
Preparing for a professional certification in Kubernetes security requires a solid understanding of both theoretical concepts and practical skills. The journey to achieving this certification can seem daunting, but with the right guidance, resources, and practice, you can confidently approach the challenge.
Success in this field relies on mastering the key areas of Kubernetes security. This includes understanding containerized environments, securing Kubernetes clusters, and applying best practices for continuous deployment. To excel, it’s essential to familiarize yourself with the types of topics commonly covered and practice solving real-world security problems.
Structured study and hands-on experience are critical for anyone looking to pass the certification assessment. Focusing on areas such as cluster hardening, network policies, and vulnerability management will prepare you for the variety of tasks and scenarios you’ll encounter during the evaluation process.
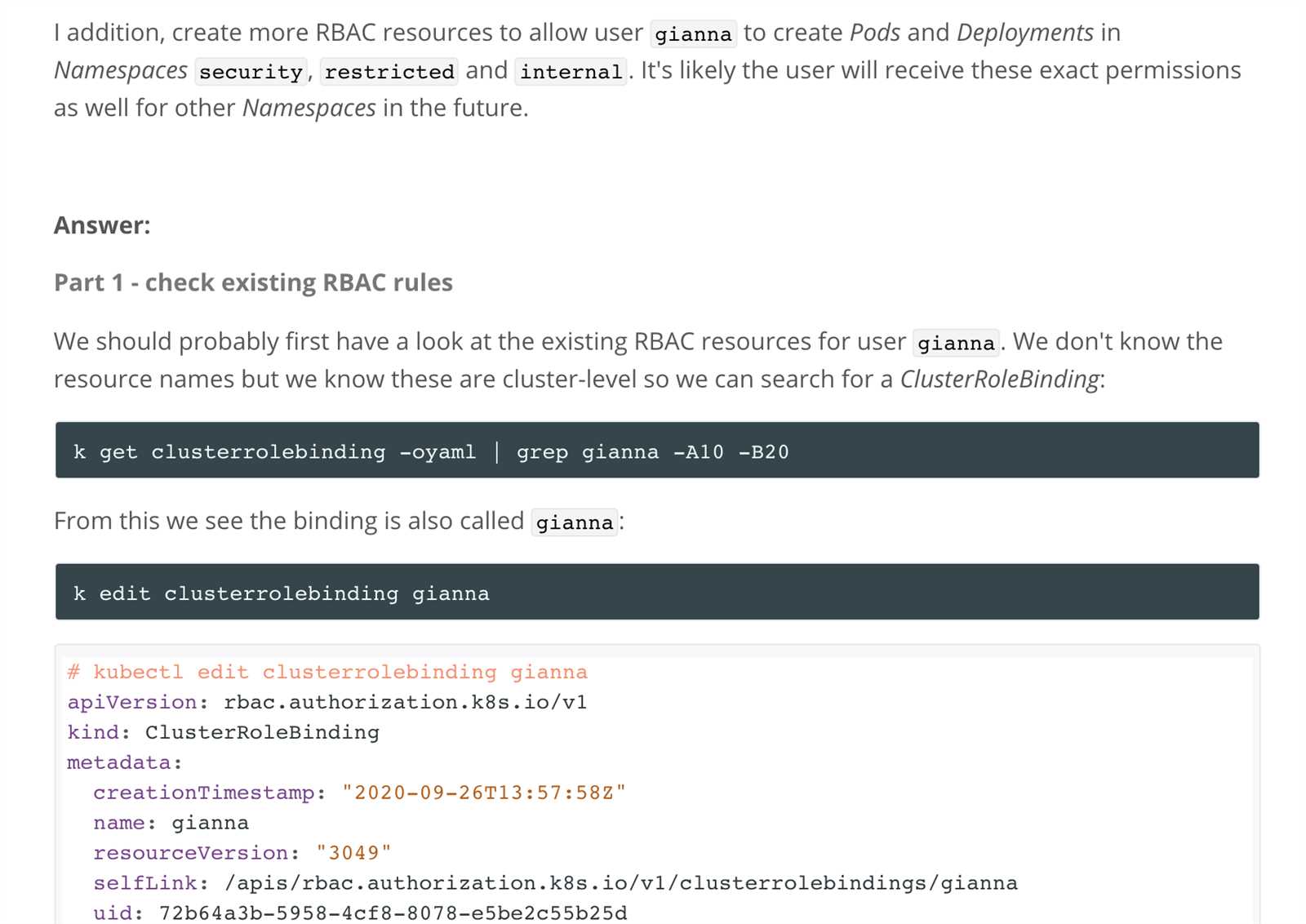
Cks Exam Questions and Answers
Achieving certification in Kubernetes security involves a rigorous assessment of your practical skills and understanding of security concepts. It is essential to engage with various problem-solving exercises to simulate real-world scenarios, allowing you to develop the necessary expertise. The focus is on securing cloud-native applications, managing cluster access, and ensuring robust network policies.
