
When it comes to managing sensitive information, proper handling and the ability to classify materials correctly is essential. Organizations, particularly those in governmental and defense sectors, rely on clear guidelines to ensure that data is treated with the appropriate level of protection. The process of determining the sensitivity of documents and how they should be shared or stored plays a critical role in maintaining national security and organizational integrity.
In many situations, individuals must demonstrate their understanding of how to manage and categorize information accurately. This includes recognizing what constitutes sensitive data and the potential risks that can arise from mishandling it. Training and assessments help to reinforce these skills, making sure that employees at all levels know how to handle various materials in compliance with strict protocols.
While the need for vigilance in these areas is clear, there are challenges in consistently applying rules and recognizing subtle nuances in what qualifies as restricted content. This can make it difficult for individuals to navigate the complexities of ensuring that information is handled according to established policies. By studying key concepts and applying them in practical scenarios, individuals can prepare for any situation that might require quick and accurate decision-making when dealing with confidential materials.
Understanding Security Awareness in Classification
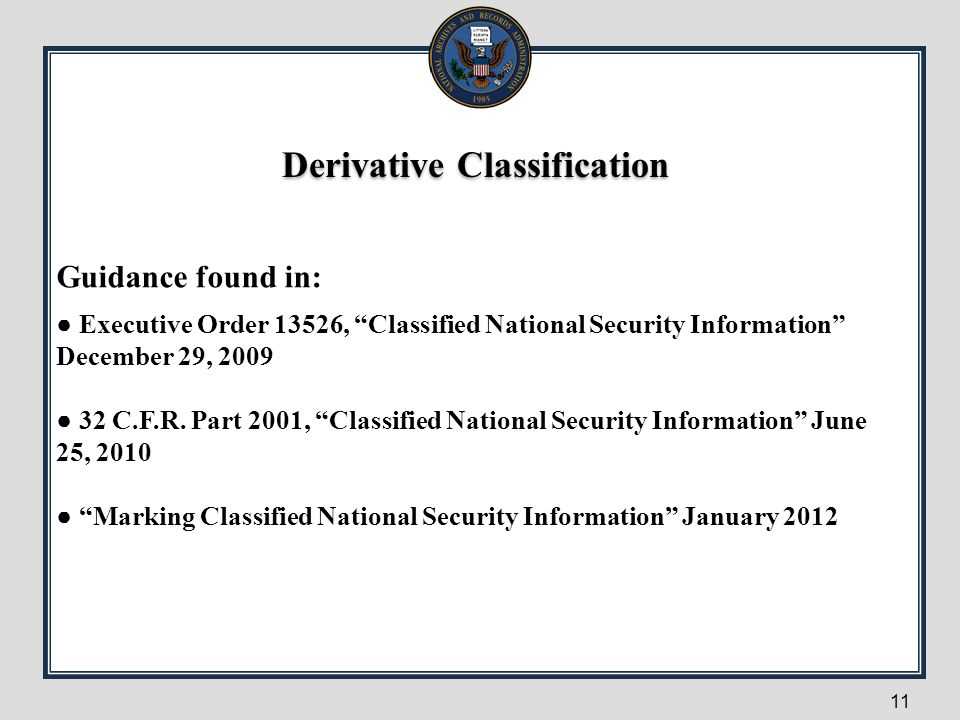
Handling sensitive information requires more than just following a set of rules; it involves a deep understanding of how to protect data from unauthorized access while ensuring compliance with established protocols. Individuals tasked with managing this information must know how to properly assess its sensitivity, store it, and share it when necessary. This process not only involves identifying which materials need protection, but also understanding the potential consequences of mishandling or misjudging the level of confidentiality required.
The Role of Individuals in Data Protection
Each person in an organization plays a critical part in maintaining the integrity of sensitive documents. Whether an employee is dealing with personal records, confidential communications, or classified reports, the responsibility to handle these materials appropriately lies with them. Mistakes or lapses in judgment can have serious ramifications, ranging from security breaches to legal consequences. Thus, fostering an environment where all personnel are equipped with the knowledge to assess and act on information security is crucial.
Challenges in Handling Confidential Information
Despite the best efforts to establish clear guidelines, challenges persist when it comes to recognizing and dealing with information that requires protection. This can include difficulty in distinguishing between different types of confidential materials or understanding how changes in context can impact the sensitivity of data. Continuous training and practice are necessary to ensure that individuals are consistently up to date and capable of making sound decisions, even in complex or rapidly changing environments.
