
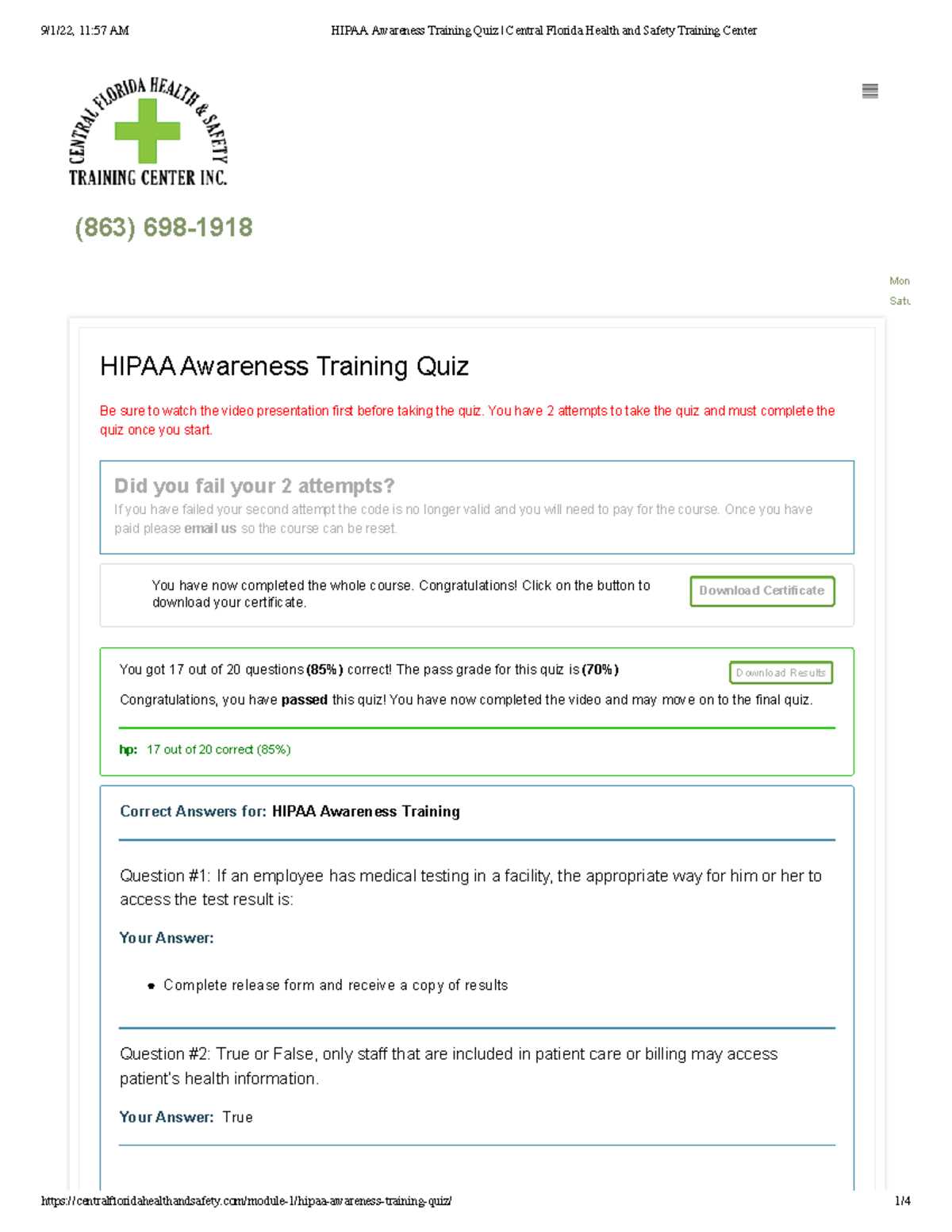
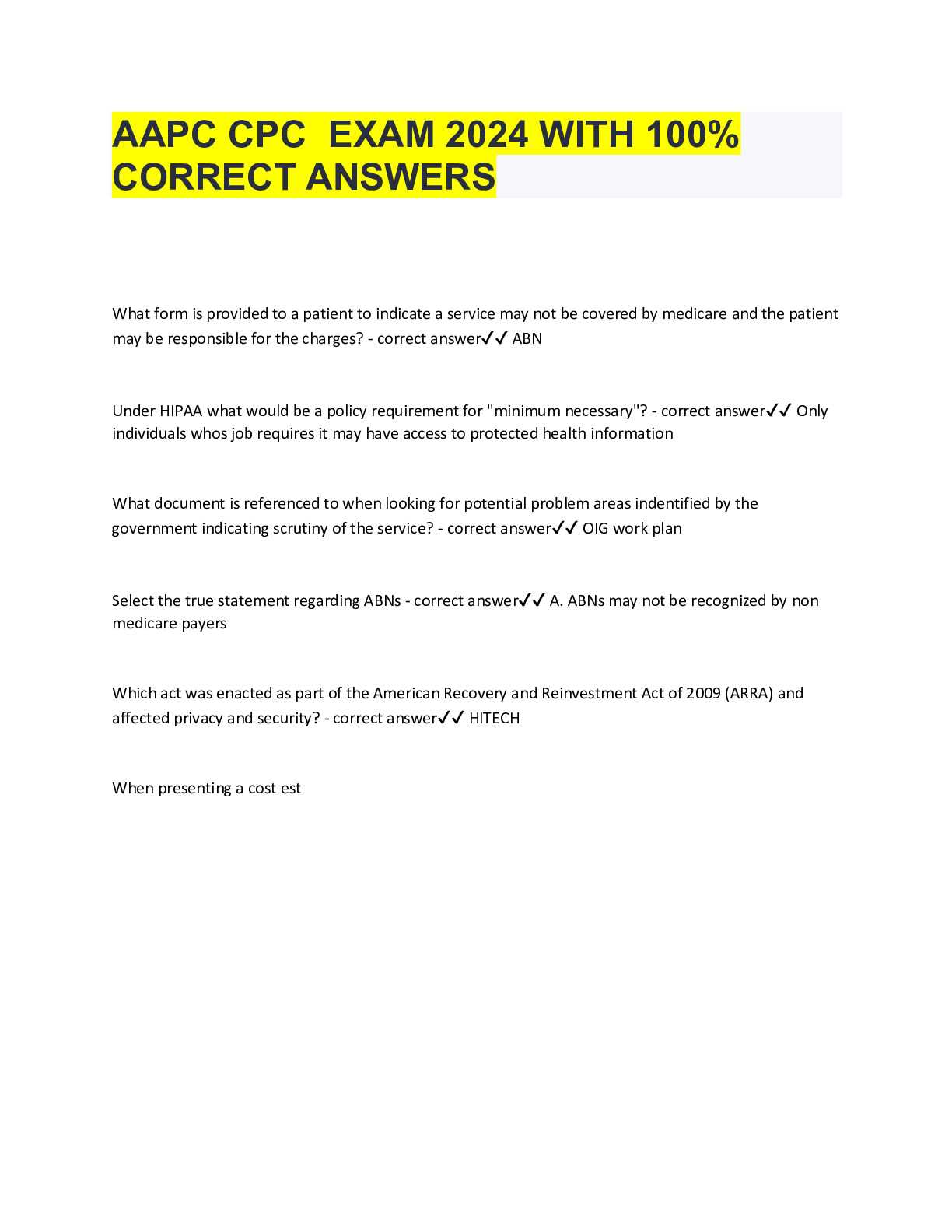
Healthcare professionals must understand the importance of safeguarding sensitive patient data and adhering to regulations that ensure confidentiality and integrity. A comprehensive grasp of these requirements is essential for passing any assessments related to data protection in medical settings.
Proper preparation involves studying key topics that test your knowledge of security protocols, privacy rules, and the best practices for handling personal health information. Understanding these principles not only helps you perform well on required tests but also builds confidence in your ability to maintain privacy in real-world situations.
Effective study strategies should focus on mastering regulatory guidelines, identifying common pitfalls, and gaining clarity on critical concepts. By the end of this section, you’ll be equipped to approach any related challenges with a well-rounded understanding of the subject matter.
Essential Guide to Healthcare Privacy and Security Assessments
In the healthcare industry, professionals are required to demonstrate a thorough understanding of privacy and security measures designed to protect patient information. This guide focuses on preparing individuals for assessments that test their knowledge in this critical area. By mastering key concepts and rules, candidates can ensure they are fully equipped to comply with legal requirements and contribute to a secure healthcare environment.
