
Understanding the intricacies of computer networks is crucial for anyone venturing into the field of digital communication. As technology evolves, staying informed about the core principles and practical applications of networking becomes a valuable skill.
In this guide, we delve into critical topics designed to enhance your knowledge of fundamental and advanced networking concepts. By exploring practical scenarios, you will gain clarity on topics like routing, switching, and secure network implementation.
Whether you are preparing for assessments or refining your technical expertise, this resource offers clear explanations and actionable tips. Strengthen your understanding of connectivity, improve your troubleshooting skills, and pave the way for success in this dynamic field.
Understanding Cisco Networking Basics
Building a strong foundation in networking principles is essential for effectively managing modern communication systems. Grasping the key elements of network design, operation, and troubleshooting provides the necessary framework to excel in this field.
At the heart of networking lies the ability to connect devices and systems seamlessly. This involves understanding how data flows, the role of infrastructure, and the protocols that govern interactions. Familiarity with these concepts ensures efficient setup and maintenance of reliable systems.
By focusing on essential topics such as routing, switching, and addressing methods, you can develop a practical understanding of how networks function. These skills not only enhance technical expertise but also empower you to adapt to diverse challenges in a fast-changing technological landscape.
Key Concepts of Routing and Switching
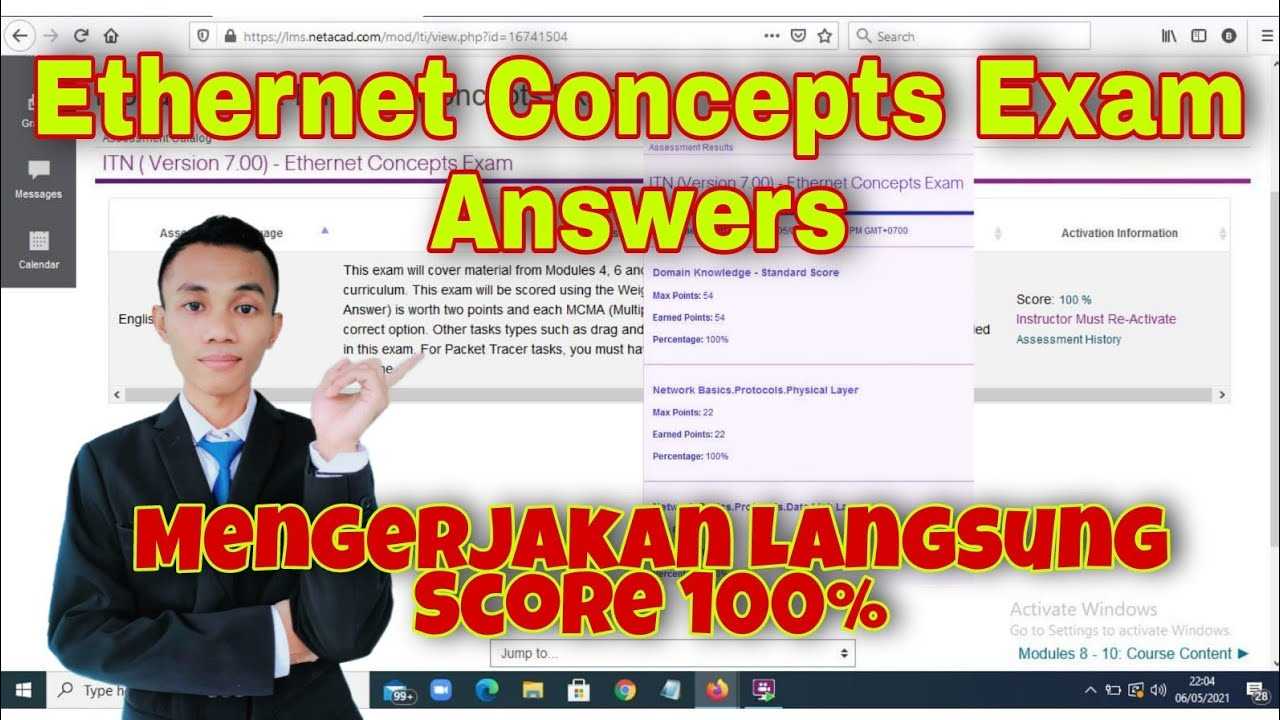
Effective communication within networks depends on the seamless transfer of information between devices. Routing and switching form the backbone of this process, ensuring that data travels accurately and efficiently to its destination.