The Role of Derivative Classification in Security
Properly identifying and managing sensitive materials is essential for protecting both organizational interests and national integrity. When individuals handle documents that are based on existing restricted content, they must understand how to apply the correct level of confidentiality to prevent unauthorized access or leakage of critical information. This process involves reviewing the content and determining whether it requires the same or a modified level of protection as the original materials.
The importance of this process lies in its ability to maintain consistent protection for information across various stages of handling. By ensuring that new documents retain the necessary safeguards, organizations reduce the risk of accidental exposure or mishandling. This responsibility extends to anyone who comes into contact with sensitive data, regardless of their role within the organization.
Key Principles for Managing Sensitive Information
To successfully maintain proper safeguards, certain core principles must be followed when evaluating and handling restricted data:
| Principle | Description |
|---|---|
| Consistency | Ensuring that all materials are evaluated and categorized according to the same standards. |
| Accountability | Taking responsibility for how information is classified and safeguarded, ensuring no unauthorized access occurs. |
| Compliance | Adhering to established regulations and guidelines to prevent improper handling of restricted materials. |
| Awareness | Being fully aware of the sensitivity level of the information and taking appropriate action to protect it. |
By following these principles, individuals help prevent vulnerabilities that might otherwise be exploited. Their role in applying the correct measures to sensitive data is fundamental to maintaining trust and safeguarding against risks associated with information exposure.
Key Concepts of Security Classification
Properly managing and safeguarding sensitive data requires a thorough understanding of how to determine the level of confidentiality necessary for different types of information. This process ensures that materials are protected from unauthorized access and misuse. Individuals who work with classified or sensitive content must be able to assess what information needs to be secured and how it should be handled in different contexts. These concepts are critical for maintaining the integrity of organizational operations and national interests.
Levels of Confidentiality
One of the primary components in handling sensitive information is identifying the appropriate level of access required for each type of data. Generally, materials are categorized into several levels, each representing varying degrees of protection. The level assigned depends on the potential harm that could result from unauthorized disclosure. Understanding these distinctions helps individuals apply the correct safeguarding measures to each piece of information.
| Classification Level | Definition | Example |
|---|---|---|
| Top Secret | Information that, if disclosed, could cause exceptionally grave damage to national security. | Military operation plans |
| Secret | Information that could cause serious damage to national security if disclosed. | Diplomatic communications |
| Confidential | Information that could cause damage to national security if disclosed. | Internal government memos |
| Unclassified | Information that does not require protection and can be freely shared. | Publicly available reports |
Determining Sensitivity
Each document or piece of information must be carefully evaluated to determine its sensitivity. This assessment considers factors such as the potential harm from unauthorized disclosure, the context in which the information is used, and the impact it could have on operations or security. By understanding these principles, individuals can make informed decisions about how to treat different types of data and apply the necessary protections to prevent misuse or leakage.
Importance of Accurate Information Handling
Correctly managing and processing confidential materials is crucial to maintaining organizational integrity and protecting national interests. The way information is handled, stored, and shared can have significant implications, not only for the entity in question but also for broader societal and geopolitical stability. By ensuring that sensitive data is treated with the appropriate care and attention, organizations can avoid serious risks such as unauthorized disclosures, data breaches, or misuse of information.
Consequences of Mishandling Data
Mishandling sensitive information can result in various negative outcomes, from reputational damage to severe legal consequences. The improper release or access to protected content can compromise public trust, hinder operations, and even put lives at risk. For instance, in government or military settings, the unintentional exposure of confidential information could undermine efforts to protect national security or disrupt vital diplomatic negotiations.
Best Practices for Managing Sensitive Data
To avoid the negative outcomes associated with mishandling, it is essential to follow best practices for handling sensitive materials. This includes maintaining proper documentation, using secure storage methods, and ensuring that access is limited to those with a legitimate need. Furthermore, regular training is critical to keep individuals informed of the latest protocols and potential risks, ensuring that they are capable of making informed decisions about data protection.