Preparation for these evaluations involves familiarizing oneself with core regulations, understanding how to implement security protocols, and knowing the appropriate actions to take when handling sensitive data. It’s essential to be aware of the specific laws governing data protection and how they apply to daily operations in healthcare settings.
To succeed, individuals should focus on the major components of healthcare privacy, including confidentiality, access controls, and breach protocols. Understanding the nuances of each area will enable candidates to answer related questions with confidence and accuracy. Proper preparation ensures that healthcare workers can meet compliance standards while maintaining trust with patients and colleagues alike.
Understanding Healthcare Privacy and Security Compliance Basics
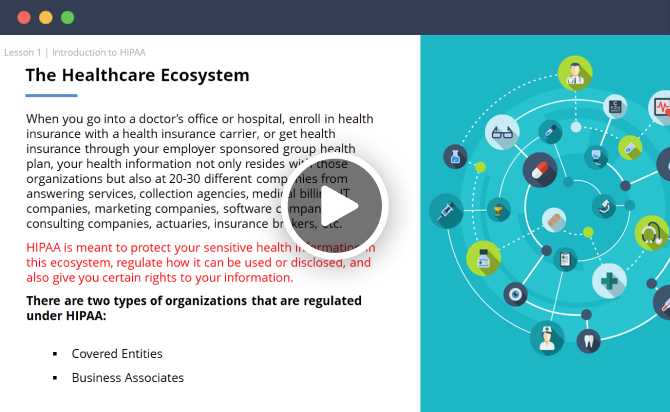
Compliance with regulations surrounding the protection of patient information is a cornerstone of the healthcare industry. Professionals must be well-versed in the fundamental principles that ensure sensitive data remains secure and confidential. These guidelines are designed to prevent unauthorized access, sharing, or misuse of personal health details.
The key elements of privacy and security compliance can be broken down into several core concepts:
- Confidentiality: Ensuring that patient information is only accessible to authorized personnel.
- Integrity: Maintaining the accuracy and completeness of patient records throughout their lifecycle.
- Availability: Ensuring that information is accessible when needed by authorized individuals.
Additionally, professionals should be aware of the specific rules that govern data usage and the security measures that must be implemented to protect against breaches. These regulations provide a framework for healthcare organizations to create systems that safeguard data while promoting effective care.
Understanding these basics is essential not only for legal compliance but also for building trust with patients and maintaining a secure healthcare environment. Proper training and continuous learning are key to staying updated on evolving standards and regulations in this area.
Key Principles for Healthcare Privacy

Protecting patient data is a critical responsibility for all healthcare professionals. The principles that guide the privacy of sensitive health information are essential to ensuring both compliance and trust. These fundamental concepts serve as the foundation for creating policies and procedures that safeguard confidentiality in healthcare settings.
The core principles of healthcare privacy include maintaining strict controls over data access, ensuring transparency in information handling, and establishing mechanisms to detect and prevent unauthorized disclosures. These principles not only protect patients but also uphold the integrity of the healthcare system as a whole.
| Principle | Description |
|---|---|
| Confidentiality | Ensures that patient data is shared only with authorized individuals. |
| Transparency | Clearly communicates how patient information will be used and protected. |
| Data Minimization | Limits the collection and use of patient data to only what is necessary for care. |
| Accountability | Holds healthcare providers responsible for safeguarding patient information. |
| Integrity | Ensures that health information is accurate and not altered without proper authorization. |
By adhering to these principles, healthcare providers can ensure that patient information is securely managed and that privacy standards are consistently met across all levels of care.
Common Questions on Healthcare Privacy Assessments
During assessments focused on healthcare privacy and security, individuals often encounter questions that test their understanding of key regulations and procedures for safeguarding patient information. These questions are designed to evaluate one’s knowledge of the rules governing confidentiality, data access, and security measures in the medical field. Being familiar with the most frequently asked questions can help individuals prepare effectively and approach the assessment with confidence.
Here are some examples of topics commonly covered in privacy-related evaluations:
- How to handle protected health information (PHI) under various circumstances.
- What actions to take when a breach or unauthorized access occurs.
- The rights of patients regarding their personal health data.
