
In today’s digital world, safeguarding sensitive information has become a priority for organizations across all industries. With the rise of cyber risks originating from within companies, understanding how to prevent and mitigate these threats is essential for maintaining security. This section provides insight into key concepts and best practices for addressing internal risks.
Recognizing vulnerabilities within an organization’s infrastructure is crucial. Employees, contractors, and other insiders may unknowingly or intentionally compromise data. The ability to detect such risks requires a solid understanding of various warning signs and the tools available for early intervention.
Throughout this guide, we will explore effective strategies, tactics, and preventive measures to help strengthen your organization’s defenses. Whether you’re preparing for an assessment or seeking to enhance your knowledge, this content will provide the necessary foundation to better handle internal security challenges.
Insider Threat Exam Answers
Successfully addressing internal risks requires a deep understanding of the various factors that contribute to security breaches from within an organization. To effectively counteract these risks, it’s essential to grasp the core principles behind identifying vulnerabilities, applying preventive measures, and responding to potential incidents. This section outlines key strategies and critical knowledge that will help you navigate this area with expertise.
Essential Concepts in Risk Detection
Understanding the motivations and behaviors that lead to compromised systems is a critical step in preventing security issues. Employees, contractors, or anyone with access to sensitive information may inadvertently or intentionally cause harm. Familiarity with common red flags and the tools used for monitoring and analysis can significantly improve detection capabilities.
Preparing for Security Evaluations
Preparing for assessments related to organizational security demands a focus on practical knowledge. Knowing how to approach potential risks, recognizing warning signs, and implementing best practices can make a significant difference in achieving security objectives. Regular training, awareness programs, and scenario-based exercises provide a robust foundation for responding to internal security challenges.
Understanding Internal Risks in Cybersecurity
Within the realm of cybersecurity, protecting sensitive data from those who have authorized access is a significant challenge. Often, the most dangerous risks come from within the organization itself, whether intentional or accidental. Recognizing and addressing these risks is crucial for maintaining a secure environment.
There are several key factors to consider when evaluating internal security vulnerabilities:
- Access control: Proper management of who has access to what information can prevent unauthorized actions.
- Behavioral monitoring: Identifying unusual patterns in employee behavior can provide early signs of potential security breaches.
- Data protection: Ensuring that sensitive data is encrypted and properly secured reduces the risk of exposure.
By understanding these aspects, organizations can take proactive measures to protect their systems and minimize the impact of internal security risks. Additionally, implementing clear policies, regular training, and using advanced security tools can help reduce the likelihood of data compromise.
Types of Internal Security Risks
Internal security risks vary greatly depending on the nature of the organization and the level of access granted to individuals. Common types of risks include:
- Unintentional actions: Employees may unknowingly violate security protocols, leading to accidental data exposure.
- Malicious intent: Individuals with malicious intentions may exploit their access to sabotage systems or steal information.
- Negligence: Poor security practices, such as weak passwords or failure to update software, can create vulnerabilities.
Understanding these categories helps in developing strategies for monitoring and mitigating potential risks within the organization. Proper security awareness and intervention protocols are key to maintaining a safe digital environment.
Key Concepts in Internal Risk Detection

Effective detection of internal security risks relies on understanding certain fundamental principles. Identifying potential issues early on involves recognizing abnormal activities, analyzing user behavior, and applying security protocols that prevent data misuse. By mastering these concepts, organizations can better anticipate and respond to risks from within their workforce.
Behavioral Analysis and Monitoring
One of the most powerful tools in detecting internal risks is monitoring employee behavior. By tracking patterns of access, communication, and actions within the network, unusual behaviors can be flagged and investigated. Examples of concerning activities might include:
- Accessing data unrelated to the employee’s role
- Unexplained attempts to bypass security measures
- Frequent transfers of sensitive information to external devices or locations
These patterns can provide early indicators of potential misuse or risk, enabling proactive responses to mitigate possible harm.
Technology and Tools for Risk Detection
Advanced security tools are essential in helping organizations detect and manage internal risks. These tools can range from basic activity logs to sophisticated artificial intelligence systems that analyze user behavior and flag anomalies. Common technologies used in risk detection include:
- Security Information and Event Management (SIEM): A centralized platform that collects and analyzes security data in real time.
- User and Entity Behavior Analytics (UEBA): A technology that uses machine learning to identify deviations from typical user behavior.
- Data Loss Prevention (DLP): Systems designed to monitor and protect sensitive data from unauthorized access or transfer.