Routing involves determining the optimal path for data to traverse between different networks. It relies on protocols and algorithms to make intelligent decisions, adapting to changes in network topology to maintain uninterrupted communication.
Switching, on the other hand, focuses on directing traffic within the same network. By creating pathways for data packets to move between devices, switches reduce congestion and improve performance. Understanding how these two mechanisms complement each other is essential for building and maintaining scalable and reliable networks.
Preparing for Networking Assessments
To achieve success in networking evaluations, it’s crucial to focus on mastering core concepts and developing hands-on skills. Preparation should go beyond simple memorization, involving practical exercises and deep understanding of the topics at hand.
A well-organized study plan can make a significant difference, allowing you to track progress and prioritize areas that require more attention. Practicing real-world scenarios and using various resources will help strengthen your skills and increase your confidence.
| Preparation Strategy | Recommended Actions |
|---|---|
| Master Core Networking Concepts | Review the fundamentals of network design, routing, and switching. |
| Hands-On Practice | Work on real network configurations and use simulators for virtual environments. |
| Understand Network Security | Learn about security protocols, firewalls, and risk management techniques. |
| Utilize Online Resources | Make use of tutorials, study guides, and forums to supplement learning. |
By following these strategies, you will enhance your problem-solving abilities and be well-prepared to tackle any networking assessment.
Tips to Tackle Assessments
Approaching technical assessments with the right mindset and strategy can significantly improve performance. It’s essential to blend theoretical knowledge with practical problem-solving techniques to address a variety of scenarios effectively.
Effective preparation involves not only reviewing key concepts but also simulating real-world situations to test your skills. Time management and understanding the structure of the assessment can also help in maximizing your results.
| Strategy | Actions |
|---|---|
| Understand the Question Format | Familiarize yourself with the typical structure of the assessment, including multiple-choice and practical components. |
| Time Management | Allocate enough time for each section, ensuring you don’t rush through important tasks. |
| Review Key Topics | Focus on areas with the highest weight and ensure deep understanding of protocols, configurations, and troubleshooting methods. |
| Practical Exercises | Practice hands-on labs and configurations to become comfortable with technical setups and problem resolution. |
By integrating these strategies into your study plan, you’ll be better equipped to approach assessments with confidence and achieve stronger results.
Common Challenges in Network Configuration
Network configuration can present a variety of challenges, particularly when dealing with complex setups and ensuring seamless connectivity. The process often requires careful planning and attention to detail, as even a small mistake can lead to significant issues.
Common difficulties include misconfigured IP addresses, routing errors, and compatibility issues between devices. Troubleshooting these problems demands a strong understanding of protocols and network design, as well as the ability to methodically isolate and resolve issues.
| Challenge | Possible Solutions |
|---|---|
| IP Address Conflicts | Ensure proper subnetting and implement DHCP for automatic address assignment. |
| Routing Errors | Verify routing tables and ensure that the correct protocols are being used for the network topology. |
| Device Compatibility | Check the firmware versions and ensure that all devices support the same standards and protocols. |
| Network Performance Issues | Monitor bandwidth usage and check for bottlenecks; adjust Quality of Service (QoS) settings as necessary. |
Understanding and addressing these common obstacles will allow network administrators to design and maintain more efficient and reliable networks.
Effective Solutions for Troubleshooting
When issues arise within a network or system, an efficient resolution requires a systematic approach. By methodically identifying the root cause and applying appropriate solutions, technical problems can be addressed promptly. Understanding common troubleshooting techniques and utilizing the right tools can significantly improve the speed and accuracy of the resolution process.
Approach to Identifying the Problem
To effectively address an issue, it’s crucial to follow a step-by-step process. First, gather all relevant details about the malfunction. Then, analyze potential causes based on the symptoms observed. Testing each hypothesis allows for a more accurate identification of the root cause. Once the issue is isolated, an appropriate solution can be applied to restore normal operations.
| Step | Action |
|---|---|
| 1 | Collect Data – Understand the symptoms and gather information about the issue. |
| 2 | Identify Potential Causes – Examine common issues or recent changes in the system. |
| 3 | Test Possible Solutions – Test each potential cause to narrow down the issue. |
| 4 | Implement Fixes – Apply the correct solution based on the identified root cause. |
| 5 | Verify Resolution – Ensure the issue is completely resolved and the system is functioning properly. |
Tools for Efficient Troubleshooting
Several tools can aid in diagnosing and resolving technical problems. These tools help gather important data, pinpoint issues, and offer insights into performance. By leveraging the right tools, troubleshooting becomes more efficient and less time-consuming.
