
Understanding how to properly assess network security is crucial for protecting systems from potential threats. The process of identifying weaknesses and ensuring their resolution is a key aspect of maintaining robust defenses. A clear and methodical approach allows for more reliable results and greater overall security effectiveness.
In order to optimize the process, it is essential to focus on various factors such as system configuration, scan depth, and the prioritization of vulnerabilities. Successful assessments involve thorough planning, proper execution, and careful analysis of the outcomes. A well-rounded approach enhances both efficiency and accuracy, ensuring that all areas are adequately reviewed.
By mastering effective techniques, individuals can achieve better security insights, streamline their workflows, and contribute to building stronger, more secure infrastructures. Whether for routine maintenance or specific evaluations, a thoughtful approach guarantees better protection against emerging risks.
Qualys Scanning Strategies and Best Practices Exam Answers
When it comes to assessing vulnerabilities within a network, following the right steps ensures comprehensive coverage of potential risks. This section explores the key concepts, methods, and tools involved in optimizing security evaluations. The main goal is to ensure a thorough understanding of how to conduct assessments that identify, prioritize, and address vulnerabilities effectively.
Key Concepts for Effective Evaluations
A structured approach to identifying security weaknesses involves more than just running simple tests. Thorough preparation, clear methodology, and understanding system configurations are essential. A precise evaluation requires the use of accurate settings, scan depth adjustments, and identifying specific areas for improvement.
Tools for Enhancing Vulnerability Assessments
Leveraging advanced tools enhances the overall process, allowing for efficient identification of issues. Automation, real-time analysis, and integration with other security systems play a major role in ensuring that scans are both effective and timely. Moreover, customizing scan profiles can help tailor the process to meet the needs of specific environments.
| Step | Description | Recommended Tools |
|---|---|---|
| Initial Setup | Configure network parameters and scan objectives | Configuration templates, system scanners |
| Scan Execution | Run vulnerability assessments based on defined goals | Automated tools, vulnerability databases |
| Analysis | Review results to identify high-risk issues | Reporting tools, risk assessment models |
| Prioritization | Rank findings based on severity and impact | Risk management systems, task management software |
Key Components of Vulnerability Assessments

To ensure the thorough identification of system weaknesses, it’s essential to understand the core elements involved in an effective evaluation process. These components range from the initial setup to the final analysis, with each step playing a critical role in detecting potential threats. A well-structured assessment relies on precise configurations, automated tools, and accurate interpretation of results to guarantee security.
System Configuration and Setup
Before starting an assessment, proper configuration is necessary to ensure that the tools are targeting the right areas of the network. This includes defining the scope of the evaluation, determining which devices and systems will be assessed, and setting specific parameters such as scan depth and frequency. Proper configuration helps maximize the effectiveness of the process, ensuring that all relevant vulnerabilities are considered.
Execution and Automation
Once the configuration is complete, running the assessment with automated tools streamlines the detection process. These tools can quickly analyze large networks and pinpoint weaknesses without the need for manual intervention. Automation reduces the time spent on repetitive tasks and enhances accuracy by eliminating human error. Customizing automated scans based on specific environments or requirements ensures that results are both comprehensive and targeted.
How to Prepare for Security Assessment Certification
Successfully preparing for a certification focused on network security requires a combination of theoretical knowledge and hands-on experience. A structured approach to studying, along with a solid understanding of the tools and techniques used in vulnerability detection, will provide the foundation necessary to excel. Key to success is mastering both the concepts and the practical application of assessment tools.
Study the Fundamentals of Security Analysis
Begin by reviewing the essential concepts related to network protection and system evaluation. Understanding the core principles will help contextualize more advanced methods. Focus on the following areas:
- Common types of vulnerabilities
- Security protocols and their importance
- Methods for analyzing network configurations
- Risk management strategies
Hands-on Experience with Assessment Tools
Practical experience is critical for applying theoretical knowledge. Use simulation tools to familiarize yourself with the steps involved in vulnerability assessments. Practice with various scanning configurations and become proficient in reading and interpreting results. Areas to focus on include:
- Setting up automated scans
- Creating custom profiles for different environments
- Analyzing scan results for actionable insights
- Generating reports based on findings
By practicing regularly and reviewing the results of different assessments, you will build the confidence needed to succeed in any certification test.