Core Areas to Master
To succeed, it’s vital to cover several critical domains. These include hardening containerized environments, applying security best practices to clusters, and defending against potential threats. A clear grasp of authentication methods, role-based access control (RBAC), and auditing tools will significantly enhance your performance. Focusing on these areas will help you tackle a wide range of practical challenges with confidence.
Approaching the Challenge
One of the best ways to prepare is by practicing with realistic scenarios that mirror the situations you will encounter. Simulating security breaches, vulnerability scans, and implementing automated security policies will help you refine your abilities. This hands-on approach ensures you’re ready to address complex issues efficiently during the evaluation process.
Understanding the CKS Exam Format
The certification assessment for Kubernetes security is designed to evaluate both theoretical knowledge and practical expertise. It consists of different components that focus on various aspects of securing cloud-native systems. The structure of the test ensures that candidates can demonstrate proficiency in deploying, managing, and securing Kubernetes clusters in a real-world environment.
Structure of the Evaluation

The evaluation process typically includes a set of performance-based tasks that simulate actual scenarios you would face in a production environment. These tasks assess your ability to implement security measures, troubleshoot issues, and configure secure Kubernetes setups. Time management is crucial, as each task has a limited duration and demands accuracy in execution.
Types of Tasks You Will Face

Tasks will vary in complexity and may require hands-on interaction with different tools and platforms. You will be asked to apply security practices, configure policies, and handle unexpected incidents. The focus is on practical knowledge, and candidates must showcase their ability to work efficiently under pressure while adhering to best practices for securing Kubernetes systems.
Key Topics Covered in CKS Exam
The assessment for Kubernetes security covers a wide range of critical topics that are essential for anyone looking to prove their proficiency in securing containerized environments. The focus is on the practical application of security measures, including the ability to manage vulnerabilities, enforce policies, and secure clusters effectively.
Key areas of focus include container security, cluster hardening, access control mechanisms, and securing the network within Kubernetes environments. Mastery of these topics is crucial, as they form the foundation for ensuring that cloud-native applications are both secure and resilient to potential threats. Additionally, managing secrets, logging, and monitoring are also key aspects that will be evaluated during the process.
Best Resources for Exam Preparation
Effective preparation for a Kubernetes security certification requires a strategic approach, leveraging quality materials that cover all critical topics. The right resources will help you build both theoretical understanding and hands-on experience, ensuring you’re well-equipped to handle practical tasks and scenarios during the evaluation process.
To enhance your preparation, it’s important to focus on a variety of materials, such as official documentation, practice labs, online courses, and community forums. Hands-on labs and interactive tutorials are particularly beneficial, as they allow you to apply what you’ve learned in a controlled environment. Additionally, staying up to date with the latest Kubernetes developments and security trends is essential to achieving success.
Common CKS Exam Question Types
The certification process evaluates candidates using a range of different task formats that test both knowledge and practical skills. The primary goal is to assess the ability to apply security principles in real-world Kubernetes environments. Candidates can expect to encounter a variety of scenarios that require problem-solving and hands-on configuration skills.
Task Types
The most common task types include:
- Configuration Challenges – Tasks where you must configure Kubernetes security settings, such as network policies or access controls.
- Security Incident Handling – Simulating security breaches and asking you to resolve vulnerabilities or mitigate threats.
