
Successfully passing the certification process for IT professionals requires a solid understanding of both theory and practical skills. To achieve this, it’s important to familiarize yourself with key topics, concepts, and practical tasks that will be tested. Comprehensive preparation can ensure you’re confident when tackling different scenarios during the evaluation phase.
The challenges presented during the assessment often involve a mix of theoretical knowledge and real-world problem-solving. Understanding how to effectively manage various network configurations, security settings, and virtualization tasks can make a significant difference. Thorough practice with real-life scenarios will help solidify your readiness and boost your chances of success.
In this guide, we will explore essential areas that are commonly covered, offering useful tips and practical examples to aid your preparation. By reviewing important areas, such as role management, troubleshooting techniques, and system configurations, you will be better equipped to navigate the evaluation process with confidence.
Windows Server 2012 Exam Preparation Tips
Preparing for a professional IT certification requires a focused and strategic approach. To succeed, it’s essential to build a strong foundation in the core concepts and practical skills that are evaluated. Identifying key topics and understanding their real-world applications will help streamline your study process and improve your performance.
One effective strategy is to break down the subject matter into manageable sections, allowing you to focus on mastering individual areas. Create a study schedule and allocate sufficient time to each topic, ensuring that you understand both the theory behind the concepts and how to implement them in practical scenarios. This balanced approach will enhance retention and boost confidence when tackling different challenges.
Additionally, practice with hands-on exercises is crucial for solidifying your knowledge. By working through realistic scenarios, you will become more familiar with the tasks that are likely to be presented. Consider using virtual labs or simulated environments to replicate real-life situations. This practical experience will help you think critically and apply your skills effectively when under time pressure.
Reviewing past materials and utilizing various study resources, such as online tutorials, practice tests, and forums, can also be beneficial. Engaging with a community of learners allows you to exchange insights and clarify doubts. By regularly assessing your progress through mock tests, you can identify weak areas and focus on improving them before the actual evaluation.
Overview of Windows Server 2012 Certification
Achieving professional certification in IT is a significant milestone that validates one’s expertise in system administration, network management, and IT infrastructure. This credential demonstrates a deep understanding of key concepts and the ability to manage and maintain complex environments. It is highly valued by employers looking for qualified professionals to handle critical tasks and ensure system stability.
Key Skills and Knowledge Areas
The certification focuses on various technical areas, such as network configuration, security protocols, role management, and virtual environments. Mastery of these topics ensures candidates can efficiently administer systems and address real-world challenges. Professionals are tested on their ability to deploy, manage, and troubleshoot essential IT solutions, equipping them with the skills needed to handle both routine and complex scenarios.
Benefits of Obtaining the Certification
Obtaining this certification offers numerous benefits, including career advancement and recognition as a qualified expert in IT administration. It provides a competitive edge in the job market and is often required for roles in enterprise-level organizations. Additionally, it boosts personal confidence by validating one’s technical knowledge and problem-solving abilities, which are crucial for managing large-scale infrastructures.
Key Concepts for Exam Success
To excel in any professional evaluation, mastering foundational concepts and developing practical skills are essential. A clear understanding of core principles allows candidates to confidently approach different tasks, whether theoretical or hands-on. Focusing on these key areas ensures better preparation and a higher likelihood of success during the assessment.
One important concept to focus on is system configuration. Understanding how to properly set up, configure, and manage various components is critical. Familiarity with network configurations, security settings, and user management ensures you’re prepared for real-world situations that require immediate and accurate solutions.
Another vital area is troubleshooting. Being able to identify and resolve issues efficiently is an indispensable skill for IT professionals. Developing a logical approach to problem-solving, along with a solid grasp of diagnostic tools, will make it easier to tackle challenges effectively under time constraints.
Additionally, having a deep knowledge of storage solutions, virtualization, and backup strategies will play a significant role in your success. These areas are crucial for ensuring system integrity and reliability, and are frequently tested. Mastery of these subjects allows you to approach the assessment with confidence and clarity.
Top Exam Questions to Expect
When preparing for a professional evaluation, it’s essential to be aware of the types of challenges that may arise. While the content can vary, certain topics tend to be emphasized, as they reflect critical aspects of system management and administration. Knowing what to expect allows you to focus your study efforts on the most important areas and enhances your readiness.