Utilizing these technologies in combination with clear policies and continuous training can significantly reduce the likelihood of internal risks affecting an organization.
Common Mistakes in Internal Risk Assessments
When preparing for assessments related to internal security, many individuals make several common errors that can impact their performance and understanding of the subject. These mistakes often stem from a lack of awareness of key concepts, improper application of tools, or overlooking critical details in case scenarios. Recognizing and avoiding these pitfalls is essential for accurate evaluation and effective risk management.
Overlooking Behavioral Indicators
One of the most frequent mistakes is neglecting to properly analyze employee behavior and actions. Many assessments focus too heavily on technical measures, missing the behavioral signals that can point to potential internal risks. Key factors such as:
- Unusual access patterns
- Changes in work habits or performance
- Increased interactions with sensitive data
are often overlooked, despite their significance in identifying problems before they escalate.
Relying Too Much on Technology

Another common error is placing too much trust in automated security tools without combining them with human oversight and analysis. While advanced software can certainly assist in detecting anomalies, it cannot replace the critical thinking and contextual understanding that come from manual investigation. Overreliance on technology can lead to missed risks or incorrect conclusions, especially when subtle, complex threats arise.
How to Identify Suspicious Behaviors
Recognizing unusual actions within an organization is essential for maintaining a secure environment. Certain behaviors can serve as warning signs of potential misuse or data compromise. Being able to spot these early indicators allows security teams to take proactive measures and mitigate risks before they escalate.
Suspicious behaviors often manifest in several ways, including:
- Unexplained access to sensitive data or systems outside of normal work duties.
- Frequent and unnecessary downloading or sharing of confidential information.
- Attempts to bypass security measures, such as disabling firewalls or security software.
- Changes in behavior, such as increased secrecy, reluctance to share information, or sudden withdrawal from colleagues.
- Accessing systems at odd hours or from unfamiliar locations without prior authorization.
Monitoring for these types of behaviors, combined with a strong security policy and response plan, is critical for detecting and addressing potential risks within the organization.
Techniques for Securing Sensitive Data
Protecting valuable information from unauthorized access is a fundamental aspect of maintaining organizational security. Implementing effective security techniques ensures that sensitive data remains secure from both internal and external risks. These techniques focus on limiting access, encrypting data, and regularly monitoring for potential vulnerabilities.
Data Encryption
One of the most effective ways to protect sensitive data is through encryption. By converting information into unreadable code, encryption ensures that even if data is intercepted, it remains inaccessible without the proper decryption key. Common encryption techniques include:
- Full disk encryption: Encrypting the entire hard drive to protect data stored on devices.
- File-level encryption: Encrypting specific files to protect them while in storage or transit.
- End-to-end encryption: Ensuring data is encrypted from the sender to the recipient, preventing access during transmission.
Access Controls and Monitoring
Another crucial technique in securing sensitive information is controlling who has access to it. Implementing strict access controls ensures that only authorized individuals can view or modify confidential data. Best practices include:
- Role-based access control (RBAC): Assigning access rights based on job roles, limiting exposure to only the necessary information.
- Multi-factor authentication (MFA): Requiring more than one form of identification to access sensitive data, adding an additional layer of security.
- Regular access reviews: Continuously assessing and updating access rights to ensure they align with current job responsibilities.
In addition to these techniques, continuous monitoring for unauthorized access attempts and maintaining secure backups of critical data help ensure ongoing protection and prompt response to potential security incidents.
Legal Aspects of Internal Security Risks
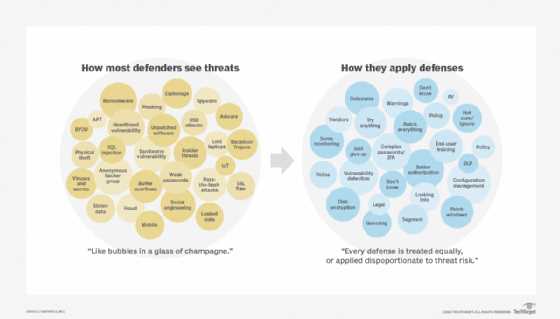
When addressing security risks originating from within an organization, it’s important to understand the legal implications involved. There are a range of laws and regulations designed to protect both the company and its employees from unlawful actions, including unauthorized access to sensitive information, data breaches, and intellectual property theft. Organizations must be aware of these legal frameworks to ensure they remain compliant while also protecting their assets.
