
In today’s rapidly evolving digital landscape, understanding advanced security systems is crucial for protecting networks and data from emerging threats. With the increasing complexity of cyberattacks, organizations are investing heavily in sophisticated tools to detect and prevent malicious activities. For professionals in the field, achieving proficiency in these technologies is essential, and certifications are one of the best ways to demonstrate this expertise.
Preparing for a certification in cybersecurity requires a deep understanding of core principles, as well as practical knowledge of the systems used to monitor and safeguard networks. This guide is designed to help candidates navigate the process by providing insights into common topics and strategies for success. By focusing on key areas of focus and mastering critical concepts, individuals can significantly improve their chances of passing and gaining valuable credentials in the industry.
Emphasizing hands-on experience and theoretical understanding, this guide will equip you with the tools and knowledge needed to excel. Whether you’re aiming to improve your skill set or take the next step in your career, the path to success lies in preparation, practice, and a solid grasp of security fundamentals.
Qualys Endpoint Detection Overview
In the world of cybersecurity, protecting systems from evolving threats requires sophisticated tools that monitor and secure network infrastructures. These tools focus on identifying suspicious activities and quickly responding to potential breaches, ensuring that businesses can operate without the risk of data compromise. The main goal of such technologies is to provide real-time visibility and prevent, detect, and respond to various types of attacks.
The effectiveness of these solutions lies in their ability to continuously monitor network traffic, applications, and endpoints, allowing for the identification of abnormal behaviors that could indicate a security threat. By using advanced algorithms, these systems can analyze vast amounts of data to recognize patterns and respond swiftly to mitigate potential damage. With the increase in remote work and cloud environments, the need for robust protective measures has never been greater.
The following table outlines the primary components of a modern monitoring solution and how they contribute to an overall security strategy:
| Component | Description | Function |
|---|---|---|
| Monitoring Tools | Software that tracks system activities and network traffic. | Provide continuous surveillance and alerts for unusual behavior. |
| Threat Intelligence | Data on known vulnerabilities and attack techniques. | Helps identify emerging threats and strengthens detection capabilities. |
| Automated Response | Systems that can take predefined actions when an issue is detected. | Reduces reaction time by automating remediation steps. |
| Data Analytics | Tools that analyze logs and network traffic data. | Enhance detection accuracy by identifying unusual patterns. |
These tools work together to create a comprehensive security strategy, providing visibility into network activity and enabling swift action against potential threats. Understanding how each component contributes to the overall solution is essential for effective implementation and operation in a business environment.
Understanding the Basics of EDR
In the realm of cybersecurity, safeguarding an organization’s systems requires continuous monitoring and proactive measures. One of the foundational approaches to achieving this is through the use of specialized software that helps identify, mitigate, and prevent cyber threats in real time. These systems are designed to provide comprehensive oversight, ensuring that any signs of malicious activity are detected early and addressed before they can cause harm.
The core functionality of these technologies revolves around tracking and analyzing network behavior, system activities, and potential vulnerabilities. By maintaining an ongoing watch over devices and infrastructure, they can immediately flag irregular patterns or actions that may indicate security breaches. These tools help organizations respond promptly, reducing the impact of cyberattacks and maintaining business continuity.
Here are the main components that form the foundation of these solutions:
- Monitoring: Continuous tracking of system activity to detect irregularities and potential threats.
- Alerting: Automated notifications that inform security teams of suspicious actions in real time.
- Investigation: Tools to allow for deep analysis into potential threats, helping teams understand the cause and impact of an incident.
- Remediation: Actions taken to contain or eliminate threats before they can cause significant damage.
These systems are not just passive, but actively engage with ongoing activities, creating an environment where threats are quickly identified and neutralized. The ability to detect and respond to attacks before they spread is what makes these solutions so effective in today’s cybersecurity landscape.
Key Concepts in Cybersecurity Defense
Cybersecurity defense is built on a set of principles and strategies aimed at protecting systems from harmful intrusions and ensuring the integrity of digital assets. As the landscape of cyber threats continues to evolve, understanding these core concepts is essential for maintaining strong protection against attacks. These concepts serve as the foundation for creating robust defenses and quick responses to potential risks in any organization.
