
In today’s digital age, securing networks and systems has become a top priority for organizations worldwide. Professionals in this field are expected to possess a deep understanding of both theoretical concepts and practical skills. Certifications designed to evaluate these abilities are highly valued by employers, as they demonstrate expertise in safeguarding critical information and infrastructure.
Achieving proficiency in this domain requires a combination of knowledge, hands-on experience, and the ability to solve real-world challenges. The certification process typically includes a comprehensive assessment that tests an individual’s ability to respond to security threats, design robust defense mechanisms, and maintain secure communication systems. Success in such assessments signals readiness to take on key roles in safeguarding digital environments.
For those looking to pursue a career in this field, thorough preparation is essential. The journey involves mastering complex topics related to system defense, risk management, and the protection of sensitive data. With the right approach and resources, individuals can improve their chances of success and advance their careers in this ever-evolving industry.
Huawei Cyber Security Exam Answers
For those preparing to validate their expertise in protecting digital networks, it is crucial to be well-versed in the specific topics that the assessment covers. While the content may seem complex, understanding the key concepts and studying real-world scenarios can significantly improve one’s ability to succeed. This section aims to provide an overview of the most important areas to focus on, offering insights into common questions and the skills required for a successful outcome.
Key Areas of Focus
The assessment typically evaluates a broad range of topics, including system defense, threat detection, and risk mitigation. A comprehensive understanding of the following concepts is essential:
- Network architecture and design principles
- Data encryption and secure communications
- Risk assessment and management strategies
- Incident response and recovery processes
- Vulnerability analysis and remediation techniques
Approaching the Test
Successful candidates often adopt a methodical approach to preparing for this evaluation. Here are some tips to help increase your chances of success:
- Study each topic in-depth, focusing on practical applications.
- Take practice assessments to familiarize yourself with the question format.
- Review case studies and real-world examples to understand how theoretical knowledge applies in practice.
- Join study groups or online forums to discuss difficult concepts and gain new insights.
By focusing on these areas and employing effective study strategies, individuals can improve their understanding and readiness for the assessment, ultimately demonstrating their competence in the field of digital infrastructure protection.
Overview of Huawei Cyber Security Certification
Obtaining a certification in network protection and digital defense is an essential step for professionals aiming to excel in the field of IT infrastructure safeguarding. This qualification not only validates the technical skills of candidates but also enhances their credibility in the industry. The certification program is designed to ensure that individuals are equipped with the necessary knowledge and hands-on experience to secure critical systems and mitigate potential threats.
Certification Process and Requirements
The certification pathway typically involves a rigorous process that evaluates both theoretical understanding and practical abilities. Candidates are required to demonstrate proficiency in a variety of topics related to system defense, network vulnerabilities, and data protection. To achieve certification, candidates must meet the following criteria:
- Completion of relevant training programs or courses
- Successful completion of a comprehensive evaluation
- Hands-on experience with real-world security scenarios
Benefits of Certification
Holding a recognized credential in the field of digital protection offers several advantages, including:
- Increased job opportunities in a rapidly growing field
- Higher salary potential and career advancement
- Enhanced credibility and recognition within the IT industry
Achieving this certification signifies a professional’s commitment to upholding the highest standards in safeguarding digital environments. It is a valuable asset for those looking to take on challenging roles in securing sensitive data and ensuring operational continuity.
Key Topics Covered in the Exam
In order to assess a professional’s ability to protect critical systems and respond to evolving threats, the certification process covers a wide range of topics. These subjects ensure that individuals possess a deep understanding of both foundational principles and advanced techniques required to secure networks and data. It is important to be well-versed in each area to succeed and demonstrate expertise in the field.
Core Areas of Focus
Several core concepts form the backbone of the evaluation, including:
- Network architecture and secure communication protocols
- Risk management and threat detection techniques
- Data encryption methods and secure transmission standards
- System hardening and vulnerability mitigation practices
- Incident response planning and disaster recovery procedures
Advanced Topics and Techniques
Alongside the fundamentals, candidates are also tested on more advanced subjects, such as:
- Advanced firewall configuration and access control mechanisms
- Intrusion detection and prevention systems
- Behavioral analytics and anomaly detection
- Ethical hacking techniques and penetration testing methods
By covering both basic principles and advanced strategies, the assessment ensures that professionals are prepared to handle a variety of challenges in protecting digital infrastructures and responding to potential risks.
