Ensuring the confidentiality and security of sensitive information is a critical aspect of modern regulatory practices, particularly in the healthcare industry. As organizations navigate complex legal frameworks, understanding how to safeguard personal data is essential. This section will guide individuals through the key concepts and best practices required to meet compliance standards, addressing the various requirements and obligations set forth in relevant legislation.
The process of meeting these standards involves both theoretical knowledge and practical applications. It is vital to be familiar with the rules that govern data management, particularly in environments where individuals’ health information is handled. This article will provide insights into the steps necessary for individuals and organizations to demonstrate their understanding and adherence to these important rules.
Through this comprehensive guide, we aim to clarify the expectations and equip you with the knowledge needed to navigate the assessment process. By mastering these principles, you can confidently manage responsibilities while ensuring the protection of valuable data.
HIPAA and Privacy Act Training Challenge Exam Answers 2025
Successfully navigating compliance requirements in the healthcare sector is crucial for professionals who manage sensitive data. Understanding the rules governing data protection ensures organizations maintain trust and meet legal obligations. This section will explore the main elements that candidates must be familiar with to demonstrate competence in data handling, focusing on safeguarding individual information in compliance with current regulations.
Key Elements for Success in Compliance Assessments
To excel in the assessments, it is essential to understand the core principles that govern data confidentiality and security. These principles guide professionals in managing personal details while ensuring that their organizations adhere to required standards. Grasping these concepts prepares individuals for a thorough evaluation of their knowledge and practical understanding of the relevant regulations.
Preparing for the Compliance Evaluation
Preparation for the evaluation involves reviewing critical topics such as consent management, data access limitations, and proper information sharing practices. Being well-versed in these topics allows professionals to navigate scenarios where data protection is tested. Below is a table summarizing some key topics covered in preparation material:
| Topic | Description |
|---|---|
| Data Security Protocols | Measures to ensure unauthorized access is prevented while managing sensitive data. |
| Confidentiality Requirements | Guidelines on keeping personal information private, both physically and electronically. |
| Legal Responsibilities | Understanding the obligations of organizations to protect individuals’ rights under the law. |
| Incident Management | Protocols for handling breaches or unauthorized access to sensitive data. |
By thoroughly studying these topics, candidates can build a solid foundation for passing their assessments and demonstrating a comprehensive understanding of their responsibilities. Familiarity with the practical application of these rules ensures that professionals are well-prepared to protect sensitive information effectively.
Overview of HIPAA Compliance Requirements
Ensuring that sensitive health information is managed in a secure and confidential manner is a key responsibility for organizations and professionals in the healthcare sector. Compliance with established standards and regulations is crucial to protect individuals’ personal data from misuse. This section will outline the essential requirements for maintaining compliance in healthcare settings, focusing on the protective measures that must be implemented to safeguard data effectively.
Essential Security Measures for Data Protection
Security measures play a vital role in preventing unauthorized access to sensitive information. Organizations must implement physical, technical, and administrative safeguards to ensure the confidentiality, integrity, and availability of personal data. The following table summarizes key security measures that must be adopted to meet compliance standards:
| Security Measure | Description |
|---|---|
| Access Control | Restricting access to sensitive information based on user roles and responsibilities. |
| Data Encryption | Protecting data from unauthorized access by encrypting it during transmission and storage. |
| Audit Trails | Maintaining logs to track access and modifications to sensitive information for accountability. |
| Employee Training | Educating staff on the importance of data security and proper handling of sensitive information. |
Compliance Requirements for Organizations

Organizations must establish comprehensive policies and procedures to meet regulatory requirements. These guidelines ensure that individuals’ health data is collected, stored, and shared responsibly. Compliance also requires regular audits and assessments to identify any potential risks or breaches. Below is a table summarizing organizational obligations to ensure ongoing adherence to the required standards:
| Obligation | Description |
|---|---|
| Data Minimization | Collecting only the necessary data required for healthcare operations and purposes. |
| Consent Management | Ensuring that patients’ consent is obtained before collecting or sharing their information. |
| Incident Response | Developing plans to address potential breaches or unauthorized access to data. |
| Ongoing Risk Assessment | Regularly evaluating potential threats to data security and implementing preventive measures. |
By adopting these security measures and organizational requirements, professionals can ensure that they are meeting compliance standards and protecting sensitive information from unauthorized use.