Understanding Vulnerability Assessments
Effectively identifying security flaws within a network requires a comprehensive approach that includes the use of specialized tools to detect vulnerabilities. This process involves evaluating various system components, assessing configurations, and identifying potential weaknesses that could be exploited. A deep understanding of how to run these assessments, along with the ability to interpret the results, is essential for maintaining a secure environment.
The evaluation process begins by targeting specific systems and applications within the network. By performing regular checks, security professionals can uncover hidden vulnerabilities that may otherwise go unnoticed. With the right methodology, this process ensures that weaknesses are addressed before they can be exploited by malicious actors.
Once an assessment is conducted, the next step involves analyzing the results to determine the severity of each finding. Prioritizing issues based on risk levels and potential impact helps ensure that the most critical threats are addressed first. Having a clear understanding of how to interpret scan results is a key factor in building a secure infrastructure.
Optimizing Vulnerability Assessments for Accuracy
Achieving reliable results from network assessments requires more than just running a basic evaluation. To ensure accuracy, it’s crucial to fine-tune the configuration settings, adjust scan parameters, and ensure that the systems being assessed are properly defined. A precise setup minimizes errors and maximizes the effectiveness of the assessment process.
One of the key aspects of improving accuracy is configuring the assessment to target the correct network devices, applications, and components. By ensuring that the scope is well-defined, unnecessary resources aren’t wasted, and critical areas are thoroughly evaluated. Additionally, adjusting the depth and frequency of the scans helps focus on high-risk areas, reducing the chances of overlooking vulnerabilities.
Another important consideration is ensuring that the most up-to-date information is being used during the assessment. This includes keeping the vulnerability database current and configuring the assessment tool to account for the latest threats. The combination of well-defined configurations, up-to-date data, and carefully managed scan processes results in more accurate and actionable insights.
Best Practices for Effective Reporting

Creating clear, concise, and actionable reports is essential for transforming raw security data into valuable insights. A well-structured report not only highlights identified vulnerabilities but also provides context, prioritization, and recommendations for remediation. Effective reporting helps stakeholders understand the risks and make informed decisions to strengthen security posture.
Key Elements of an Effective Report
An effective report should include the following critical elements:
- Executive Summary: A high-level overview of the findings, tailored for decision-makers.
- Detailed Findings: A thorough breakdown of vulnerabilities, including their severity and potential impact.
- Risk Assessment: A clear categorization of vulnerabilities based on their potential threat to the system.
- Recommendations: Actionable steps for addressing identified issues, including quick fixes and long-term solutions.
Presenting Data for Maximum Clarity
To ensure that the report is easily understood, consider the following tips:
- Use Visual Aids: Incorporate charts, graphs, and tables to present data in a visually digestible format.
- Organize Findings by Severity: Prioritize vulnerabilities based on their risk to the organization to focus efforts on the most critical issues.
- Provide Context: Explain the potential consequences of vulnerabilities to help readers understand their significance.
- Be Clear and Concise: Avoid unnecessary jargon and ensure that the report can be easily understood by both technical and non-technical audiences.
Common Mistakes in Vulnerability Assessments
When conducting network vulnerability assessments, it is easy to make mistakes that can compromise the accuracy and effectiveness of the results. Common errors often stem from improper configuration, inadequate scoping, or misinterpreting the findings. Recognizing these mistakes can help ensure more reliable assessments and prevent security gaps from being overlooked.
Configuration Errors
Incorrect configurations can lead to incomplete or misleading results. Here are some common issues:
- Incorrect Scope Definition: Not defining the correct systems, devices, or network segments to be tested can result in missed vulnerabilities.
- Improper Scan Settings: Choosing the wrong depth or frequency of scans may lead to false negatives or incomplete assessments.
- Outdated Vulnerability Databases: Using outdated threat intelligence can lead to missed detection of the latest vulnerabilities.