The following table outlines some of the most common topics and areas you should focus on to increase your chances of success:
| Topic | Key Areas to Study |
|---|---|
| Network Configuration | IP addressing, DNS setup, subnetting |
| System Security | Firewall configurations, user permissions, encryption |
| Virtualization | Hyper-V setup, virtual machine management, resource allocation |
| Backup & Recovery | Backup strategies, recovery methods, disaster recovery planning |
| Role Management | Active Directory, user group policies, resource access |
| Performance Monitoring | System performance tools, resource allocation, troubleshooting |
Focusing on these key topics will provide a strong foundation and help you approach your assessment with confidence. By reviewing these areas in depth and understanding their practical applications, you’ll be better prepared for the challenges ahead.
Understanding Active Directory in Detail
Active Directory is a fundamental component of IT infrastructures, providing a centralized framework for managing users, devices, and various resources. Understanding how to configure, manage, and troubleshoot this service is crucial for IT professionals. It plays a central role in ensuring secure access, managing permissions, and facilitating communication between different systems in an enterprise environment.
Key Concepts of Active Directory
At its core, this technology organizes network elements in a hierarchical structure that enables efficient administration. It uses domains, trees, and forests to group and manage network resources. Users, computers, and other resources are identified by unique objects within this structure, each with specific attributes that define their roles and permissions.
Managing Users and Permissions
One of the primary functions of Active Directory is user account management. It allows administrators to create, modify, and delete user accounts, assigning appropriate permissions for access to resources. Understanding how to set up user roles, apply group policies, and implement access controls is essential for maintaining security and operational efficiency within an organization.
Exam Insights on Server Management
Effective management of IT infrastructure is crucial for maintaining system performance and reliability. Mastering the processes that ensure smooth operation, from deployment to ongoing maintenance, is key for IT professionals. The ability to manage resources efficiently and resolve issues quickly is tested in various scenarios, making this a critical area of focus for any assessment.
Key Aspects of Resource Management
Resource management involves optimizing the use of hardware and software to meet business needs. This includes configuring storage solutions, managing memory, and allocating processing power to ensure the system operates at peak efficiency. Understanding how to monitor and adjust resources dynamically is essential for handling fluctuating workloads and preventing performance bottlenecks.
Security and Access Control

Security is another integral aspect of managing IT infrastructure. Protecting data and ensuring secure access to system resources requires a strong understanding of access controls, user permissions, and encryption methods. Administrators must be able to configure security settings, apply group policies, and implement audit trails to safeguard sensitive information from unauthorized access or breaches.
Mastering Windows Server Networking
Networking is a critical aspect of IT infrastructure management, and understanding how to configure and troubleshoot network connections is essential for any professional. From basic connectivity to advanced configurations, mastering networking concepts ensures that systems can communicate effectively and securely across an organization. A solid grasp of network protocols, IP addressing, and routing mechanisms is necessary for seamless data flow and efficient resource management.
Core Networking Concepts
To succeed in this area, focus on the following key networking components:
- IP Addressing: Understanding how to configure static and dynamic IP addresses, subnetting, and address allocation is fundamental.
- DNS Configuration: Setting up domain name resolution for efficient resource location is crucial for network operations.
- DHCP Setup: Configuring Dynamic Host Configuration Protocol ensures that devices on the network can automatically receive their IP addresses.
- Routing: Knowing how to set up and troubleshoot routing tables for efficient data transfer between different network segments is essential.
Advanced Networking Tasks
In addition to the basics, there are advanced tasks that professionals must master for complex network environments:
- VLAN Configuration: Segmenting networks for security and efficiency is crucial in large infrastructures.
- Network Monitoring: Tools for tracking and analyzing network performance are vital for maintaining optimal operation.
- VPN Setup: Configuring secure remote access for users requires an understanding of virtual private networks and encryption methods.
- Load Balancing: Ensuring high availability by distributing network traffic across multiple resources is essential for mission-critical applications.
Focusing on these areas will provide the necessary knowledge to manage complex network infrastructures effectively. Being proficient in network management is key to ensuring that communication within an organization is smooth, secure, and reliable.