Core Areas of Cybersecurity
There are several key areas that contribute to a comprehensive defense strategy. These areas work together to provide multi-layered protection, addressing vulnerabilities before they can be exploited. Below are some of the most critical concepts:
| Concept | Description | Importance |
|---|---|---|
| Threat Prevention | Measures to block potential attacks before they can occur. | Reduces risk by stopping attacks at the entry point. |
| Vulnerability Management | Identifying and fixing weaknesses in systems. | Minimizes the chances of attackers exploiting security gaps. |
| Incident Detection | Monitoring systems for signs of malicious activity. | Enables early detection to prevent further damage. |
| Response Strategy | Actions taken to limit damage and recover from attacks. | Helps organizations quickly recover and return to normal operations. |
Importance of a Proactive Approach
Cybersecurity is not just about responding to threats once they occur but about building systems that prevent issues before they escalate. A proactive approach focuses on anticipating potential vulnerabilities, implementing preventive controls, and continuously monitoring for unusual activity. By integrating prevention, detection, and recovery strategies into a cohesive plan, organizations can enhance their resilience against the ever-changing landscape of cyber threats.
How EDR Solutions Improve Protection
In the evolving landscape of cybersecurity, protecting digital infrastructures requires more than just basic security measures. Advanced systems are needed to continuously monitor network activities, identify threats, and quickly neutralize potential risks. By incorporating sophisticated tools, businesses can enhance their overall protection and respond faster to emerging vulnerabilities.
These solutions help improve security in several ways, providing a multi-layered defense strategy that combines proactive monitoring with rapid incident response. They focus on minimizing the window of exposure by detecting malicious actions early and automatically initiating protective measures. With real-time insights into system behavior, security teams can act quickly to block harmful activities and prevent widespread damage.
Additionally, by integrating automation and machine learning, these systems continuously adapt to new attack techniques, making them more effective over time. This adaptability ensures that as new threats emerge, the protective measures in place evolve to address these challenges promptly, keeping organizations ahead of potential risks.
Exam Format and Structure
Understanding the layout and organization of any certification test is crucial for effective preparation. A well-structured assessment helps candidates focus on key topics, ensuring that their knowledge and skills are thoroughly evaluated. The format of such a test typically combines various types of questions to assess both theoretical understanding and practical application of security concepts.
The structure of this assessment is designed to challenge individuals on a wide range of subjects related to security technologies. It includes multiple-choice questions, scenario-based questions, and practical exercises that test the ability to apply knowledge in real-world situations. The questions may cover a variety of topics, from threat identification to response actions, providing a comprehensive review of the subject matter.
To succeed in this type of test, it’s important to be familiar with the various types of questions you may encounter. Preparation involves both understanding theoretical principles and being able to make quick, informed decisions based on the scenarios presented.
What to Expect on the Test
When preparing for a certification in cybersecurity, it’s important to understand the nature of the assessment you’ll be facing. The test is designed to evaluate your ability to apply security knowledge and practices in a range of real-world situations. This includes both theoretical knowledge and practical problem-solving skills that are critical for anyone working in the field of information security.
Types of Questions
The test includes a variety of question types, each designed to assess different aspects of your knowledge. You can expect a mix of:
- Multiple-Choice Questions: These questions will test your theoretical understanding of cybersecurity concepts, such as threat identification and security frameworks.
- Scenario-Based Questions: These will present real-world situations where you need to demonstrate your ability to analyze a problem and propose an effective solution.
- Practical Exercises: Some questions may require you to perform specific tasks, such as configuring a security tool or interpreting system logs, to show your hands-on skills.
Time Management and Strategy
During the test, you’ll need to manage your time effectively to ensure you can address all sections within the allotted period. It’s advisable to first answer the questions you’re most confident about, leaving more complex or time-consuming ones for later. This approach helps maximize your score by ensuring that you complete the easier sections quickly and have ample time for the more challenging parts of the test.
EDR Tools and Features
Modern cybersecurity solutions rely on a range of specialized tools that are designed to protect systems and networks from malicious activities. These tools combine various capabilities that enable organizations to detect, block, and respond to potential threats in real time. By offering advanced monitoring, threat analysis, and automated actions, these solutions provide comprehensive protection against ever-evolving cyber risks.