Key Privacy Act Provisions for 2025
In 2025, the landscape of data protection continues to evolve, with new provisions designed to strengthen the security and confidentiality of personal information. These regulations are aimed at ensuring that sensitive data remains protected from unauthorized access, misuse, and disclosure. Understanding the key provisions that govern data handling is essential for professionals tasked with maintaining compliance in this ever-changing regulatory environment.
One of the central elements of these provisions is the emphasis on enhancing transparency in data collection and use. Organizations are required to clearly communicate how personal information is being gathered, stored, and shared, ensuring individuals are informed about their rights. This includes the implementation of stricter controls over access to sensitive data, reinforcing the need for secure systems and protocols.
Furthermore, the regulations now call for a more proactive approach to data security. This means not only reacting to incidents but also anticipating potential threats through continuous monitoring and regular risk assessments. Organizations must take responsibility for identifying vulnerabilities and implementing safeguards to prevent unauthorized access, breaches, or leaks of sensitive information.
As we move further into 2025, it is critical for professionals to remain up-to-date with these provisions to maintain compliance and avoid penalties. This requires a thorough understanding of the updated requirements and their practical application within their respective organizations.
How to Prepare for HIPAA Exams
Successfully completing the required assessments to demonstrate knowledge in data protection requires careful preparation. Understanding the core principles and regulations is essential, as the assessments evaluate both theoretical knowledge and practical application. This section provides guidance on how to effectively prepare and perform well in these critical evaluations.
Key Topics to Study

To ensure success, focus on the most important topics covered in the assessment. Understanding the following areas is crucial:
- Data confidentiality and security measures
- Regulatory guidelines for handling sensitive information
- Procedures for ensuring compliance with data protection laws
- Incident response protocols in case of data breaches
- Best practices for employee training and awareness
Effective Study Strategies

Adopting the right study strategies can greatly enhance your understanding and retention of key concepts. Consider the following tips:
- Review official materials and study guides that cover the most recent updates.
- Practice with mock questions to simulate the test environment and improve response time.
- Join study groups or online forums to discuss challenging topics with peers.
- Use visual aids such as charts and diagrams to better understand complex concepts.
- Take regular breaks and pace your study sessions to avoid burnout.
By focusing on the core subjects and using effective study techniques, you will be well-prepared to pass the assessment with confidence.
Understanding Protected Health Information
In the healthcare sector, ensuring the confidentiality of individual health data is a fundamental responsibility. Personal health details, including medical histories and treatment plans, are highly sensitive and must be carefully safeguarded. This section explores the importance of protecting these types of information and the legal requirements surrounding their use and disclosure.
What Constitutes Protected Health Data?
Protected health information refers to any details related to an individual’s health status, medical treatment, or payment for services that can identify the person. This includes both physical and electronic records, and it is critical to understand the various forms this data can take. It is not limited to traditional paper records but also extends to digital formats such as medical files in electronic systems, emails, or even voice messages.
Legal Protections for Health Data
Legal regulations require strict guidelines for managing and sharing protected health information. Access to this data is restricted to authorized personnel only, and any breach or unauthorized use is subject to significant penalties. The following guidelines are designed to ensure the security and proper handling of this sensitive data:
- Limit access to individuals directly involved in the care or payment processes.
- Use encryption and secure storage methods to protect data from unauthorized access.
- Implement access controls and audit trails to track who accesses the information.
- Obtain explicit consent from individuals before sharing their information with third parties.