- Cluster Management – Managing cluster security, including configuring secrets and hardening the environment.
- Audit and Monitoring – Tasks requiring you to configure or interpret audit logs and monitoring tools to identify potential risks.
Scenario-Based Exercises
Scenarios may involve specific challenges that require you to apply multiple security practices to address the issue at hand. Some common examples include:
- Implementing RBAC policies to ensure proper access controls across various user roles.
- Securing a container registry by configuring scanning tools and policies for vulnerability management.
- Configuring network security through the application of network segmentation or firewall rules.
Time Management Strategies for CKS

Successfully navigating a professional certification for Kubernetes security requires not only technical knowledge but also effective time management. With a limited amount of time to complete each task, it’s essential to approach the evaluation process with a clear strategy to ensure you can address each challenge thoroughly and efficiently.
Prioritize Key Tasks
Start by identifying the most critical areas that require your attention. Focus on tasks that involve complex configurations or require a deeper understanding of Kubernetes security principles. This approach will ensure that you allocate more time to challenges that could be more time-consuming or difficult to resolve.
Practice with Timed Scenarios
One of the best ways to develop your time management skills is through practice. Set up timed simulations that mirror the type of scenarios you’ll face. This will help you become familiar with the time pressure and identify areas where you may need to speed up or adjust your approach.
How to Improve Your Kubernetes Skills
Enhancing your expertise in Kubernetes requires a combination of theoretical study and hands-on experience. Focusing on key areas such as cluster management, security practices, and automation will help you become proficient in deploying, managing, and securing containerized applications. Building practical skills and understanding best practices is essential to mastering this powerful platform.
One effective way to improve your skills is by engaging in practical exercises that simulate real-world scenarios. In addition, following structured learning paths, using official documentation, and participating in community forums can further boost your understanding.
| Area of Focus | Recommended Resources | Practice Strategies |
|---|---|---|
| Cluster Setup | Official Kubernetes Documentation, Online Courses | Build clusters using Minikube, K3s, or other local tools |
| Security Practices | Books, Webinars, Security Guides | Practice securing a cluster with RBAC, network policies, and secrets management |
| Monitoring and Logging | Tutorials, Community Blogs | Set up monitoring tools like Prometheus and Grafana in a test environment |
| Automation | Online Courses, GitHub Repositories | Automate deployments and configurations with Helm charts and CI/CD pipelines |
Essential Tools for CKS Exam Success
Achieving success in Kubernetes security certification requires more than just knowledge; it also demands the use of the right tools. These tools not only help you prepare more effectively but also enhance your ability to handle practical scenarios during the evaluation process. From container orchestration platforms to security scanning tools, each resource plays a critical role in your journey to mastery.
Key Tools for Configuration and Security
When preparing for the assessment, there are several must-have tools that will help you configure, secure, and monitor Kubernetes environments:
- Minikube – A lightweight tool that allows you to run a local Kubernetes cluster for testing and experimentation.
- Kubeadm – Useful for creating and managing Kubernetes clusters in different environments.
- Helm – A package manager for Kubernetes that simplifies the deployment of applications and configuration management.
- kubectl – The command-line tool for interacting with your Kubernetes clusters, essential for managing resources and debugging issues.
Tools for Monitoring and Auditing
Ensuring that your clusters are secure and functioning optimally involves constant monitoring. These tools are invaluable for identifying potential vulnerabilities and performance issues:
- Prometheus – An open-source monitoring and alerting toolkit for Kubernetes, useful for tracking cluster health and performance.
- Grafana – A powerful visualization tool that works with Prometheus to create interactive dashboards for monitoring cluster activity.
- Kube-hunter – A security scanning tool that identifies vulnerabilities within your Kubernetes environment.
Preparing for the Security Domain
The security domain is a crucial area of focus when pursuing certification in Kubernetes security. It involves understanding how to protect both the infrastructure and the applications running within a Kubernetes environment. Mastering this domain requires knowledge of security best practices, tools, and strategies to secure clusters, manage access, and mitigate vulnerabilities.
