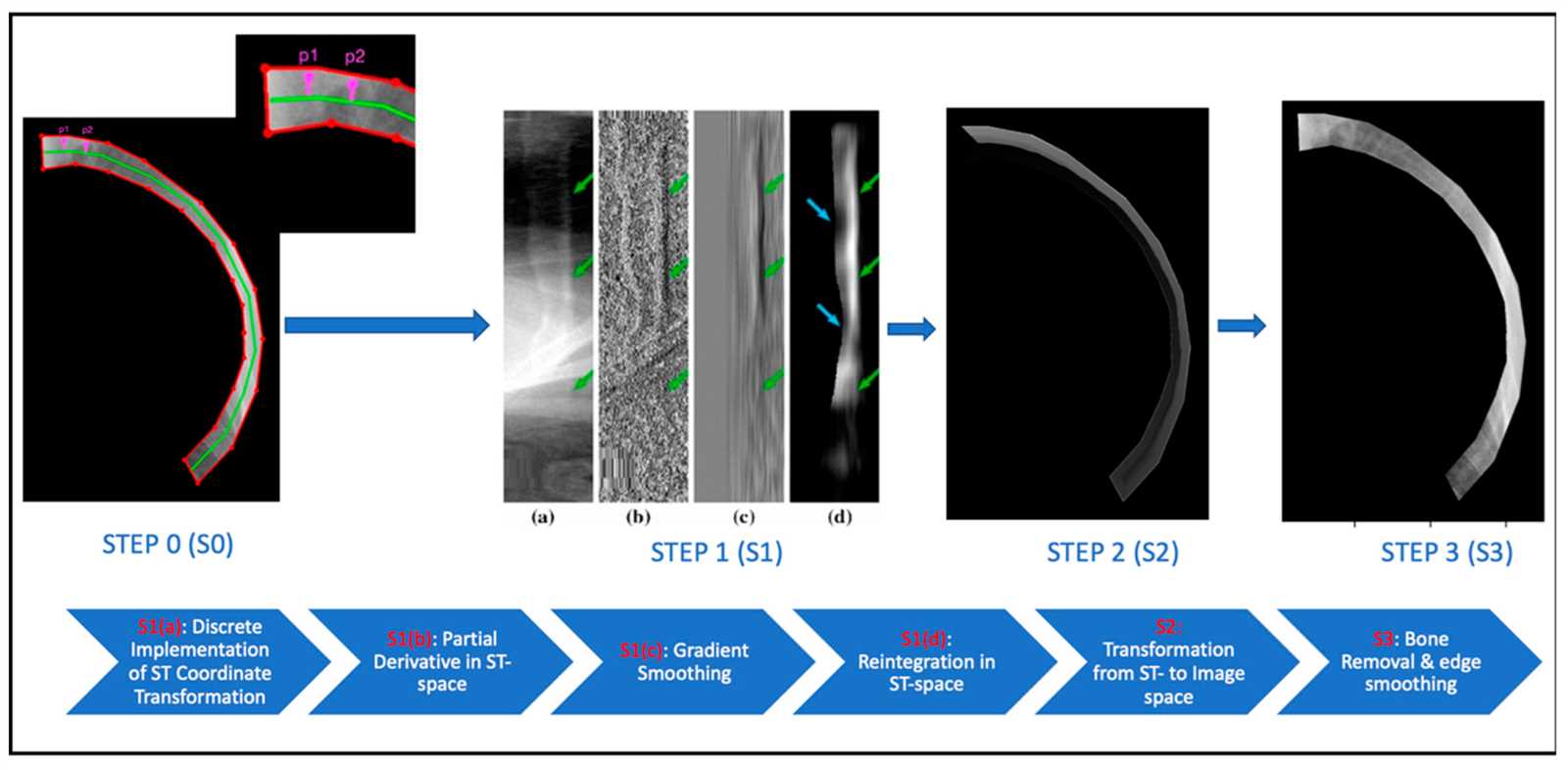
When dealing with sensitive government information, understanding how to correctly assess and label material is essential for maintaining national security. This process ensures that only authorized individuals have access to specific types of information based on its level of confidentiality.