It is essential for organizations to adhere to these rules to prevent data breaches and maintain trust with patients. By understanding the types of information classified as protected and the necessary measures to ensure its security, healthcare professionals can better safeguard sensitive health data.
Common Challenges in HIPAA Training

Training professionals to handle sensitive health data appropriately can be a complex process. With the ever-changing nature of regulations and the increasing need for data security, individuals often face difficulties in fully grasping the required protocols. This section highlights some of the common obstacles encountered during the preparation process and offers insight into how they can be addressed.
One major challenge is the vast amount of information that must be understood. Professionals need to learn detailed regulations concerning how personal health data should be collected, used, and shared. This often results in information overload, making it hard for trainees to focus on key concepts. Additionally, many individuals struggle with applying theoretical knowledge in practical, real-world scenarios, leading to a gap between understanding the rules and executing them effectively.
Another challenge is keeping up with frequent updates and changes in regulations. Healthcare laws evolve over time, and staying current with the latest amendments can be difficult. Training programs need to ensure that they incorporate the latest changes to maintain compliance, which can add complexity to the learning process for staff.
Finally, engaging participants during training can be a significant hurdle. Traditional methods, such as lengthy lectures or basic written materials, may fail to capture the interest of learners. Without proper engagement, retention of important concepts becomes more difficult, and professionals may struggle to apply the rules effectively in their daily tasks.
Privacy Act Training Essentials for Success
Effective learning in the realm of data protection requires a clear understanding of the core principles and rules governing the handling of sensitive information. For individuals working with confidential health or personal data, mastering the necessary guidelines is crucial to ensure compliance and avoid costly mistakes. This section focuses on the key elements that make training successful and how organizations can optimize their approach to these essential educational programs.
Core Topics for Effective Learning
To build a solid foundation, it’s important to focus on the most essential subjects. Training should cover both the theoretical framework and practical strategies for ensuring proper data management. The following table outlines the primary topics that should be addressed to ensure comprehensive understanding:
| Topic | Description |
|---|---|
| Data Handling Procedures | Methods for safely collecting, storing, and sharing sensitive data. |
| Access Control | Strategies to limit who can view or edit personal information. |
| Incident Management | Steps to follow in case of a breach or unauthorized access to data. |
| Compliance Monitoring | Processes to regularly assess adherence to data protection rules. |
Engagement and Retention Strategies
For training to be successful, it’s essential that participants are actively engaged in the process. Passive learning methods often fail to produce lasting results. Interactive sessions, such as workshops or case studies, allow participants to apply the rules in simulated scenarios, helping them better retain the information. Additionally, providing real-world examples of data breaches or compliance failures can make the material more relatable and emphasize the importance of following the guidelines.
Organizations should also prioritize regular refresher courses to keep employees up to date with changes in the regulatory landscape. This ongoing education ensures that individuals remain knowledgeable and prepared to handle sensitive data securely throughout their careers.
HIPAA Violations and Consequences Explained
Understanding the potential risks associated with mishandling sensitive information is crucial for anyone working in healthcare or related industries. When data is improperly accessed, shared, or disposed of, it can lead to significant consequences both for individuals and organizations. This section breaks down the common violations that occur and the penalties that may arise from them.
Common Violations of Data Protection Regulations
Violations typically stem from failure to follow established protocols for safeguarding sensitive information. Some of the most common offenses include:
- Improper access to confidential records without legitimate need
- Unauthorized sharing or disclosure of personal health data
- Failure to implement adequate security measures, such as encryption
- Not notifying individuals of breaches in a timely manner
- Negligence in training staff on data protection protocols
Consequences of Violations
The impact of breaching data protection rules can be severe. Organizations and individuals found guilty of violations can face a range of penalties. These may include:
- Financial Penalties: Fines can range from minor fees for inadvertent breaches to substantial amounts for willful misconduct. In extreme cases, these fines can exceed millions of dollars.
- Reputational Damage: Loss of trust from patients or clients can be difficult to recover from, leading to a decline in business or job opportunities.