Preparation for this domain should include hands-on experience with key security practices, such as configuring role-based access control (RBAC), securing communications, and implementing network policies. Additionally, you should familiarize yourself with threat detection tools, incident response protocols, and the principles behind securing containerized applications. By practicing real-world scenarios and staying updated with the latest security trends, you can ensure a comprehensive understanding of Kubernetes security.
Practice Questions for CKS Exam
Preparing for a certification focused on Kubernetes security requires rigorous practice to test your skills and knowledge. Engaging with realistic scenarios and tasks will help you become comfortable with the challenges you may face. These practice exercises are designed to reinforce core concepts, improve problem-solving abilities, and prepare you for the actual environment.
To fully prepare, consider using mock tasks that mirror the types of practical exercises you will encounter. Below are some examples of areas where you can test your readiness:
- Network Policy Configuration: Practice defining network policies to control traffic flow and enhance security between pods in your cluster.
- RBAC Role Management: Set up role-based access control to restrict or allow specific actions for different users within your Kubernetes environment.
- Container Security: Test your ability to secure containers by scanning images for vulnerabilities and setting up secure configurations for container runtimes.
- Incident Response: Simulate a breach scenario and practice identifying the vulnerability, investigating logs, and applying fixes.
- Secrets Management: Practice securely storing and managing sensitive information using Kubernetes secrets and other best practices.
Common Mistakes to Avoid in CKS
When preparing for a certification focused on Kubernetes security, it’s essential to recognize and avoid common pitfalls that can hinder your progress. Many candidates, especially those new to the platform, make mistakes that can be easily avoided with the right preparation and mindset. These mistakes often stem from insufficient understanding of key concepts or underestimating the complexity of certain tasks.
Common Errors in Configuration and Setup
Improper configurations or skipping essential setup steps can lead to significant issues down the line. Below are some of the most common mistakes related to configuration and cluster setup:
| Error | Impact | Solution |
|---|---|---|
| Not using RBAC properly | Weakens access control and security policies | Ensure proper role definitions and permissions for users and services |
| Misconfiguring network policies | Exposes the cluster to unauthorized access and communication | Double-check network rules and ensure restrictive policies are applied |
| Ignoring container security best practices | Increases the risk of vulnerabilities in containers | Implement image scanning tools and avoid running containers with unnecessary privileges |
Neglecting Testing and Validation
Many fail to thoroughly test their configurations before deploying them into a live environment. This can lead to missed vulnerabilities or misconfigurations. Here’s what to avoid:
| Error | Impact | Solution |
|---|---|---|
| Skipping testing on staging environments | Risk of issues in production | Always test configurations and deployments in a staging environment first |
| Not validating security policies | Exposes critical infrastructure to potential breaches | Regularly audit and test security configurations |
How to Tackle Complex Scenarios
Complex tasks in Kubernetes security often involve multiple steps, decision points, and the need for a solid understanding of various concepts. Approaching these challenges requires a methodical and strategic mindset. Breaking down each problem into smaller, manageable parts can help clarify the most effective solutions and prevent overwhelming the candidate. A structured approach combined with hands-on practice is key to mastering difficult scenarios.
Here are a few strategies to successfully navigate challenging situations:
- Identify Key Requirements: Start by understanding the core objectives of the scenario. What are you asked to secure or configure? Breaking down the problem helps you focus on the most relevant areas.
- Analyze the Environment: Pay attention to the specific details of the environment in which you’re working. Take note of current configurations, security policies, and any restrictions that could impact your approach.
- Plan Your Actions: Rather than jumping straight into a solution, create a plan that includes clear steps. Consider the most efficient order to apply configurations and monitor the effects as you go.
- Stay Calm Under Pressure: Difficult scenarios may involve high-stress situations. It’s important to stay composed, analyze the problem logically, and avoid rushing to conclusions.
- Test and Verify: After implementing changes, test them to ensure they have the desired effect. Validation is critical in preventing misconfigurations that could lead to security risks.
By applying these strategies and practicing regularly with real-world scenarios, you’ll build the confidence needed to tackle complex tasks effectively.
Study Plans for CKS Exam Success
Creating an effective study plan is crucial when preparing for certification in Kubernetes security. A well-structured approach ensures that you cover all necessary topics in a logical and systematic manner. The key to success lies in prioritizing areas that are more complex or require hands-on experience, while also revisiting the foundational concepts that provide a strong understanding of the platform.