| Tool | Function |
|---|---|
| Ping | Tests network connectivity and identifies issues like packet loss or latency. |
| Traceroute | Maps the path data takes through a network, helping identify disruptions or bottlenecks. |
| Wireshark | Monitors and analyzes network traffic to detect security threats or communication failures. |
| NetFlow | Monitors traffic flow, detecting network congestion and optimizing performance. |
By following a structured approach and utilizing troubleshooting tools effectively, technical problems can be resolved with minimal disruption, ensuring optimal system performance.
Exploring LAN and WAN Technologies
Understanding the differences and applications of various network types is essential for building robust communication infrastructures. Local Area Networks (LAN) and Wide Area Networks (WAN) serve different needs and operate at distinct scales. Each network type uses specific technologies to ensure connectivity, efficiency, and security. Exploring these technologies helps in designing networks that meet the requirements of different environments, whether for small businesses or large enterprises.
Local Area Networks (LAN)
A Local Area Network connects devices within a limited geographical area, such as an office, home, or campus. LAN technologies are designed to offer high-speed data transfer and reliable connections, making them suitable for smaller environments. Some key components of LANs include:
- Ethernet cables for wired connections
- Wi-Fi routers for wireless connections
- Switches to manage data flow between devices
- Access points for extending wireless coverage
In addition to these hardware components, LANs often use protocols like TCP/IP to ensure that devices can communicate with each other seamlessly.
Wide Area Networks (WAN)
A Wide Area Network covers a broader geographical area, often spanning cities, countries, or even continents. WANs are typically used by large organizations, governments, or service providers to enable communication across distant locations. Unlike LANs, WANs require more advanced technologies to ensure stable and secure connections. Key technologies used in WANs include:
- Fiber optic cables for high-speed data transmission
- Satellite connections for remote or rural areas
- Virtual Private Networks (VPN) for secure data transfer
- Multiprotocol Label Switching (MPLS) for efficient routing
WANs are often built by service providers who manage the infrastructure and provide the necessary connections for users. These networks are designed to handle larger traffic loads and deliver data over longer distances, making them crucial for large-scale operations.
By understanding the technologies behind LANs and WANs, organizations can optimize their networks for performance, security, and scalability, ensuring they meet the needs of both local and global communication.
Best Practices for Device Security
Ensuring the security of devices connected to a network is crucial in protecting sensitive data and maintaining overall system integrity. With the growing number of cyber threats, it is essential to implement best practices to safeguard devices from unauthorized access, malware, and other potential vulnerabilities. Proper device security measures help in reducing the risk of breaches and ensuring the continuity of business operations.
Essential Security Measures for Devices
There are several effective strategies that can be applied to secure devices across various networks. These measures focus on minimizing vulnerabilities and enhancing the protection of hardware and software. Key practices include:
- Regularly updating software and firmware to fix known vulnerabilities
- Implementing strong, unique passwords for each device
- Utilizing multi-factor authentication (MFA) for added security
- Encrypting sensitive data stored on devices
- Disabling unused services or ports to reduce the attack surface
Network Security Considerations
Along with securing individual devices, protecting the network itself is equally important. Devices are often compromised through network vulnerabilities, so securing the communication channels between devices is essential. Key network security strategies include:
- Configuring firewalls to filter unauthorized traffic
- Using Virtual Private Networks (VPNs) to encrypt data transmissions
- Segmenting networks to limit access to critical systems
- Regularly monitoring network traffic for unusual activity
- Establishing strict access controls for networked devices
By implementing these best practices, organizations can significantly enhance their device and network security, ensuring that sensitive information remains protected from malicious attacks and unauthorized access.
Analyzing Network Layer Protocols
The network layer is a crucial component in the communication process within a computer network. It is responsible for facilitating data transmission between devices across different networks. This layer ensures that data packets are properly routed, addressing issues like packet forwarding, addressing, and path selection. Analyzing the protocols that operate at this layer helps in understanding how data moves from source to destination efficiently and securely.
Key Network Layer Protocols
Several protocols operate at the network layer, each playing a vital role in ensuring seamless communication. The most important protocols include:
- Internet Protocol (IP): The primary protocol used for routing data across networks. It is responsible for addressing and ensuring that data packets reach the correct destination.