- When and how healthcare professionals can share patient data with others.
- Understanding the penalties for non-compliance with privacy regulations.
Familiarizing yourself with these areas is key to passing the assessment and ensuring ongoing compliance with healthcare privacy standards. By focusing on the most relevant topics, individuals can strengthen their understanding of healthcare regulations and their role in protecting sensitive information.
How to Prepare for Healthcare Privacy and Security Assessment
Preparing for assessments related to healthcare privacy and security requires a focused approach that covers the core principles, regulations, and best practices for protecting patient data. A thorough understanding of the rules and guidelines is essential to succeed and ensure compliance with industry standards. This preparation will help healthcare professionals navigate the complexities of data security and privacy in their day-to-day work.
Study the Key Regulations

Start by reviewing the key regulations that govern the protection of personal health information (PHI). Focus on understanding the privacy rules, security protocols, and breach notification requirements. Familiarity with these concepts will help you apply them accurately during the assessment and in your professional practice.
Utilize Practice Questions and Study Guides
One of the most effective ways to prepare is by using practice questions and study materials tailored to the topics covered in privacy assessments. These resources provide insight into the type of questions you may face and offer opportunities to reinforce your knowledge. Consistent practice will improve your confidence and readiness.
By following these steps and dedicating time to study, you will be well-equipped to pass the assessment and demonstrate a strong understanding of healthcare privacy and security practices.
HIPAA Security Rule Explained
The security rule is a vital component in the framework designed to protect sensitive patient information from unauthorized access, breaches, and misuse. It sets out a series of safeguards that healthcare organizations must implement to ensure the confidentiality, integrity, and availability of electronic health information. Understanding the specifics of these requirements is essential for maintaining a secure environment in healthcare settings.
Key Components of the Security Rule
The security rule is divided into three main areas: administrative safeguards, physical safeguards, and technical safeguards. Each of these areas focuses on different aspects of protecting electronic health data.
- Administrative Safeguards: Policies and procedures that manage the selection, development, implementation, and maintenance of security measures to protect electronic health information.
- Physical Safeguards: Measures to protect electronic systems and related buildings from unauthorized physical access, tampering, or theft.
- Technical Safeguards: Technologies and systems designed to protect and control access to electronic health records, including encryption and access controls.
Implementing the Security Rule
To comply with the security rule, healthcare organizations must ensure that they implement appropriate measures in each of the three areas. This includes assigning responsibility for security management, conducting regular risk assessments, and ensuring that systems are in place to monitor and track access to patient data. By following these guidelines, healthcare providers can better protect their patients’ information and ensure compliance with regulatory standards.
Protected Health Information Overview
Protected health information (PHI) refers to any personal data related to an individual’s health status, treatment, or payment for healthcare services that is safeguarded by privacy regulations. This information must be securely handled to ensure patient confidentiality and prevent unauthorized access. Understanding what constitutes PHI and how to manage it is a crucial aspect of compliance in healthcare settings.
Types of Protected Health Information
PHI can include a wide range of information, both in electronic and physical forms. The most common examples include:
- Medical records, including diagnosis and treatment details
- Test results and lab reports
- Insurance information and payment history
- Personal identifiers such as names, addresses, phone numbers, and social security numbers
How to Safeguard Protected Health Information
Healthcare organizations must take steps to protect PHI by implementing various safeguards. These include both technical measures, such as encryption and secure communication channels, and administrative measures, such as policies governing access to sensitive data. Additionally, training healthcare professionals on the importance of confidentiality and secure data handling is essential for maintaining compliance.
Common Mistakes on Healthcare Privacy and Security Assessments
When preparing for assessments focused on healthcare privacy and security, candidates often make certain errors that can affect their performance. These mistakes typically stem from misunderstandings of key regulations, improper interpretations of scenarios, or a lack of attention to detail. Recognizing these common pitfalls can help individuals improve their readiness and avoid preventable errors during the assessment process.