How to Prepare for the Exam
Preparing for a certification in digital infrastructure protection requires a strategic approach, as it encompasses a variety of technical areas and practical skills. To excel, candidates must develop a clear study plan, familiarize themselves with key concepts, and gain hands-on experience. Proper preparation is crucial for understanding complex topics and effectively applying them in real-world scenarios.
Study Plan and Key Resources
Creating a structured study schedule helps ensure comprehensive coverage of the essential topics. Prioritize areas based on their relevance to the assessment and your existing knowledge. Below is a table outlining key resources and strategies to enhance your preparation:
| Study Area | Recommended Resources | Study Tips |
|---|---|---|
| Network Protection Techniques | Online courses, textbooks | Focus on network design, firewalls, and VPNs |
| Risk Management | Workshops, practice scenarios | Understand risk assessment models and mitigation strategies |
| Data Encryption | Video tutorials, labs | Study cryptographic algorithms and protocols |
| Incident Response | Case studies, simulation tools | Practice creating and executing response plans |
Practical Experience
While theoretical knowledge is essential, hands-on experience plays a vital role in reinforcing concepts and building confidence. Engage in practical exercises such as:
- Setting up and configuring security devices
- Simulating threat scenarios and practicing mitigation
- Working with virtual environments to test various defense strategies
By combining a structured study plan with practical exercises, you can improve your readiness and boost your chances of success in the assessment process.
Common Questions and Answers for the Certification
During the certification process, candidates often encounter specific questions that assess their knowledge and ability to apply concepts in practical scenarios. Understanding the types of questions that typically appear can help individuals prepare more effectively and increase their chances of success. In this section, we will explore some common queries that are frequently tested, along with key insights to guide your preparation.
Frequently Asked Questions
The following questions are commonly seen on the assessment, focusing on various aspects of digital infrastructure protection:
- What is the primary function of a firewall in network defense?
- How do you identify and mitigate vulnerabilities in a system?
- What methods are used to encrypt sensitive data during transmission?
- Explain the process of performing a risk assessment for an organization.
- How would you respond to a breach of confidential information in a network?
Sample Responses
Here are sample responses to some of the above questions that demonstrate the level of detail and understanding required:
- Firewall Function: A firewall acts as a barrier between a trusted internal network and untrusted external networks, controlling incoming and outgoing traffic based on predefined security rules.
- Identifying Vulnerabilities: System vulnerabilities can be identified through regular security audits, vulnerability scanning tools, and penetration testing, followed by the application of patches or configuration changes to mitigate risks.
- Data Encryption: Data encryption techniques such as AES (Advanced Encryption Standard) or RSA are used to protect sensitive information by converting it into an unreadable format during transmission, ensuring that only authorized parties can decrypt and access the data.
- Risk Assessment: A risk assessment involves identifying potential threats, evaluating the impact of those threats, and determining the likelihood of their occurrence. It also involves implementing appropriate countermeasures to reduce the level of risk to acceptable levels.
- Incident Response: When faced with a breach, an immediate response plan should be activated, including isolating affected systems, assessing the extent of the breach, and executing recovery procedures to minimize damage and restore normal operations.
By understanding the types of questions and practicing these key responses, candidates can sharpen their knowledge and improve their performance during the certification process.
Tips for Passing the Certification Test
Successfully passing a certification assessment in the field of digital infrastructure defense requires not only theoretical knowledge but also practical application. By adopting the right strategies and focusing on key areas, candidates can significantly improve their chances of success. This section outlines several proven tips to help individuals prepare more effectively and tackle the test with confidence.
Effective Study Strategies
A well-structured study plan is essential for mastering the material. Focus on the most relevant topics and practice applying them in real-world situations. The following table highlights key strategies and resources to guide your preparation:
| Strategy | Action Plan | Resources |
|---|---|---|
| Understand Core Concepts | Review fundamental topics such as network design, encryption, and risk management. | Textbooks, online courses, and video tutorials |
| Practice with Simulations | Engage in hands-on exercises to simulate real-world defense scenarios. | Virtual labs, practice tests |
| Take Timed Practice Tests | Familiarize yourself with the test format and time constraints by completing mock tests. | Sample questions, online practice exams |
| Join Study Groups | Collaborate with others to discuss complex topics and share insights. | Online forums, local study groups |
Key Focus Areas
While it’s important to study all relevant topics, some areas tend to be emphasized more frequently in the assessment. Pay special attention to:
- Network protocols and defense mechanisms
- Data protection techniques and encryption methods
- Incident response and disaster recovery planning
- Threat detection tools and strategies
By following these strategies and concentrating on key areas, you’ll be well-prepared to approach the test with confidence and increase your chances of success.