Here are some key tools and features that are commonly found in such systems:
- Real-Time Monitoring: Continuous tracking of network activity and system behavior to identify suspicious actions immediately.
- Threat Intelligence Integration: Leveraging external data sources to identify known attack patterns and emerging risks.
- Automated Incident Response: Tools that automatically take corrective actions, such as isolating compromised systems or blocking harmful traffic, to reduce response time.
- Data Analytics: Advanced analytics that provide deeper insights into security events, helping teams understand the scope and impact of threats.
- Advanced Search and Query Tools: Allowing security teams to search through vast amounts of data and logs to quickly identify the root cause of incidents.
- Endpoint Protection: Ensuring that every device connected to the network is secured and continuously monitored for vulnerabilities and signs of compromise.
These tools work together to enhance an organization’s ability to prevent, detect, and respond to cyber threats efficiently. By automating much of the process and providing detailed insights into system behavior, they reduce the workload on security teams while improving overall protection.
Overview of Available Detection Tools

To maintain robust security in today’s digital environments, various tools are available to monitor, identify, and counteract cyber threats. These tools help organizations spot suspicious activities, track potential vulnerabilities, and ultimately protect sensitive data from being compromised. By leveraging advanced technologies, businesses can strengthen their defenses and ensure rapid responses to emerging risks.
These systems are equipped with a range of capabilities, each designed to address different aspects of cybersecurity. Whether it’s detecting network anomalies, scanning files for malicious code, or analyzing user behavior, these tools provide a layered approach to threat identification.
- Network Traffic Analysis: Monitors all incoming and outgoing data to detect irregularities that could signify an attack or data breach.
- Signature-Based Scanners: Identifies known threats by comparing files or behaviors to predefined threat signatures stored in databases.
- Behavioral Monitoring: Tracks user and system behaviors to identify abnormal patterns that could indicate a potential threat.
- File Integrity Checkers: Compares files to baseline values to identify unauthorized changes or modifications.
- Heuristic Analysis: Uses algorithms to analyze files and behaviors for suspicious patterns or activities that may not yet be known threats.
- Cloud-Based Threat Detection: Leverages cloud computing to analyze data and threats at scale, providing real-time threat intelligence.
Each tool offers unique advantages, and when used together, they create a more resilient defense system capable of addressing a wide variety of security challenges. The key to success lies in selecting the right combination of detection methods for your organization’s needs and integrating them into a comprehensive cybersecurity strategy.
Preparing for the Certification Test
Successfully passing a certification in the field of cybersecurity requires thorough preparation and a clear understanding of the topics being tested. To increase your chances of success, it is crucial to approach the study process strategically. The test is designed to assess both theoretical knowledge and practical application of security practices, so it’s important to cover a wide range of areas related to system protection, threat management, and incident response.
Here are a few steps to help you effectively prepare for the test:
- Understand the Exam Scope: Familiarize yourself with the topics that will be covered. This typically includes system defense techniques, network monitoring, threat detection methods, and response strategies.
- Review Official Study Materials: Official resources, guides, and practice questions provide insights into the specific content that will be tested, helping you focus on the most important areas.
- Hands-On Practice: Practical experience is essential. Set up labs or use virtual environments to practice tasks such as configuring security tools, responding to incidents, and interpreting logs.
- Take Practice Tests: Simulate the test environment by taking timed practice exams. This will help you become familiar with the question format and improve time management skills.
- Join Online Communities: Engage with others who are also preparing for the test. Online forums, study groups, and discussion boards can provide valuable insights and tips.
- Stay Updated: Cybersecurity is a fast-evolving field, so it’s important to stay current with the latest trends, threats, and technologies that may be included in the test.
By following these steps, you will not only build your knowledge base but also improve your confidence in applying this knowledge under exam conditions. Being well-prepared will give you the best chance of success and help you achieve your certification goals.
Effective Study Strategies for Success
Achieving success in a certification test requires more than just hard work–it demands a structured and strategic approach to studying. Effective study habits can make a significant difference in both your understanding of the material and your performance on the test. By developing a plan, setting clear goals, and using the right resources, you can maximize your chances of success.