Analysis and Reporting Mistakes
Errors in interpreting scan results can diminish the usefulness of the assessment. Common analysis mistakes include:
- Overlooking False Positives: Failing to filter out false positives can overwhelm the report with irrelevant findings.
- Poor Risk Assessment: Not accurately assessing the severity of vulnerabilities can lead to improper prioritization of remediation efforts.
- Inadequate Reporting: Reports lacking clarity or actionable recommendations may fail to communicate the true risks to decision-makers.
Advanced Vulnerability Assessment Features
Modern vulnerability evaluation tools offer advanced features that enhance their ability to identify and assess risks in complex IT environments. These features provide greater flexibility, improved detection capabilities, and more accurate results, allowing security professionals to tailor the evaluation process to specific needs. By leveraging these advanced options, organizations can ensure comprehensive security assessments that are both efficient and effective.
Custom Scan Profiles
One of the most powerful features in vulnerability evaluation tools is the ability to create custom scan profiles. These profiles allow security experts to define specific parameters for different environments or applications, ensuring that the assessment focuses on the most relevant areas. Customization options include:
- Targeting specific IP ranges or systems
- Adjusting the depth of analysis based on system criticality
- Configuring the scan to focus on particular vulnerabilities or threat categories
Advanced Detection Techniques
Advanced detection methods are designed to identify vulnerabilities that are often difficult to spot with basic scans. These techniques include:
- Credentialed Scans: Scans that authenticate with systems to provide deeper visibility into vulnerabilities that are not visible through external scans.
- Deep Packet Inspection: Analyzing the network traffic to identify hidden threats or misconfigurations that might evade other detection methods.
- Continuous Monitoring: Constantly tracking changes to systems and configurations to quickly detect new vulnerabilities as they arise.
Role of Policies in Vulnerability Assessments

In any comprehensive vulnerability evaluation process, policies play a critical role in guiding the scope, configuration, and execution of assessments. Policies ensure that scans are consistent, repeatable, and aligned with an organization’s security requirements. By defining rules and guidelines for conducting these assessments, policies help streamline the process and ensure that security professionals focus on the most significant risks.
How Policies Impact the Assessment Process
Policies define various parameters that can significantly affect the effectiveness of a vulnerability assessment. These include:
- Scope of the Assessment: Policies determine which systems, devices, and applications are included in the evaluation, helping focus efforts on high-risk areas.
- Scan Frequency: Defining the frequency of assessments ensures that vulnerabilities are identified in a timely manner, minimizing the risk of exploitation.
- Severity Levels: Policies outline how vulnerabilities are categorized based on their potential impact, helping prioritize remediation efforts.
Benefits of Well-Defined Policies
Establishing clear policies for conducting vulnerability assessments provides numerous advantages:
- Consistency: Policies ensure that every assessment is performed the same way, producing consistent and comparable results over time.
- Efficiency: By automating repetitive tasks and defining scanning rules, policies help reduce the amount of time spent on each assessment.
- Compliance: Organizations can ensure that their assessments meet regulatory requirements by incorporating relevant security standards into their policies.
Example Policy Table
| Policy Component | Details |
|---|---|
| Scope | Specify target systems, network segments, and applications to be included in the assessment. |
| Frequency | Define how often scans should be performed based on the level of risk and system changes. |
| Severity Levels | Establish severity categories (e.g., low, medium, high) for vulnerabilities to guide prioritization. |
| Compliance Standards | Incorporate regulatory requirements or security frameworks (e.g., PCI-DSS, NIST) into assessment policies. |
Securing Your Network with Vulnerability Assessments
Securing a network requires a proactive approach to identifying potential weaknesses and addressing vulnerabilities before they can be exploited. Conducting regular assessments across various systems and devices helps uncover security gaps that could pose significant risks. These evaluations are essential for maintaining a strong defense against cyber threats, ensuring that your network remains protected and resilient in the face of evolving security challenges.
By implementing vulnerability detection measures, organizations can gain insights into areas that require attention, such as unpatched software, misconfigured settings, or vulnerable open ports. The goal is to continuously monitor and address potential vulnerabilities, effectively preventing cyberattacks and data breaches.