- Routing Information Protocol (RIP): A protocol used for dynamic routing that helps routers decide the best path for data transmission.
- Open Shortest Path First (OSPF): A link-state protocol that helps routers efficiently determine the shortest path for packet transmission within large networks.
- Border Gateway Protocol (BGP): A path vector protocol used for exchanging routing information between different autonomous systems on the internet.
- Internet Control Message Protocol (ICMP): A protocol used for error reporting and diagnostics in network communication, such as with ping commands.
Functions and Benefits of Network Layer Protocols
Understanding the functions of these protocols allows for better troubleshooting and optimization of network performance. The key benefits of these protocols include:
- Routing Efficiency: Protocols like IP and OSPF ensure that data packets find the most optimal path across networks.
- Error Handling: ICMP plays a critical role in identifying and addressing network issues, such as packet loss or delays.
- Network Scalability: Protocols like BGP enable large-scale routing across different networks, supporting the growth of the internet.
- Reliability: By using routing algorithms, these protocols ensure that data is reliably transmitted even in complex network topologies.
Analyzing these protocols helps network professionals to configure, troubleshoot, and optimize network systems for better performance and security. By gaining a deeper understanding of the network layer’s protocols, it becomes easier to identify potential issues and enhance overall network efficiency.
Optimizing Network Design Strategies
Effective network design is essential for ensuring smooth and efficient communication within an organization. Optimizing network architecture involves considering multiple factors such as scalability, redundancy, security, and performance. A well-optimized network not only supports current demands but also allows for future growth without compromising on reliability or security.
Key Factors in Network Optimization
When designing and optimizing a network, several key elements should be considered:
- Scalability: A scalable design ensures that the network can grow in size and capacity as needed. This involves choosing hardware and protocols that can handle increased data traffic and more devices.
- Redundancy: To prevent downtime, redundancy strategies like load balancing and failover systems must be implemented. This ensures that if one part of the network fails, another can take over, maintaining service availability.
- Security: Protecting the network from threats is vital. Incorporating security protocols such as firewalls, intrusion detection systems, and encryption ensures that data is safe from unauthorized access.
- Performance: Optimizing performance involves ensuring that the network is responsive and efficient, with minimal latency and congestion. Techniques such as Quality of Service (QoS) can be employed to prioritize critical traffic.
Best Practices for Efficient Network Design
To achieve an optimized network, following these best practices is crucial:
- Layered Approach: Use a layered design model to separate different network functions. This helps in troubleshooting, scalability, and flexibility in the network’s management.
- Modular Design: Implement modularity to break the network into smaller, more manageable components. This improves both flexibility and efficiency while reducing the complexity of network management.
- Cost Efficiency: Choose cost-effective solutions that meet current needs while keeping future growth in mind. This may involve using open-source software or affordable hardware solutions without compromising performance.
- Regular Monitoring and Maintenance: Continuously monitor the network’s performance and conduct regular maintenance to identify and resolve issues before they impact network performance.
By focusing on these strategies and best practices, organizations can build networks that not only meet the immediate needs but are also adaptable for future expansion and challenges.
Advanced Packet Flow Techniques
Understanding the flow of data within a network is critical for designing efficient and secure systems. Advanced packet flow techniques involve optimizing how data packets are routed, prioritized, and processed across a network to achieve improved performance, reduced latency, and enhanced security. These techniques are fundamental in modern networks where high availability and rapid data exchange are required.
Key Concepts in Advanced Packet Flow
Several concepts are central to managing packet flow effectively in a complex network environment:
- Traffic Shaping: This technique involves controlling the flow of data to prevent network congestion. By regulating the rate at which packets are sent, traffic shaping helps ensure that the network can handle bursts of data without slowing down.
- Quality of Service (QoS): QoS allows for the prioritization of critical traffic over less important data. This ensures that time-sensitive applications, like video conferencing or VoIP, receive the bandwidth they need, even during high traffic periods.
- Packet Filtering: By inspecting packet headers and content, packet filtering can block unwanted or malicious traffic, improving network security. This process ensures that only authorized packets are allowed to pass through specific points in the network.
- Load Balancing: Distributing packets across multiple paths or servers helps optimize resource usage, minimize response time, and avoid overloading any single point of the network, ensuring high availability and reliability.