Here are some proven strategies to help you prepare effectively:
- Set a Clear Study Schedule: Organize your time by creating a realistic study schedule. Break down the material into manageable sections and allocate specific times to review each topic.
- Focus on Key Concepts: Prioritize the most important and complex concepts that will be tested. Focus on understanding the “why” behind the material, rather than just memorizing facts.
- Use Active Learning Techniques: Engage with the material actively through techniques like summarizing information in your own words, teaching others, or solving practice problems.
- Utilize a Variety of Resources: Don’t rely on a single study guide. Use a combination of books, online courses, practice exams, and videos to gain different perspectives on the material.
- Practice Under Test Conditions: Simulate exam conditions by taking timed practice tests. This will help you build confidence and improve your time management skills.
- Review Mistakes and Learn: After taking practice tests or quizzes, thoroughly review the answers you got wrong. Understand why you made those mistakes and take note of the correct solutions to avoid repeating them.
- Stay Consistent: Consistency is key. Study regularly rather than cramming all at once, as spaced repetition improves long-term retention.
By incorporating these strategies into your study routine, you’ll be better prepared and more confident when it’s time to take the test. The right approach can help you stay on track, manage your stress, and achieve your certification goals.
Common Challenges in EDR Exams
When preparing for a certification focused on cybersecurity tools and strategies, candidates often encounter various obstacles that can hinder their progress. These challenges can arise from both the complexity of the subject matter and the format of the test itself. Identifying these difficulties in advance allows for better preparation and more effective study strategies.
Some of the most common challenges include:
- Understanding Complex Concepts: Many topics in cybersecurity are highly technical and require a deep understanding of how systems work. Without a solid grasp of the foundational principles, it can be difficult to apply them to real-world scenarios.
- Time Management: The pressure of completing the test within a limited time frame can be overwhelming. Some candidates struggle to balance speed with accuracy, especially when faced with tricky questions or unfamiliar topics.
- Practice and Hands-On Experience: A major challenge is gaining sufficient hands-on experience. While theoretical knowledge is important, practical application through labs or simulations is essential for mastering the material and understanding its real-world use.
- Test Anxiety: The stress of taking a test, especially one that impacts professional advancement, can affect performance. Test anxiety may lead to difficulty focusing or making decisions under pressure.
- Keeping Up with New Technologies: The field of cybersecurity evolves rapidly, and staying current with the la
How to Overcome Test Difficulties
Facing challenges during a certification assessment can be frustrating, but with the right strategies, these obstacles can be overcome effectively. Whether it’s managing time, understanding complex concepts, or staying calm under pressure, there are ways to turn potential difficulties into opportunities for improvement. The key is to approach preparation with a clear, focused mindset and to develop skills that will help you tackle even the most challenging questions.
Here are some strategies to help you overcome test-related difficulties:
- Break Down Complex Topics: If you encounter difficult concepts, try breaking them down into smaller, more manageable sections. Approach each part individually, and don’t hesitate to revisit challenging material until it clicks.
- Practice with Timed Mock Tests: Simulate real test conditions by taking timed practice tests. This will help you develop a sense of timing and reduce anxiety when you’re in the actual testing environment.
- Focus on Key Areas: Identify the areas where you feel least confident and focus your study efforts on them. Strengthening weak spots will give you more confidence and help reduce overall stress.
- Stay Calm and Confident: Test anxiety can affect performance, so it’s important to stay calm. Practice relaxation techniques such as deep breathing or visualization to help maintain focus and clarity during the assessment.
- Review Mistakes Thoroughly: After completing practice tests, review the mistakes you made. Understanding why you got a question wrong and learning from it will help you avoid repeating the same errors.
- Use Resources Effectively: Don’t hesitate to use all available resources, such as study guides, online forums, or instructors. Getting different perspectives can deepen your understanding and clarify any confusion.
- Time Management: During the test, prioritize questions you feel most confident about first, then return to more difficult ones. Allocate enough time for each section to avoid rushing through critical parts.