Understanding the Security Framework
In today’s digital landscape, robust defense mechanisms are essential for protecting critical information and infrastructure. A comprehensive security framework is designed to establish a structured approach to safeguarding systems and data from various threats. This framework outlines policies, procedures, and technologies that work together to ensure the integrity, confidentiality, and availability of data.
Key Components of the Framework
The security framework is built upon several core components that help organizations address potential vulnerabilities and implement effective defense strategies. These components include:
- Risk Management: Identifying potential threats and vulnerabilities and taking proactive steps to mitigate or eliminate them.
- Access Control: Implementing measures to ensure that only authorized users can access sensitive systems and data.
- Data Encryption: Protecting information by converting it into a secure format that can only be read by authorized individuals or systems.
- Incident Response: Establishing processes for detecting, responding to, and recovering from security breaches or disruptions.
- Continuous Monitoring: Regularly analyzing systems for potential weaknesses and unusual activity to maintain a high level of vigilance.
Framework Benefits
By implementing a well-defined security framework, organizations can:
- Enhance their ability to defend against evolving threats.
- Establish clear protocols for handling potential risks and breaches.
- Ensure compliance with industry standards and regulatory requirements.
- Increase stakeholder confidence in the organization’s ability to protect sensitive information.
A comprehensive security framework provides organizations with the tools and strategies needed to safeguard their digital assets and maintain operational continuity in the face of potential threats.
Essential Skills for Digital Protection Professionals
In the ever-evolving world of technology, professionals tasked with safeguarding digital infrastructures must possess a diverse set of skills to effectively combat emerging threats. The role of a digital protection expert requires both technical proficiency and strategic thinking. Mastering certain abilities is crucial for identifying vulnerabilities, defending against attacks, and ensuring the continuity of critical systems and data.
Core Technical Competencies
To excel in this field, individuals need a strong foundation in various technical areas. These include:
- Network Protocols: Understanding how different communication protocols work, including TCP/IP, HTTP, DNS, and others, is vital for detecting and mitigating potential risks.
- System Hardening: The ability to strengthen operating systems and software to prevent unauthorized access or exploitation.
- Incident Response: The ability to quickly and effectively respond to security breaches, containing damage and ensuring that operations resume with minimal disruption.
- Cryptography: Knowledge of encryption algorithms, key management, and secure communication methods is critical to protecting sensitive information.
- Threat Analysis: Identifying and evaluating threats through tools like vulnerability scanners, penetration testing, and threat intelligence platforms.
Soft Skills and Strategic Thinking
While technical expertise is essential, soft skills are equally important in the realm of digital protection. These skills enable professionals to work effectively within teams, communicate risks clearly, and make informed decisions. Key soft skills include:
- Problem-Solving: Being able to approach complex challenges with logical solutions is crucial when dealing with intricate security issues.
- Communication: The ability to clearly articulate security risks and mitigation strategies to both technical teams and non-technical stakeholders is vital.
- Attention to Detail: Small oversights can lead to significant vulnerabilities, so attention to every aspect of the system is necessary to ensure comprehensive protection.
- Adaptability: The technology landscape is constantly changing, so professionals must be able to quickly adapt to new tools, methods, and threats.
Mastering both technical competencies and soft skills will position professionals to effectively address the diverse challenges in digital protection, ensuring a proactive approach to defending critical systems.
Role of Digital Protection in IT

In today’s digital landscape, ensuring the safety of information systems is crucial to maintaining the integrity and functionality of IT infrastructures. The field of digital defense plays a significant role in protecting sensitive data, preventing unauthorized access, and maintaining the availability of critical applications. As businesses become more reliant on technology, the demand for robust defense measures has never been greater. This domain encompasses a wide range of strategies, tools, and methodologies aimed at safeguarding digital assets against ever-evolving threats.