Proper evaluation involves identifying the right security level for documents, based on their content, sources, and the implications of their disclosure. For those responsible for making these assessments, it is critical to have a solid grasp of the principles, guidelines, and procedures in place. Mastery of these concepts not only enhances security but also ensures compliance with regulations.
In this section, we will explore key strategies for effectively handling material assessment, avoiding common mistakes, and providing valuable insights into the best practices that lead to successful decision-making in this field. The goal is to equip you with the necessary tools and knowledge to confidently navigate these responsibilities and avoid costly errors.
Document Security Assessment Evaluation
In the field of government security, correctly assessing and labeling sensitive documents is a crucial task. Those responsible for determining the level of confidentiality must follow strict guidelines to ensure that information is properly protected. Accurate evaluations are vital for safeguarding national interests and preventing unauthorized access to classified material.
One of the key challenges in this process is understanding how to interpret and apply security regulations effectively. It requires a strong knowledge of classification standards, potential risks of disclosure, and the proper procedures for handling protected content. By mastering these concepts, individuals can make informed decisions that maintain security integrity and comply with legal requirements.
This section provides essential guidance for those preparing to take the test related to document handling responsibilities. It covers common areas of confusion, practical tips for approaching the questions, and strategies for accurately applying classification rules. Success in these evaluations ensures that sensitive information remains secure and that individuals in charge of these tasks can perform their duties with confidence.
Understanding the Security Document System
In any organization handling sensitive government information, it is essential to have a clear structure for determining the level of confidentiality that should be applied to documents. This system ensures that information is protected based on its significance and the potential impact of its unauthorized disclosure. By adhering to these standards, organizations can safeguard national security and prevent mishandling of classified material.
Key Principles of the Security System
At the heart of this system are the principles that guide how information is categorized and safeguarded. These principles are designed to ensure that sensitive data is only accessible by individuals with the proper clearance and need-to-know basis. The framework includes various levels of security, each representing a different degree of sensitivity, from unclassified to top-secret material.
The Role of Security Markings
Security markings play a critical role in identifying the appropriate level of confidentiality for each document. These markings indicate whether the material is restricted or if it can be shared with others. Understanding these labels is essential for anyone responsible for managing sensitive content, as they provide clear guidelines on how to handle the information securely and legally.
Key Principles of Document Security Evaluation

When managing sensitive government materials, it is vital to understand the core principles that guide the assessment of information. The task of determining the correct security level for documents requires a deep understanding of how to interpret existing guidelines, apply them accurately, and avoid errors. This section focuses on the essential principles that form the foundation for making informed decisions in document evaluation.
Principles for Proper Evaluation
Effective handling of classified documents involves several guiding principles that help ensure proper security measures are followed. These principles include:
- Need-to-Know Basis: Information should only be shared with individuals who have the necessary clearance and a legitimate need to access it for their work.
- Consistency: Security levels must be consistently applied to all documents based on the same criteria to avoid confusion and errors.
- Accuracy: Evaluators must ensure that all decisions regarding document classification reflect the true sensitivity of the information contained within.
- Accountability: Individuals making decisions about document evaluation must be held accountable for their actions, ensuring that the process is transparent and secure.
Applying Security Labels Correctly
Security labels and markings are crucial in identifying how a document should be treated. These markings guide individuals in how to handle the document, who can access it, and what precautions are needed. Key steps include:
- Ensure the correct security level is assigned based on the content and potential risk.
- Use approved labels and markings to clearly define the document’s security classification.
- Reassess the document’s classification regularly to ensure it remains accurate and up-to-date.
Importance of Accurate Document Evaluation Responses
When it comes to handling sensitive information, making precise decisions about how to categorize and protect documents is crucial. Any misjudgment in this process can lead to severe consequences, including unauthorized disclosure or mishandling of classified materials. The responsibility to assess the confidentiality of documents with accuracy is a vital part of ensuring national security and organizational integrity.