By incorporating these strategies into your preparation, you can improve your performance and approach the assessment with greater confidence. Focused practice, steady learning, and maintaining a calm mindset are crucial for overcoming test difficulties and achieving success.
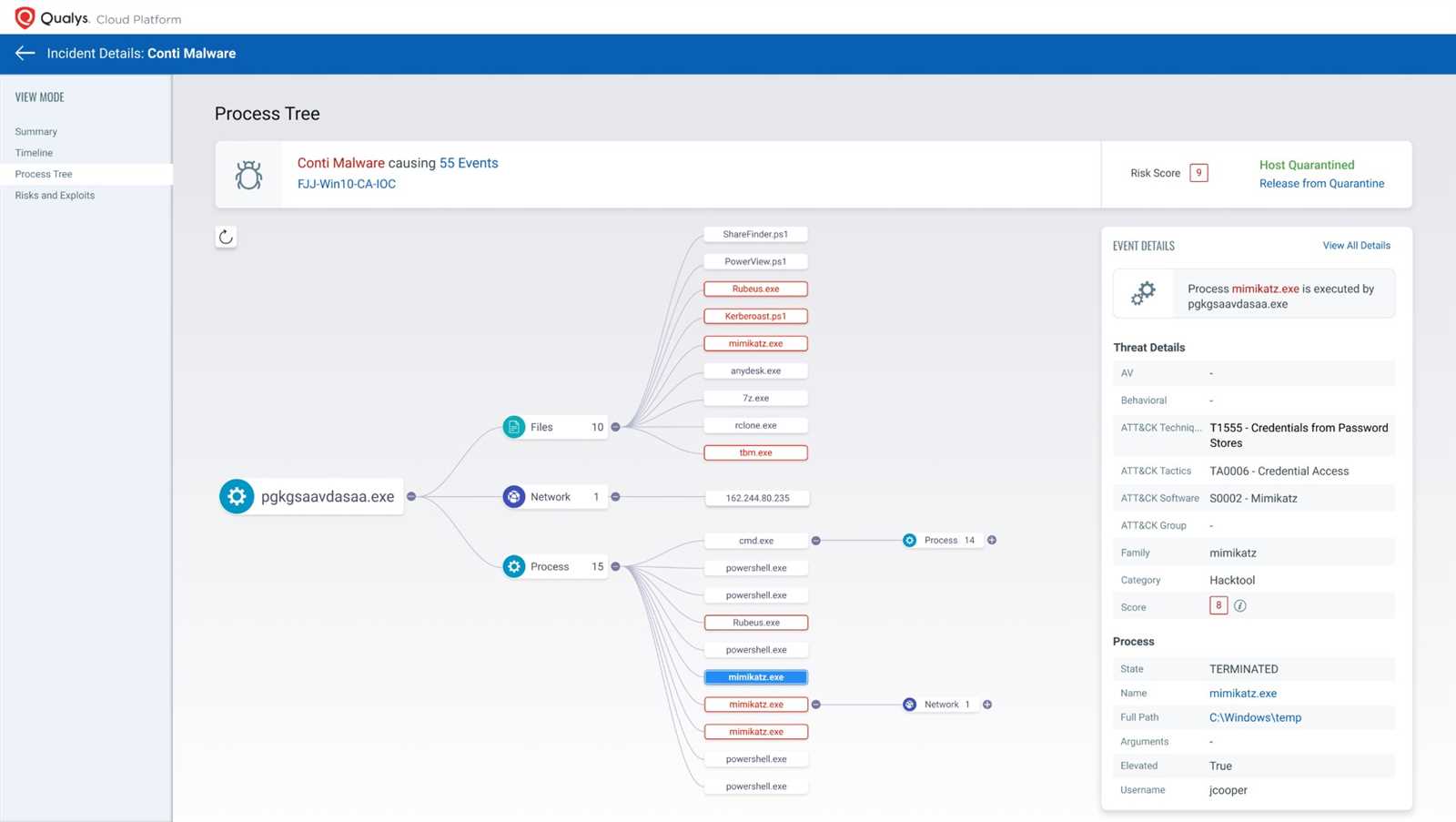
How to Interpret EDR Data
Understanding the data generated by security monitoring systems is essential for identifying threats and securing a network. The ability to accurately interpret this information helps professionals make informed decisions and respond to incidents in a timely manner. Whether it’s network traffic logs, event data, or system alerts, every piece of information can provide valuable insight into potential risks. Learning to analyze and prioritize this data is key to enhancing security measures.