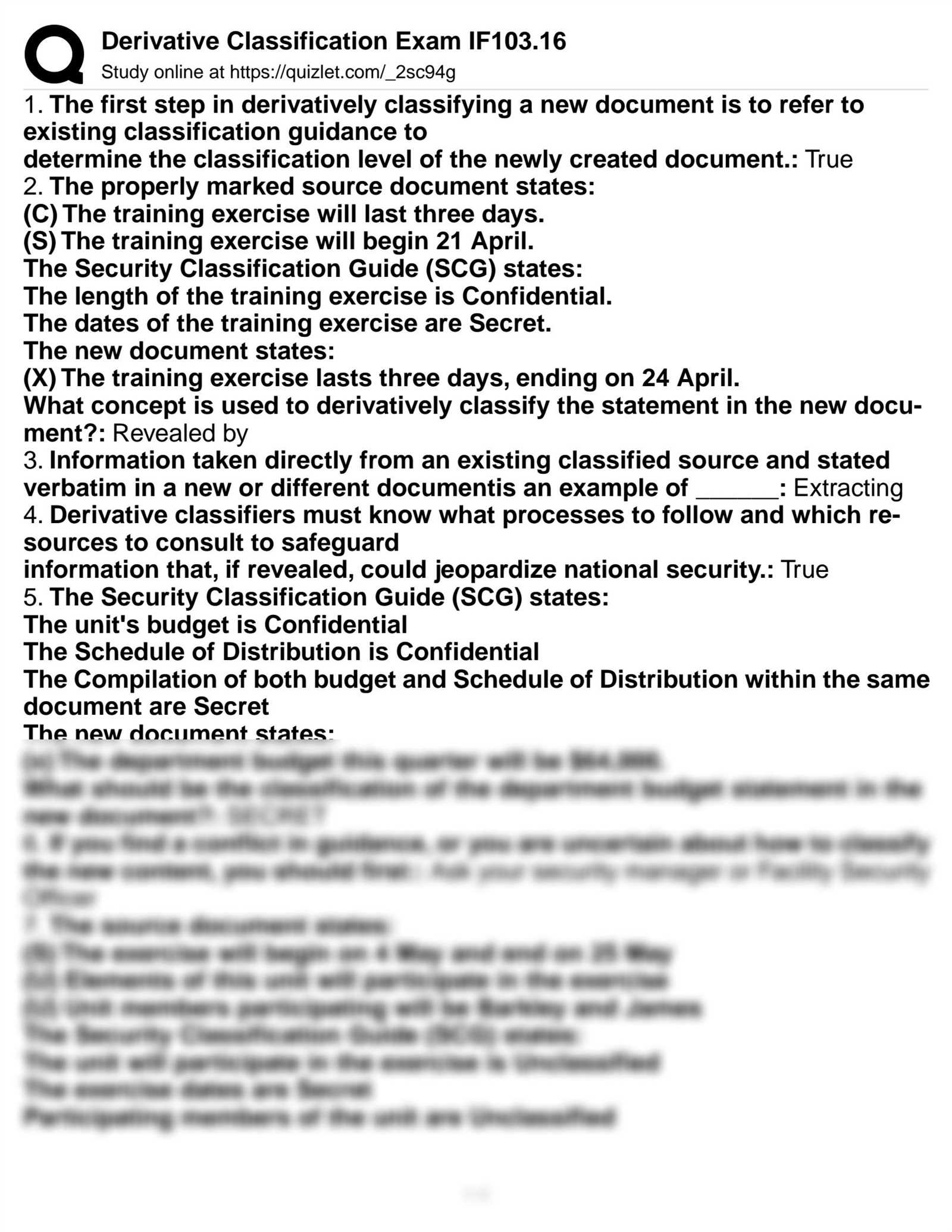
Common Errors in Derivative Classification
Handling sensitive materials requires attention to detail and adherence to established protocols. Even small mistakes in determining the appropriate level of protection can have serious consequences. Many errors stem from a lack of understanding or misapplication of the guidelines for assessing and managing confidential information. Identifying these common mistakes helps reduce the risk of mishandling data and ensures that information remains properly protected.
Failure to Assess Sensitivity Properly
One of the most common errors is failing to fully assess the sensitivity of the information. In some cases, individuals may apply an incorrect classification level to materials without thoroughly reviewing the content or context. This can occur when assumptions are made about the content’s importance or relevance, leading to an over- or under-estimation of its need for protection. Proper evaluation is essential to ensure that no data is exposed to unnecessary risk.
Improper Use of Markings and Labels

Another frequent mistake is the improper use of classification markings or labels on documents. Incorrectly labeling a document or failing to mark it at all can lead to confusion and increase the chance of unauthorized access. Additionally, failing to update labels when the sensitivity level changes can result in documents being improperly handled or shared. Accurate and timely updates to markings are vital to maintaining the integrity of information management procedures.
