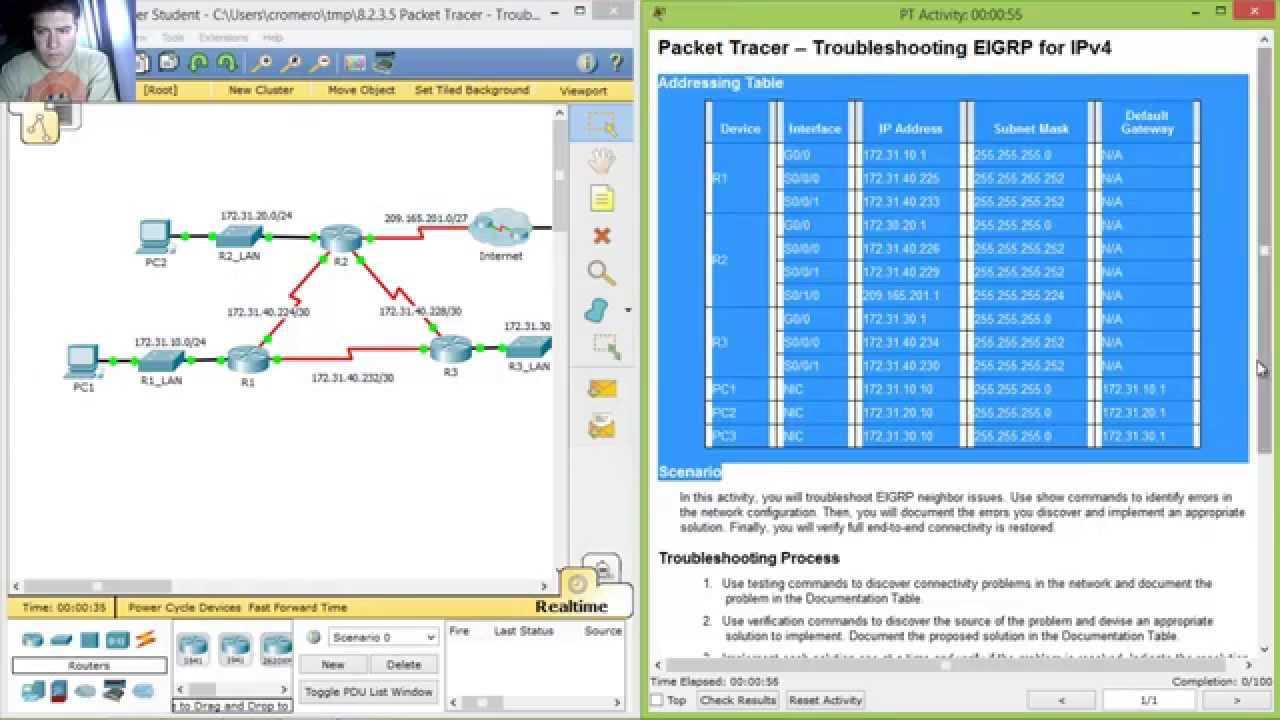
Ensuring smooth network operation often requires managing and monitoring the flow of data between devices. One crucial aspect of network configuration is controlling access to certain resources. While it may seem straightforward, mistakes in setting up access policies can cause significant disruptions in network performance. This section focuses on resolving common issues related to network access management and how to systematically identify and correct these problems.
By understanding the basic concepts of network filtering and applying best practices, network administrators can quickly diagnose and fix issues that arise from misconfigured access rules. Through a series of steps, you can enhance your troubleshooting skills, identify configuration errors, and implement solutions that restore functionality and security across your network infrastructure.
Practical knowledge of common mistakes and how to approach resolution is key. This guide walks you through common pitfalls, effective debugging techniques, and how to evaluate the impact of access restrictions on network traffic. Whether you are new to network configuration or an experienced professional, mastering these skills will improve your troubleshooting efficiency and ensure a more robust network design.
Understanding Network Access Control in Simulation Tools
In network configurations, controlling access to certain resources is essential for maintaining both security and efficient data flow. By setting restrictions on traffic based on specific criteria, administrators can prevent unauthorized access and ensure that only authorized users can interact with certain network segments. This is particularly important in virtualized environments where simulations of real-world networks are created to model different configurations and test various scenarios.
Within these simulation tools, network filtering mechanisms allow users to define rules that either permit or deny traffic based on set conditions. Understanding the basic structure of these filters is crucial for identifying where misconfigurations might occur and how to fix them. These rules can be applied at various points in the network, controlling both inbound and outbound traffic for devices, ensuring that unwanted communication does not take place.
The structure of these access control lists (ACLs) is typically composed of a series of statements that determine the fate of incoming or outgoing packets. Each statement specifies conditions such as the source and destination addresses, the protocol type, and even the port numbers. By adjusting these conditions, network administrators can fine-tune the security of their systems, ensuring that only the right traffic is allowed through.
| Action | Description |
|---|---|
| Permit | Allows the specified traffic to pass through the network. |
| Deny | Blocks the specified traffic from passing through the network. |
| Implicit Deny | If no rules are matched, traffic is automatically denied. |
Mastering the fundamentals of these rules and understanding how to apply them effectively can help users avoid common mistakes and improve their network security posture. Proper configuration ensures that the right traffic is allowed, while unauthorized access is effectively blocked, creating a safer and more stable network environment.