Key Data Types to Analyze
There are several types of data that need to be interpreted for effective security management:
- System Logs: These records provide detailed information about actions taken on devices and applications. Anomalies in these logs, such as unexpected user actions or failed login attempts, may indicate suspicious activity.
- Network Traffic: Monitoring network traffic helps to identify unusual patterns, such as spikes in data transfer or connections to unrecognized IP addresses, which could suggest a security breach.
- Alerts and Notifications: Alerts generated by security tools often contain actionable information that requires immediate attention. Interpreting these alerts correctly is crucial for timely responses.
How to Analyze and Prioritize Data
Once you’ve collected and organized security data, the next step is analysis. Here are some techniques for interpreting data effectively:
- Identify Patterns: Look for recurring patterns in the data. These patterns could reveal trends that suggest malicious behavior or system vulnerabilities.
- Cross-Reference Information: Compare data from multiple sources, such as logs, traffic reports, and alerts, to form a more complete picture of potential risks.
- Prioritize Critical Events: Not all data is equally important. Focus on high-priority incidents that pose immediate threats to system integrity or user data.
- Contextualize the Data: Understand the context in which the data was generated. For example, a high volume of outgoing traffic might be normal for a server during an update but could be suspicious during other periods.
By effectively interpreting security data, you can stay ahead of potential threats, improve incident response, and ensure better protection for your organization’s assets. The ability to make sense of this information is a vital skill for anyone working in cybersecurity.
Analyzing Security Threat Indicators
Identifying and analyzing potential security threats is a critical task in protecting an organization’s infrastructure. Threat indicators are signals or signs that suggest malicious activity is occurring or could occur. These indicators can come in many forms, including unusual network traffic, irregular system behavior, or suspicious user actions. By analyzing these indicators, professionals can detect threats early and take appropriate action before significant damage occurs.
Common Types of Threat Indicators
There are several key indicators that security analysts monitor to identify potential risks:
- Unusual Network Traffic: Anomalies in data flow, such as unexplained spikes in bandwidth usage or connections to unfamiliar external servers, can suggest an ongoing attack or data exfiltration attempt.
- Unexpected System Changes: Unauthorized changes to system configurations, file modifications, or the installation of unknown software can be signs of a breach or unauthorized access.
- Abnormal User Activity: Sudden changes in user behavior, like logging in at odd hours or accessing files they don’t typically interact with, can indicate account compromise or insider threats.
- Malicious File Indicators: The presence of known malicious files, suspicious executables, or altered software can suggest that malware has infiltrated the system.
How to Effectively Analyze Threat Indicators
Effectively analyzing threat indicators requires a structured approach to investigation. Here are key steps for conducting a thorough analysis:
- Correlate Data: Cross-reference data from multiple sources, such as logs, network traffic, and user activities, to identify patterns and confirm whether an indicator is part of a larger malicious event.
- Leverage Threat Intelligence: Use external and internal intelligence sources to validate whether observed indicators match known attack tactics, techniques, and procedures (TTPs) of threat actors.
- Investigate Context: Always assess the context around a suspicious indicator. For example, a new file appearing on a system might not be malicious if it’s part of a scheduled update, but further analysis is necessary to verify this.
- Prioritize Threats: Not all indicators represent immediate danger. Assess the severity and potential impact of each threat, and prioritize responses based on the criticality of the assets at risk.
By effectively analyzing threat indicators, security professionals can proactively defend against malicious activities, mitigate risks, and enhance the overall security posture of the organization. Early detection and response are key to minimizing the potential damage caused by security threats.
Advanced EDR Techniques and Approaches
In the ever-evolving landscape of cybersecurity, advanced methods and strategies are crucial for effectively identifying and mitigating sophisticated threats. Traditional security tools may not be sufficient to combat modern attacks, which are becoming increasingly stealthy and complex. Advanced approaches provide deeper insights and more robust defenses, helping organizations to detect malicious activity in its early stages and prevent breaches before they escalate.