Principles of Information Sensitivity Management
Effective management of confidential data is vital to ensuring that it remains protected and is only accessible to those who are authorized to view it. The fundamental principles guiding the treatment of sensitive materials are designed to help individuals assess, handle, and safeguard information in a manner that minimizes risks and complies with legal and organizational standards. By following these principles, organizations can maintain control over critical data while preventing unauthorized exposure.
Need-to-Know and Access Control
The principle of “need-to-know” is central to managing sensitive information. It dictates that access to confidential materials should be limited to individuals who have a legitimate reason to know or use the information. This ensures that only those with the necessary authority or responsibility are privy to specific details, reducing the likelihood of accidental exposure or misuse. Access control systems should be in place to enforce this principle, ensuring that permissions are carefully managed and regularly updated.
Minimizing Risk through Proper Handling
Another critical principle is minimizing risk by handling sensitive information with the highest level of caution. This includes storing data in secure environments, using encryption when transmitting information, and regularly reviewing materials to ensure that they are classified and protected appropriately. Additionally, training individuals to recognize the sensitivity of the materials they work with and to follow best practices for secure handling is essential in mitigating the potential for leaks or unauthorized access.
How to Identify Classified Material
Recognizing materials that require protection is a crucial skill for anyone handling sensitive documents. Proper identification ensures that restricted information is not inadvertently exposed or mishandled. Understanding the signs and markers of confidential content is vital in maintaining proper access control and safeguarding valuable data. It’s essential to be able to distinguish between materials that are publicly available and those that must be kept secure.
The most obvious indicators of confidential materials are the markings and labels used to denote their sensitivity level. These markings are often required by law or policy and should be checked carefully when handling any documents. In addition to physical markings, the context in which the information is used and the potential consequences of unauthorized disclosure can also help determine whether something is classified.
Besides labels, the content itself may provide clues. If the information pertains to sensitive topics, such as national defense, intelligence operations, or private business strategies, it may require extra precautions. When in doubt, individuals should always err on the side of caution and treat materials as classified until they can confirm otherwise through the proper channels.
Classified vs. Unclassified: Key Differences
Understanding the distinction between restricted and open information is crucial for ensuring the proper handling and distribution of data. The level of sensitivity attached to various materials directly influences who can access them, how they should be stored, and the protocols required for sharing. These differences are key to maintaining operational integrity and preventing unauthorized exposure of important details.
Restricted Information
Restricted or confidential data is subject to strict control measures, as it contains sensitive content that could harm national interests, security, or other critical areas if disclosed to unauthorized individuals. Access to such materials is limited to personnel with the appropriate clearance level and a legitimate need to know. Typically, these documents are accompanied by specific protocols for handling, transmission, and storage.
- Access is restricted to approved individuals only.
- Improper handling or exposure can lead to severe consequences.
- Requires secure storage and transmission methods.
Open Information
On the other hand, open data is freely available and does not contain any sensitive or confidential content. It can be shared openly within the public domain or among groups without the risk of compromising any security or operational integrity. This type of information is typically less controlled and can be distributed without the same level of oversight as restricted content.
- No limitations on who can access or share it.
- Can be freely distributed and made public.
- Does not require special storage or transmission measures.
Training Requirements for Classification Compliance

Ensuring that personnel are properly equipped to handle sensitive materials requires comprehensive training on the correct procedures for managing and protecting such information. Employees must understand the rules governing access, distribution, and safeguarding of data to prevent inadvertent mishandling. This training helps maintain organizational integrity and reduces the risk of breaches or unauthorized disclosures.
Key Components of Training
Training programs should cover a range of topics to ensure employees are fully aware of their responsibilities and obligations when dealing with sensitive content. Key areas include recognizing different levels of confidentiality, knowing how to handle restricted materials, and understanding the protocols for marking and safeguarding data.
- Understanding different data sensitivity levels and their implications.
- Procedures for securing sensitive information during handling, storage, and transmission.
- Identifying common risks and how to mitigate them.
Ongoing Education and Certification
Compliance is an ongoing process, and regular training is essential for reinforcing key concepts and ensuring that employees stay up-to-date with any changes in guidelines or regulations. In addition to initial training, periodic refresher courses and certifications should be part of the ongoing professional development plan.
- Mandatory refresher sessions at regular intervals.
- Re-certification to ensure ongoing competency and awareness of updated standards.
- Evaluation of employees’ understanding through assessments and feedback.