The importance of an effective defense framework in IT extends beyond just protecting data; it also involves ensuring business continuity, managing risks, and enabling secure digital transformation. As organizations integrate more connected devices, cloud computing, and mobile technology into their operations, the need for comprehensive defense strategies grows exponentially. The role of digital defense is no longer limited to traditional IT departments but has expanded to become a fundamental component of overall business strategy.
Key Contributions to IT Infrastructure
Digital defense solutions contribute to the IT ecosystem in several vital ways:
- Data Protection: Safeguarding personal and corporate data from unauthorized access, theft, or corruption is a primary focus. Encryption, firewalls, and intrusion detection systems are essential tools for this.
- Incident Management: A critical aspect of defense is having the ability to detect, respond to, and recover from security breaches or attacks, ensuring minimal disruption to business operations.
- Regulatory Compliance: Adhering to industry standards and government regulations is necessary to avoid legal consequences and maintain customer trust. Digital protection frameworks help organizations meet these compliance requirements.
- Risk Management: Proactively identifying potential threats and vulnerabilities in the IT environment allows businesses to implement measures that reduce risks before they become critical issues.
Enabling Innovation and Digital Transformation
As businesses adopt new technologies, such as cloud computing and the Internet of Things (IoT), digital defense solutions play a pivotal role in ensuring these innovations are secure. By providing a strong defense framework, organizations can confidently embrace digital transformation, knowing that their systems and data are protected from evolving cyber threats. This, in turn, fosters an environment of trust, enabling businesses to innovate and grow without fear of compromising security.
In conclusion, digital defense is an indispensable aspect of modern IT infrastructure, providing the necessary tools and strategies to protect against cyber threats, ensure regulatory compliance, and support innovation. Its role in safeguarding both data and operations is crucial for businesses to thrive in the digital age.
Challenges Faced in Security Assessments

When preparing for assessments in the field of digital defense, candidates often face a variety of hurdles that test not only their technical knowledge but also their ability to apply concepts in real-world situations. These evaluations are designed to challenge individuals’ understanding of critical frameworks, tools, and strategies used to safeguard networks and information systems. As such, aspiring professionals must navigate various obstacles to perform well and succeed in these high-stakes evaluations.
Complexity of Topics
One of the primary challenges in these assessments is the breadth and complexity of the topics covered. The field is vast, and candidates must have a deep understanding of numerous concepts, including:
- Encryption Methods: Understanding how different encryption algorithms work, along with their applications and potential weaknesses.
- Network Security Protocols: Mastering various protocols, such as IPsec, SSL/TLS, and VPNs, which are essential for protecting communication channels.
- Incident Response Procedures: Knowing how to handle security breaches, from identification to containment and recovery, can be intricate and highly detailed.
These topics require thorough preparation, as each subfield has its own set of principles and techniques that must be understood to correctly answer related questions.
Time Pressure and Practical Application
Another challenge that candidates face is the time constraint imposed during assessments. Many tests involve practical scenarios where the candidate must demonstrate their ability to solve real-time security problems. This pressure can be overwhelming for some, as they must not only recall information quickly but also apply it effectively under tight deadlines. Additionally, hands-on exercises may require the use of specific tools or configurations that candidates may not be completely familiar with, adding another layer of complexity.
- Simulated Attacks: In some assessments, candidates are tasked with responding to simulated cyberattacks, requiring quick thinking and an understanding of attack vectors and mitigation strategies.
- System Configuration and Troubleshooting: Configuring and troubleshooting systems within a limited time frame can be a difficult task, requiring both theoretical knowledge and practical experience.
Ultimately, succeeding in these assessments demands a combination of deep technical knowledge, practical skills, and the ability to perform under pressure, making preparation critical for candidates.
Study Resources for Certification
Preparing for a certification in the field of digital defense requires a structured approach and access to various learning materials. A comprehensive understanding of key concepts, tools, and best practices is essential for achieving success in these assessments. Fortunately, there are a variety of resources available to help individuals gain the knowledge and hands-on experience needed to excel. Whether you are new to the field or looking to deepen your expertise, these resources can provide valuable insights and support.
Official Study Materials
One of the most reliable sources of information comes directly from the official materials provided by the certifying body. These resources are specifically designed to guide candidates through the required knowledge areas and offer in-depth explanations of essential topics. They may include:
- Official Training Courses: Structured lessons designed to cover all relevant topics in detail, often led by industry experts or certified trainers.