Accurate evaluations not only protect sensitive data but also ensure compliance with legal and regulatory standards. Failing to assign the correct level of protection could result in significant risks, from data leaks to legal repercussions. Therefore, those tasked with making these evaluations must have a strong understanding of the guidelines and protocols involved.
Key Consequences of Incorrect Decisions
- Risk of Unauthorized Disclosure: Improper handling of classified material can lead to unauthorized access by individuals without the proper clearance.
- Legal and Financial Penalties: Mistakes in classification can lead to legal consequences, including fines and other penalties for both individuals and organizations.
- Loss of Trust: Incorrect classifications can erode confidence in the organization’s ability to manage sensitive information, affecting relationships with external partners and government agencies.
Accuracy in this process is non-negotiable, and those responsible must take every step to ensure their decisions align with established guidelines and standards. Effective training, attention to detail, and a commitment to following proper procedures are essential to preventing mistakes and maintaining the integrity of the security system.
Common Mistakes in Document Evaluation Assessments
When tasked with assessing sensitive materials, individuals often encounter common pitfalls that can lead to incorrect decisions. These mistakes, whether due to misinterpretation or lack of attention to detail, can compromise the integrity of the security process. Understanding these frequent errors is essential for anyone involved in document handling and evaluation, as it helps prevent costly missteps.
Overlooking Key Guidelines
A frequent mistake is failing to carefully follow the established guidelines when determining how a document should be protected. These rules provide clear instructions for making classification decisions, but individuals may overlook specific details or apply them inconsistently. This can result in misclassifying documents, either by assigning them too high or too low a security level.
Confusing Security Markings
Another common error is misunderstanding or incorrectly interpreting the security markings on documents. These labels are essential for ensuring that sensitive information is handled correctly, but if they are misread or ignored, it can lead to improper handling or unauthorized disclosure. Understanding the significance of each marking and how it relates to document security is crucial for making accurate assessments.
Preparing for the Document Evaluation Assessment Effectively
Proper preparation is key to succeeding in any evaluation related to sensitive material handling. Understanding the guidelines, practicing the procedures, and reviewing past content are essential steps for anyone who needs to assess the confidentiality of documents. A well-prepared individual is more likely to make accurate decisions and avoid common mistakes.
Review Key Guidelines and Protocols
One of the most important preparation steps is to thoroughly review the guidelines and protocols that govern the evaluation process. These rules outline the correct procedures for assessing the security level of documents and are essential for making informed decisions. By familiarizing yourself with these standards, you will better understand how to apply them consistently and accurately in real-world scenarios.
Practice with Sample Scenarios
Another effective strategy is to practice with sample scenarios that mimic real-life situations. These exercises allow you to apply the concepts you’ve learned and test your ability to make correct decisions under realistic conditions. Practicing different types of documents and security scenarios will help you build confidence and improve your ability to respond quickly and accurately when needed.
What to Expect During the Assessment
Understanding what to expect during the evaluation process is crucial for success. This section provides an overview of the format and structure, helping you prepare mentally for the types of questions and scenarios you will encounter. The process is designed to test your knowledge and ability to apply security guidelines to real-world situations, ensuring that sensitive materials are handled appropriately.
Assessment Format and Structure
The assessment will generally consist of multiple-choice questions, situational scenarios, and practical examples that test your understanding of security protocols. Each question is crafted to evaluate how well you can identify the correct procedures for handling classified information. It is important to read each question carefully and consider all options before selecting your response.
Types of Questions

Questions during the assessment will focus on several key areas, including the correct application of security standards, identifying document markings, and understanding the handling protocols for different types of materials. Below is a breakdown of the types of questions you may encounter:
| Category | Description |
|---|---|
| Document Markings | Questions regarding the proper interpretation and application of security labels on documents. |
| Procedural Application | Scenarios testing your ability to apply security protocols to various situations involving classified information. |
| Regulatory Knowledge | Questions focused on the rules and regulations surrounding the classification and protection of sensitive material. |
It is essential to approach each question with careful attention, making sure to apply your knowledge of security procedures and guidelines in every situation. Understanding the structure and types of questions will help you stay focused and confident during the assessment.