Impact of Misclassification on National Security
Improper handling and incorrect categorization of sensitive information can have severe consequences, especially when it involves national defense or critical government operations. When data is not properly identified or marked, it can either lead to unnecessary restrictions on important information or, conversely, make sensitive content accessible to unauthorized individuals. Both scenarios pose risks that can affect the safety, stability, and strategic advantages of a nation.
Risks of Overclassification
When information is classified at higher levels than necessary, it can create unnecessary barriers to the efficient sharing and use of important data. This overclassification can slow down decision-making processes, prevent collaboration between agencies, and hinder innovation. Moreover, the excessive control over non-sensitive information often leads to wasted resources and increased bureaucracy.
- Delayed decision-making due to restricted access to relevant data.
- Increased administrative overhead and inefficiency.
- Potential public frustration or mistrust if information is overly restricted.
Consequences of Underclassification

On the other hand, when materials that should be protected are improperly labeled as non-sensitive, they may fall into the wrong hands, leading to potentially dangerous situations. Unauthorized access to critical intelligence, defense strategies, or diplomatic discussions can undermine national interests and security. In some cases, it can directly contribute to espionage or terrorism.
- Unauthorized access to critical defense or intelligence information.
- Exposure of national vulnerabilities to adversaries.
- Damage to diplomatic relations and international trust.
In short, proper management of sensitive information is essential to avoid both the risks of overburdening systems with unnecessary restrictions and the dangers of exposing critical details to those who should not have access. Accurate classification ensures the right balance between transparency and protection, safeguarding a nation’s most vital interests.
Understanding Declassification Processes
The process of removing restrictions from previously protected materials is a critical part of ensuring that valuable information becomes accessible when it no longer poses a threat. As time passes, many documents or data that were once deemed sensitive may lose their relevance or pose no risk if shared. Understanding the procedures for lifting these restrictions ensures that data can be released responsibly, maintaining a balance between accessibility and protection of critical interests.
Criteria for Declassification
To determine when materials can be de-restricted, several factors are considered. These criteria help assess whether the information still holds strategic value or if it can be safely made available without compromising national interests or operational effectiveness. Typically, this involves reviewing the content for any potential risks and evaluating the evolving context surrounding the data.
| Criteria | Description |
|---|---|
| Time-based considerations | Some materials lose their sensitivity after a certain period or event. |
| Relevance | If the information is no longer critical for operations or strategic purposes. |
| Risk assessment | Evaluating if releasing the data would expose vulnerabilities or cause harm. |
Declassification Procedures
The formal process for de-restricting documents typically involves a thorough review by appropriate authorities, such as subject matter experts or designated officials. This review ensures that all risks are mitigated before any materials are released. In some cases, partial declassification may be applied, where only certain sections of a document are made public, while other parts remain restricted due to ongoing sensitivity.
- Initial review by authorized personnel to assess the document’s sensitivity.
- Consultation with relevant agencies or experts to determine potential risks.
- Approval and official release of de-restricted information.
Practical Tips for Security Testing
Ensuring that employees are proficient in handling sensitive information and following best practices is essential to protecting an organization. Regular testing can help assess the effectiveness of training and identify areas where improvements are needed. Effective testing methods ensure that personnel are equipped to recognize potential risks and follow the necessary procedures when interacting with critical data.
Designing Effective Testing Scenarios
Creating realistic and challenging scenarios is key to evaluating how well individuals understand and react to different situations. Tests should reflect common threats and challenges, such as phishing attempts or social engineering tactics, that employees might encounter. Additionally, scenarios should cover a range of difficulty levels, from basic recognition of secure practices to more complex decision-making situations.
- Simulate common phishing or fraud attempts to assess how employees respond.
- Include scenarios involving password protection, data sharing, and system access.
- Test employees’ ability to recognize and report suspicious behavior or threats.
Evaluating Results and Providing Feedback

After testing, it’s important to analyze the results and provide targeted feedback. This allows you to identify gaps in knowledge or areas where individuals may need additional guidance. Constructive feedback helps reinforce correct behaviors and address any misunderstandings before they lead to mistakes. Follow-up training sessions may be necessary to ensure that everyone is consistently applying the right practices.
- Review test results to identify common mistakes or knowledge gaps.
- Offer targeted follow-up training for areas that require improvement.
- Provide positive reinforcement for correct behavior and decision-making.