- Criminal Charges: In some cases, individuals found guilty of severe violations may face criminal charges, including imprisonment.
- Termination of Employment: Employees who fail to follow regulations may face termination, particularly if their actions lead to significant data breaches.
Preventing violations requires a commitment to education, regular compliance checks, and robust data protection practices. By staying vigilant, individuals and organizations can avoid the severe consequences of non-compliance and ensure that sensitive information is handled securely.
Top Resources for Privacy Act Exam Prep
Preparing for assessments related to the handling of confidential information requires access to the right materials. Professionals seeking to demonstrate their knowledge must utilize effective study resources to fully understand the rules, regulations, and best practices for data protection. This section presents some of the most reliable tools to aid in preparation and help achieve success.
Comprehensive study guides, online courses, and practice tests are some of the most valuable resources. By utilizing a combination of these, individuals can reinforce their understanding of key principles while getting familiar with the format of potential questions. Below is a table outlining some of the best tools available for exam preparation:
| Resource | Description |
|---|---|
| Online Study Guides | In-depth written materials that explain rules, regulations, and common practices related to safeguarding sensitive data. |
| Practice Tests | Interactive quizzes that simulate the format of the actual assessment, allowing candidates to test their knowledge. |
| Webinars & Workshops | Live or recorded sessions with experts that provide insights, real-world examples, and clarification of complex topics. |
| Online Courses | Self-paced learning programs that cover all necessary topics in detail, often including videos, readings, and quizzes. |
| Regulatory Websites | Official resources from regulatory bodies offering the most current laws, amendments, and guidelines for handling protected data. |
By using a combination of these resources, learners can build a solid foundation of knowledge, boost their confidence, and be well-prepared for any assessment related to data security compliance.
Frequently Asked Questions on HIPAA Exams
As individuals prepare to assess their knowledge on the handling of confidential information, numerous questions often arise about the process and requirements. Understanding what to expect and how to approach the preparation can make a significant difference in achieving success. Below are some of the most commonly asked questions regarding these types of assessments.
What topics are covered in the assessment?
The test typically covers a range of topics related to the protection of sensitive data, including legal requirements, confidentiality measures, security practices, and compliance protocols. Participants should be familiar with the standards, regulations, and best practices required for safeguarding information.
How long does the assessment take?
The duration of the assessment varies depending on the format and depth of the questions. Most tests last between one to two hours, with some allowing additional time for review. It is important to check the specific time constraints for the relevant test.
Are there study materials available?
Yes, various resources are available to help candidates prepare. These include online courses, practice quizzes, detailed study guides, and official documentation on security measures. Utilizing these tools can enhance understanding and readiness for the assessment.
What is the passing score?
The passing score varies, but most assessments require a minimum of 75% to pass. It is important to understand the specific requirements set by the organization administering the test.
How often do I need to renew my certification?

Depending on the industry or organization, certifications may need to be renewed every 1 to 2 years. Be sure to verify the renewal timeline and any additional training or requirements needed to maintain certification.
Can I retake the assessment if I fail?
Yes, in most cases, individuals can retake the test if they do not pass. However, there may be a waiting period between attempts. Check the specific guidelines of the certifying organization for details on retake policies.
By understanding these frequently asked questions, individuals can better prepare for the process and approach the assessment with confidence. Proper preparation ensures a higher likelihood of success in safeguarding sensitive data and meeting compliance requirements.
What to Expect in the 2025 Challenge Exam

When preparing for the upcoming assessment related to safeguarding sensitive information, it’s important to understand the structure and content of the test. This will ensure that candidates are fully equipped to succeed and meet the required standards. Here’s what you can expect when sitting for this critical assessment.
- Multiple-choice questions: The test will feature a range of questions that assess your knowledge of key principles related to data protection, legal requirements, and confidentiality. These questions are designed to evaluate both theoretical understanding and practical application.