- Study Guides: Comprehensive books and online guides that break down complex concepts into more digestible sections, perfect for self-study.
- Practice Tests: Simulated questions that mirror the actual assessments, allowing you to familiarize yourself with the format and test your knowledge.
Online Platforms and Communities
In addition to official study materials, online platforms provide a wealth of supplementary resources to aid your preparation. These platforms offer flexibility and a broad array of learning options, including:
- Webinars and Video Tutorials: Visual and interactive lessons that explain key concepts and provide demonstrations of practical applications.
- Discussion Forums: Communities of professionals and learners where you can ask questions, share experiences, and get advice from those who have already completed the certification process.
- Online Courses: Flexible and self-paced courses available through various educational websites, often offering specialized content and expert instructors.
Hands-on Practice
Practical experience is crucial for mastering the concepts involved in digital defense. The following methods can help reinforce theoretical knowledge through direct application:
- Simulated Environments: Virtual labs that mimic real-world systems, allowing you to practice tasks like network configurations and vulnerability assessments.
- Open Source Tools: Free security tools that you can download and experiment with, gaining hands-on experience in areas like penetration testing and encryption.
- Internships or Volunteering: Gaining real-world experience by working with professionals in the field or contributing to projects can provide invaluable learning opportunities.
By utilizing a combination of these resources, candidates can enhance their understanding, sharpen their skills, and approach the certification process with confidence.
Practice Tests for Digital Defense Certifications
One of the most effective ways to prepare for certification assessments in the realm of information protection is through practice tests. These simulated tests help candidates familiarize themselves with the format and style of the questions they will encounter, allowing them to assess their knowledge and identify areas that need improvement. By regularly engaging in practice exercises, individuals can build confidence, enhance their test-taking strategies, and improve their chances of success.
Benefits of Practice Tests
Taking practice tests offers numerous advantages, including:
- Improved Familiarity with Question Format: Practice questions often mirror the style and difficulty level of actual assessments, helping you become accustomed to the types of queries you will face.
- Time Management Skills: Simulated tests often have time limits, which allows candidates to practice answering questions within the required time frame.
- Enhanced Retention: Regularly testing yourself reinforces key concepts and increases long-term retention, making it easier to recall important information during the actual assessment.
- Identifying Weak Areas: By reviewing your performance in practice tests, you can pinpoint areas where you need more study and direct your efforts accordingly.
Where to Find Practice Tests
There are various platforms where candidates can access high-quality practice tests designed to simulate the real certification process. These include:
- Official Certification Websites: Many certification bodies provide sample questions and practice exams on their websites, allowing you to test your knowledge in a controlled environment.
- Third-Party Learning Platforms: Websites like Udemy, LinkedIn Learning, and Pluralsight offer practice exams as part of their certification preparation courses, providing valuable practice material.
- Books and Study Guides: Many study guides come with a set of practice questions at the end of each chapter or in a dedicated section, giving you additional opportunities for hands-on practice.
Utilizing a variety of practice tests from these sources will help ensure a well-rounded preparation strategy, offering both theoretical insights and practical testing experience to maximize your performance in the actual certification assessment.
Security Certification Question Patterns
Understanding the structure and patterns of questions in a certification assessment can significantly improve your chances of success. By recognizing common types of questions and their underlying concepts, you can tailor your study approach and focus on the most important areas. Knowing the typical question formats helps reduce anxiety and enables you to approach each section with confidence and clarity.
Common Question Types
The questions in such assessments typically fall into several categories, each designed to test different aspects of knowledge. The main types include:
- Multiple Choice: These questions present a scenario followed by a list of possible answers. Only one of the options is correct, requiring the candidate to choose the most appropriate answer based on the question context.
- True or False: This type of question provides a statement, and the candidate must determine whether it is accurate or not.
- Scenario-Based: These questions describe a real-world situation, and the candidate must choose the most suitable response or solution based on the given scenario.
- Fill-in-the-Blank: A question is presented with missing words or phrases, and the candidate must complete the sentence correctly using the appropriate terms.
Question Difficulty Levels
Questions are generally categorized by their difficulty level, which helps to assess a candidate’s overall understanding of the subject matter:
- Beginner-Level: These questions assess fundamental concepts and terminology. Candidates should have a basic understanding of the principles to answer these correctly.
- Intermediate-Level: These questions involve more complex scenarios, requiring a deeper understanding of the concepts and how they apply in practice.