Common Issues with Access Control Lists
When configuring rules to control network traffic, several common issues can arise that may impact the functionality of the network. Misconfigured access controls can lead to unwanted interruptions or security vulnerabilities. Identifying and addressing these issues is crucial for maintaining a smooth and secure network environment.
Incorrect Rule Order
One of the most frequent problems occurs when the order of rules within the filter is not properly set. Access control lists process rules sequentially, meaning the first rule that matches the traffic will be applied. If a more specific rule is placed after a more general one, it might be ignored, leading to unintended access being allowed or denied. Proper ordering of rules is essential to ensure that the correct traffic is processed as expected.
Overly Broad Rules
Another common issue is the use of overly broad rules that unintentionally allow or block too much traffic. For example, a rule that permits all traffic from a certain IP range might inadvertently allow malicious traffic from unauthorized sources within that range. Fine-tuning the conditions, such as specifying the exact ports or protocols, can help narrow down the scope of access and enhance network security.
Addressing these common problems requires careful planning and attention to detail. Regularly reviewing and testing access control policies can help prevent misconfigurations and ensure that the network operates as intended.
How to Configure Access Control Lists Correctly
Configuring traffic filters correctly is essential for managing network security and performance. To achieve this, network administrators must define clear rules that control which traffic is allowed or denied, based on specific criteria such as IP addresses, protocols, or ports. A well-configured access policy can prevent unauthorized access and ensure that the network operates smoothly.
The first step in creating effective filters is determining the specific requirements for traffic control. Identify which devices, services, or applications need access, and define the necessary parameters for both inbound and outbound traffic. Once the goals are clear, rules should be defined in a logical sequence, ensuring that more specific rules are placed before broader ones to avoid unintentional mismatches.
When configuring the rules, always consider both the source and destination IP addresses, as well as the type of traffic (e.g., HTTP, FTP). Use precise criteria to minimize unnecessary access and ensure that the network remains secure. Test the configuration after applying the rules to ensure they behave as expected, and adjust if needed to avoid connectivity issues or security lapses.
Key Concepts Behind Access Control Lists
Access control lists (ACLs) are essential tools for managing network traffic and enforcing security policies. They allow administrators to define a series of rules that either permit or deny traffic based on certain parameters, such as source or destination addresses, protocols, and ports. Understanding the key principles behind these lists is crucial for ensuring that the network operates efficiently and securely.
At their core, ACLs evaluate packets based on specific criteria, applying rules in a sequential manner. When a packet enters the network, it is checked against the list, and the first rule that matches determines whether the packet is allowed or blocked. This makes the order of rules critically important–misplaced rules can result in unintended access or blockages.
Another fundamental concept is the difference between permissive and restrictive rules. A “permit” rule allows certain types of traffic to pass, while a “deny” rule blocks it. In many cases, an implicit deny rule is assumed at the end of the list, meaning that any traffic not explicitly allowed by earlier rules will be automatically rejected.
Step-by-Step Troubleshooting Network Access Controls
When access restrictions fail to work as expected, it’s essential to follow a systematic approach to identify and resolve the underlying issues. A structured troubleshooting process helps to pinpoint misconfigurations or errors in the rules, ensuring that the network operates securely and efficiently. By breaking down the process into manageable steps, administrators can quickly address problems without unnecessary delays.
1. Review the Configuration
Start by carefully reviewing the configuration settings to ensure that the rules are properly defined. Look for common mistakes such as:
- Incorrect rule order–more specific rules should precede general ones.
- Missing or overly broad conditions (e.g., permitting all traffic from an IP range).
- Unintentional denial of critical services or devices.
2. Test and Verify the Rules
Once the configuration is reviewed, testing is crucial to verify the behavior of the traffic rules. Use the following steps to test and validate:
- Check connectivity between devices to ensure that permitted traffic is flowing as expected.
- Use diagnostic tools like “ping” or “traceroute” to trace the path of the traffic and check for blockages.
- Monitor the access logs to see if any denied traffic is being logged unexpectedly.
After testing, adjust the rules accordingly based on the findings. This iterative process will help identify any misconfigurations and resolve them for optimal performance.
Debugging Access Control List Configuration
When access control policies do not function as expected, debugging the configuration is essential to pinpoint the problem. In a virtualized environment, you can use built-in diagnostic tools to identify errors and misconfigurations in the rules. Understanding how to use these tools effectively can save time and prevent potential security issues. Debugging involves both reviewing the configuration for mistakes and testing the impact of the rules on traffic flow.
Step-by-step debugging often begins with examining the configuration for any obvious issues such as incorrect rule order or syntax errors. Once the configuration is verified, diagnostic commands and real-time monitoring can help pinpoint specific problems. Tools such as “show” commands provide valuable insight into how the rules are applied and which traffic is being blocked or allowed.
Additionally, running debugging commands in the command-line interface allows you to view detailed logs of traffic flows, helping to track the journey of packets through the network. By using these methods, you can quickly identify which traffic is being incorrectly filtered and adjust the configuration to resolve the issue.