Here are several tips for designing a study plan that maximizes your chances of success:
- Set Clear Goals: Define what you aim to achieve within a set timeframe. For example, aim to master specific topics each week, such as securing container runtimes or configuring network policies.
- Allocate Time Wisely: Balance theory with practical exercises. Plan to spend a significant amount of time on labs and hands-on practice, as real-world experience is essential for mastering complex concepts.
- Follow a Structured Curriculum: Utilize official resources, textbooks, and online courses to guide your study. Follow a proven curriculum that ensures you don’t miss any critical topics.
- Track Your Progress: Regularly review what you’ve learned and track your progress. Set small, achievable milestones to help maintain motivation and ensure you’re on track to cover all material.
- Review and Revise: In the final stages of preparation, dedicate time to review and reinforce key concepts. Focus on areas where you feel less confident and practice mock scenarios to build your problem-solving skills.
By following a structured study plan, you can approach your certification with confidence, ensuring you’re fully prepared to tackle even the most challenging scenarios.
Overview of Kubernetes Security Best Practices
Maintaining a secure Kubernetes environment requires the implementation of a comprehensive set of best practices. These practices not only help protect applications and data but also mitigate the risk of security breaches and unauthorized access. Security must be a fundamental consideration at every stage of the development and deployment lifecycle, from container image creation to runtime security and network management.
Below are some critical best practices for securing a Kubernetes environment:
Cluster Hardening
Cluster hardening involves securing the infrastructure that Kubernetes runs on. This includes setting up secure access controls, ensuring that only authorized users can access the cluster, and regularly updating the underlying operating system and Kubernetes components to patch known vulnerabilities.
- Role-Based Access Control (RBAC): Implement RBAC policies to ensure that users only have the permissions necessary for their tasks.
- Use Namespaces for Isolation: Organize workloads into separate namespaces to isolate sensitive applications and reduce the impact of potential security threats.
- Node Security: Secure Kubernetes nodes by restricting access, using minimal operating systems, and ensuring the nodes are regularly updated.
Container Security

Containers must be secured from the moment they are built until they are deployed. This includes scanning container images for vulnerabilities and ensuring that only trusted images are used in production environments.
- Image Scanning: Use tools to scan container images for known vulnerabilities and malware before they are deployed.
- Limit Privileges: Containers should run with the least privileges necessary to function. Avoid running containers as root whenever possible.
- Use Read-Only File Systems: Run containers with read-only file systems to prevent attackers from modifying containerized applications.
Network Security
Securing network traffic between containers, nodes, and services is critical in any Kubernetes deployment. Effective network policies help to limit access and secure data communication across the cluster.
- Network Policies: Implement network policies to control the traffic flow between pods and services, limiting access based on the principle of least privilege.
- Use TLS for Encryption: Always use Transport Layer Security (TLS) to encrypt communications between services and applications within the cluster.
- Limit Ingress and Egress Traffic: Restrict unnecessary inbound and outbound network traffic to and from the cluster, reducing the attack surface.
Compliance and Monitoring
Continuous monitoring of the Kubernetes environment is essential for detecting potential threats and ensuring compliance with security standards. Implement logging, auditing, and continuous vulnerability scanning to stay ahead of emerging risks.
- Audit Logs: Enable audit logging to track all access and actions taken within the cluster for troubleshooting and compliance purposes.
- Security Tools Integration: Use security tools to continuously monitor the cluster and alert administrators to unusual activity or vulnerabilities.
By adhering to these best practices, organizations can ensure a secure Kubernetes environment that supports safe, efficient, and reliable application deployments.
How to Take the CKS Exam
Successfully completing a certification test requires careful preparation, understanding the process, and knowing what to expect on the day of the assessment. Proper planning and focus on essential concepts will help you achieve the desired outcome. This guide walks you through the essential steps to effectively participate in the assessment and perform at your best.
Step 1: Registration Process
The first step towards completing the certification is registering for the test. The process is straightforward but requires you to choose a date and time that works best for you. Ensure that you have the necessary prerequisites, such as knowledge of Kubernetes and security fundamentals, as they are integral to the test.