Key Steps in Securing Your Network
To maximize network security, it’s crucial to follow a structured process when identifying and mitigating vulnerabilities:
- Comprehensive Coverage: Ensure that every device, server, and network component is included in the assessment scope to prevent overlooked vulnerabilities.
- Timely Patching: Regularly update software and systems to fix known security flaws, reducing the risk of exploitation.
- Access Controls: Implement strict access policies to limit the exposure of sensitive systems and data.
Effective Vulnerability Management
Effective vulnerability management involves identifying, evaluating, and mitigating security risks. The process typically follows these stages:
- Detection: Use advanced tools to identify vulnerabilities across the network.
- Prioritization: Rank vulnerabilities based on their severity and potential impact to focus on the most critical issues first.
- Remediation: Apply patches, configuration changes, or other fixes to resolve identified issues.
Example Network Vulnerability Table
| Vulnerability Type | Risk Level | Recommended Action |
|---|---|---|
| Outdated Software | High | Apply the latest patches or updates to close known vulnerabilities. |
| Weak Passwords | Medium | Enforce stronger password policies and multi-factor authentication. |
| Open Ports | Low | Close unnecessary ports and use firewalls to block unauthorized access. |
Managing Assessments for Large Environments
When managing security evaluations across large-scale networks, organizations must adopt a strategic approach to ensure efficiency and thoroughness. With numerous systems, devices, and applications to monitor, it becomes increasingly challenging to conduct assessments manually. Automating the process, prioritizing critical assets, and segmenting the network into manageable units are key steps to ensuring comprehensive coverage without overloading resources.
Properly managing assessments in expansive environments requires a combination of efficient tools and a structured methodology. By optimizing resources and focusing efforts where they are most needed, security teams can ensure that vulnerabilities are identified and addressed promptly, preventing potential risks from turning into serious threats.
Key Considerations for Large-Scale Vulnerability Management

- Asset Prioritization: Focus on the most critical systems and networks that are essential to business operations or contain sensitive data.
- Automation: Leverage automation to run routine assessments, reducing the workload on security teams while maintaining consistent coverage.
- Segmented Scanning: Break down large environments into smaller segments, allowing for more targeted and manageable scans that reduce the strain on resources.
Tips for Optimizing Scan Management
- Load Balancing: Distribute the scanning workload across multiple servers to avoid bottlenecks and ensure scans are completed efficiently.
- Scheduled Scans: Run scans during off-peak hours to minimize the impact on network performance and business operations.
- Regular Updates: Keep security tools and vulnerability databases up to date to ensure the most accurate results during assessments.
Automation and Scheduling with Security Assessments
In the realm of vulnerability management, automation and scheduling are crucial elements that enhance the efficiency and consistency of security checks. By automating routine assessments, organizations can save time, reduce human error, and ensure that security evaluations are conducted regularly without manual intervention. Scheduling these assessments strategically further ensures that critical scans are carried out at the most optimal times, without disrupting network operations or system performance.
Through effective automation and scheduling, companies can stay ahead of potential threats, address vulnerabilities more promptly, and maintain a proactive approach to cybersecurity. With the ability to automate both simple and complex tasks, security teams can focus on more strategic initiatives, such as analyzing results and implementing security measures.
Advantages of Automation in Security Monitoring
- Time Efficiency: Routine security checks are completed automatically, freeing up valuable resources for other critical tasks.
- Reduced Human Error: Automated processes are consistent and minimize the likelihood of mistakes that can occur during manual assessments.
- Enhanced Coverage: Automation ensures that all assets are assessed regularly, without missing key components of the network.
Effective Scheduling Practices for Vulnerability Assessments
- Off-Peak Scheduling: Schedule scans during off-peak hours to minimize impact on system performance and user activities.
- Frequent Interval Scans: Set up recurring assessments at appropriate intervals to maintain continuous visibility into system health.
- Prioritization of Critical Systems: Configure schedules that prioritize assessments for high-risk or critical infrastructure components.