How to Approach Multiple-Choice Questions
Multiple-choice questions are a common format used to assess knowledge and understanding. When faced with this type of question, it’s important to have a strategic approach to increase your chances of selecting the correct answer. By staying organized and methodical, you can confidently navigate through each question and avoid common pitfalls.
Read Each Question Carefully
The first step in tackling multiple-choice questions is to carefully read the entire question. Pay attention to key words and phrases that may help clarify the context. Understanding exactly what is being asked ensures that you don’t make unnecessary mistakes due to misinterpretation. Avoid rushing through questions and take your time to absorb all the details.
Evaluate All Options Before Answering
Once you’ve read the question, carefully evaluate all of the answer choices. Often, multiple options may seem plausible, but there will be one that is the best fit based on your knowledge. Eliminate any obviously incorrect answers first to narrow down your choices. Then, compare the remaining options and choose the one that most accurately aligns with your understanding of the material.
Additionally, watch out for “distractor” answers–incorrect choices designed to seem similar to the correct one. These are often included to test your attention to detail and understanding of the material. Be sure to review all the choices before making a final decision.
Tips for Memorizing Classification Guidelines
Memorizing guidelines related to document security can be a challenging task, but it is essential for making accurate decisions in real-world scenarios. Effective memorization techniques can help you retain the information you need and apply it consistently. The following tips will assist you in remembering key principles and procedures for handling sensitive materials.
Break Information Into Manageable Chunks
One of the most effective ways to memorize guidelines is by breaking them down into smaller, more digestible pieces. Instead of trying to memorize large sections of information all at once, focus on smaller chunks. This method, known as “chunking,” helps to prevent overload and makes it easier to recall specific details when needed.
- Divide guidelines into categories (e.g., document types, security levels, handling procedures).
- Focus on one category at a time before moving on to the next.
- Review each category until you can recall the information without looking at your notes.
Use Mnemonics and Associations
Mnemonics are memory aids that help you remember complex information. Creating associations between the guidelines and familiar concepts can also help reinforce your memory. For example, you can create acronyms or memorable phrases that summarize the main points of the guidelines.
- Make acronyms from key terms (e.g., using the first letter of each principle to create a word or phrase).
- Visualize the process by creating mental images or flowcharts to represent the steps.
- Relate new information to something you already know to strengthen your memory connections.
Incorporating these strategies into your study routine will help you retain important guidelines and apply them with confidence during assessments or in practical situations.
How to Avoid Classification Errors
Making errors in determining the security level of documents can lead to serious consequences. To avoid misclassifications, it’s essential to have a clear understanding of the guidelines and follow a structured approach when reviewing materials. By paying close attention to detail, adhering to proper procedures, and using effective strategies, you can significantly reduce the likelihood of errors in judgment.
Review the Guidelines Thoroughly
The first step to preventing mistakes is ensuring that you have a comprehensive understanding of the relevant standards. Regularly reviewing the guidelines will help reinforce your knowledge and make it easier to apply them correctly in various situations.
- Make sure you are familiar with the criteria for different security levels.
- Understand the rules for marking documents and handling sensitive information.
- Stay updated on any changes or revisions to the procedures.
Follow a Step-by-Step Approach

Instead of rushing through the process, take your time to assess the documents carefully. Establishing a step-by-step approach can help ensure that no details are overlooked. By following a consistent method, you reduce the risk of overlooking crucial factors that could lead to misclassification.
- Identify key information before making a decision (e.g., classification markings, content sensitivity).
- Consult relevant references or experts if you’re unsure about the correct classification.
- Double-check your decision before finalizing the classification process.
By implementing these strategies, you can improve your accuracy and minimize the chances of making errors in the classification process.
Commonly Tested Topics on the Exam
When preparing for assessments related to document security, it’s important to focus on the core concepts that are frequently tested. Understanding the key topics will help you navigate through the questions more effectively and increase your chances of success. Certain areas are typically emphasized, and having a solid grasp of these subjects is crucial for performing well on the test.