- Choose a Test Window: Select a convenient time frame for your test and make sure to complete your registration ahead of the deadline.
- Payment and Confirmation: After registration, you’ll need to confirm your payment and review the final test details provided in your confirmation email.
Step 2: Preparing for the Assessment
Preparation is key. You should review the topics covered in the test and focus on any weak areas. Hands-on practice is invaluable, as real-world experience helps solidify your understanding of the concepts and tools involved.
- Study Official Documentation: Utilize the official Kubernetes documentation and other trusted resources to ensure you’re familiar with all relevant concepts.
- Simulate the Environment: Set up test environments to practice tasks in a controlled setting. This will help you gain the confidence to tackle practical scenarios during the test.
- Practice Under Time Constraints: Time management is crucial. Try to complete practice tasks within the time limits to ensure you’re ready for the time-bound nature of the assessment.
Once you’re fully prepared, the day of the assessment will be less stressful. Take a deep breath, manage your time wisely, and stay focused on the tasks at hand. With the right preparation and mindset, you will be able to demonstrate your knowledge and skills effectively.
Top Strategies for Passing the Exam
Achieving success in any certification assessment requires more than just knowledge; it demands careful planning, strategy, and a clear focus. By applying the right approach, you can maximize your chances of success and complete the challenge with confidence. This section highlights the most effective methods to help you prepare, stay organized, and perform well during the assessment.
1. Understand the Assessment Format
Familiarizing yourself with the structure of the assessment is essential. Knowing the types of tasks and how they are evaluated will help you approach them more effectively. Understanding the test format also allows you to develop a study plan that covers the necessary skills and knowledge areas.
- Review Task Types: Ensure you’re clear on the kind of activities that will be tested, whether theoretical or practical.
- Time Management: Knowing the time constraints will help you pace yourself during the test, allowing you to allocate time appropriately to each task.
- Prioritize Key Areas: Focus on the areas that are most likely to be covered based on the assessment’s objectives.
2. Hands-on Practice and Real-world Experience
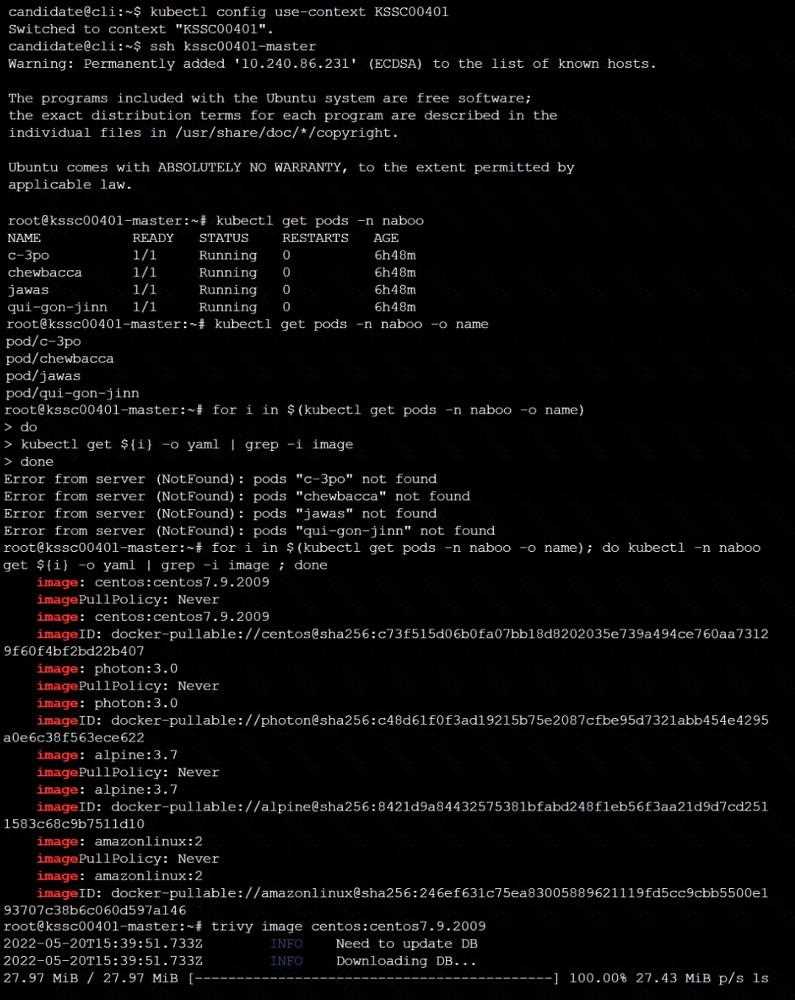
Theory alone isn’t enough to succeed. Practicing in real-world environments and applying what you’ve learned in actual scenarios will reinforce your knowledge and increase your confidence. This practical experience is crucial for tackling complex scenarios that may arise during the test.