Integrating Security Tools for Enhanced Effectiveness
Integrating vulnerability management platforms with other security tools allows organizations to streamline their operations and improve overall security. By combining different systems, teams can achieve better visibility, enhance threat detection, and automate workflows. This integration ensures that data from various sources is consolidated, providing a more comprehensive approach to risk management and remediation.
When integrating security tools, it is essential to ensure that the systems can exchange information seamlessly, allowing for real-time updates and collaboration across different platforms. Effective integration helps in reducing manual effort, improving response times, and providing more accurate and up-to-date insights on vulnerabilities.
Key Benefits of Integration
- Streamlined Operations: Automation of processes across multiple tools reduces redundancy and manual intervention, leading to more efficient security management.
- Improved Threat Detection: By combining data from multiple security platforms, organizations can gain deeper insights into potential risks and vulnerabilities.
- Faster Response Times: Automated workflows enable quicker identification and remediation of vulnerabilities, minimizing the time between detection and resolution.
Best Practices for Tool Integration
- API Usage: Leverage APIs to enable seamless communication between different security tools, ensuring smooth data flow and consistent updates.
- Centralized Dashboards: Use a centralized dashboard to manage all integrated tools, providing a unified view of vulnerabilities, threats, and remediation efforts.
- Regular Syncing: Ensure that data across platforms is regularly synchronized to maintain the accuracy and relevance of the security information.
Creating Custom Scan Profiles
Creating customized profiles for security assessments allows organizations to tailor their vulnerability detection to specific needs, improving the relevance and efficiency of the process. Custom profiles can be designed to focus on particular assets, configurations, or security checks, ensuring a more precise evaluation of potential risks. By defining these profiles, teams can optimize scanning for their unique environment, making it easier to identify critical vulnerabilities.
When developing personalized scan profiles, it is important to consider the scope, frequency, and depth of the assessments. Customization can help address specific concerns, whether it’s focusing on a particular network segment, type of device, or a set of security standards. The more accurately the profiles align with organizational priorities, the better the scanning results will reflect real-world risk scenarios.
Steps to Create Custom Profiles
- Define Scope: Determine the specific assets or systems to be targeted. This could include servers, endpoints, network devices, or web applications.
- Set Custom Parameters: Adjust settings such as scanning frequency, types of checks, and specific vulnerability categories to align with organizational priorities.
- Review Profile Results: After scanning with the custom profile, evaluate the results and refine the profile as necessary to improve accuracy and effectiveness.
Best Approaches for Custom Profile Design
- Use Templates: Start with predefined templates that can be modified according to the specific needs of your environment, saving time and effort.
- Test and Iterate: Continuously test the custom profiles to ensure they are producing accurate and actionable results. Refine the profiles based on feedback and changing conditions.
- Focus on Critical Assets: Prioritize profiles for critical infrastructure or sensitive systems, ensuring these receive more frequent or deeper checks.
Understanding Scan Results and Alerts
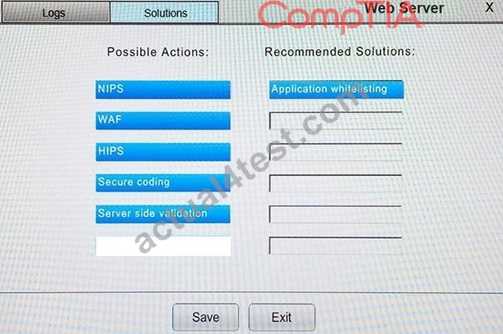
When conducting a security assessment, interpreting the results and alerts correctly is crucial to effectively addressing vulnerabilities. These findings provide detailed information on potential weaknesses within the system, ranging from low-risk issues to critical security flaws. The challenge lies in analyzing this data accurately to prioritize remediation actions based on the severity and impact of the detected risks.
Alerts typically highlight areas requiring immediate attention. By categorizing these alerts into different risk levels, organizations can focus their efforts on addressing the most critical issues first. Understanding the context of each alert is essential to ensure that no significant vulnerability is overlooked, and that less severe warnings do not divert attention from more pressing concerns.