Document Markings and Handling Procedures
One of the most important areas covered in the assessment is understanding the correct markings for different types of documents. Knowing when and how to apply specific labels, as well as how to handle classified materials, is essential. Questions often focus on identifying the appropriate symbols, classification levels, and storage methods required for secure management.
- Identification of different security levels.
- Correct procedures for document storage and transmission.
- Understanding of authorized access and handling restrictions.
Security Impact and Information Sensitivity
Another key area that is commonly tested is the impact of releasing certain information. Understanding how information sensitivity affects security is crucial for making informed decisions. Questions may revolve around evaluating the risks associated with disclosing sensitive details and the potential consequences for national security.
- Assessing the sensitivity of information based on context.
- Recognizing the potential risks of unauthorized disclosure.
- Determining appropriate protective measures for sensitive data.
By familiarizing yourself with these topics, you will be better prepared to answer questions accurately and with confidence during the assessment.
Understanding Classification Markings and Labels
In any environment where sensitive information is managed, understanding how to properly mark and label documents is a critical skill. These markings serve as a guide to identify the level of sensitivity and the required precautions for handling, storing, or sharing specific materials. A clear understanding of how these labels function can help ensure that documents are appropriately protected from unauthorized access or disclosure.
Types of Security Markings
Documents containing sensitive information are typically labeled with various security markings to indicate their level of confidentiality. These markings help personnel understand the potential risks associated with the material and ensure that it is handled correctly.
- Top Secret: Indicates the highest level of sensitive information, with strict controls on access and distribution.
- Secret: Represents sensitive information that could cause harm to national security if disclosed.
- Confidential: Information that, if revealed, could harm interests but not to the extent of “Secret” material.
- Unclassified: Materials that are not considered sensitive but may still contain proprietary or restricted data.
Additional Labeling Requirements
In addition to the main classification levels, documents often require other specific labels that further clarify their handling procedures. These additional markers provide detailed instructions regarding how the material should be used or shared.
- Declassification Date: Specifies when the document is eligible for declassification, or public release.
- Releasability: Identifies who is authorized to view or access the document, including any restrictions based on clearance level.
- Special Handling Instructions: Provides specific guidance on the handling, storage, or destruction of the document to prevent unauthorized access.
By understanding these classifications and their corresponding labels, individuals can ensure that sensitive documents are properly protected, reducing the risk of unauthorized access or misuse.
What is Declassification and Downgrading?
In the realm of information security, it is important to understand the processes that allow for the change in the sensitivity level of certain materials. These processes are known as declassification and downgrading. Both are methods used to adjust the access restrictions or confidentiality levels of previously protected information, either by making it publicly available or reducing its level of sensitivity.
Declassification
Declassification refers to the formal decision to remove the restricted status of a document or material, making it accessible to the public or to a wider group of individuals. This decision is typically based on the passage of time or changes in the relevance of the information contained within the document. The purpose is to promote transparency while still safeguarding sensitive information when necessary.
- Public Access: Once declassified, the document becomes available to the general public or specific authorized individuals.
- Time-based Declassification: Many documents are declassified after a set period has passed, such as 5, 10, or 25 years.
- Review Process: Before declassification, documents are reviewed to ensure that no sensitive or classified material is inadvertently released.
Downgrading

Downgrading is a process that reduces the sensitivity level of a document or material without making it fully accessible to the public. This may happen when a document that was once considered highly sensitive no longer requires such stringent protection due to changes in the geopolitical environment or the expiration of a specific threat.
- Lowering Security Level: A document that was once “Top Secret” may be downgraded to “Secret” or “Confidential” if it no longer contains critical information.
- Controlled Access: Even after downgrading, the document may still be accessible only to individuals with specific clearance levels.
- Re-evaluation: Downgrading typically occurs after a review process that assesses the ongoing relevance and risks associated with the document.
Both declassification and downgrading help balance national security needs with the principle of transparency, allowing for controlled access to important information as circumstances evolve.