- Set Up Simulated Environments: Create test scenarios in controlled settings to gain familiarity with different configurations and tasks.
- Use Online Labs: Many platforms offer interactive labs that simulate real-world environments, providing hands-on practice without needing to set up your own system.
- Apply Concepts in Practice: Work on actual use cases and troubleshoot problems to build problem-solving skills under realistic conditions.
3. Take Care of the Logistics
Ensure that you have everything in place well before the assessment day. This includes technical preparations, understanding the rules, and having the necessary resources ready. Proper logistics help you reduce stress and focus on performing your best.
- Verify System Requirements: Ensure your system is set up to meet all technical requirements and you have access to the platform on test day.
- Know the Rules: Familiarize yourself with the testing policies, including time limits, available resources, and acceptable practices.
- Get Enough Rest: Don’t neglect your health. Ensure you are well-rested and mentally prepared for the challenge ahead.
By following these strategies and maintaining a disciplined approach, you’ll be in a strong position to pass the assessment with ease. Preparation, practice, and focus will ensure you’re fully equipped to succeed when the time comes.
Understanding Certification Requirements
Before pursuing any professional certification, it is important to understand the key prerequisites and conditions that must be met. This includes a thorough understanding of eligibility criteria, required skills, and specific expectations that will ensure you are fully prepared for the certification process. This section outlines what you need to know to meet the requirements and achieve success.
1. Prerequisites for Certification
Each certification has specific eligibility criteria that must be fulfilled prior to registration. These requirements typically include a combination of prior experience, knowledge, and sometimes training. It is essential to assess whether you meet these conditions before starting your preparation.
- Required Experience: Certain certifications require candidates to have hands-on experience in relevant fields such as cloud computing, container orchestration, or security management.
- Training and Courses: Some certifications may require you to complete a certain number of training hours or courses before applying for the certification.
- Pre-existing Certifications: In some cases, candidates are required to have a foundational certification before moving on to more advanced levels.
2. Skills and Knowledge Areas
To succeed in the certification process, candidates need to have a solid understanding of key concepts and technologies related to the certification domain. This involves not only theoretical knowledge but also practical experience in applying those concepts in real-world scenarios.
- Technical Proficiency: A deep understanding of the tools, platforms, and technologies in use, including container management systems, networking protocols, and security frameworks.
- Hands-on Practice: The ability to practically apply theoretical knowledge through simulated environments or real-life situations will help reinforce key concepts and improve problem-solving abilities.
- Problem-Solving Skills: Many certifications assess your ability to handle complex situations and make decisions under pressure. Practicing decision-making and troubleshooting techniques is vital for success.
3. Preparing for the Assessment
Once the eligibility and knowledge areas are understood, it is important to develop a study plan and use the right resources to ensure preparation is focused and effective. Familiarize yourself with available study materials, practice tools, and online resources that can assist in mastering the required topics.
- Study Materials: Books, online guides, and video tutorials that cover both theoretical and practical aspects of the subject matter.
- Practice Tools: Utilizing mock assessments or hands-on labs to test your skills and identify any areas of improvement.
- Community Support: Joining forums, study groups, or online communities can provide valuable insights, tips, and additional resources to aid your preparation.
By understanding these core requirements, you will be well-equipped to pursue your certification goals and increase your chances of success. Proper planning, skill development, and resource utilization are key to achieving your certification objectives.