- Scenario-based questions: Expect real-world scenarios that require you to apply your knowledge to solve problems related to the security and handling of sensitive data. These questions test your decision-making skills and ability to identify compliance issues.
- Time constraints: The assessment is typically timed, with a set period for completion. It’s important to manage your time effectively to ensure you can answer all questions thoroughly.
- Practical application: The exam may include sections that test your ability to interpret and implement the standards and guidelines set for handling confidential information, especially in high-pressure or complex situations.
As you prepare for the assessment, it’s crucial to familiarize yourself with the types of questions and topics that are covered. Review key concepts related to security protocols, compliance regulations, and risk management strategies to enhance your readiness. Being well-prepared will boost your confidence and improve your performance on the test.
Understanding Safeguards and Protocols
In any organization that handles sensitive information, it is critical to implement a robust framework of protective measures and procedures. These safeguards ensure that data remains secure, confidential, and protected from unauthorized access or misuse. Understanding these protocols is vital to achieving compliance and mitigating risks.
- Physical Safeguards: These measures involve securing the physical locations where confidential information is stored or processed. This includes locked filing cabinets, secure access to office spaces, and controlled entry points to prevent unauthorized individuals from accessing sensitive areas.
- Technical Safeguards: These safeguards refer to the use of technology to protect data, such as encryption, secure networks, and access control systems. Strong passwords, multi-factor authentication, and firewalls are key components of a secure environment for managing information.
- Administrative Safeguards: These policies and procedures define how organizations manage and monitor access to sensitive data. They include employee training programs, audits, role-based access controls, and regular reviews of practices to ensure compliance and identify potential vulnerabilities.
- Risk Management: Effective risk management involves identifying potential threats to information security and taking proactive steps to minimize or eliminate them. This includes conducting regular risk assessments and implementing corrective actions based on identified weaknesses.
By understanding and implementing these safeguards and protocols, organizations can maintain a high level of security and prevent unauthorized access to critical data. Adherence to these practices is not just a regulatory requirement but also an essential part of building trust and ensuring the integrity of sensitive information.
Importance of Data Security in Healthcare
In the healthcare sector, safeguarding sensitive patient information is essential to maintaining trust, ensuring compliance, and preventing data breaches. With the increasing reliance on electronic systems to manage medical records, the need for robust security measures has never been more critical. Protecting patient data not only ensures privacy but also contributes to the integrity of healthcare services.
Protecting Patient Confidentiality
Patient confidentiality is a fundamental pillar of healthcare. When individuals share personal health details with medical providers, they trust that their information will be kept secure and used appropriately. A breach of confidentiality can lead to serious consequences, including reputational damage, legal repercussions, and a loss of trust between healthcare providers and patients.
Preventing Data Breaches and Cyber Threats
The healthcare industry is a prime target for cybercriminals due to the wealth of personal and financial information stored in medical records. Data breaches can result in the exposure of sensitive information, leading to identity theft, fraud, and other criminal activities. Implementing strong data security protocols helps mitigate these risks by ensuring that only authorized personnel have access to confidential information.
Ensuring the security of healthcare data is not only a matter of compliance but also a critical step in maintaining the trust and safety of patients. As the healthcare landscape continues to evolve with technological advancements, the role of data security will remain central in protecting both patients and organizations from potential threats.
HIPAA and Privacy Act Updates for 2025

As healthcare regulations continue to evolve, staying informed about the latest updates is crucial for organizations and professionals working in the field. Changes to legal frameworks surrounding patient confidentiality and data protection affect not only compliance requirements but also operational procedures. The updates introduced in 2025 reflect ongoing efforts to enhance security, streamline processes, and protect individuals’ personal health information.
Key Changes in Data Handling Requirements
One of the major updates includes new provisions related to data handling. Organizations will be required to implement stricter access controls and improve encryption measures to safeguard sensitive information. These adjustments are designed to reduce vulnerabilities to cyber threats and ensure that personal health data remains secure during both storage and transmission.