Using the Security Classification Guide
A Security Classification Guide (SCG) is an essential tool used by authorized individuals to determine the level of protection required for specific types of information. It provides detailed instructions on how to categorize and safeguard materials based on their sensitivity. By following these guidelines, personnel can ensure that they are applying the appropriate security measures and maintaining the integrity of sensitive information.
Purpose of the Security Classification Guide
The primary purpose of a Security Classification Guide is to establish a clear framework for handling sensitive data, ensuring consistency and compliance with security protocols. It acts as a reference document, guiding personnel on how to apply security measures appropriately. This guide outlines the conditions under which information should be classified and specifies the required handling and access protocols.
- Provides Clarity: The guide helps to clarify what qualifies as sensitive information and how it should be protected.
- Ensures Consistency: By following the guide, personnel can apply security measures consistently across all information.
- Defines Handling Procedures: The guide includes specific instructions on how to manage, store, and disseminate classified material safely.
How to Use the Security Classification Guide
To use the SCG effectively, individuals must be familiar with its contents and follow the steps outlined for classifying and safeguarding information. This includes identifying the nature of the information, reviewing the guide’s recommendations, and applying the correct classification based on the guidelines provided. Below are some common steps to follow when utilizing the SCG:
- Identify the Information: Determine the type of information you are handling and whether it falls under specific protection categories.
- Review Classification Criteria: Examine the guide to understand the criteria that apply to your specific type of information.
- Apply Classification: Based on your review, assign the appropriate classification level to the information.
- Follow Handling Instructions: Ensure that you adhere to the storage, distribution, and disposal procedures outlined in the guide.
By understanding and utilizing the Security Classification Guide properly, individuals can play an integral role in safeguarding sensitive information while maintaining compliance with security protocols.
Reviewing the Directive 5200.1

Directive 5200.1 provides crucial guidelines for managing and safeguarding sensitive information across various sectors of government and military operations. It establishes a framework for protecting national security and ensuring that classified materials are handled in accordance with specific security protocols. Understanding this directive is essential for anyone involved in the processing, storing, or dissemination of sensitive data.
This directive lays out the responsibilities of personnel in safeguarding classified information, as well as the procedures for determining the appropriate levels of protection for different types of information. It serves as a key reference for understanding how to align with security standards and maintain compliance with the protection requirements for sensitive materials.
Key Provisions of Directive 5200.1
Directive 5200.1 is built around several important principles aimed at ensuring the integrity and confidentiality of sensitive information. The following provisions are central to its guidance:
- Security Requirements: Establishes clear security requirements for handling classified materials, ensuring that all personnel understand their obligations.
- Responsibility of Personnel: Outlines the specific duties of individuals in safeguarding classified information, from classification to dissemination.
- Compliance and Accountability: Ensures that personnel are held accountable for adhering to security protocols, with detailed procedures for monitoring and reporting compliance.
How the Directive Affects Security Practices
The provisions within Directive 5200.1 directly impact the daily operations of those handling classified materials. By adhering to its guidelines, personnel ensure that sensitive information is protected from unauthorized access, alteration, or destruction. This helps prevent security breaches and ensures that sensitive information remains within the bounds of security regulations. The directive also emphasizes the importance of maintaining records of access to and handling of classified data, further strengthening overall security measures.
Overall, Directive 5200.1 provides a critical framework for ensuring that classified information is managed securely. Understanding its provisions is essential for maintaining the highest standards of information security and supporting national defense efforts.
The Role of the Classifier in Security
The individual responsible for determining the level of protection required for sensitive materials plays a critical role in safeguarding national security. This role involves carefully evaluating information to assess its security needs and ensuring that it is adequately protected according to established guidelines. A classifier must possess a deep understanding of security protocols and the potential risks of mishandling information.
The classifier’s primary task is to make informed decisions about which information requires safeguarding and to what extent. They must evaluate the content in question, consider its potential impact on national security, and assign appropriate protection levels. This process helps ensure that sensitive information does not fall into the wrong hands or become compromised in any way.
Key Responsibilities of the Classifier
The role of the classifier is multifaceted, and their responsibilities extend beyond simple data assessment. Some of their key duties include:
- Evaluation of Information: Classifiers must thoroughly examine materials to determine if they contain sensitive data that requires safeguarding.