Identifying Mistakes in Access Control Rules
When configuring rules to manage network access, it’s easy to introduce mistakes that can disrupt traffic flow or leave the network vulnerable. Identifying these mistakes early is crucial to maintaining both security and functionality. Common errors often stem from incorrect rule syntax, misordering of conditions, or overly broad filters that fail to restrict traffic as intended.
One of the most common issues is placing more general rules before more specific ones. In rule-based filtering systems, the first rule that matches a packet’s criteria will be applied, which means that a broad rule placed at the top of the list may unintentionally block or allow traffic that should have been controlled by a more specific rule further down the list. Careful attention should be given to rule order to ensure the most granular filters are applied first.
Another frequent error is using overly vague conditions, such as permitting all traffic from a specific IP range without considering the specific protocols or ports that should be allowed. This can lead to unintended access, especially if an attacker is able to exploit the broad permissions. It is important to specify the relevant ports and protocols clearly to restrict access to only the necessary services.
To identify these mistakes, carefully review the access control list and ensure that all conditions are properly defined and ordered. Using diagnostic tools like logging and traffic analysis can help to identify which traffic is being blocked or allowed and provide insights into where adjustments may be needed.
Testing ACL Functionality with Packet Tracer
Testing the effectiveness of network access controls is essential for ensuring that the defined rules behave as expected. By using simulation tools, network administrators can verify that traffic is filtered correctly and that only authorized data flows through the network. These tools allow administrators to simulate various network conditions and test the impact of access control settings in a controlled environment before applying them to a live network.
One of the first steps in testing is to observe the traffic behavior before and after applying the rules. This involves creating scenarios that mimic real-world traffic patterns, such as sending packets from various sources to different destinations. By monitoring whether the traffic is correctly allowed or denied based on the established rules, administrators can assess whether the controls are functioning properly.
Additionally, it is important to use diagnostic features such as log analysis or packet capture to track the movement of data and identify any discrepancies. These tools can provide real-time feedback, allowing network engineers to make adjustments to the configuration if necessary. With the right testing approach, administrators can ensure that the access control settings are both effective and secure, reducing the likelihood of misconfigurations in a live environment.
Common Misconfigurations in Network Simulation Tools
When configuring network access controls, there are several common mistakes that can prevent policies from being effective. Misconfigurations often arise from oversights in rule order, incorrect syntax, or misunderstanding of how certain conditions are applied. These errors can lead to unintended access or disruptions in network traffic. Recognizing these misconfigurations is key to ensuring that the network operates as intended.
One frequent issue is the incorrect ordering of rules. In access control systems, rules are evaluated sequentially, meaning that more specific rules should be placed higher in the list than general ones. Failing to do so can result in traffic being improperly allowed or denied, as a more general rule may override a specific one.
Another common mistake is the improper use of address or port specifications. Often, network engineers may mistakenly allow or block entire IP ranges or services, instead of targeting specific ports or protocols. This broad approach can create security vulnerabilities or block legitimate traffic. It is crucial to define specific address ranges, protocols, and ports for more granular control.
Misapplication of implicit deny is also a common problem. Many assume that the implicit deny rule at the end of a list will automatically catch all unauthorized traffic. However, if a rule is incorrectly defined earlier in the list, legitimate traffic can be blocked without a clear explanation, leading to confusion during testing or troubleshooting.
To avoid these errors, it is important to carefully review each rule, check for proper order, and ensure that each condition is correctly specified. Using simulation tools and diagnostic features can help identify these misconfigurations early, preventing issues before they affect a live network.
How to Use Packet Tracer for Troubleshooting
Network simulation tools provide powerful capabilities to identify and resolve issues within a virtualized network environment. By creating realistic network topologies and simulating traffic, you can easily identify potential problems without affecting the production network. These tools are especially useful for testing configurations, verifying the impact of network policies, and performing detailed diagnostics on network behavior.
One of the most effective ways to troubleshoot using simulation tools is to start by building a model of the network environment. Once the devices and connections are in place, you can apply different configurations and monitor how they impact traffic flow. For example, if a network segment isn’t functioning properly, you can isolate it within the simulation to see how traffic is being blocked or allowed at various points in the network.
Additionally, simulation tools offer diagnostic features such as real-time traffic analysis and packet tracing. These tools allow you to observe how packets travel through the network, where they get stopped, and which rules are being applied at each point. The ability to pause the simulation, examine traffic logs, and test different configurations makes it easier to pinpoint the exact source of an issue.
| Action | Description |
|---|---|
| Start with a Baseline | Model the network and configure initial settings to establish a starting point for troubleshooting. |
| Simulate Traffic | Generate traffic flows across the network to observe how the configurations impact packet delivery. |
| Use Real-Time Analysis | Monitor live traffic and packet logs to identify any issues related to routing or security rules. |
| Modify Configurations | Make adjustments to the configuration, such as changing rule order or IP settings, and test the results. |
By using these diagnostic methods, you can effectively identify network issues, make changes in real-time, and gain a deeper understanding of how network policies affect traffic behavior. This approach allows you to solve problems efficiently, saving time and reducing the likelihood of introducing errors in a live environment.
Tools and Commands for ACL Troubleshooting
When working with network configurations, having the right set of tools and commands is essential for diagnosing issues with access control and network traffic management. These tools allow administrators to check how traffic is being handled, inspect the configuration settings, and pinpoint where things might be going wrong. By utilizing the proper commands, you can quickly gather insights and identify areas needing adjustment.