Here are some common mistakes to be aware of:
| Mistake | Explanation |
|---|---|
| Confusing confidentiality with data integrity | Many candidates mix up these two concepts. While confidentiality focuses on keeping information private, data integrity ensures the information is accurate and unaltered. |
| Overlooking patient rights | Failing to recognize and understand patient rights under privacy laws can lead to mistakes, particularly when it comes to patient consent and access to their health records. |
| Neglecting to consider the consequences of non-compliance | Some may underestimate the penalties and repercussions of violating privacy standards, leading to incorrect responses regarding enforcement and penalties. |
| Misunderstanding the scope of “need to know” access | It’s crucial to correctly apply the “minimum necessary” rule, which dictates that only those with a legitimate need for information should have access to it. |
| Failing to account for emerging security threats | Many overlook new risks, such as cyber threats and data breaches, which are increasingly important in today’s healthcare environments. |
By recognizing these errors and dedicating time to understand the core principles of privacy and security regulations, individuals can better prepare for the assessment and avoid common mistakes that may hinder their success.
Importance of Confidentiality in Healthcare
Confidentiality is a cornerstone of trust between healthcare providers and patients. Safeguarding personal health information ensures that individuals can share sensitive details with their providers without fear of unauthorized disclosure. The protection of this data is not only a legal requirement but also a key ethical responsibility for healthcare professionals.
Why Confidentiality Matters
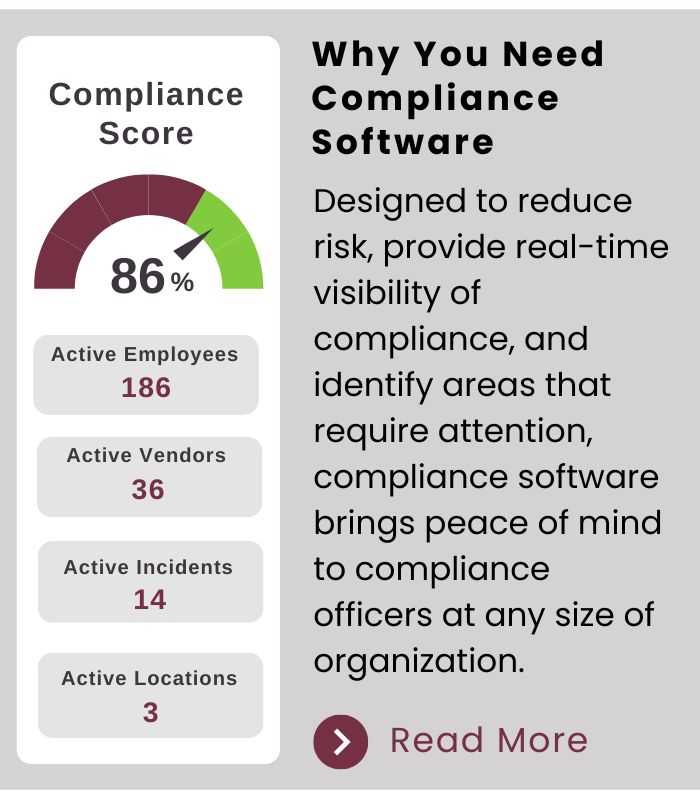
There are several key reasons why maintaining confidentiality in healthcare is crucial:
- Building Trust: Patients are more likely to seek care and disclose necessary information when they trust that their personal details will remain private.
- Respecting Patient Rights: Patients have the right to control who accesses their health information, which is integral to their autonomy and dignity.
- Preventing Harm: Unauthorized access or exposure of sensitive health data can lead to reputational damage, discrimination, and other forms of harm to individuals.
- Ensuring Legal Compliance: Healthcare organizations must adhere to laws and regulations designed to protect patient data, avoiding significant legal consequences for breaches.
Consequences of Breaching Confidentiality
Failing to protect patient information can have severe consequences for both healthcare professionals and institutions. These may include:
- Loss of patient trust and loyalty
- Legal actions, fines, and sanctions
- Damage to professional reputation and career
- Potential harm to patients due to improper sharing of their health information
Maintaining confidentiality is essential not only to comply with legal standards but also to foster an environment where patients feel safe and supported in their healthcare journey.
Roles of Healthcare Workers Under Privacy and Security Regulations

Healthcare workers play a critical role in ensuring the protection of sensitive patient information. They are responsible for safeguarding privacy, maintaining confidentiality, and adhering to security measures when handling personal health data. Each healthcare worker, from doctors to administrative staff, has specific duties to comply with privacy regulations, which are essential for creating a secure and trustworthy healthcare environment.