Techniques for Enhanced Packet Processing
To further enhance packet flow, several advanced processing techniques can be applied:
- Deep Packet Inspection (DPI): DPI involves examining the full content of packets to detect advanced threats or unauthorized activities. It provides more granular control over network traffic, allowing for more informed decision-making regarding packet handling.
- Multiprotocol Label Switching (MPLS): MPLS optimizes packet flow by using labels instead of long network addresses. It speeds up the routing process and improves traffic management, making it particularly useful for large-scale networks.
- Flow Control Protocols: Protocols such as TCP’s flow control mechanisms regulate the rate at which data is sent to prevent network congestion and ensure that receiving devices are not overwhelmed by too much data at once.
- Traffic Engineering: Traffic engineering involves designing the network to optimize the path that packets take, reducing delays and preventing bottlenecks. Techniques such as path optimization and dynamic load balancing are part of this process.
Implementing these advanced techniques ensures that network traffic flows smoothly, with minimal latency and maximum efficiency, supporting the increasing demands of modern applications and services.
Mastering Subnetting in Networking
Subnetting is a crucial skill in modern networking that enables the efficient management and utilization of IP addresses. It involves dividing a large network into smaller, more manageable segments, which enhances performance, security, and scalability. Mastering subnetting allows network professionals to optimize resource allocation and ensure networks can handle growing demands while maintaining security and ease of management.
Understanding how to break down networks into subnets requires knowledge of binary arithmetic, IP address structure, and the roles of subnet masks. By gaining expertise in these areas, network engineers can design networks that are both efficient and flexible, while minimizing wasted address space.
Subnetting Fundamentals
At its core, subnetting is about determining the number of subnets and hosts required within a network. This is done by adjusting the subnet mask, which dictates how many bits are allocated for the network and host portions of an IP address. The key concepts to master include:
- Subnet Mask: Defines which portion of an IP address identifies the network and which part identifies the host. It plays a vital role in splitting an IP address into smaller subnets.
- Network Address: This address identifies the subnet itself and is used to route data to the correct network segment.
- Host Address: The unique identifier assigned to each device within a subnet.
Steps for Effective Subnetting
To efficiently perform subnetting, follow these steps:
- Determine the network size: Understand the number of hosts required for each subnet to calculate the subnet mask.
- Convert IP addresses to binary: Working with binary makes it easier to determine the subnet mask and how the addresses will be divided.
- Calculate the number of subnets: Using the subnet mask, calculate how many subnets can be created from the available address space.
- Assign subnet addresses: Assign each subnet a unique network address based on the desired network size and design.
Mastering subnetting not only improves network performance but also reduces network complexity, allowing for more precise control over how devices communicate within a network.
Understanding IP Addressing Schemes
IP addressing is a fundamental concept in networking, providing the structure necessary for devices to communicate across a network. By assigning unique addresses to each device, an efficient and organized communication system is created, ensuring proper routing of data packets. This section delves into the various IP addressing schemes used to allocate and manage these addresses effectively, offering insights into both public and private addressing, as well as the differences between IPv4 and IPv6.
Types of IP Addressing
IP addresses are categorized into different types, each serving specific purposes in network communication. Understanding the different schemes is essential for network configuration and troubleshooting:
- IPv4: The most commonly used version, IPv4 uses a 32-bit address to uniquely identify devices. It is divided into four octets, written in decimal format, making it easy to manage and recognize.
- IPv6: With the growing demand for IP addresses, IPv6 was introduced to provide a much larger address space. It uses a 128-bit address, allowing for a vastly increased number of unique addresses.
- Private IP Addresses: These addresses are used within local networks and are not routable over the internet. They help conserve the limited number of public addresses and enable secure internal communications.
- Public IP Addresses: These addresses are assigned to devices directly accessible from the internet. They are unique worldwide and are used for communication between networks across the globe.
Address Allocation and Subnetting
In addition to understanding the types of IP addresses, it’s important to grasp how IP address allocation works. This involves dividing networks into subnets, making the network more efficient and easier to manage:
- Classful Addressing: This older system divides the IP address space into classes based on the size of the network. It includes Class A, B, C, D, and E, with Class A, B, and C used for regular network addressing.
- Subnetting: Subnetting allows network administrators to create smaller sub-networks within a larger network, optimizing address allocation and enhancing network performance.
- CIDR (Classless Inter-Domain Routing): CIDR offers a more flexible method for allocating IP addresses by eliminating the fixed class boundaries and allowing more precise address assignments.