Key Diagnostic Tools
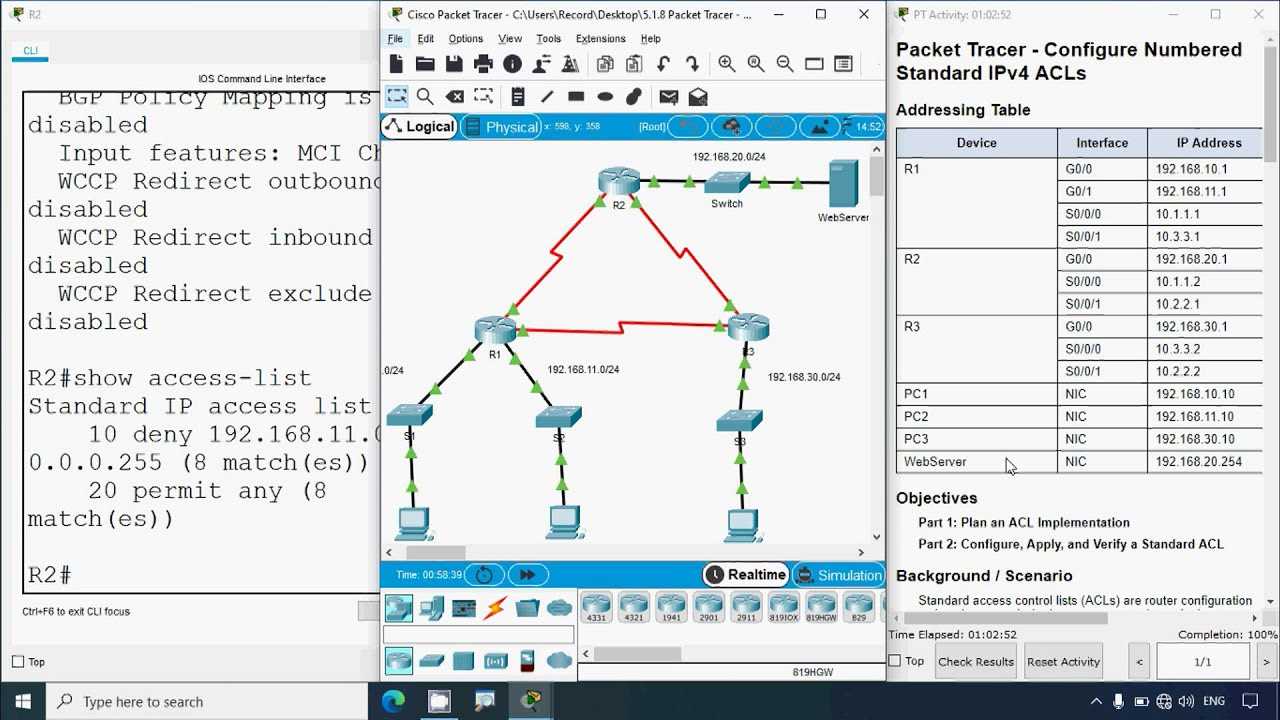
- Ping – A basic tool used to test connectivity between devices. It helps determine whether devices can reach each other across the network.
- Traceroute – Used to track the path of packets as they travel from source to destination, providing visibility into how traffic is routed across different network segments.
- Telnet/SSH – Remote access tools for connecting to network devices, allowing the user to inspect configurations and test connectivity directly on the device.
- Packet Capture Tools – Tools such as Wireshark can be used to monitor live traffic, capture packets, and analyze their contents to identify problems such as dropped or misrouted packets.
Important Commands for Configuration Checks
- show running-config – Displays the current configuration of the device, which is essential for checking the applied rules and settings.
- show access-lists – Lists all configured access control entries and their status, helping you see which rules are active and how they are affecting traffic.
- show ip interface – Provides details about the interface status and IP addressing, which can be crucial when troubleshooting access control related to routing or IP addresses.
- debug – A powerful command that allows you to view real-time debugging output for various network activities, including packet forwarding and rule application.
- clear counters – Resets the traffic counters, allowing you to gather fresh data and track specific issues that might occur after changes have been made.
By combining these tools and commands, network engineers can more effectively monitor and analyze network traffic. Whether you are investigating issues related to blocked packets, misconfigured rules, or improper routing, these resources provide the necessary visibility and control to resolve problems quickly.
Analyzing ACL Impact on Network Traffic
Access control lists (ACLs) play a crucial role in regulating network traffic by determining which data flows are allowed or denied based on specified criteria. Understanding how these controls affect traffic behavior is essential for maintaining optimal network performance and security. A well-configured ACL ensures that only authorized users or devices can access specific resources, while improper rules can lead to unexpected connectivity issues or security vulnerabilities.
Identifying the Impact of ACL Rules
When an ACL is applied to an interface, it filters incoming or outgoing traffic based on criteria such as IP addresses, protocols, and ports. The impact of these rules can be significant, as they directly affect the ability of devices to communicate across the network. Misconfigured ACLs can result in traffic being unintentionally blocked or allowed, causing disruptions to network services.