- Enhanced access management systems to limit unauthorized access
- Stronger encryption protocols for both digital and physical records
- More robust auditing mechanisms to track data access and usage
Changes to Breach Notification Procedures

The rules surrounding the notification of data breaches have also been updated. A more streamlined process will ensure that affected individuals are notified promptly in the event of unauthorized access to their information. This is intended to minimize the potential harm caused by breaches and give individuals the opportunity to take proactive steps to protect themselves.
- Shortened notification timelines for affected parties
- Clearer guidelines on the scope and nature of breaches
- Stricter penalties for delayed or inadequate notifications
These updates reflect a broader effort to create a more secure, transparent, and effective system for handling personal health information. By adhering to the new regulations, organizations can not only ensure legal compliance but also foster greater trust with patients and the public.
Exam Strategies for Privacy Act Success
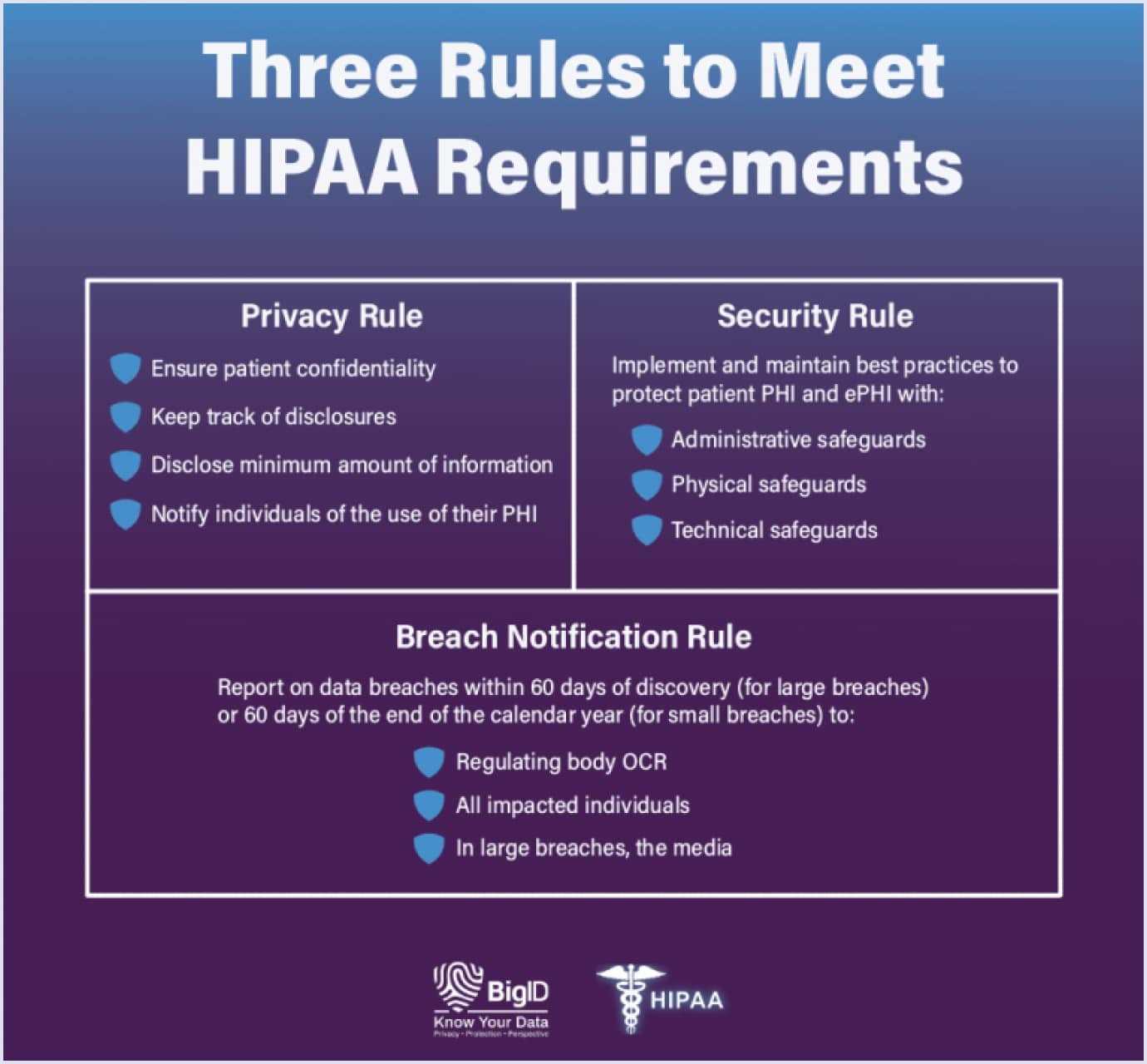
Successfully navigating regulatory assessments requires more than just knowledge–it demands effective preparation and strategic thinking. Whether you are an individual preparing for a certification or part of an organization undergoing an evaluation, mastering the key concepts and understanding the structure of the assessment is essential. By focusing on the right strategies, you can improve your chances of success and ensure that you’re fully prepared for the task ahead.
First, it’s important to identify the core areas covered in the assessment. These typically include legal frameworks, compliance protocols, data handling, breach management, and patient rights. Understanding these topics in depth is crucial for both the theory and application parts of the evaluation.
Focused Review of Key Concepts

A critical strategy is to prioritize your study efforts on the most frequently tested concepts. Focus on understanding the detailed guidelines for managing sensitive information, including proper documentation, access control, and security measures. Spend time reviewing case studies, as these can help you apply theoretical knowledge to real-world situations, which is often tested.
- Study key policies related to data access and sharing.
- Review specific rules for managing patient information securely.
- Practice answering scenario-based questions to hone practical application skills.
Time Management During the Assessment

Time management is a vital component when taking any form of assessment. Allocate time for each section based on its complexity and weight. Be sure to leave extra time to review your responses, especially in sections that involve complex scenarios or detailed regulations.