Storage Solutions and Their Importance
Efficient data management is at the core of every IT infrastructure, making reliable storage solutions essential for organizations of all sizes. The ability to store, access, and protect vast amounts of data is critical to ensuring business continuity and smooth operations. With the growing volume of digital information, choosing the right storage options can significantly impact both performance and security.
There are various types of storage technologies, each serving a specific need. Some are designed for speed, others for redundancy, while some focus on scalability. Understanding the benefits and limitations of each option is key to making informed decisions that align with an organization’s goals.
Types of Storage Solutions
Different types of storage are designed to address various requirements, from high-speed access to long-term archival storage. Key options include:
- Direct-attached storage (DAS): Ideal for local systems, providing quick access with minimal configuration.
- Network-attached storage (NAS): A shared storage solution for easy file access and collaboration over a network.
- Storage Area Network (SAN): High-performance storage designed for large-scale environments with advanced needs for data throughput.
- Cloud storage: A flexible and scalable option that offers remote data storage with access from anywhere.
Ensuring Data Security and Redundancy
Data protection is a priority in any infrastructure. Storage solutions should incorporate security measures such as encryption, access control, and redundancy to safeguard valuable information from potential threats. Implementing effective backup strategies ensures that, even in the event of a failure, data can be restored quickly with minimal disruption.
Choosing the right storage strategy can significantly improve performance, scalability, and reliability, while also reducing costs and simplifying data management. Mastery of storage technologies is a vital skill for IT professionals tasked with maintaining robust and secure systems.
Virtualization Essentials for the Exam
Virtualization has become a cornerstone of modern IT environments, allowing businesses to maximize hardware efficiency and streamline resource management. Understanding the principles of virtualization, along with its configuration and management, is essential for professionals seeking to prove their expertise. This technology enables multiple virtual instances to run on a single physical machine, offering flexibility, cost savings, and scalability.
Key Concepts of Virtualization
Mastering virtualization requires familiarity with several core concepts:
- Hypervisor Types: Understanding the difference between Type 1 (bare-metal) and Type 2 (hosted) hypervisors is critical for deployment scenarios.
- Virtual Machines (VMs): VMs are the core units in virtualized environments, and knowledge of their configuration, management, and performance tuning is essential.
- Snapshots and Cloning: These features allow users to capture the state of a VM and replicate configurations, making it easier to manage system backups and tests.
- Resource Allocation: Efficiently assigning CPU, memory, and storage to virtual machines is crucial to maintain performance across virtualized systems.
Benefits and Challenges of Virtualization
While virtualization offers numerous advantages, it also presents unique challenges that must be addressed:
- Cost Reduction: By consolidating physical hardware, organizations can reduce expenses related to equipment and energy consumption.
- Scalability: Virtual environments are highly scalable, allowing for quick deployment of new instances without the need for additional physical hardware.
- Resource Contention: Virtual machines can compete for limited physical resources, so effective resource management and monitoring are essential to avoid performance degradation.
- Security Risks: Virtualized systems can face unique security challenges, such as vulnerabilities in the hypervisor layer or inter-VM threats.
Mastering these virtualization essentials will enable professionals to implement, manage, and troubleshoot virtualized environments effectively, ensuring high availability and optimized performance across systems.
How to Manage Security Settings
Managing security settings is crucial to protecting sensitive data and ensuring that systems remain resilient against threats. Properly configuring security options helps to prevent unauthorized access, data breaches, and system vulnerabilities. A well-maintained security posture requires regular updates, monitoring, and adjustments to settings to adapt to evolving risks and new attack vectors.
Key Security Settings to Focus On
Effective security management requires a deep understanding of several key areas:
- User Account Control (UAC): Ensuring that UAC is properly configured prevents unauthorized users or software from gaining elevated privileges.
- Firewall Configuration: A properly configured firewall restricts incoming and outgoing network traffic to only what is necessary, reducing the risk of external attacks.
- Antivirus and Anti-malware: Keeping antivirus software up to date and running regular scans helps protect systems from known threats.
- Encryption: Enabling encryption for sensitive data ensures that even if data is compromised, it remains unreadable without the proper decryption keys.
Additional Best Practices for Security Management
In addition to basic configuration, consider these best practices for maintaining strong security across all systems:
- Regular Patching: Keeping all software up to date with the latest patches ensures that vulnerabilities are closed before they can be exploited.