- Access Denial: A common issue occurs when an ACL mistakenly blocks necessary traffic. For example, blocking a legitimate IP address or port can disrupt communication between devices, leading to application failures or inability to access essential resources.
- Unintended Allowance: Conversely, an ACL might allow traffic that should be restricted, creating security risks. This can happen if the rules are too permissive or if the deny statements are placed incorrectly.
- Performance Degradation: ACLs can also affect network performance if they are not properly optimized. When there are many rules, especially complex ones, it can cause delays in packet processing as the device evaluates each condition before making a decision.
Evaluating Network Behavior with ACLs
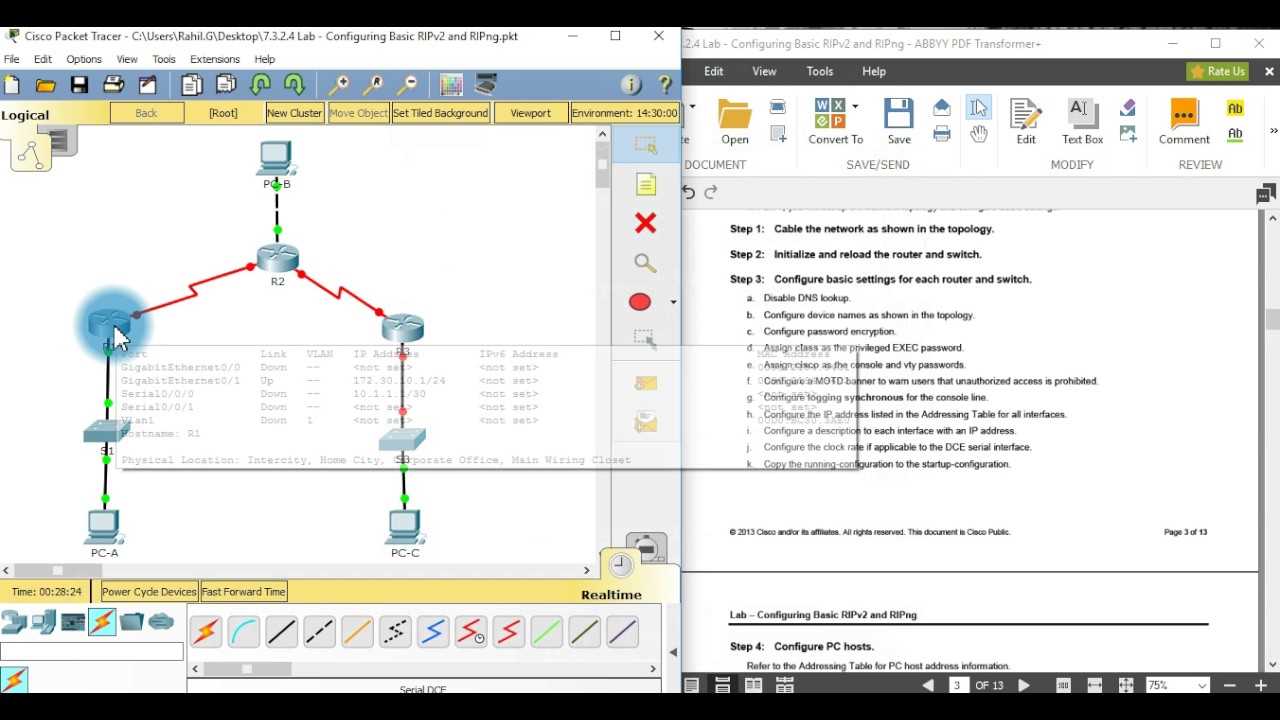
To assess the actual effect of ACLs on network traffic, administrators can monitor the flow of data through various tools and commands. Observing the traffic patterns helps identify any deviations from expected behavior, such as traffic that is mistakenly blocked or improperly routed.
- Traffic Monitoring: Using network monitoring tools allows administrators to observe the flow of packets in real-time and determine whether specific types of traffic are being correctly filtered according to the ACL rules.
- Packet Capture: A packet capture tool like Wireshark enables administrators to examine the packets at a deeper level, ensuring they comply with the applied access controls. This can be especially helpful for identifying issues with denied or allowed traffic.
- Rule Testing: By temporarily adjusting or disabling specific ACL rules, administrators can test the impact of those changes on network traffic. This controlled testing can help pinpoint problematic configurations.
In summary, analyzing the impact of access controls on network traffic is an ongoing process that requires careful observation and fine-tuning. Properly configured ACLs ensure the security and efficiency of network operations, while misconfigurations can result in unwanted consequences such as access issues or security breaches.
IPv4 ACLs vs Extended ACLs
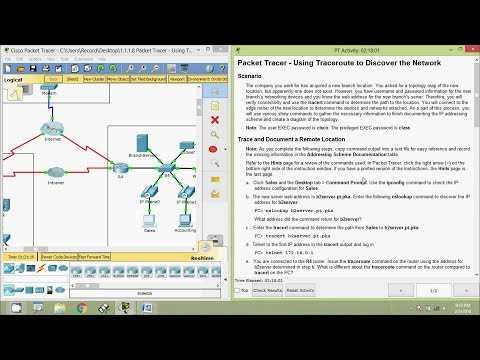
When managing network security, there are two primary types of access control lists used to filter traffic based on various criteria: basic and extended. Both types serve the purpose of controlling data flow, but they differ in terms of their functionality, flexibility, and the level of detail they can apply to traffic filtering. Understanding the differences between these two options is essential for effective network design and security management.