Responsibilities of Healthcare Providers
Healthcare providers, including doctors, nurses, and specialists, have direct responsibilities when it comes to protecting patient information:
- Patient Confidentiality: Providers must ensure that any health information they access or discuss remains confidential and is only shared with those who have a legitimate need to know.
- Secure Data Handling: Providers are responsible for implementing appropriate security measures to protect patient data during storage, transmission, and retrieval.
- Patient Rights: Healthcare providers must inform patients about their rights related to their personal health data and respect those rights at all times.
Roles of Administrative and Support Staff
Administrative staff and support workers, while not directly involved in patient care, also play an essential role in safeguarding health information:
- Access Control: Administrative personnel must ensure that only authorized individuals have access to sensitive health information.
- Compliance with Policies: All healthcare workers, including administrative and clerical staff, must follow organizational policies related to data protection and confidentiality.
- Training and Awareness: Staff should be regularly trained on privacy regulations and the proper handling of patient information to minimize the risk of accidental breaches.
By understanding and fulfilling their respective roles, healthcare workers contribute to a culture of compliance and help maintain the trust that patients place in the healthcare system.
What to Expect on the Certification Assessment
When preparing for the final assessment related to healthcare privacy and security, it’s important to understand what topics and areas will be covered. The test is designed to evaluate your knowledge of key regulations, concepts, and practical applications related to safeguarding patient information. Candidates should be prepared for questions that assess both theoretical knowledge and the ability to apply it in real-world scenarios.
Key Topics Covered
During the assessment, expect to encounter questions that test your understanding of several critical areas, such as:
- Privacy and Security Regulations: You will be tested on the legal frameworks and standards that govern the protection of healthcare data.
- Data Handling and Encryption: Expect questions on how to securely store, transmit, and manage sensitive patient information.
- Patient Rights and Consent: You’ll need to demonstrate knowledge of patient rights related to their personal health information, including consent and access procedures.
- Risk Management and Breach Protocols: Questions may focus on identifying and mitigating risks to patient data, as well as responding to potential security breaches.
Types of Questions to Anticipate

Prepare for a mix of question formats, including:
- Multiple Choice: These questions will test your recall of key facts and principles.
- Scenario-Based: These questions will present real-life situations requiring you to apply your knowledge to solve practical challenges.
- True/False: Some questions may test your understanding of specific policies or regulations.
With a clear understanding of the core topics and question formats, you’ll be better equipped to approach the assessment confidently and successfully.
Privacy Rule Essentials in Healthcare
The primary purpose of privacy regulations in the healthcare industry is to protect patients’ personal and medical information from unauthorized access or disclosure. These rules outline specific standards that organizations and healthcare professionals must follow to ensure that sensitive data remains secure while still allowing it to be shared when necessary for treatment, payment, or healthcare operations.
Core Principles of Privacy Protections
The key components of privacy rules are built around maintaining confidentiality and limiting the exposure of personal health information (PHI). These principles are crucial to safeguard individuals’ rights while promoting trust within the healthcare system:
- Confidentiality: Health information must be protected from unauthorized access, ensuring that only those with proper authorization can view or use it.
- Transparency: Patients should be informed about how their data will be used, stored, and shared, with clear consent obtained where necessary.
- Access and Control: Patients have the right to access their own information, request corrections, and restrict how their information is shared.
Enforcement and Compliance Obligations

Healthcare providers and organizations must take active steps to implement policies that comply with these privacy rules. This includes:
- Training and Awareness: Regular education for healthcare workers on how to protect patient data and maintain privacy.
- Audit and Monitoring: Continuous monitoring of data access and usage to detect potential breaches.
- Penalties for Non-Compliance: Violations of privacy rules can lead to fines, legal action, and reputational damage for organizations and individuals.
By adhering to these principles and regulations, healthcare professionals ensure they are both protecting patient rights and maintaining the integrity of the healthcare system.
Testing Your Knowledge of Healthcare Privacy Regulations
One of the most effective ways to gauge your understanding of the privacy and security standards in the healthcare field is through practical assessments. These evaluations help ensure that individuals working with sensitive health data have the necessary knowledge to protect it effectively. By testing your comprehension of key regulations, you can identify areas of strength and those that may need further attention.
