple Choice Questions
Multiple choice questions often present subtle traps designed to test your attention to detail. Be cautious of answers that seem almost right but are slightly off, such as options that include small factual errors or misleading terminology. Carefully analyze each choice and eliminate the obviously incorrect answers first. This process increases your chances of selecting the correct one, even if you are unsure at first.
Understanding OSI Model Layers
The OSI model is a conceptual framework that standardizes how different systems communicate over a network. It divides the communication process into seven distinct layers, each responsible for specific tasks. Understanding these layers is crucial for anyone working with network protocols, as they help clarify the different stages of data transmission, from physical connections to application-level functions.
Each layer of the OSI model has its own set of responsibilities, and the data is passed through these layers during communication between devices. By breaking down the network process into these manageable components, the OSI model allows for easier troubleshooting, protocol development, and system design.
Overview of the Seven Layers
Below is a table summarizing the seven layers of the OSI model, from the lowest level to the highest:
| Layer | Name | Description |
|---|---|---|
| 7 | Application | Interacts with software applications to provide network services like email, file transfers, etc. |
| 6 | Presentation | Formats data for the application layer, including encryption, compression, and translation. |
| 5 | Session | Manages and controls the communication session between devices, establishing, maintaining, and terminating connections. |
| 4 | Transport | Ensures reliable data transfer through error detection, correction, and flow control mechanisms. |
| 3 | Network | Routes data packets across the network, managing addressing and routing protocols. |
| 2 | Data Link | Handles physical addressing, error detection, and frame synchronization. |
| 1 | Physical | Transmits raw bits over the physical medium, including cables and wireless signals. |
How the OSI Model Affects Troubleshooting
Understanding the OSI layers also greatly aids in troubleshooting. For example, if an issue arises with data transmission, knowing which layer the problem originates from helps you narrow down potential causes quickly. Is the issue with the physical connection? Or does it lie in how the data is being routed or formatted? By methodically testing each layer, you can isolate and resolve issues more efficiently.
Reviewing Networking Security Principles
Understanding the principles behind securing data and communication channels is crucial for ensuring the integrity, confidentiality, and availability of information. Security measures are designed to protect systems from unauthorized access, prevent data breaches, and ensure that sensitive information is only accessible to authorized parties. These foundational principles are vital for building a robust and secure infrastructure in any environment.
Security can be achieved through a combination of technology, policies, and best practices. It involves safeguarding not only physical devices but also virtual systems and communication paths. By implementing these core principles, businesses and individuals can prevent unauthorized access, mitigate risks, and respond to threats swiftly.
Core Security Principles
- Confidentiality: Ensures that data is only accessible by those authorized to view it.
- Integrity: Guarantees that information remains accurate and unaltered during transmission.
- Availability: Ensures that data and systems are available and accessible when needed, even during an attack.
- Authentication: Verifies the identity of users or devices attempting to access a system or network.
- Non-repudiation: Ensures that actions taken by individuals or systems cannot be denied or disputed later on.
Best Practices for Implementing Security Measures
- Use strong passwords and multi-factor authentication to secure access points.
- Encrypt sensitive data both during transmission and while stored on devices or servers.
- Regularly update software and firmware to patch vulnerabilities and minimize the risk of exploitation.
- Monitor network traffic for unusual activity that could indicate potential threats or breaches.
- Apply the principle of least privilege, giving users only the permissions necessary to perform their tasks.
Tools for Networking Troubleshooting
Diagnosing and resolving issues in any communication system requires the right set of tools. These tools help identify the root cause of problems, whether they involve connectivity, speed, or performance issues. Proper troubleshooting not only saves time but also ensures that the system operates efficiently, reducing downtime and improving overall reliability.
There are a variety of tools available to assist in pinpointing network failures, diagnosing configurations, and ensuring smooth communication across devices and systems. From command-line utilities to sophisticated software applications, these tools enable IT professionals and engineers to quickly isolate and fix problems, minimizing disruptions to service.
Essential Tools for Troubleshooting
- Ping: A basic tool used to test connectivity between devices on a network. It sends ICMP echo requests to a target device and measures the response time.
- Traceroute: This tool helps trace the route packets take from one device to another, highlighting potential delays or failures along the path.
- NetFlow: Used to monitor traffic patterns, NetFlow provides valuable data for identifying bandwidth bottlenecks and unauthorized traffic.
- Nslookup: A tool used to query DNS servers and obtain information about domain names and their associated IP addresses.
- Wireshark: A powerful packet analyzer that captures and inspects network packets in real time, helping to diagnose and troubleshoot network communication issues.
Advanced Diagnostic Tools
- Netcat: Often referred to as the “Swiss Army knife” of networking, it allows for both testing and debugging of network connections by reading or writing data across network connections.
- Nmap: A network discovery tool used for security auditing and finding vulnerabilities by scanning ports and services on a network.
- Wi-Fi Analyzer: This tool helps analyze wireless network performance, identify signal strengths, and detect interference that could impact connectivity.
- Tcpdump: A command-line packet analyzer that provides a detailed view of network traffic, often used for low-level debugging of network protocols.
Effective Time Management During the Exam
Managing your time efficiently during an assessment is key to ensuring that you can tackle all sections effectively and avoid unnecessary stress. By allocating enough time to each part of the test and staying focused throughout, you increase your chances of answering questions thoroughly without rushing or missing any critical points.
Successful time management begins with planning ahead. By understanding the structure of the assessment and prioritizing the questions based on difficulty and point value, you can ensure that you spend the appropriate amount of time on each section. Staying mindful of the clock without becoming overly distracted is crucial for maximizing performance during the entire process.
Strategies for Time Management
- Understand the Format: Before starting, make sure you are familiar with the layout of the assessment, including the number of questions, their types, and the time allocated for each section. This knowledge will help you manage your time accordingly.
- Start with Easier Questions: Begin by answering the questions you find easiest. This builds confidence and ensures you complete the quicker tasks first, freeing up time for more difficult ones later.
- Keep an Eye on the Clock: Regularly check the time to ensure you’re staying on track. Don’t spend too much time on a single question, especially if you find yourself stuck.
- Skip and Return: If you encounter a particularly challenging question, move on to others and come back to it later. This ensures that you don’t waste valuable time on a question that might not have a clear answer immediately.
How to Handle Time Pressure
- Stay Calm: Stress can impact your ability to think clearly. If you start to feel pressured, take a few deep breaths to refocus and continue working steadily.
- Break It Down: Break complex questions or tasks into smaller steps. This approach helps you manage the information more effectively and avoids overwhelming yourself with too much at once.
- Review Your Work: If time allows, reserve a few minutes at the end to review your answers. This final check can help you catch any mistakes or missed questions.