Basic Access Control Lists (ACLs)
Basic ACLs are used for simple traffic filtering based on IP addresses. They offer a limited level of control, focusing primarily on granting or denying access to specific networks or hosts. These lists are easier to configure but lack the granularity offered by extended ACLs.
- Simple Criteria: Basic ACLs only filter traffic based on the source IP address, making them suitable for straightforward access control tasks.
- Limited Control: They do not allow filtering based on protocols, ports, or other parameters, which can limit their flexibility in more complex network environments.
- Faster Processing: Due to their simplicity, basic ACLs are processed more quickly by network devices, leading to less strain on network performance.
Extended Access Control Lists
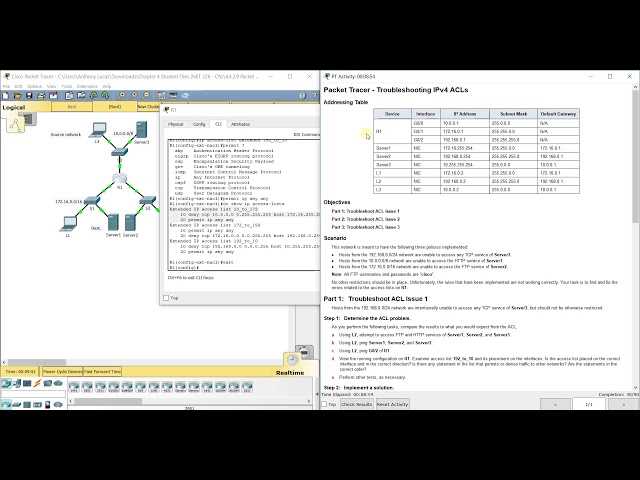
Extended ACLs provide much more control over network traffic than their basic counterparts. In addition to filtering traffic based on IP addresses, extended ACLs can also evaluate other parameters such as source and destination ports, protocol types, and even the specific type of traffic being transmitted.
- Granular Filtering: Extended ACLs allow filtering based on source and destination IP addresses, protocols (TCP, UDP, ICMP), ports, and even the direction of traffic.
- More Complex Configuration: Due to the broader range of criteria, extended ACLs are more complex to configure, but they provide much more precise control over traffic.
- Better for Security: Because extended ACLs offer detailed filtering capabilities, they are more effective at securing the network by controlling access to specific services or applications.
Key Differences
Below is a comparison of the basic differences between these two types of access control lists:
| Feature | Basic ACL | Extended ACL |
|---|---|---|
| Criteria for Filtering | Source IP Address | Source/Destination IP, Ports, Protocols |
| Complexity | Simple | Complex |
| Traffic Control | Limited (IP address only) | Detailed (protocols, ports, etc.) |
| Performance | Faster Processing | Slower Processing |
In conclusion, the choice between basic and extended ACLs depends on the specific requirements of the network. Basic ACLs are ideal for simpler scenarios where only basic filtering is needed, while extended ACLs offer far more control and flexibility for complex network setups requiring detailed access restrictions.
Verifying ACL Implementation in Packet Tracer
Ensuring that access control configurations are functioning as intended is a crucial step in securing a network. Verification involves checking whether the rules applied to the network are properly filtering traffic, and whether the network behaves according to expectations. A variety of methods can be used to verify these settings and ensure that no unintended traffic is allowed or blocked.
Checking ACL Status
The first step in verifying the implementation of access control configurations is to check the status of the rules applied to the network devices. This can be done through the command-line interface (CLI), where you can list all the applied rules and confirm their correctness. Use the following steps to check the status:
- Command: show access-lists – This command will display all the access control entries that have been configured on the device.
- Command: show running-config – This will provide the current running configuration, allowing you to inspect any access control entries applied to interfaces.
- Command: show ip interface – This command shows the status of the interfaces and any associated access control lists.
Testing Traffic Flow
Once the configuration is verified, testing the traffic flow is the next logical step. By using simulated devices or actual traffic, you can confirm whether the rules are working as expected. Follow these steps for effective traffic testing:
- Ping Test: Use the ping command from one device to another within the network. This will help determine if the access control entries are blocking or permitting ICMP traffic.
- Telnet or SSH Test: Try accessing services on remote devices. If the ACL is configured to block certain ports, this will help verify whether the ACL is filtering out traffic based on port numbers.
- Traceroute: This can help identify the path that packets take across the network, revealing whether any ACLs are blocking specific routes or hops.