- Access Control: Implement strict access controls by ensuring that users and applications have only the permissions necessary to perform their tasks.
- Audit Logs: Regularly reviewing audit logs helps detect unusual activity and potential security breaches early, allowing for faster response times.
- Backup and Recovery Plans: Regular backups and a tested recovery plan ensure that, in the event of a breach or disaster, data can be restored with minimal downtime.
Proper management of security settings is essential for safeguarding systems, data, and users from potential threats. By staying vigilant and following best practices, you can maintain a secure environment that minimizes risks and ensures business continuity.
Backup and Recovery Techniques for the Exam
Effective backup and recovery strategies are essential components of any IT infrastructure, ensuring that critical data is protected from loss and can be quickly restored in case of system failures. Understanding various backup methods, as well as recovery processes, is crucial for maintaining business continuity and minimizing downtime. These techniques play a key role in preparing for potential disruptions, whether caused by hardware failure, accidental deletion, or other disasters.
Types of Backup Methods
There are several approaches to backing up data, each with its own advantages and use cases:
- Full Backup: A full backup captures a complete copy of all selected data, providing a comprehensive solution for recovery, but requiring more time and storage space.
- Incremental Backup: This method only backs up data that has changed since the last backup, making it faster and more storage-efficient, though recovery can be slower as multiple backups may need to be restored.
- Differential Backup: A differential backup captures all changes since the last full backup, offering a balance between speed and recovery time.
- Mirror Backup: A mirror backup creates an exact copy of the data in real-time, providing redundancy but without the versioning benefits of other methods.
Recovery Techniques and Best Practices
Having a solid recovery plan is just as important as creating backups. The following techniques help ensure fast and efficient restoration of data:
- Granular Recovery: This involves restoring specific files or folders from a backup, rather than recovering the entire system, which is useful for minimizing downtime when only a small portion of data is lost.
- Bare-metal Recovery: In the event of a system crash, a bare-metal recovery allows for restoring the entire system to a new machine, including the operating system, applications, and data.
- Cloud-based Recovery: Leveraging offsite backups in the cloud ensures that data can be recovered even if physical infrastructure is compromised or destroyed.
- Tested Recovery Plan: Regularly testing the recovery process helps ensure that backup strategies will work as intended during an actual disaster scenario.
Mastering backup and recovery techniques is vital for anyone responsible for managing IT systems. By implementing these strategies and understanding their nuances, professionals can safeguard valuable data and ensure a smooth recovery in times of need.
Group Policy in Windows Server 2012

Group policies play a central role in managing and configuring network settings across multiple devices in an enterprise environment. They provide administrators with a means to enforce security, standardize configurations, and control user access in a seamless manner. By implementing policies centrally, IT professionals can ensure consistency across a network while minimizing the effort required for individual configurations.
Core Features of Group Policy
Group policies offer a wide range of functionalities that simplify network administration:
- Centralized Configuration: Administrators can define settings in one place, which are then applied automatically to all relevant computers and users.
- Security Management: Policies can enforce security-related settings such as password complexity, lockout rules, and user rights, enhancing the network’s security posture.
- Software Distribution: Administrators can remotely deploy and update software across machines, ensuring that all users have the latest versions of required applications.
- Access Control: Group policies enable fine-grained control over who can access particular resources, providing administrators with the tools to manage permissions effectively.
Types of Group Policy Objects (GPOs)
Group policy settings are applied through Group Policy Objects (GPOs). These objects can be customized to meet the specific needs of the organization:
- Local GPO: Applied to a single machine, local GPOs are useful for configuring settings that only affect one system.
- Domain GPO: These GPOs are applied across the entire domain, ensuring that policies are enforced uniformly across multiple devices and users.
- Organizational Unit (OU) GPO: Policies linked to an organizational unit allow administrators to apply specific settings to a subset of users or computers within the domain.
- Site GPO: These policies are applied to all users and computers within a specific site, helping to manage geographical or network segment-based configurations.
Best Practices for Managing Group Policies
To maximize the effectiveness of group policies, it is essential to follow best practices:
- Testing Before Implementation: Always test new policies in a controlled environment to ensure they do not negatively impact existing configurations or user workflows.