Key Topics to Test Your Knowledge
To accurately assess your grasp of healthcare privacy principles, consider reviewing the following core concepts:
- Data Privacy and Confidentiality: Understanding the guidelines for safeguarding personal health information and who is authorized to access it.
- Patient Consent and Rights: Recognizing the importance of patient autonomy and ensuring they are informed about how their data is used and shared.
- Security Measures and Safeguards: Knowledge of physical, technical, and administrative measures to prevent unauthorized access and breaches.
- Compliance Requirements: Familiarity with the rules and obligations that organizations must follow to stay compliant with privacy regulations.
Testing Methods and Techniques
There are several ways to evaluate your understanding and preparedness:
- Practice Quizzes: Taking quizzes based on real-world scenarios can help reinforce key concepts and improve recall.
- Mock Assessments: Simulating the actual assessment environment can provide valuable insight into your readiness and highlight areas for improvement.
- Case Studies: Reviewing practical examples of data breaches or privacy violations can enhance your ability to apply theoretical knowledge to real-world situations.
By regularly testing your knowledge, you can build confidence in your understanding of privacy practices and ensure compliance with regulatory standards in the healthcare industry.
Tips for Answering Healthcare Privacy Questions
When preparing to respond to questions related to healthcare confidentiality and security regulations, it’s important to approach them strategically. Understanding the core principles of protecting patient information and maintaining compliance is essential for answering accurately. The following tips will help you enhance your ability to tackle questions effectively and efficiently.
Focus on Key Regulations
Before attempting any question, it’s crucial to have a solid grasp of the main concepts surrounding data protection in healthcare. Be sure to review the most critical aspects such as:
- Data Access: Who can access personal health records and under what circumstances.
- Patient Rights: Understanding patients’ rights to control their data and make informed decisions about its use.
- Security Measures: Knowing the technical, physical, and administrative safeguards in place to protect data.
Stay Calm and Read Carefully

When answering questions, carefully read each one to ensure you fully understand what’s being asked. Pay attention to keywords such as “must,” “always,” or “never,” which can alter the meaning of the question. Consider the context of each scenario and think about the regulations or best practices that apply in that situation.
Additionally, practice recalling real-life scenarios where these regulations have been applied, as this can help you quickly identify the correct answer when confronted with complex situations.
By following these strategies, you can improve your accuracy in responding to questions related to healthcare privacy standards and demonstrate your understanding of essential regulations.
Best Study Resources for Healthcare Privacy Certification
Preparing for a certification focused on healthcare confidentiality and data protection can be a challenging yet rewarding task. The key to success lies in using the right resources that cover both the fundamental principles and the practical application of regulations. Below are some of the most effective study materials to help you master the content and ensure your success.
Books and Study Guides
Comprehensive books and study guides are often the first step in preparing for certification assessments. These resources provide detailed explanations of regulations and standards, often with practice questions. Some popular options include:
- Healthcare Privacy and Security Compliance Manual: A thorough guide to privacy and security requirements, ideal for beginners.
- Official Compliance Textbooks: Books recommended by professional associations often include in-depth coverage of topics and real-world case studies.
- Certification Study Guides: Books specifically designed for exam prep with focus on practice questions and answers.
Online Courses and Webinars
Online courses are an excellent way to learn at your own pace and often come with interactive elements such as quizzes and videos. Many platforms offer comprehensive courses designed for certification, such as:
- Compliance Training Centers: Accredited institutions offer online modules that cover all essential topics and include mock tests to track progress.
- Webinars from Experts: Online seminars conducted by industry professionals who provide insights into the latest trends and updates in privacy regulations.
- Healthcare Associations: Many professional bodies offer webinars, often with a focus on legal and operational compliance in healthcare environments.
Practice Tests and Question Banks
Practice exams are crucial to gauge your readiness. These resources simulate the real assessment experience and help you identify areas that need further review:
- Online Question Banks: Websites offering hundreds of practice questions, many of which are designed by experts in the field.
- Mock Exams: Full-length practice tests that mirror the structure and timing of the actual certification exam.
Discussion Forums and Study Groups

Engaging with peers who are also studying for certification exams can enhance your learning experience. Study groups and discussion forums allow you to share knowledge, clarify doubts, and learn from others:
- Online Forums: Websites where students and professionals discuss key topics related to privacy and security, providing tips and resources.