- Set a time limit for each section and stick to it.
- Use any remaining time to double-check for errors or missed details.
- Prioritize questions based on your knowledge, starting with those you feel most confident in.
By incorporating these strategies into your study and assessment approach, you can significantly enhance your readiness and achieve success. Confidence in your ability to recall key information and apply it effectively will be your greatest asset during the evaluation process.
Case Studies on Privacy Law Enforcement
Real-world scenarios play a crucial role in understanding the application and enforcement of legal frameworks governing sensitive information. Through case studies, we can gain valuable insights into how these laws are applied in practice, the challenges organizations face, and the consequences of non-compliance. These cases also illustrate the measures taken to safeguard confidential data and protect individuals’ rights, ensuring that businesses remain accountable for their actions.
In this section, we will explore notable instances where legal breaches in the handling of personal information have led to significant consequences. These examples help highlight the importance of adhering to regulatory standards and provide clear lessons on how to avoid similar mistakes.
Case 1: Data Breach in a Healthcare Organization

One of the most common types of violations involves unauthorized access to confidential medical records. In this case, a healthcare provider faced a major data breach after a former employee accessed and shared patient records without permission. The organization failed to implement adequate access control mechanisms, which led to the exposure of sensitive information affecting thousands of patients.
The consequences for this breach were severe, both legally and financially. The organization was fined heavily for failing to enforce proper security measures and was required to offer affected individuals free credit monitoring services. This case demonstrates the critical importance of securing personal data, implementing strict access controls, and ensuring that employees are properly trained to handle sensitive information.
Case 2: Financial Institution Fined for Inadequate Data Protection
Another case involved a large financial institution that was fined after a third-party vendor exposed customer financial data due to inadequate encryption practices. The company had outsourced its data management but did not ensure that its vendor followed strict security protocols, leading to a large-scale exposure of private financial information.