Analyzing Log Files
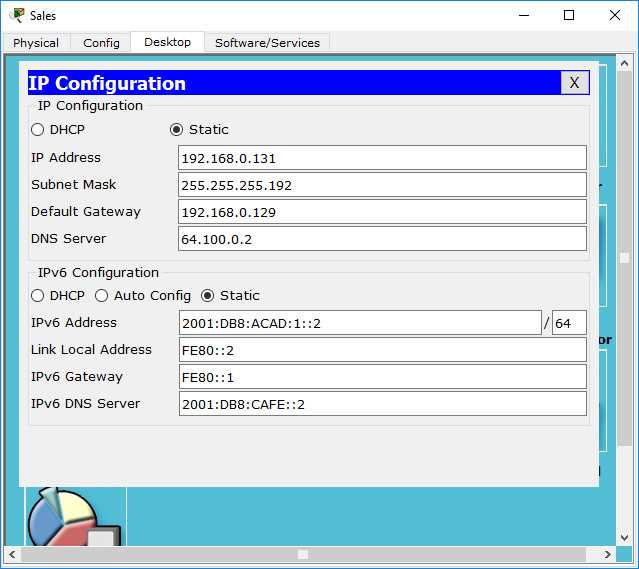
Another key aspect of verification is checking the device logs. These logs can provide real-time data on how traffic is being handled, including whether it is being allowed or denied according to the configured rules. Logs can often be used to troubleshoot issues that may not be immediately apparent through other verification methods.
- Command: show logging – Displays the device’s log, which can show whether ACLs have been triggered and which traffic has been blocked or permitted.
- Command: debug ip packet – This command can be used to display the details of the IP packets as they are processed by the router, which can help identify whether ACLs are interfering with traffic flow.
In conclusion, verifying the successful implementation of access control configurations is essential to ensure that the network security measures are effectively working. By checking the configuration, testing traffic flow, and reviewing log files, network administrators can confirm that the applied rules are functioning as intended and troubleshoot any potential issues.
Improving Security with Proper ACL Setup
Implementing well-designed access controls is vital for securing any network. These configurations dictate which traffic can pass through the network devices and which should be blocked, ensuring that only legitimate users and systems can access sensitive resources. Properly applying these rules helps minimize the attack surface, protecting the network from unauthorized access, potential attacks, and data breaches.
To enhance security, the access control lists must be carefully planned and configured to reflect the organization’s security policies. Incorrect setups can either leave the network vulnerable or unnecessarily block legitimate traffic, causing operational issues. By applying the right strategies, administrators can ensure that access is granted only to trusted sources while unwanted traffic is efficiently filtered out.
Principles of Effective Access Control
Effective security through access control starts with understanding the fundamental principles of controlling traffic flow:
- Least Privilege: Always apply the principle of least privilege by only allowing the minimum level of access necessary for users or devices to perform their tasks. This limits exposure to potential attacks.
- Explicit Deny: Deny traffic that is not explicitly allowed. This approach ensures that any traffic not explicitly permitted by the rules will be blocked by default.
- Order of Rules: The order in which rules are configured is crucial. ACLs are processed sequentially, so more restrictive rules should appear before more permissive ones to ensure proper filtering.
Strategies for Better Security
There are several strategies that can be applied to further strengthen security through access control configurations:
- Use Extended Filters: For finer control over traffic, use extended filters that can examine not just source and destination IP addresses, but also port numbers and protocols. This enables more precise access control based on the specific needs of the network.
- Apply Access Controls to Specific Interfaces: Rather than applying broad access control lists across the entire device, configure them to specific interfaces or subnets to limit the scope and impact of each rule.
- Regular Audits and Updates: Regularly review and update the access control rules to account for changes in the network or security landscape. Outdated rules can create vulnerabilities, so periodic reviews are necessary to ensure the rules are still valid and secure.
In conclusion, the right setup of access control configurations is crucial in creating a secure network environment. By following best practices, such as applying the least privilege principle, using explicit deny rules, and carefully crafting the sequence of ACL entries, network administrators can ensure that only authorized traffic is allowed, minimizing the risk of unauthorized access or security breaches.
Advanced Techniques for ACL Troubleshooting
When access controls are not functioning as expected, the process of identifying and resolving issues can become complex. Advanced techniques allow network administrators to efficiently diagnose problems and ensure that traffic is properly managed. These methods focus on isolating variables, examining logs, and using powerful tools to uncover hidden issues. Understanding how to implement these techniques can significantly improve the accuracy and speed of troubleshooting, reducing downtime and enhancing network security.
Utilizing Packet Capture and Traffic Analysis
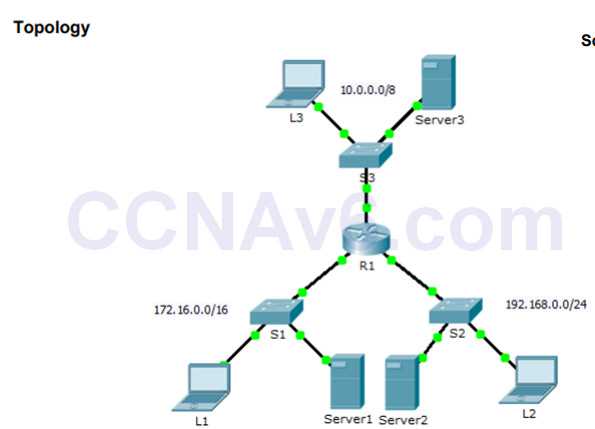
One of the most effective ways to troubleshoot access control issues is by analyzing the traffic flowing through the network. By capturing packet data, administrators can see exactly what traffic is being allowed or denied. This process helps identify discrepancies between expected and actual behavior, especially when access restrictions do not appear to be applied correctly. Tools such as packet analyzers or built-in network monitoring features allow for real-time inspection of traffic patterns.