Real-World Scenarios in Derivative Classification
In the real world, professionals are often tasked with handling and labeling information that originates from various sources. Understanding how to correctly mark and safeguard sensitive materials is critical in everyday operations, especially when it comes to managing data that could have broader implications if exposed. Applying proper procedures when working with such content ensures that sensitive details are not inadvertently disclosed or mishandled.
Scenario 1: Handling Documents with Multiple Sources
Imagine you are tasked with reviewing a report that consolidates information from various departments within your organization. Some sections of the report may include sensitive details from a higher-level internal brief, while others contain general publicly available data. Properly identifying and marking the sensitive portions of the report is crucial to maintaining control over what information is shared and with whom.
- Identify sensitive data from each department before combining the information.
- Ensure any proprietary or restricted material is marked appropriately.
- Cross-check the document to ensure no sensitive information is unintentionally included in the non-sensitive sections.
Scenario 2: Reusing Sensitive Content in New Reports
When reusing sections of previous reports or documents, it’s important to assess whether any information retains its sensitive nature. For example, if you are incorporating sections of a previous internal memo into a new presentation, you must verify that no restricted content is included or accidentally exposed through the new format.
- Review the original document for sensitive details before extracting content.
- Reassess any reused material to ensure it is still subject to restrictions.
- Clearly mark any newly included sections if they contain previously classified information.
Scenario 3: Collaborating on Shared Sensitive Information
In collaborative settings, multiple individuals may contribute to a document or project that involves sensitive content. This increases the likelihood of mistakes, as different people may have different levels of understanding of the sensitivity of various materials. Coordination and clear communication are key to ensuring that the final product is properly handled.
- Clearly communicate the importance of proper information handling to all collaborators.
- Designate one individual to review the document for sensitive content before finalizing it.
- Ensure that all collaborators understand the implications of improperly sharing sensitive data.
Challenges in Maintaining Security Standards

Maintaining high standards for handling sensitive information can be an ongoing struggle for many organizations. As threats evolve and regulations change, organizations must continually adapt to new methods and practices to safeguard their most critical data. This requires not only implementing the right policies but also ensuring that employees consistently follow them, even as the work environment shifts and new risks emerge.
Adapting to Changing Threats
One of the main difficulties organizations face is keeping up with the constantly evolving nature of threats. As new technologies and tactics emerge, so do new risks. Organizations must continuously update their practices to address these risks while maintaining operational efficiency. This can be particularly challenging when dealing with a rapidly changing technological landscape or when responding to emerging trends in cyberattacks or data breaches.
- Staying informed about the latest threats and attack vectors.
- Regularly updating policies and procedures to address new risks.
- Training employees on how to recognize and mitigate emerging threats.
Balancing Efficiency and Compliance
Another challenge is finding the right balance between maintaining operational efficiency and adhering to stringent standards for handling sensitive materials. While it is crucial to protect data, overly complex or cumbersome procedures can slow down workflows and reduce productivity. Organizations must develop processes that meet the required standards without creating unnecessary friction or hindering performance.
- Streamlining procedures without compromising on data protection.
- Ensuring compliance while maintaining productivity.
- Finding the right tools and technologies to support both efficiency and safety.
Legal and Ethical Considerations in Classification
When dealing with sensitive information, there are significant legal and ethical responsibilities that must be considered. The way in which data is handled, shared, and protected is governed by laws and regulations that aim to prevent misuse and ensure the privacy of individuals, organizations, and even national interests. Ethical considerations also play a crucial role in balancing transparency and the protection of critical information, ensuring that decisions made around data management are responsible and justifiable.
Legal Implications
Legal requirements surrounding the handling of sensitive data are designed to ensure compliance with national and international standards. Failure to adhere to these regulations can lead to serious legal consequences, including penalties, lawsuits, or even criminal charges. Organizations must stay up-to-date with changing laws and regulations that govern the management of information to ensure that they remain compliant.
- Strict adherence to national laws regarding data protection and privacy.
- Compliance with international standards for the handling of sensitive materials.
- Legal consequences for the unauthorized release or mishandling of confidential data.
Ethical Responsibilities
Ethically, organizations must ensure that they do not abuse their control over sensitive materials. This includes making decisions about who has access to certain information, ensuring that the data is used for legitimate purposes, and safeguarding it from exploitation or misuse. Ethical considerations also require organizations to strike a balance between protecting sensitive data and providing transparency where possible, especially when public trust is at stake.
- Protecting privacy and confidentiality while ensuring transparency when appropriate.
- Responsible decision-making about who is granted access to sensitive data.
- Avoiding misuse of sensitive information for personal or political gain.