The investigation revealed that the institution had not conducted regular audits of its third-party vendors and had not ensured proper compliance with security requirements. As a result, the company faced a substantial fine, legal actions from affected customers, and a damaged reputation. This case highlights the importance of not only protecting internal systems but also carefully vetting and monitoring third-party vendors to ensure compliance with relevant standards.
These case studies highlight how crucial it is to have robust data protection practices, regular monitoring, and a strong understanding of the legal frameworks surrounding information management. They also serve as a reminder that non-compliance can lead to significant financial penalties, legal action, and a loss of public trust.
How HIPAA Impacts Healthcare Professionals
The regulatory frameworks that govern the protection of personal health information have a profound influence on healthcare workers. These laws require professionals to adopt strict guidelines for handling sensitive patient data, ensuring confidentiality, security, and transparency. As healthcare becomes increasingly digital, professionals are tasked with balancing efficient care delivery with stringent privacy obligations, all while staying compliant with these legal requirements.
Healthcare providers, from doctors and nurses to administrators and technicians, must understand how their roles intertwine with these standards. Every interaction with patient data, whether through electronic records, billing information, or communications, must be conducted in adherence to these rules. This impacts not only the way they deliver care but also the administrative and operational procedures within their institutions.
Impact on Daily Operations
Healthcare professionals must implement specific practices that ensure sensitive information is not improperly shared or exposed. This includes following secure methods for storing and transmitting patient data, using encryption tools, and limiting access to only those who need it for their work. Routine activities, such as scheduling, billing, or diagnosing, now require more careful attention to safeguard personal information.
- Use of secure communication channels for patient information
- Regular audits and documentation of data access and transmission
- Implementing strong authentication protocols for healthcare systems
- Ongoing employee education on compliance standards
Legal Consequences for Non-Compliance
Failure to adhere to these laws can result in severe legal and financial repercussions for healthcare professionals and their employers. For instance, unauthorized disclosures of patient information, whether accidental or intentional, can lead to hefty fines, legal claims, and even job termination. In some cases, healthcare workers may face criminal charges if they are found to be willfully negligent in protecting patient privacy.
Professionals must stay vigilant and up-to-date with evolving regulations and institutional policies to avoid breaches that could jeopardize their careers and the trust patients place in their care. It is essential for healthcare providers to foster a culture of compliance that prioritizes security, privacy, and the ethical handling of patient information.
Final Tips for Passing the HIPAA Challenge Exam

Success in achieving compliance and understanding of regulations hinges on being well-prepared and focused. Whether you’re tackling a professional certification or a regulatory assessment, thorough preparation and a strategic approach are key. This section offers insights to help you approach the assessment with confidence and increase your chances of success.
Understand the Core Concepts
Familiarize yourself with the fundamental principles that govern the handling of sensitive personal data. These key areas often include rules around confidentiality, the secure transmission of information, and how to manage records. A solid grasp of these concepts will not only help you during the assessment but also guide you in your daily professional practices.
- Focus on the principles of data security and confidentiality
- Review common protocols for handling and sharing sensitive data
- Understand the role of healthcare professionals in compliance and security
Practice with Sample Scenarios
One of the best ways to prepare is by applying theoretical knowledge to real-world situations. Review case studies or sample scenarios that simulate practical applications of the rules. This will help you learn how to make decisions in real-time and sharpen your problem-solving skills.
- Work through mock scenarios that test your understanding of security practices
- Consider what the consequences would be for different types of data breaches
- Understand the responsibilities of each party involved in safeguarding information
Stay Calm and Focused
As with any assessment, it’s important to remain calm and focused. Avoid rushing through the questions and take your time to read them thoroughly. Pay attention to the wording, as questions may ask for specific details related to compliance or protocols. If you’re unsure of an answer, eliminate obviously incorrect options and make an educated guess.
With the right preparation and mindset, you will be ready to demonstrate your knowledge and pass with confidence.