Behavioral Analytics for Threat Detection
One of the most powerful techniques in modern security practices is behavioral analytics. This approach monitors user and system behavior to establish a baseline of “normal” activity. By continuously analyzing actions such as login patterns, file access, and network traffic, security solutions can spot anomalies that deviate from this baseline, indicating a potential threat. These anomalies can then trigger alerts for further investigation, enabling faster detection of emerging threats.
- Machine Learning Models: Automated learning algorithms enhance the ability to detect subtle deviations in behavior, improving detection accuracy over time.
- Contextual Analysis: By taking into account the context in which the behavior occurs, advanced systems can reduce false positives and focus attention on actual risks.
Threat Hunting and Proactive Defense
Threat hunting involves actively searching for signs of malicious activity rather than waiting for automated systems to detect it. Security teams use advanced tools to comb through system logs, network traffic, and endpoint data, looking for indicators of compromise that might have gone unnoticed. This proactive approach is essential for identifying sophisticated or targeted attacks that may not be detected by traditional security measures.
- Hypothesis-Driven Investigations: Analysts create hypotheses about potential threats and use specific queries to test them, narrowing down the search for hidden risks.
- Collaboration with Intelligence Sources: Threat hunters can leverage external threat intelligence to correlate internal data with known attack techniques, improving their ability to identify advanced persistent threats.
Advanced techniques such as behavioral analytics and threat hunting provide security teams with the tools needed to stay ahead of attackers. By embracing these approaches, organizations can build a more resilient defense posture, detecting sophisticated threats early and reducing the risk of significant damage.
Leveraging Automation for Detection
In today’s cybersecurity landscape, automation plays a pivotal role in enhancing the speed, accuracy, and efficiency of threat identification. Manual monitoring can be time-consuming and error-prone, making it challenging to respond swiftly to potential risks. By incorporating automated systems into security workflows, organizations can rapidly process vast amounts of data, enabling them to detect potential issues faster and with greater precision.
Automated tools can analyze logs, network traffic, and user behavior at scale, identifying patterns that may otherwise go unnoticed. By reducing the reliance on human intervention, these systems allow security teams to focus on higher-priority tasks, such as investigating confirmed threats and fortifying defenses.
Key Benefits of Automation in Cybersecurity
- Increased Speed: Automated systems can analyze data in real-time, providing near-instantaneous alerts for suspicious activity.
- Reduced Human Error: By eliminating manual processes, automation decreases the likelihood of overlooking critical threats or misinterpreting data.
- Scalability: Automation allows organizations to scale their security operations to handle large volumes of data without overwhelming resources.
Common Use Cases for Automated Detection
Automation is particularly effective in several key areas of cybersecurity:
Use Case Automation Benefits Intrusion Detection Automated systems can monitor network traffic in real-time and identify anomalies that indicate an attempted breach. Phishing Email Identification Automated filters can scan incoming emails for signs of phishing attempts, blocking malicious messages before they reach users. Vulnerability Scanning Automated scanners continuously search for vulnerabilities across systems and networks, ensuring timely patches and updates. By leveraging automation, organizations can strengthen their detection capabilities, significantly improving their ability to identify and address threats. The integration of these tools not only enhances the overall security posture but also streamlines workflows, allowing teams to stay ahead of evolving cyber threats.
Tips for Mastering EDR Questions
Achieving proficiency in cybersecurity-related assessments requires not only understanding the core concepts but also developing the ability to apply that knowledge effectively in various scenarios. Whether you’re preparing for a certification or aiming to enhance your practical skills, mastering key topics and refining your approach to solving problems can significantly improve your performance. In this section, we’ll explore some practical tips to help you tackle questions related to advanced security techniques and solutions with confidence.
1. Focus on Real-World Scenarios
One of the best ways to prepare is to immerse yourself in real-world use cases. Understanding how security mechanisms work in actual environments will help you answer questions that test your ability to analyze and respond to various situations. When reviewing materials, consider how the concepts apply to current threats and attack methods. This contextual knowledge will make it easier to interpret questions and select the most appropriate answers.