- Scope Policies Carefully: Apply policies only to the relevant users or computers to avoid unintended consequences. Limiting scope ensures that configurations are targeted and precise.
- Regular Audits: Periodically review and audit policies to ensure they remain effective and up-to-date with the organization’s evolving requirements.
- Clear Naming Conventions: Use descriptive names for GPOs to help identify their purpose quickly and make management easier over time.
Effective management of group policies ensures a secure, consistent, and well-organized IT environment. By leveraging the capabilities of GPOs, administrators can enhance the overall performance and security of their network while streamlining administrative tasks.
Preparing for Troubleshooting Scenarios
When it comes to resolving technical issues in a networked environment, preparation is key. Troubleshooting requires a systematic approach to identify, diagnose, and resolve problems efficiently. Understanding common issues, familiarizing yourself with diagnostic tools, and knowing the right steps to follow are essential components in preparing for real-world troubleshooting scenarios. By practicing problem-solving techniques, IT professionals can handle unexpected challenges with confidence.
Common Troubleshooting Challenges

In any IT environment, several recurring issues tend to arise, and knowing how to tackle them is crucial:
- Connectivity Problems: Issues related to network access, such as misconfigured IP settings or faulty cables.
- Slow Performance: Performance degradation often caused by resource constraints or misconfigured settings.
- Permission Issues: Incorrect access controls preventing users from accessing specific resources or applications.
- Software Conflicts: Problems arising from incompatible or outdated software versions installed on the system.
- Hardware Failures: Devices that malfunction or stop functioning due to age or wear, such as hard drives or network adapters.
Step-by-Step Troubleshooting Process
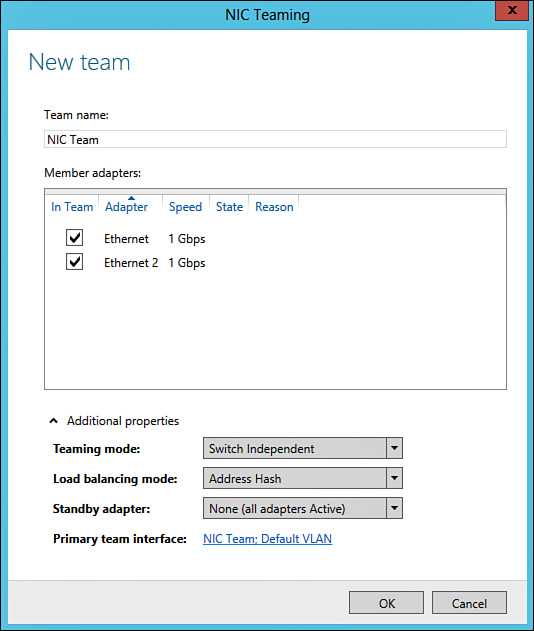
Following a structured methodology is essential for efficient problem resolution. The typical troubleshooting process includes the following steps:
| Step | Description |
|---|---|
| Step 1 | Identify the problem by gathering information about the issue and any error messages. |
| Step 2 | Diagnose the root cause through tools like event logs, network analyzers, or hardware diagnostics. |
| Step 3 | Implement a solution by applying fixes or adjusting configurations based on the diagnosed issue. |
| Step 4 | Test the solution to confirm that the problem has been resolved and that no new issues have been introduced. |
| Step 5 | Document the process for future reference, including the problem, solution, and steps taken. |
By mastering the troubleshooting process and familiarizing oneself with common issues, IT professionals can significantly improve their ability to quickly and effectively resolve technical problems. A proactive approach, combined with ongoing learning and practice, ensures a smoother workflow and more reliable network operations.
Understanding Roles and Features
In any IT infrastructure, understanding the different functionalities and components that can be deployed is crucial. Roles define the primary purpose of a machine or system, while features add additional capabilities that enhance the system’s performance and utility. Together, these elements form the backbone of an efficient environment, allowing administrators to tailor their configurations to specific needs.
Roles refer to the core responsibilities a system assumes in the network. These roles are typically focused on providing specific services such as hosting databases, managing user authentication, or enabling web services. On the other hand, features are optional capabilities that complement the core role. These can include things like advanced security protocols, monitoring tools, or enhanced file management capabilities that improve the system’s overall efficiency and security.