- Application of Security Measures: Once a decision is made, classifiers assign the appropriate level of protection, such as restrictions on access or handling procedures.
- Documentation and Reporting: Classifiers are also responsible for maintaining accurate records of the classification decisions made and any related actions taken, ensuring transparency and accountability.
The Impact of Accurate Classification
Accurate classification decisions are essential for maintaining the integrity of security systems. The proper handling of sensitive information ensures that it is protected against unauthorized access, which could potentially jeopardize national security. A classifier’s decisions can prevent unnecessary risk and maintain the trust and effectiveness of security programs across various sectors. By assigning the right level of security protection, classifiers contribute directly to preventing leaks, espionage, and other security threats.
Ultimately, classifiers are integral to the overall security framework, helping to maintain a balance between the need for transparency and the necessity of protecting sensitive information.
Benefits of Passing the Classification Exam
Successfully completing a certification test in security protection protocols brings numerous advantages for professionals working with sensitive information. It not only enhances one’s qualifications but also opens doors to various opportunities in the field of national security and information protection. Passing such a test demonstrates a high level of expertise and knowledge in handling and managing classified materials, making individuals valuable assets to their organizations.
The process of certification ensures that professionals possess the necessary skills and understanding of security practices. It helps individuals become proficient in managing sensitive data in accordance with regulations, and it also boosts their credibility in the workplace. Furthermore, passing the certification can lead to career advancement, as it indicates to employers that the individual is well-versed in maintaining the integrity and confidentiality of critical information.
Key Advantages
Here are some of the primary benefits for individuals who pass the certification test:
- Career Advancement: Successfully passing the test can increase opportunities for promotions and higher positions in the field of security and information management.
- Professional Recognition: Being certified highlights a person’s qualifications, earning them recognition as a trusted expert in their field.
- Increased Job Security: With a strong understanding of classification protocols, certified professionals are seen as indispensable to organizations requiring secure handling of sensitive data.
- Enhanced Knowledge: The preparation and successful completion of the certification process increase knowledge in security regulations and guidelines, making professionals more efficient and effective in their roles.
Opportunities for Growth

Achieving certification creates a solid foundation for further professional development. It allows individuals to pursue advanced training or specialized roles that require a higher level of responsibility. Many organizations value certified individuals and offer them opportunities to work on higher-profile projects, manage sensitive information, or contribute to policy development. Additionally, certification can lead to increased pay, as organizations often offer financial incentives to professionals with recognized security qualifications.
| Benefit | Description |
|---|---|
| Career Advancement | Increases the chances of promotions and growth within the organization. |
| Professional Recognition | Earns respect and recognition as an expert in information security. |
| Job Security | Establishes individuals as key personnel in handling sensitive data. |
| Knowledge Growth | Enhances understanding of security protocols and best practices. |
In conclusion, passing the certification not only improves individual career prospects but also contributes to overall organizational security by ensuring that professionals are capable of managing classified data effectively. This certification provides individuals with a strong platform for long-term success in the field of information security.
Post-Exam Tips for Success
After completing an assessment, it’s essential to focus on the next steps that contribute to long-term success. This phase involves reflecting on performance, managing stress, and preparing for future challenges. Whether the goal is to improve on weak areas or maintain strengths, the approach after the test is just as important as preparation.
Review and Reflect
Take the time to analyze your responses and the areas where you might have struggled. Understanding your mistakes can provide valuable insights and help you refine your approach in the future. Reviewing materials related to the topics can help solidify your knowledge and ensure that any gaps are addressed effectively.
Maintain a Balanced Mindset
Staying calm and focused after the test is crucial. While it’s natural to feel anxious, maintaining a positive and balanced mindset allows you to move forward without dwelling too much on the past. It’s also helpful to celebrate small wins and acknowledge your progress.
Stay Organized and keep track of deadlines and upcoming tasks. Being prepared for what’s next ensures you stay on top of your goals and manage stress effectively.