Organizations are required to establish clear policies regarding data access and usage, which are essential in defining acceptable behaviors and preventing legal violations. Violations of these policies can lead to significant legal consequences, including criminal prosecution, civil lawsuits, and regulatory penalties.
Common legal considerations in managing internal risks include:
- Privacy laws: Ensuring compliance with data protection regulations, such as GDPR or CCPA, to safeguard personal and sensitive information.
- Intellectual property protection: Legal measures to prevent the theft or unauthorized sharing of proprietary information.
- Employment laws: Balancing security practices with employees’ rights, ensuring that monitoring and investigations do not infringe on privacy or labor regulations.
- Contractual obligations: Enforcing non-disclosure agreements (NDAs) and other contractual terms that protect sensitive company information from being disclosed or misused.
Organizations must take a proactive approach to ensure they understand the legal risks and implement policies that protect both their assets and their workforce. Legal counsel should be consulted regularly to ensure that security measures align with evolving laws and regulations.
Preventive Measures Against Internal Risks
Implementing proactive measures to prevent internal security risks is crucial for maintaining a safe organizational environment. By addressing potential vulnerabilities before they manifest, organizations can significantly reduce the likelihood of security breaches and minimize the impact of any incidents that do occur. These preventive strategies focus on both technical controls and organizational policies designed to limit access, monitor activities, and educate employees on security best practices.
Access Control and Monitoring
One of the most effective ways to prevent unauthorized actions within an organization is through strict access control and continuous monitoring. These measures help to ensure that only authorized individuals can access sensitive data or systems, while also allowing security teams to detect suspicious activity early on. Key strategies include:
- Role-based access control (RBAC): Assigning access rights based on employees’ job roles to limit unnecessary exposure to sensitive information.
- Least privilege principle: Granting users only the minimum level of access necessary to perform their duties.
- Real-time monitoring: Continuously monitoring network activity and system access to quickly detect any unusual behavior or unauthorized actions.
- Audit logs: Keeping detailed logs of system activities, which can be reviewed to identify potential issues or track any suspicious behavior.
Employee Education and Awareness

Another critical preventive measure is ensuring that employees understand the importance of security and are trained to recognize potential risks. Educating staff about company policies, data protection practices, and how to report suspicious activities can greatly reduce the chances of an internal incident occurring. Important steps in this area include:
- Regular training programs: Offering ongoing training sessions to ensure that employees are aware of current security threats and best practices.
- Clear policies and procedures: Establishing and communicating clear guidelines regarding data access, usage, and handling.
- Phishing awareness: Educating employees on how to recognize phishing attempts and other social engineering tactics used by malicious actors.
By combining strong access controls with comprehensive employee training, organizations can create a layered defense strategy that minimizes the risk of internal security breaches and helps maintain a secure work environment.
Steps for Investigating Internal Security Incidents
When a security breach or suspicious activity is suspected within an organization, it is crucial to follow a clear and methodical process to investigate the incident. A structured approach helps to identify the root cause, assess the damage, and take appropriate corrective actions. These investigations require thoroughness, attention to detail, and the ability to handle sensitive information with care.
Here are the key steps involved in investigating internal security incidents:
- Initial Detection: The first step is identifying the incident. This could be triggered by alerts from monitoring systems, unusual employee behavior, or reports from other team members. Timely detection is critical to preventing further damage.
- Containment: Once an incident is detected, immediate containment measures should be taken to limit its spread. This might involve isolating affected systems, disabling compromised accounts, or cutting off network access to prevent further damage.
- Evidence Collection: During the investigation, it is important to gather relevant data and preserve evidence for analysis. This can include log files, emails, access records, and any other documentation related to the incident. Proper handling and storage of this evidence are essential for maintaining its integrity.
- Analysis: Analyze the collected evidence to determine the scope and impact of the incident. This includes identifying how the breach occurred, what data or systems were affected, and whether it was a targeted attack or a result of negligence.
- Interviews and Witness Statements: Interviews with involved parties, such as employees or external vendors, can provide valuable insights into the incident. Gathering statements from individuals who may have witnessed unusual activity can help fill in gaps and piece together the timeline.
- Root Cause Analysis: Understanding the root cause of the incident is vital for preventing future occurrences. This might involve reviewing existing security protocols, identifying vulnerabilities, and determining whether the issue was due to human error, system failure, or malicious intent.