2. Strengthen Core Technical Skills

To excel in any technical assessment, a solid foundation is crucial. Make sure you have a clear understanding of the fundamental tools, strategies, and processes used in the field. Pay close attention to topics such as:
- Threat Detection Techniques: Understanding the various methods used to identify potential security risks, from behavioral analysis to signature-based detection.
- Incident Response Strategies: Knowing the proper procedures for investigating and mitigating security incidents, from initial detection to recovery.
- Security Frameworks: Familiarize yourself with industry standards and best practices that guide threat management and security measures.
Mastery of these core areas will not only help you in answering questions accurately but also give you the practical knowledge needed for success in real-world situations.
3. Practice with Mock Questions and Simulations

One of the most effective ways to prepare is through practice. Utilize mock tests, quizzes, and interactive simulations that mimic the types of questions you might encounter. Practicing under timed conditions will help you become familiar with the format and improve your ability to respond quickly and accurately. Additionally, reviewing the explanations behind each answer will help reinforce your understanding of key concepts and provide insight into how to approach different types of questions.
By following these tips, you can improve your preparation and increase your chances of success in tackling questions related to security systems and solutions. With a blend of technical knowledge, practical application, and focused practice, you will be well on your way to mastering these challenging topics.
Key Areas to Focus on for Accuracy
Achieving accuracy in technical assessments requires a focused approach, as the questions often demand a deep understanding of complex concepts and their practical applications. By honing in on specific areas and developing expertise in them, you can ensure that your responses are not only correct but well-reasoned. In this section, we will explore key topics that are essential to mastering the material and improving the precision of your answers.
1. Threat Intelligence and Analysis
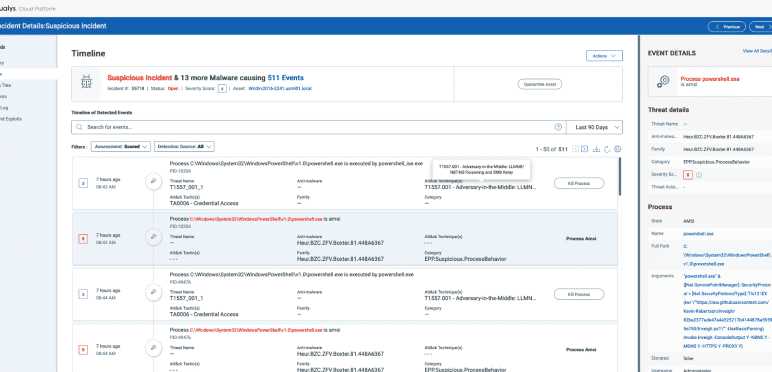
A key area for accurate decision-making involves understanding the landscape of cyber threats. This includes recognizing common attack patterns, identifying various threat actors, and being able to analyze how specific risks manifest in different environments. To achieve accuracy, it’s important to focus on:
- Malware behavior analysis: Understanding how different types of malware operate, propagate, and evade detection.
- Indicators of compromise (IoC): Familiarizing yourself with the common signs of an attack, such as unusual network traffic, unauthorized system access, or file alterations.
- Threat intelligence feeds: Using intelligence sources to stay up-to-date on emerging threats and tactics, and applying this information to mitigate potential risks.
By mastering these aspects, you will be able to accurately assess threat scenarios and respond with the appropriate security measures.
2. Incident Response Procedures
Another critical area for accuracy is understanding the procedures involved in responding to a security incident. This includes knowing how to contain, investigate, and resolve potential breaches while minimizing damage. Key areas to focus on include:
- Initial detection and assessment: Developing the ability to quickly identify signs of a breach and evaluate the scope of the incident.
- Containment strategies: Knowing how to isolate affected systems to prevent further compromise without disrupting normal operations.
- Recovery and post-incident analysis: Understanding how to restore affected systems and perform root cause analysis to prevent future incidents.
Focusing on these core procedures ensures that you can provide accurate responses when discussing incident management, as well as understand the steps required for effective resolution.
Mastering these areas will not only help you achieve greater accuracy in your assessments but will also prepare you to handle real-world security challenges with confidence and precision.