Common Categories in Scan Results
Scan results usually fall into several key categories, each representing a different level of risk. These categories help security professionals prioritize response actions based on the severity and potential impact of each identified vulnerability.
| Risk Level | Description | Action Required |
|---|---|---|
| Critical | Vulnerabilities that could lead to severe security breaches, such as unauthorized access or data exfiltration. | Immediate remediation is required to protect the network. |
| High | Potential risks that could be exploited under certain conditions but do not represent an immediate threat. | Address these issues as soon as possible to minimize exposure. |
| Medium | Less urgent vulnerabilities, often associated with system misconfigurations or outdated software. | Schedule fixes for a later time, but do not ignore them. |
| Low | Minor vulnerabilities that are unlikely to result in exploitation but should be addressed as part of routine maintenance. | Fix as part of regular security upkeep or during the next update cycle. |
Handling Alerts Effectively
- Prioritize Remediation: Begin with the highest-risk issues, addressing critical and high-level alerts first.
- Regular Monitoring: Continuously monitor alerts to ensure that new vulnerabilities are identified and managed quickly.
- Automate Responses: Where possible, automate responses to certain alerts to speed up the remediation process and reduce human error.
How to Troubleshoot Scan Issues
When conducting assessments, technical issues may arise that prevent scans from running smoothly. Identifying and addressing these issues promptly is essential to maintain the accuracy and efficiency of the process. Troubleshooting often involves understanding the underlying cause of failures, whether due to configuration errors, network problems, or system incompatibilities.
The first step in troubleshooting is to review the error messages or logs generated during the process. These can provide valuable insights into what went wrong, helping to pinpoint specific issues such as connectivity failures or misconfigurations. Once the problem is identified, resolving it may involve adjusting system settings, verifying network access, or updating software components.
Common Causes of Scan Failures
- Network Connectivity: Issues like firewalls, proxy settings, or incorrect IP address configurations can block access to the target systems.
- Misconfigured Settings: Incorrect parameters in the scan configuration, such as wrong credentials or scan targets, can cause failures.
- System Resource Limitations: Insufficient memory or CPU power can hinder scan performance, leading to incomplete or failed attempts.
- Outdated Software: Using outdated tools or components may cause compatibility issues with newer system configurations.
Troubleshooting Steps
- Check Network Connectivity: Ensure the target system is accessible from the scanning device and that no firewalls or network configurations block communication.
- Review Scan Configuration: Verify that the scan settings, including IP ranges, credentials, and protocol selection, are correctly configured.
- Examine Logs: Look at error logs to gather more specific details about why the scan did not complete as expected.
- Check System Resources: Ensure that the scanning process is not being interrupted due to lack of resources like memory or processing power.
- Update Components: Regularly update both the scanning tools and the target systems to prevent compatibility issues.
Final Tips for Success in Qualys Exams
Preparing for assessments in this field requires more than just theoretical knowledge; hands-on experience and a deep understanding of core concepts are key. To achieve success, it’s important to approach the process methodically, leveraging both study materials and practical skills to ensure thorough preparation.
By focusing on key areas such as system configurations, troubleshooting methods, and understanding different protocols, you can build the necessary foundation. Consistent practice, along with understanding real-world applications, will help reinforce the knowledge you need to excel.
Effective Study Techniques
- Review Core Concepts: Ensure you have a strong grasp of the fundamental concepts and tools used in the field.
- Practice Hands-On: Simulating real-world scenarios through practice exercises can enhance your understanding and retention.
- Use Available Resources: Take full advantage of study guides, manuals, and online resources to fill in any gaps in your knowledge.
- Understand the Tools: Familiarize yourself with the tools and technologies used to carry out assessments, focusing on common configurations and settings.
On the Day of the Assessment

- Stay Calm: Approach the assessment with a calm and focused mindset. This will help you think clearly and manage time effectively.
- Review Instructions Carefully: Read through all instructions before starting. Ensure that you understand the requirements of each task or question.
- Manage Time Wisely: Allocate time appropriately to each section, avoiding spending too much time on any one question or task.
- Check Your Work: If possible, review your answers before submitting. This will help ensure there are no overlooked mistakes.