- Reporting and Documentation: Once the investigation is complete, a detailed report should be prepared, documenting the findings, actions taken, and any recommendations for improvements. This report is crucial for internal records and may be required for compliance purposes.
- Corrective Actions: Based on the findings, corrective actions must be implemented to address vulnerabilities and strengthen security measures. This can involve updating policies, training staff, enhancing monitoring systems, or applying patches to affected systems.
Following these steps ensures that incidents are handled professionally and efficiently, minimizing damage and improving overall security posture within the organization.
Tools Used for Analyzing Internal Security Risks

In the modern landscape of cybersecurity, various tools are available to help organizations identify and analyze potential risks originating within their workforce. These tools enable security teams to monitor activities, detect suspicious behavior, and investigate incidents efficiently. By leveraging the right technologies, organizations can gain valuable insights into their internal security environment and address any vulnerabilities before they become significant issues.
Types of Tools for Risk Analysis
Several categories of tools are employed to analyze internal risks, each serving a specific function within an organization’s overall security strategy. These tools are designed to track user activities, monitor system access, and provide alerts in real-time when anomalies are detected.
| Tool Category | Function | Examples |
|---|---|---|
| Behavioral Analytics | Detect unusual user behavior and flag potential risks | Varonis, Sumo Logic |
| Endpoint Monitoring | Track activity on endpoints such as workstations and mobile devices | Symantec, CrowdStrike |
| Data Loss Prevention (DLP) | Prevent unauthorized access or sharing of sensitive data | Digital Guardian, McAfee DLP |
| Log Management | Collect and analyze logs from various systems and devices | Splunk, LogRhythm |
| Identity and Access Management (IAM) | Manage and monitor access rights and credentials | Okta, Microsoft Azure AD |
Choosing the Right Tool
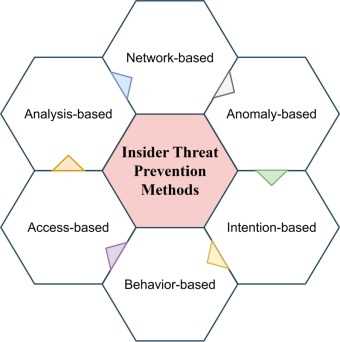
When selecting a tool for analyzing internal security risks, organizations should consider factors such as scalability, integration with existing systems, and the tool’s ability to provide real-time alerts. Additionally, the effectiveness of these tools relies on their configuration and continuous monitoring, ensuring that potential risks are detected early and addressed promptly. By using a combination of these tools, organizations can develop a comprehensive security posture that safeguards against potential internal incidents.
Real-Life Examples of Internal Security Incidents
Understanding the impact of security breaches originating from within an organization can be better achieved by examining real-world cases. These incidents highlight how vulnerable organizations can be to actions taken by their own employees or trusted individuals. By reviewing these examples, businesses can learn valuable lessons on how to prevent similar occurrences in the future and better safeguard their sensitive information.
Here are a few notable examples of internal security breaches:
- Case 1: Data Theft by an Employee
In one instance, a former employee at a technology company was found to have stolen sensitive data before leaving the organization. The individual had accessed proprietary information over a period of several months, which they then attempted to sell to competitors. The breach was only detected after the data began to surface on external forums. - Case 2: Unauthorized Access to Client Data
A healthcare worker used their position to gain unauthorized access to patient records. Despite having legitimate access to certain information for professional reasons, the employee went beyond their authorized scope and accessed private data, later using it for personal financial gain. - Case 3: Sabotage of Systems
In another case, a disgruntled employee with administrative privileges intentionally caused system outages and disrupted operations. They were able to tamper with system configurations, deleting critical files and causing financial loss for the company before the incident was fully detected and resolved. - Case 4: Social Engineering Exploited by an Insider
An employee at a financial firm unknowingly helped an outsider gain access to the company’s network by responding to a social engineering attack. The individual was tricked into providing login credentials, which were then used to infiltrate the network, leading to the theft of funds.
These real-life incidents illustrate how vulnerabilities can emerge within organizations, even when employees have the best intentions. It emphasizes the importance of monitoring internal access, conducting regular audits, and creating a strong security culture to mitigate the risk of such breaches.
Effective Communication During Security Incident Management
When dealing with a security event, clear and efficient communication is crucial to minimizing damage and ensuring a swift resolution. The coordination between team members, stakeholders, and external partners can significantly influence the outcome of the situation. By fostering an environment of transparency and responsiveness, organizations can act quickly and effectively in mitigating risks and protecting critical assets.