- Advanced-Level: Advanced questions are designed to challenge the candidate’s expertise, requiring not only knowledge but also the ability to apply concepts in complex situations.
Being familiar with these common question patterns and difficulty levels will help you focus your preparation efforts and approach each section of the assessment with a clear strategy.
Understanding Network Protection Tools
Network protection is a critical aspect of modern IT infrastructure, and a range of tools exist to help safeguard systems from potential threats. These tools are designed to prevent unauthorized access, monitor network traffic, and ensure the integrity of sensitive information. They play a key role in both detecting and mitigating risks in real-time. Understanding how these tools function and how to implement them effectively is essential for maintaining a robust and secure network environment.
Types of Network Protection Tools
There are several types of tools used in network defense, each with specific functions to address various vulnerabilities:
- Firewalls: These act as barriers between trusted internal networks and untrusted external sources, filtering incoming and outgoing traffic based on predetermined security rules.
- Intrusion Detection Systems (IDS): These systems monitor network traffic for suspicious activity or known threats and can alert administrators about potential intrusions.
- Intrusion Prevention Systems (IPS): Unlike IDS, IPS not only detects but also takes action to block potential threats in real time, preventing them from causing harm.
- Virtual Private Networks (VPNs): VPNs encrypt data traffic between users and networks, ensuring that sensitive information is transmitted securely over the internet.
- Anti-virus and Anti-malware Software: These tools scan network devices for malicious software and viruses, providing an additional layer of protection by preventing malware from spreading.
Implementing Network Protection Tools
While the tools mentioned above are essential for securing a network, their effective implementation requires careful planning and configuration. Some key considerations include:
- Regular Updates: Keeping the protection tools up to date with the latest definitions and security patches ensures they are effective against new and emerging threats.
- Comprehensive Monitoring: Continuous monitoring of network traffic allows for the early detection of suspicious activities and enables quick responses to potential security breaches.
- Access Control: Properly configuring access control lists (ACLs) and network segmentation helps limit unauthorized access to sensitive resources, reducing the risk of exploitation.
Mastering the use of these tools is a crucial step in defending networks from malicious actors, ensuring that systems remain operational, secure, and resilient against evolving threats.
How to Use Cyber Defense Labs
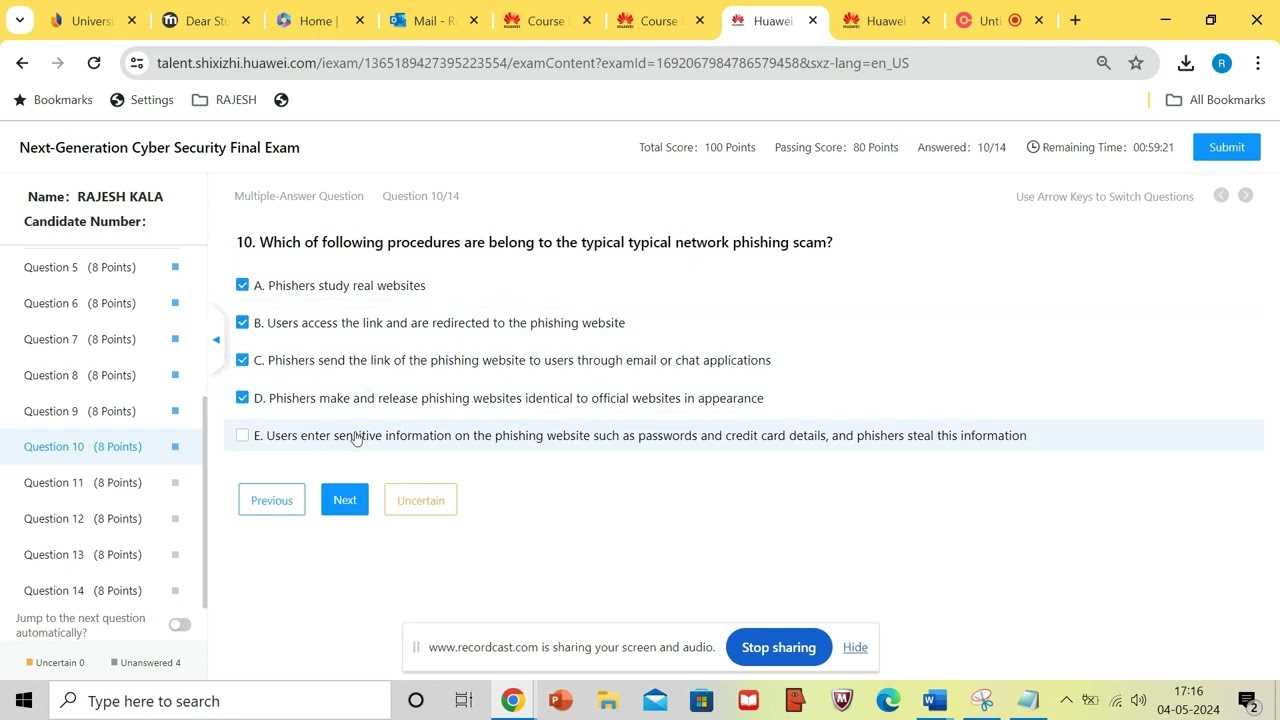
Hands-on practice is essential for mastering the tools and techniques required to defend digital networks. Cyber defense labs provide a controlled environment where individuals can simulate real-world attacks and test defensive measures without the risk of damaging live systems. These labs offer a variety of scenarios, enabling users to experiment with different configurations and gain valuable experience in network protection.