- Packet Sniffers: Tools like Wireshark can be used to capture packets on the network, providing a detailed look at which packets are being dropped or permitted by the access rules.
- Traffic Simulation: Using network simulation tools, administrators can simulate traffic patterns to test how the access control configurations are behaving under different conditions.
Implementing Logging for Detailed Insights
Access control logs are essential for diagnosing issues. By enabling logging on the network devices, administrators can track which traffic is being allowed or denied, and understand the reasons behind these decisions. Logs often contain valuable details, such as the specific rule that matched a packet or the interface where the packet was dropped, providing insights into where the problem lies.
- Log Filtering: To manage large amounts of data, logs can be filtered by time, source, destination, or protocol, making it easier to pinpoint problematic traffic.
- Log Analysis Tools: Automated tools can help analyze logs by identifying patterns or errors in rule configurations, improving the troubleshooting process.
Testing with Conditional Access Rules
Another advanced technique involves the creation of conditional rules, which are particularly useful when trying to isolate the source of a problem. By applying temporary rules that are specifically designed to match certain traffic types, administrators can narrow down whether specific access controls are the cause of an issue. This method helps pinpoint misconfigurations and provides a step-by-step approach to verify which part of the configuration is not functioning as intended.
- Temporary Allow Rules: For troubleshooting, temporary rules that allow all traffic from a specific source or destination can be applied to see if the issue lies with blocking behavior.
- Network Isolation: Testing can be performed in a controlled section of the network to see how changes affect only the impacted areas without disrupting other traffic flows.
In summary, advanced troubleshooting techniques provide deeper visibility into network behavior, helping to resolve issues with greater precision. By leveraging packet capture, log analysis, and targeted testing strategies, administrators can quickly identify the root causes of access control issues and ensure that their configurations are both effective and secure.
Best Practices for Managing IPv4 ACLs
Effective management of access controls is crucial for maintaining a secure and well-functioning network. Properly configuring, monitoring, and optimizing these controls ensures that network resources are only accessed by authorized users while preventing unauthorized traffic. By adhering to best practices, network administrators can streamline the implementation of these rules, reduce errors, and improve overall security. This section covers key strategies for managing network access restrictions effectively.
1. Keep Access Control Lists Organized
Maintaining a clear and organized structure for access control rules is essential for efficient management. Rules should be grouped logically based on their function, such as restricting internal traffic, allowing external access, or controlling administrative traffic. Having an intuitive structure helps when reviewing or updating rules, ensuring that they are applied consistently and reducing the risk of mistakes.
- Use Descriptive Names: When creating access rules, use clear names and comments to describe their purpose. This helps administrators quickly identify and modify rules when necessary.
- Segment Rules by Function: Organize rules into logical segments, such as inbound and outbound rules, to make them easier to manage and troubleshoot.
2. Apply the Principle of Least Privilege

The principle of least privilege is a foundational security concept that suggests users or devices should only be granted the minimum level of access necessary to perform their tasks. When configuring access controls, only allow traffic that is absolutely required. This minimizes potential attack vectors and limits exposure to malicious activities.
- Allow Specific Traffic Only: Be as restrictive as possible when defining allowed traffic. Instead of allowing all traffic from a source or network, specify only the necessary ports and protocols.
- Use Deny by Default: Apply a “deny all” rule at the end of the list to block any traffic not explicitly allowed by earlier rules.
3. Regularly Review and Update Access Controls
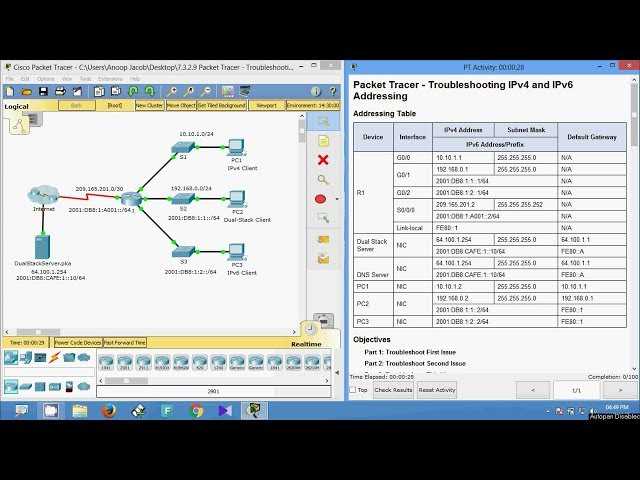
Access control lists should not be static; they must evolve with changing network needs and security threats. Regularly reviewing and updating these rules ensures that they remain aligned with organizational requirements and best practices. This helps eliminate outdated or unnecessary rules that may pose security risks.
- Perform Routine Audits: Set up regular audits to check for any redundant or conflicting rules. This helps streamline the rule set and ensures efficient performance.
- Update for New Network Changes: When network architecture or user roles change, access control rules should be updated accordingly to reflect the new requirements.
By following these best practices, administrators can ensure that their access control configurations are secure, efficient, and easy to manage. A well-maintained set of access restrictions will help protect the network from unauthorized access while allowing legitimate traffic to flow smoothly.