Key strategies for ensuring effective communication during security incidents include:
- Establish Clear Channels
It’s important to have pre-established communication channels for incident response. These channels should be secure, reliable, and accessible to key personnel at all times. Having a designated incident communication platform helps avoid confusion and delays. - Timely Updates
Regular updates during a security incident keep everyone informed about the situation’s status. Delays in sharing information can lead to misunderstandings or poor decision-making. Providing timely updates, even if the news is not ideal, ensures that all parties involved are prepared for the next steps. - Clarity and Precision
During a crisis, it is essential to communicate in a clear and precise manner. Vague or overly complex messages can confuse responders and slow down the resolution process. Ensure that all information shared is straightforward and actionable. - Cross-Department Collaboration
Security incidents often require the collaboration of various departments, including IT, legal, compliance, and public relations. Cross-functional teams should be equipped with the necessary information to make informed decisions and act in coordination. Regularly scheduled meetings can help keep all parties aligned. - Post-Incident Communication
Once the incident is resolved, communication doesn’t stop. Organizations should conduct debriefs to evaluate the effectiveness of their response. Sharing lessons learned and identifying areas for improvement can help strengthen future security preparedness.
By prioritizing effective communication during security events, organizations can ensure that they respond in a coordinated, timely, and efficient manner, reducing the potential for lasting damage and reinforcing their security posture.
Roles of Employees in Security Risk Prevention

Employees play a critical role in the overall security framework of an organization. While IT and security teams are responsible for implementing technical measures, it is the collective responsibility of all staff members to contribute to creating a secure work environment. Their awareness, behavior, and adherence to security protocols can make a significant difference in preventing potential security incidents.
Key responsibilities of employees in preventing security risks include:
- Following Established Security Protocols
Employees must understand and comply with the organization’s security policies. This includes using strong passwords, securely handling sensitive data, and following proper procedures for accessing systems and networks. Adherence to these practices reduces the risk of accidental breaches. - Recognizing and Reporting Suspicious Activity
Employees are often the first to notice unusual or suspicious activity. Encouraging a culture where staff members feel comfortable reporting concerns, such as irregular access attempts or unexpected system behavior, helps identify potential risks before they escalate. - Participating in Security Training
Regular training sessions ensure that employees are equipped with the knowledge and skills necessary to recognize and avoid security risks. Continuous education helps reinforce security best practices, keeping staff informed about evolving threats and the latest preventive measures. - Promoting a Culture of Security Awareness
Each employee can contribute to fostering a security-conscious environment. By staying vigilant and encouraging others to follow security practices, employees help establish security as a shared priority. Open discussions about security concerns and potential vulnerabilities can improve the organization’s overall security posture. - Minimizing Human Error
Many security incidents occur due to human error, such as clicking on phishing emails or failing to update software. Employees should be mindful of their actions, avoid risky behaviors, and use caution when handling sensitive information, especially in digital communications.
By understanding their individual role in security risk prevention, employees can contribute to safeguarding the organization’s assets and information. Their vigilance and adherence to best practices are essential in creating a proactive defense against potential risks.
Ethical Considerations in Risk Management
When addressing potential security incidents within an organization, ethical concerns play a crucial role in balancing the need for effective protection with respect for individual rights. Handling these situations requires a careful approach to ensure that actions taken align with both legal requirements and moral obligations. Organizations must consider fairness, transparency, and privacy while mitigating risks that may arise from malicious or negligent actions.
Respecting Privacy and Employee Rights
One of the primary ethical challenges in security management is protecting the privacy of employees while identifying and addressing risks. It is important for organizations to ensure that their monitoring and investigative activities do not infringe upon personal freedoms. Surveillance should be justified, transparent, and carried out in accordance with relevant privacy laws and company policies. Striking a balance between safeguarding company interests and respecting employee rights is essential for maintaining trust within the workforce.
Ensuring Fairness and Transparency in Investigations
Another critical aspect is the fairness and transparency of investigations. When potential misconduct is suspected, it is essential that employees are treated equitably throughout the process. Clear communication of the company’s policies and the steps involved in the investigation helps prevent misunderstandings and promotes a culture of fairness. Organizations should ensure that decisions are based on verified facts and not on assumptions or biases, ensuring that employees have the opportunity to explain their actions and circumstances before any conclusions are drawn.