Accessing the Labs
To begin using the cyber defense labs, users typically need to register for an account and gain access to a virtual environment designed for testing and learning. The process often involves the following steps:
- Sign-up: Register for a platform that offers access to virtual labs, usually provided by educational institutions, security vendors, or certification providers.
- Lab Setup: After registration, users can select the desired scenarios or modules based on their learning objectives, such as testing intrusion prevention systems or simulating phishing attacks.
- Interactive Exercises: Users can complete exercises that focus on real-world cyber threats, helping them to practice techniques like vulnerability scanning, packet analysis, and traffic monitoring.
Maximizing Learning Opportunities

To get the most out of the cyber defense labs, it is important to approach the learning process systematically:
- Start with Basics: Begin by mastering foundational concepts like network architecture, access control, and firewalls before diving into more complex simulations.
- Practice Regularly: Consistent hands-on experience is key to building confidence and expertise. The more you interact with the tools and environments, the better your ability to respond to actual threats.
- Participate in Challenges: Many platforms offer challenges and competitions where users can test their skills against each other, simulating attack and defense scenarios in a competitive setting.
Using cyber defense labs not only helps sharpen technical skills but also prepares individuals for real-world security tasks. These environments allow for safe experimentation and problem-solving, essential for anyone looking to develop proficiency in network defense and risk mitigation.
Post-Exam Career Opportunities in Cyber Defense
After completing a certification in network protection, many individuals seek to advance their careers in this rapidly growing field. The knowledge and skills gained through structured learning can open up a wide range of career paths, especially as organizations continue to invest in their digital infrastructure. Those who have completed relevant training are often equipped with the expertise needed to tackle real-world challenges and contribute to safeguarding critical systems.
Potential Career Paths
There are various professional avenues available for those with a background in digital protection, from technical roles to managerial positions. Some of the most common career options include:
| Job Title | Primary Responsibilities | Skills Required |
|---|---|---|
| Network Security Engineer | Design, implement, and manage security systems to protect network infrastructure. | Network protocols, firewall configuration, intrusion detection systems. |
| Incident Response Specialist | Handle security breaches, investigate incidents, and mitigate damage. | Forensic analysis, problem-solving, crisis management. |
| Security Analyst | Monitor and assess potential threats, report vulnerabilities, and improve defense mechanisms. | Risk assessment, penetration testing, vulnerability scanning. |
| Penetration Tester | Simulate attacks to identify weaknesses in systems and networks. | Ethical hacking, vulnerability assessment, scripting. |
Advancing in the Field
For those interested in advancing their career, there are numerous opportunities for further education and specialization. Some professionals choose to pursue advanced certifications, while others focus on gaining practical experience in specific industries such as finance, healthcare, or government. Additionally, roles in management, such as Chief Information Security Officer (CISO), may become accessible to those who demonstrate leadership skills and a deeper understanding of the broader business context.
Ultimately, the digital protection field offers a diverse range of opportunities, allowing professionals to pursue their interests and further develop their expertise. As technology continues to evolve, so too do the challenges and opportunities in this field, making it a dynamic and rewarding career path.