- Study Groups: Local or virtual groups where learners meet regularly to discuss materials and quiz each other on the content.
By utilizing these resources, you can build a solid foundation of knowledge and boost your confidence in passing your healthcare privacy certification.
Understanding Breach Notifications
In healthcare, ensuring the security of sensitive data is crucial, and when a security breach occurs, it is important to take immediate action. Breach notifications are an essential part of managing such incidents, ensuring that affected individuals are informed, and regulatory bodies are notified in a timely manner. These notifications are part of a larger framework that ensures the protection and transparency of confidential information.
What Constitutes a Breach?
A breach occurs when there is an unauthorized access or disclosure of protected health information (PHI) that compromises its confidentiality, integrity, or availability. This can happen through various means, such as hacking, accidental sharing, or physical theft. Understanding the criteria for a breach is the first step in determining when a notification is required.
Notification Requirements
Once a breach has been identified, it is vital to follow specific notification protocols to ensure compliance. These notifications must be provided to the affected individuals and regulatory authorities within a prescribed timeframe. The following table outlines the key elements of breach notifications:
| Notification Type | Timeframe for Notification | Details to Include |
|---|---|---|
| Individual Notification | Within 60 days of discovery | Details of the breach, the type of information involved, and the steps individuals can take to protect themselves. |
| Regulatory Notification | Within 60 days for breaches affecting 500+ individuals | Must be sent to the U.S. Department of Health and Human Services (HHS), with a description of the breach and corrective actions. |
| Media Notification | If more than 500 individuals are affected and contact information is insufficient | Notification should be sent to prominent media outlets serving the affected area. |
Best Practices for Handling Breaches
To avoid potential breaches or mitigate their impact, healthcare organizations should implement robust security measures and training programs. Additionally, organizations must have a clear protocol for identifying, reporting, and responding to security incidents. These best practices can help ensure that any breach is handled efficiently and in compliance with the regulations.
How to Handle HIPAA Violations
When a breach of confidentiality occurs involving sensitive patient information, it is critical to act swiftly and appropriately. Ensuring compliance with privacy and security rules is essential for maintaining trust in healthcare systems. Addressing violations efficiently and transparently helps to mitigate any potential risks and ensures the organization remains in compliance with the law.
Steps for Immediate Response
Upon identifying a potential violation, the first step is to assess the situation and determine the scope of the issue. This includes identifying which information was exposed, how the breach occurred, and who is responsible. A rapid response can help minimize damage and prevent further unauthorized access. Key actions to take include:
- Notify the relevant internal team members, including the compliance officer and legal team.
- Begin an investigation to assess the breach’s impact and gather evidence.
- Contain the breach and stop any further unauthorized access or disclosures.
- Document the incident thoroughly for reporting and review purposes.
Regulatory Reporting and Corrective Measures
Once the violation has been confirmed, organizations must follow the necessary reporting procedures. This may involve notifying affected individuals, reporting the breach to regulatory bodies, and possibly notifying the media if the breach impacts a large group of individuals. Depending on the nature of the violation, corrective actions may include:
- Implementing additional security measures to prevent future breaches.
- Providing training or refresher courses to staff on privacy and security protocols.
- Reviewing and updating internal policies and procedures to enhance compliance.
Properly handling violations ensures not only legal compliance but also demonstrates the organization’s commitment to protecting sensitive information and maintaining patient trust.
Final Thoughts on HIPAA Success
Achieving success in maintaining privacy and security in healthcare settings is not just about meeting legal requirements, but about creating a culture of awareness and responsibility. Protecting sensitive patient information requires continuous effort, collaboration, and education. Organizations that prioritize compliance and implement robust policies can better ensure trust and safeguard against potential risks.
Consistency and diligence are essential for maintaining compliance. Training staff regularly and updating procedures as new regulations emerge are key to staying ahead. Ensuring that all personnel understand the importance of protecting patient data is fundamental to creating a secure environment.
Long-term success relies on regular assessments of existing practices, adapting to changing laws, and cultivating a proactive approach. By fostering a culture where everyone plays an active role in privacy protection, organizations can minimize the risk of violations and maintain strong relationships with patients and regulatory bodies alike.