When configuring a system, understanding the distinction between roles and features is essential for ensuring the right combination is chosen. Roles generally set the primary direction of the system’s function, while features are layered on to expand its capabilities. Careful selection of both is necessary to maintain a streamlined and optimized environment that meets business requirements.
For example, a machine designated as a domain controller would primarily focus on handling authentication and managing network resources, which is its role. Features like DNS, DHCP, or Remote Desktop Services might be enabled to provide additional functionality depending on the organization’s needs.
In summary, knowing when to add features or assign specific roles allows IT professionals to create highly customized and efficient systems. By thoroughly understanding each role and feature, system administrators can ensure they are fully utilizing the available resources while keeping their environment secure and optimized.
Configuring Remote Access Services

Enabling remote connectivity is an essential part of modern IT infrastructures. It allows users to securely access network resources from virtually any location, enhancing flexibility and productivity. Setting up remote access involves configuring services that facilitate secure communication between remote clients and internal systems, whether through a virtual private network (VPN), remote desktop access, or other solutions.
To begin with, it is important to understand the different types of remote access methods. Each has specific use cases and security requirements, making it crucial to select the most appropriate service for the environment. Below are some common remote access services and their configuration details:
VPN Setup
A Virtual Private Network (VPN) creates a secure tunnel over the internet, allowing users to connect to the network as if they were physically present. Configuring VPN access involves several steps, such as enabling VPN server roles, choosing the appropriate VPN protocols (PPTP, L2TP, or SSTP), and setting up user authentication methods.
Remote Desktop Access
Remote desktop allows users to access a computer’s desktop remotely. This service is often used by IT administrators to troubleshoot or manage systems, but it can also be used for general remote work. Configuration includes setting up the Remote Desktop role, adjusting user permissions, and ensuring proper firewall settings are in place.
In both cases, strong encryption methods should be used to protect data transmitted over the internet. Additionally, authentication methods like multi-factor authentication (MFA) can add an extra layer of security.
| Remote Access Service | Key Configuration Steps | Security Considerations |
|---|---|---|
| VPN | Install VPN role, configure protocols, set up IP address pools | Enable strong encryption, use multi-factor authentication |
| Remote Desktop | Enable Remote Desktop, configure user access, adjust firewall rules | Configure secure access policies, use network level authentication (NLA) |
Overall, configuring remote access services requires careful planning to ensure that users can connect securely while maintaining the integrity of the internal network. Following best practices for encryption, authentication, and access control will help mitigate security risks and ensure reliable remote access to organizational resources.
Practice Questions and Final Tips
Preparing for any certification assessment requires both understanding core concepts and practicing problem-solving. One of the most effective ways to get ready is by engaging with mock scenarios that simulate the actual conditions of the test. By doing so, you not only reinforce your knowledge but also familiarize yourself with the format and difficulty level of the challenges you might face.
In this section, we will explore a few practice scenarios that can help sharpen your skills and provide valuable insights into the areas that require more focus. Additionally, we will offer some final tips that can help you approach your preparation and test day with confidence.
Sample Practice Scenarios
- Scenario 1: You are tasked with configuring a remote connection for users working from home. What are the steps to establish a secure VPN and what security protocols should you implement?
- Scenario 2: An administrator needs to create a backup strategy for critical data. Which options are available, and how would you ensure that the backup is both reliable and efficient?
- Scenario 3: You need to troubleshoot a performance issue with a network service. What diagnostic tools would you use, and what steps would you take to resolve the issue?
Final Tips for Success

- Understand Key Concepts: Make sure you have a strong grasp of the foundational principles before diving into advanced topics. This includes understanding network infrastructure, security principles, and disaster recovery protocols.
- Practice Regularly: Engage with practice scenarios and quizzes as frequently as possible. This helps in identifying areas that need improvement and builds confidence in answering questions quickly and accurately.
- Time Management: During your preparation, simulate timed assessments to get a feel for the actual test conditions. On the test day, ensure you manage your time effectively so that you can tackle every section with focus.
- Stay Updated: Keep up with the latest updates in technology and best practices. The field is always evolving, and being aware of the latest trends will give you an edge.
By focusing on practice scenarios and following these final tips, you will be better prepared for the challenges ahead. Take the time to review your weak points and improve on them, and don’t forget to stay calm and confident as you approach the assessment.