By addressing these ethical concerns, organizations can manage security risks while fostering a responsible and fair work environment. Striving for an ethical approach in these situations helps protect both the organization’s assets and its employees, ultimately promoting a culture of mutual respect and trust.
Training Strategies for Risk Awareness

Effective training programs are essential in equipping employees with the knowledge and skills necessary to recognize and respond to potential security risks within an organization. These programs should focus on building a comprehensive understanding of security policies, as well as fostering a proactive culture that encourages vigilance and responsibility. By focusing on both awareness and practical steps, organizations can create a more secure environment while empowering their staff to play an active role in risk prevention.
Core Elements of an Effective Training Program
Training programs should cover a range of topics to ensure a holistic understanding of risk management. The key elements include:
| Topic | Objective |
|---|---|
| Security Policies and Procedures | Ensure employees understand organizational guidelines for protecting sensitive information. |
| Recognizing Suspicious Behavior | Teach employees to identify red flags and unusual activities in the workplace. |
| Reporting Protocols | Empower staff to report suspicious activities in a timely and safe manner. |
| Data Protection Best Practices | Equip employees with the knowledge to handle confidential information securely. |
| Incident Response Procedures | Prepare employees to react appropriately in the event of a security breach. |
Interactive and Engaging Training Methods
In addition to traditional training methods such as workshops and seminars, interactive approaches are vital for increasing engagement and retention. These methods include:
- Simulated Scenarios: Allowing employees to experience real-world security challenges in a controlled environment.
- Gamification: Using game-based elements to make training more engaging and rewarding.
- Role-playing: Enabling staff to practice responses to potential security risks in various situations.
By incorporating a variety of learning techniques, organizations can ensure that employees are not only aware of the risks but also prepared to take appropriate action to protect the organization’s assets.
Challenges in Risk Detection
Identifying potential risks within an organization can be a complex and nuanced process. Various factors contribute to the difficulty of detection, including human behavior, technological limitations, and the evolving nature of internal security risks. Effective detection systems require a balance between thorough monitoring and the ability to filter out false positives, which can be time-consuming and resource-intensive. This section explores some of the key challenges organizations face when attempting to identify risks early and accurately.
Key Obstacles in Risk Detection
Several factors complicate the process of identifying potential security issues, including:
| Challenge | Description |
|---|---|
| Behavioral Complexity | Human behavior is difficult to predict, making it hard to differentiate between normal activities and suspicious actions. |
| Data Overload | Organizations often generate vast amounts of data, making it challenging to analyze and identify relevant patterns without advanced tools. |
| Resource Constraints | Limited budgets and staffing can hinder the ability to deploy and maintain sophisticated detection systems. |
| False Positives | Excessive alerts can overwhelm security teams, leading to desensitization or errors in response. |
| Insider Knowledge | Employees with access to sensitive data may exploit their knowledge to bypass security measures, making detection even more difficult. |
Technological and Human Factors

Both technological and human factors play a critical role in the challenges faced during risk detection:
- Technological Limitations: Tools and software used for monitoring and detection may not always be sophisticated enough to catch subtle anomalies or patterns indicative of potential risks.
- Human Error: Even with the best tools in place, human oversight, such as failing to recognize patterns or misinterpreting data, can lead to missed risks.
- Motivation and Intent: Detecting malicious intent is often difficult because the individual may not show overt signs of misconduct, especially if they are well-versed in the organization’s systems and policies.
These challenges emphasize the need for a multi-faceted approach to risk detection, incorporating both technology and human expertise to minimize the impact of potential security breaches.
Preparing for the Security Awareness Assessment
Successfully preparing for a security awareness evaluation requires a strategic approach to understanding core principles, identifying potential risks, and applying effective mitigation techniques. Individuals looking to excel in these assessments must focus on both theoretical knowledge and practical skills. Familiarity with the latest security trends, recognizing warning signs of internal vulnerabilities, and understanding the key frameworks for addressing security risks are essential components of thorough preparation.
Begin by reviewing the foundational concepts in security management, as this knowledge forms the basis for identifying possible risks in an organization. It is also critical to stay up-to-date with the latest developments in cybersecurity, particularly those that deal with internal organizational challenges and security breaches. Practicing the identification of suspicious behaviors and the appropriate responses is another important area for preparation.
In addition to studying the theoretical material, individuals should practice using real-world case studies and scenarios. These practical exercises provide insights into how security measures are applied in diverse situations and help develop a hands-on understanding of the techniques needed to address emerging risks.