Tools for Real-Time Network Monitoring
Effective network management requires continuous observation to ensure optimal performance and prevent disruptions. Real-time network monitoring tools are essential for identifying issues, tracking data traffic, and ensuring smooth communication across a network. These tools provide immediate insights into network health, enabling administrators to take corrective actions before minor issues escalate into major problems.
Key Features of Real-Time Monitoring Tools
Real-time monitoring tools come with a variety of features designed to enhance network management:
- Traffic Analysis: These tools track data flow, helping to identify bottlenecks, congestion, and unusual activity.
- Device Status Monitoring: They keep tabs on connected devices, providing status updates, performance metrics, and alerts for any failures or anomalies.
- Alerts and Notifications: Real-time notifications are triggered for specific events, such as downtime or security threats, allowing administrators to act swiftly.
- Security Monitoring: Tools track unauthorized access attempts, vulnerabilities, and other security issues to ensure the integrity of the network.
Popular Real-Time Monitoring Tools
Several tools are widely used for real-time network monitoring, each offering unique features to suit different network environments:
- Wireshark: A packet analysis tool that allows detailed inspection of network traffic to identify issues and optimize performance.
- SolarWinds Network Performance Monitor: A comprehensive solution offering advanced monitoring capabilities, including real-time alerts, traffic analysis, and device health monitoring.
- PRTG Network Monitor: Known for its versatility, this tool offers network traffic monitoring, bandwidth analysis, and device performance tracking all in one interface.
- Nagios: An open-source monitoring tool that provides comprehensive network and server monitoring, allowing users to set up custom alerts and track system performance.
Learning from Real-World Case Studies
Real-world case studies offer invaluable insights into the challenges and successes of practical network management. By examining the experiences of others, professionals can gain a deeper understanding of problem-solving techniques, resource allocation, and strategic decision-making. Analyzing such cases allows individuals to learn from both the mistakes and the effective solutions implemented in various scenarios, thereby improving their own problem-solving capabilities and operational efficiency.
Case Study 1: Improving Network Performance in a Growing Organization
In this case, a company faced significant slowdowns as it expanded its network infrastructure. The network was initially designed to handle a smaller volume of traffic, but as the organization grew, the system began to suffer from performance issues. The solution involved upgrading hardware, optimizing routing protocols, and introducing load balancing techniques to distribute traffic efficiently.
| Issue | Solution | Outcome |
|---|---|---|
| Slow network speeds | Upgrade routers and switches, implement load balancing | Significant improvement in network speed and reliability |
| Network congestion | Optimized routing protocols and traffic segmentation | Reduced congestion, smoother data flow |
Case Study 2: Securing a Corporate Network from Cyber Threats
Another case study focused on securing a company’s internal network after a series of cyber-attacks threatened to compromise sensitive data. The organization implemented a multi-layered security strategy, including firewalls, intrusion detection systems, and employee training programs to enhance overall security awareness.
| Issue | Solution | Outcome |
|---|---|---|
| Frequent cyber-attacks | Deploy firewalls, intrusion detection systems, and VPNs | Improved security and protection against unauthorized access |
| Low employee awareness of security | Conduct regular security training sessions | Reduced risk of internal security breaches |
Building Confidence for Certification Exams
Confidence is key when preparing for professional certification assessments. By developing a thorough understanding of the material and applying strategic study techniques, individuals can improve their chances of success. Effective preparation not only boosts knowledge but also enhances the ability to manage time and stress during the assessment process. In this section, we will explore practical strategies to help individuals build their confidence and perform their best when facing these important milestones.
1. Master the Core Concepts
Building confidence begins with mastering the fundamental concepts. A deep understanding of the key principles and techniques related to the certification subject is essential. This knowledge forms the foundation for tackling more complex questions and challenges. Take time to break down difficult topics and revisit them regularly until they become second nature.
- Study foundational materials, such as textbooks, manuals, and practice guides.
- Focus on understanding concepts rather than memorizing answers.
- Use real-world examples to contextualize theoretical knowledge.
2. Practice with Mock Tests
Simulating the test environment with practice exams can help reduce anxiety and increase familiarity with the format. Mock tests enable individuals to gauge their readiness, identify areas of weakness, and improve their time management. Regularly taking these practice assessments ensures that you are well-prepared for the real test scenario.
- Set a timer to replicate exam conditions and improve focus.
- Review incorrect answers to understand mistakes and learn from them.
- Gradually increase the difficulty of practice tests to build endurance.